[Banner Source: The ever-handy http://www.downloadmoreram.com.]
When a tactic becomes less and less effective, it's important to shift strategies and adapt. With malware, attackers are doing exactly that. As preventative measures such as antivirus and endpoint detection and response continue to improve, it's harder for commodity and even obfuscated malware to successfully install and persist on target machines unnoticed.
The most effective pivot, in this continuous back-and-forth, has been to minimize the footprint left after compromising the system. A favorite method is to use stolen credentials—impersonating company employees and services continues to be the top attack vector behind breaches. A newer range of attacks now take advantage of built-in administration tools, such as Powershell and PSExec, that are standard on every Windows machine.
This tactic has many names, including:
- Process Hollowing
- Hijacking Processes
- Remote Code Execution
This stealthy type of attack works best on high-value assets that can be assumed to be closely monitored. For example, let's take a case where an attacker has internal corporate network access via a remote access trojan (RAT) on a low-value, unmonitored asset.
After running reconnaissance, the attacker may use an exploit kit on a vulnerability to gain access to the high-value asset. Once at mission target, they can inject a command & control payload, such as Meterpreter, into a legitimate running process, such as Service Host—svchost.exe. The attacker can then access monetizable files and proceed with data exfiltration. The only traces of this attack exist within Random Access Memory (RAM), rendering it invisible to most antivirus and signature-based detection methods. In fact, if the asset is rebooted, all traces of the attack cease to exist. The attacker can always leave a scheduled task on the system or re-enter the network through the unmonitored asset and laterally move back to the critical target.
Well, how do you identify it then?
Identifying this type of behavior has been a top request from our Managed Detection and Response (MDR) team. We have integrated the CounterTack Digital DNA (DDNA) technology into our MDR offering, which adds an on-demand memory analysis intelligence engine to investigations. This allows our analysts to investigate a layer deeper on customer endpoints and identify processes running with unexpected capabilities.
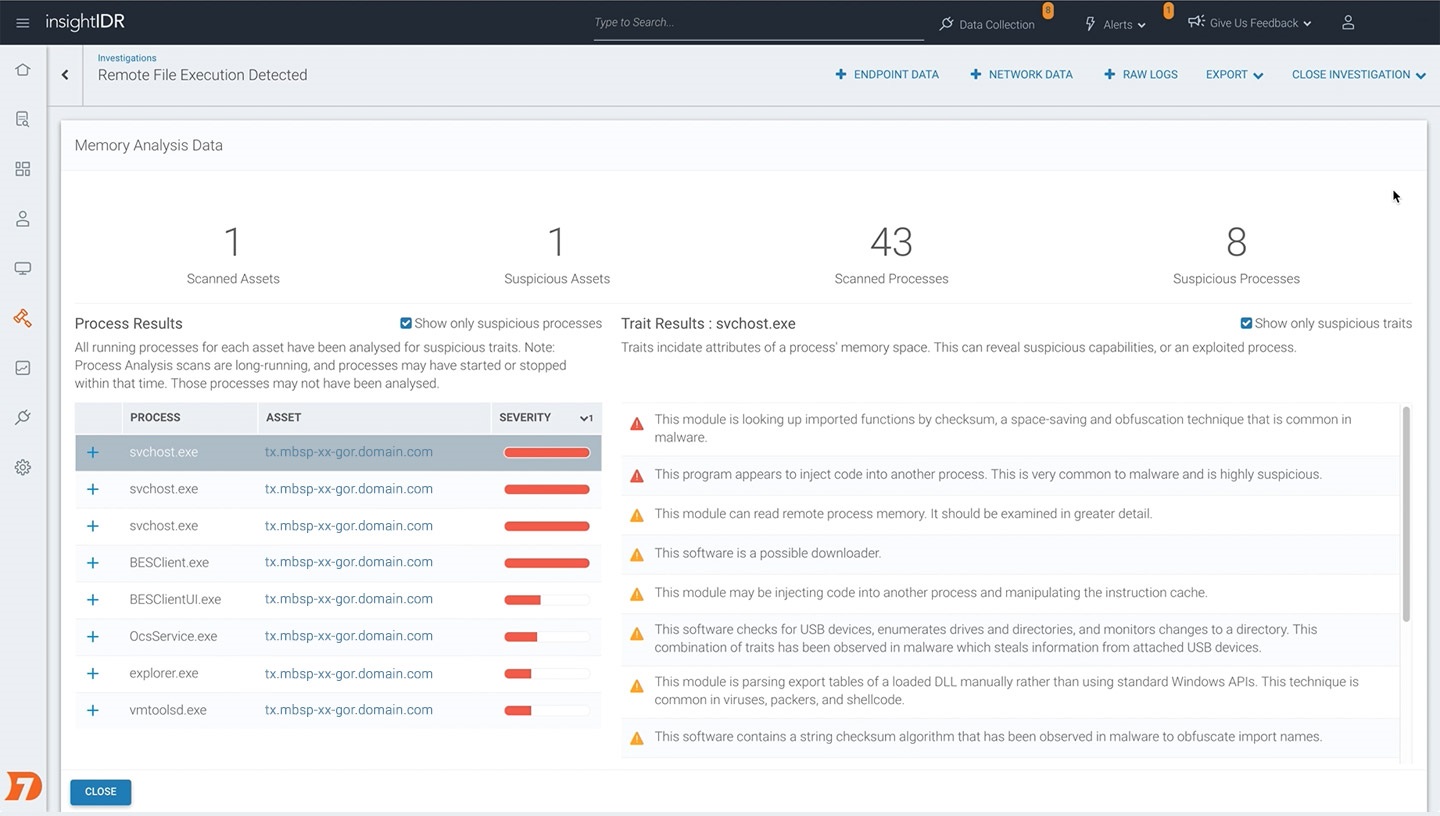
With the Process Memory Analyzer, every running process is analyzed for suspicious capabilities. If the process is performing suspicious behavior, such as injecting code, or looking up imported functions by checksum, this is flagged, and can be added to to the investigations timeline in InsightIDR. In the above screenshot, you'll notice that the feature ranks processes by risk, so it's easy to pick out anomalous processes which may have been victim to process hollowing.
Can I do the same analysis in InsightIDR?
Short answer: stay tuned! We're working closely with CounterTack and our MDR team to ensure this feature is available and intuitive for customers. Once it's out, you'll be the first to know via the guided messaging inside InsightIDR.
This sounds great if I know which assets to investigate. How do I get ahead of that?
Within InsightIDR, we've continued to build our detections library to find attacks other tools miss. For example, you'll receive alerts detecting a wide range of popular pen test and attack tools such as Responder, Mimikatz, Meterpreter, and can easily deploy the included deception technology for earlier attack chain coverage. Learn more about top customer use cases by exploring our InsightIDR Product.
If you leverage our Managed Detection and Response service, that comes with an added layer of 24/7 analyst monitoring, vertical-specific threat intelligence, proactive hunts by our analysts, and of course, the detailed reporting and communication provided by your Customer Advisor. If you'd like to learn more, Kimberlee Bachman will be hosting a webcast with SecurityWeek: Managed SOC — Why Some Fail. Learn more and register here!