No matter how much you mature your security program and reduce the risk of a breach, your life includes the need to report across the company, and periodically, to auditors. We want to make that part as easy as possible.
We built InsightIDR as a SaaS SIEM on top of our proven User Behavior Analytics (UBA) technology to address your incident detection and response needs. Late last year, we added the ability to create custom dashboards and reports through the Card Library and the Log Entry Query Language (LEQL).
Now, we’ve added seven pre-built cards that align directly to PCI DSS v3.2, to help you find important behaviors and communicate it out across the company, the board, and external auditors.

Let’s walk through a quick overview of the seven cards and how it ties to the requirements in PCI DSS v3.2.
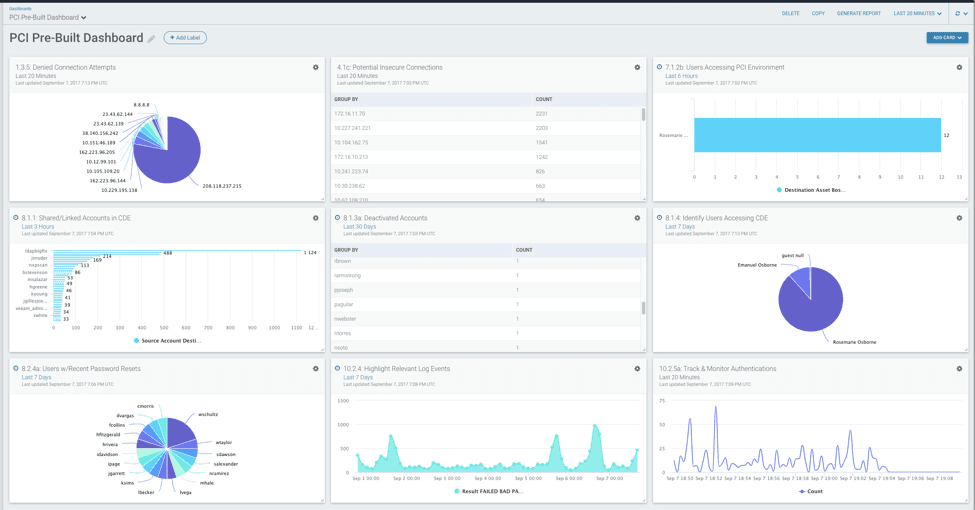
1.3.5: Denied Connection Attempts
PCI Requirement 1 covers installing and maintaining a firewall configuration to protect cardholder data. InsightIDR can easily ingest and visualize all of your security data, and with our cloud architecture, you don’t need to worry about housing and maintaining a datastore, even as your organization grows with global offices or acquisition.
The above card is a standard, important use-case to identify anomalies and trends from your firewall data. In this case, the card runs the query, “where(connection_status=DENY) groupby(source_address)” over your firewall log data.
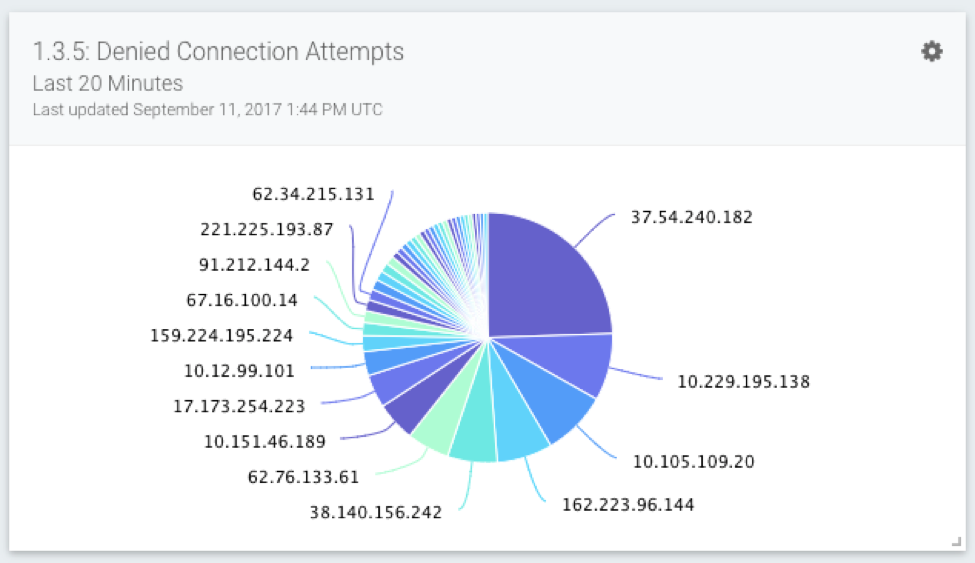
4.1c: Potential Insecure Connections
It’s important to identify traffic with destination to port 80, or the use of outdated SSL/TLS, especially for traffic around the CDE. This can help identify misconfigurations and ensure per Req 4, transmission of cardholder data is encrypted. As with all cards, you can click on the top right gear to pivot into log search, for more context around any particular IP address.
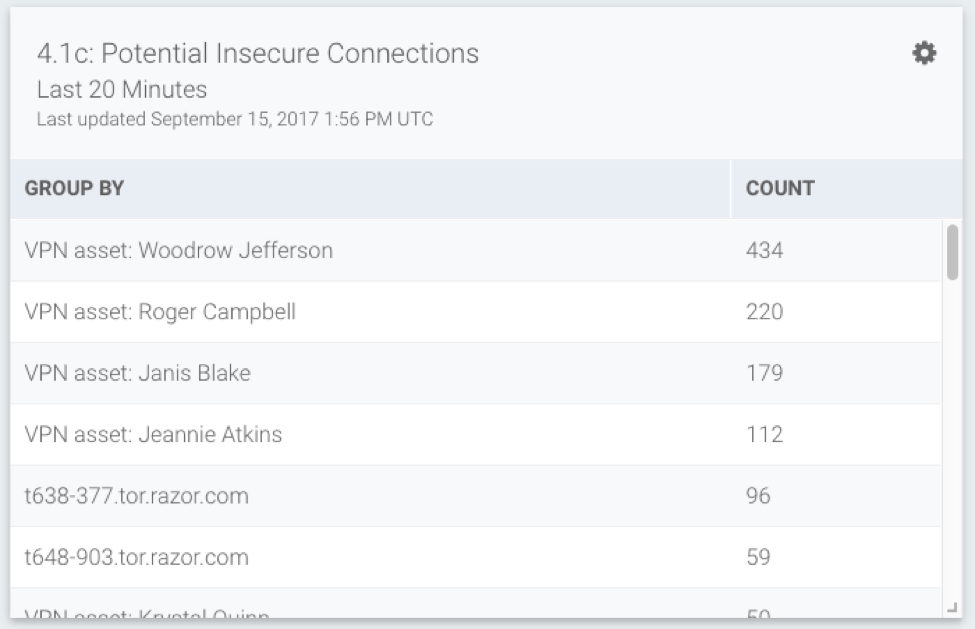
7.1.2b & 8.1.4: Users Accessing the CDE
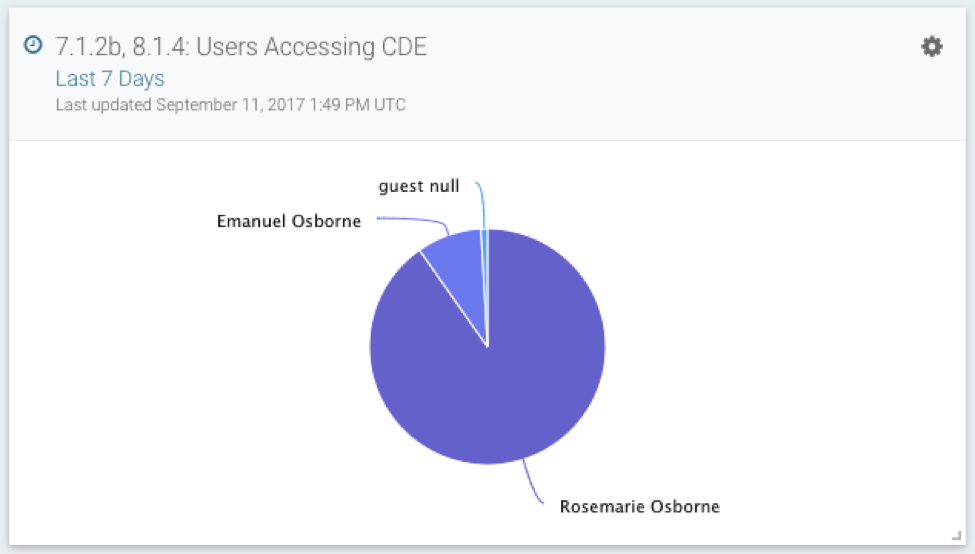
Identifying which users have accessed the PCI environment is important, as is digging a layer deeper. When did they last access the CDE, and from what asset? This is all important context used when identifying the use of compromised credentials. If the creds for Emanuel Osborne, who has access to the cardholder environment, are used to log in from a completely new asset, should your team be worried? We think so—and that’s why our pre-built detections will automatically alert you.
From this card, you can pivot to log search to identify the date of last access. On the top global search, any name can be entered to show you all of the assets where those credentials have been used (new asset logon is tracked as a notable behavior).
8.1.1: Shared/Linked Accounts in the CDE
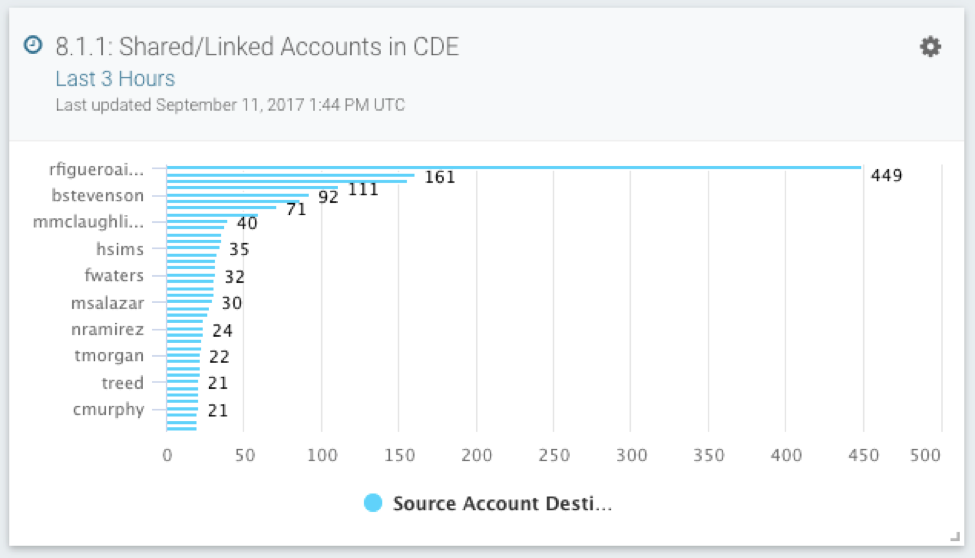
Credentials being shared by multiple people is dangerous, as it makes it much more difficult to retrace behavior and identify compromise. This card draws from asset authentication data to identify when the source account is not the destination (where(sourceaccount != destinationaccount) groupby(destinationaccount)), so your team can proactively reduce this risk, especially for the critical CDE.
8.1.3a: Monitor Deactivated Accounts
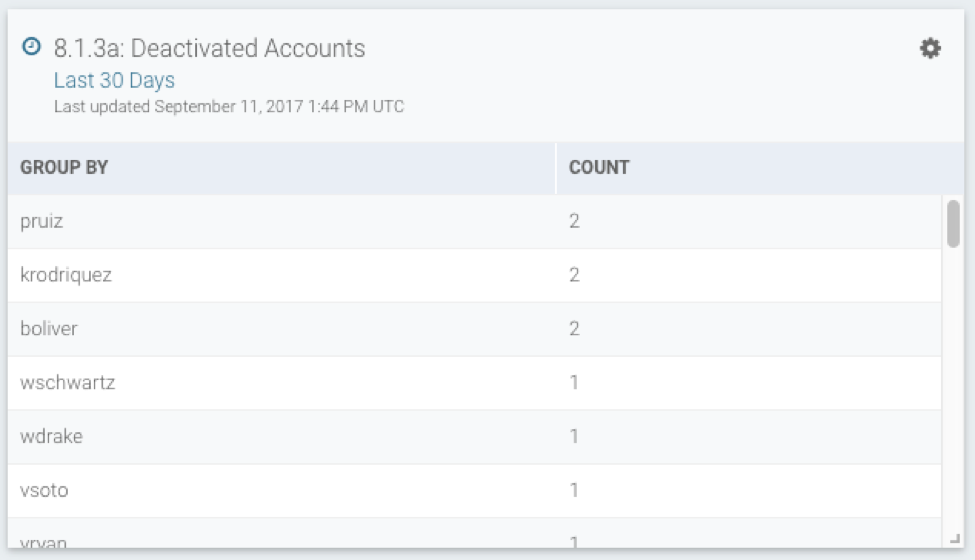
Similar to the above, it’s important to know when deactivated accounts are re-enabled and used to access the CDE—many InsightIDR alerts focus on this attack vector as we’ve found that disabled and service accounts are common targets for lateral movement.
This card highlights users with accounts deactivated over the last 30 days.
10.2.4: Highlight Relevant Log Events
10.2.5a: Track & Monitor Authentications
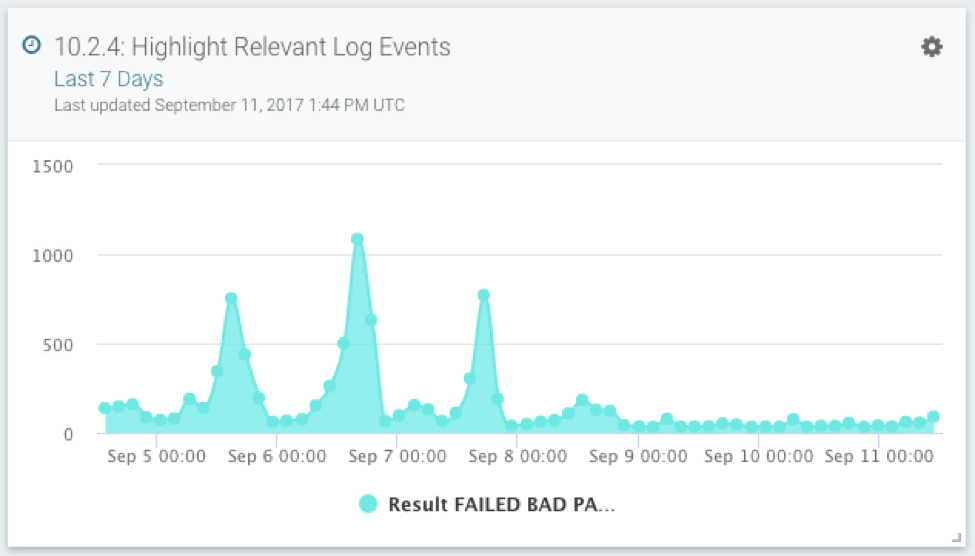
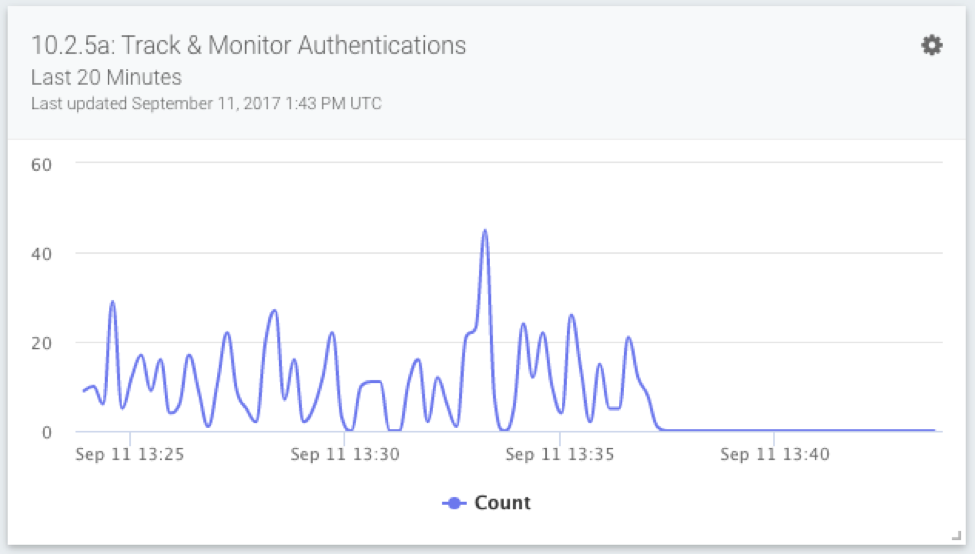
Ah, the beefy Requirement 10: track and monitor access to network resources and cardholder data. This is where InsightIDR shines. All of your disparate log data is centralized (Req. 10.2) to detect malicious behavior across the attack chain (Req. 10.6). With the standard subscription, the data is stored and fully searchable for 13 months (Req. 10.7).
These two cards highlight failed and successful authentications, so you can quickly spot anomalies and dig deeper. If you’ve been able to use InsightIDR for a few months, you already know that we’ll surface important authentication events to you in the form of alerts and notable events. These cards will ease sharing your findings and current posture outside the team.
For a comprehensive list of how InsightIDR can help you maintain PCI Compliance, check out our PCI DSS v3.2 guide.