Important update: 2018/01/25
BPC informed Rapid7 that this vulnerability only impacted the specified version of SmartVista Front-End (2.2.10, revision 287921), which had very limited distribution. Once the vulnerability described below was discovered, BPC released a patch on Jul 19, 2017, before the issuance of the public disclosure by Rapid7 on Oct 17, 2017. We have no reason to believe that any other versions of SmartVista Front-End are vulnerable to this issue. Rapid7 believed the issue to still be an outstanding vulnerability when it was disclosed and apologizes to BPC and its customers for any inconvenience caused.
Rapid7 thanks BPC for their assistance on this issue. Vulnerability reports for BPC software can now be sent to [email protected].
Original Introduction
Today we are announcing a SQL injection vulnerability discovered in BPC’s SmartVista, a suite of products related to e-commerce and other financial transaction operations. Exploiting this vulnerability requires authenticated access to the Transactions portion of SmartVista Front-End. A successful exploitation can yield sensitive data, including usernames and passwords of the database backend. This vulnerability is characterized as CWE-89 (Improper Neutralization of Special Elements used in an SQL Command).
Product Description
SmartVista is a suite of payment infrastructure and management systems created by BPC Group. A full description can be found on the vendor's website.
Credit
These issues were discovered by Rapid7 researcher Aaron Herndon, and are being disclosed in accordance with Rapid7's vulnerability disclosure policy.
Details and Exploitation
The SQL injection vulnerabilities found were specifically time-based and Boolean-based. They were discovered in the “Transactions” interface of SmartVista Front-End (SVFE), version 2.2.10, revision 287921.
Users with access to the Transactions interface (located under SVFE > Customer Service > Transactions) are provided with three input fields: “Card Number”, “Account Number”, and “Transaction Date from”. The first two input fields allow for any text to be entered, and do not sanitize user-supplied input before passing it to a database query.
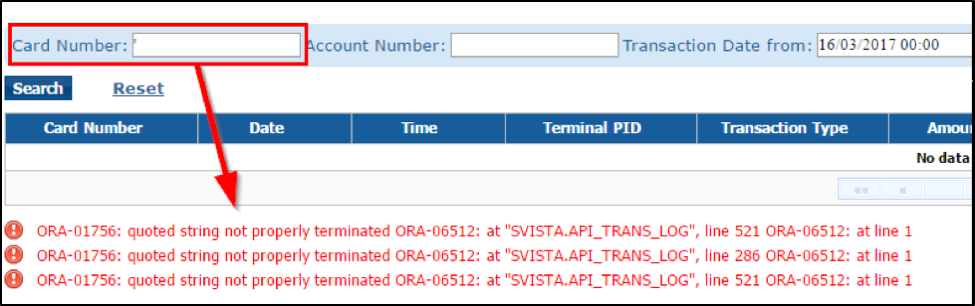
Figure 1 shows a single quotation mark input into the Card Number field, which results in a verbose database error:
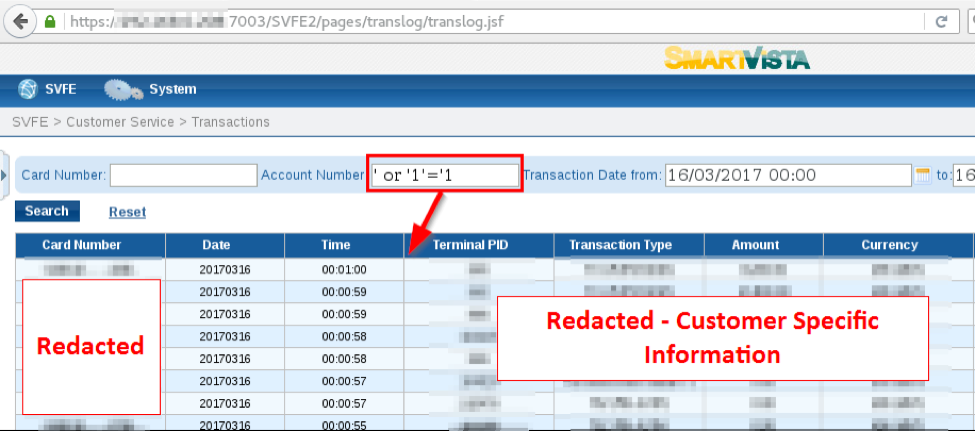
A Boolean true search term input to the Account Number field, such as ‘ or ‘1’=’1, results in a list of all transactions as shown in Figure 2:
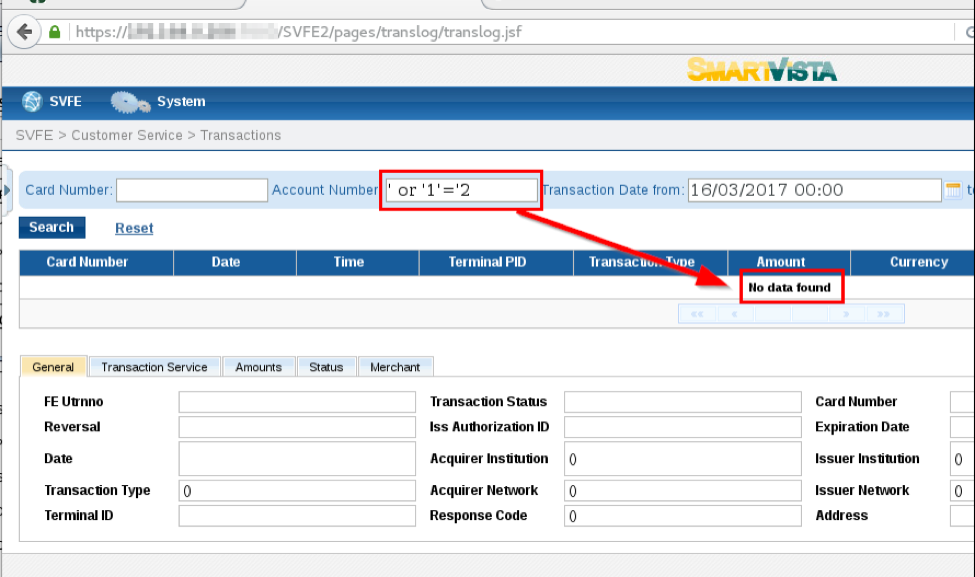
However, when a Boolean false search term, such as ‘ or ‘1’=’2, is input to the Account Number field, the application returned “No data found” as shown in Figure 3:
The Card Number field required an exact card number to provide output. Therefore, without knowing a card number beforehand, Boolean-based SQL injection was not possible through this field.
However, the database responded with a five second delay when Boolean true statements (such as ‘ or ‘1’=’1) were provided, resulting in a time-based SQL injection vector. Using these methods, it would be possible for an attacker to brute-force query the database, allowing information from accessible tables to be exposed.
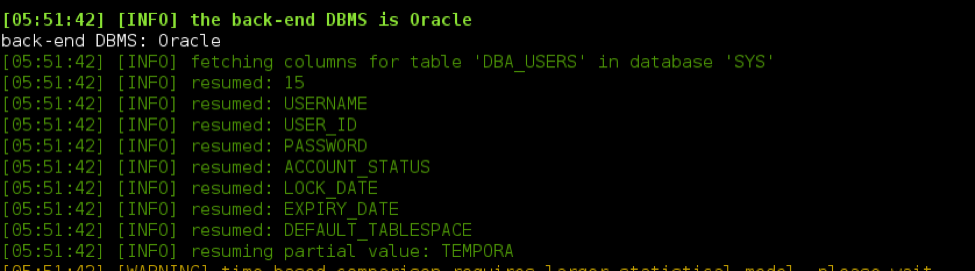
For example, to access usernames and encrypted passwords in the DBA_USERS table of database SYS (Oracle specific), one could craft a series of database queries to ask true/false statements such as “Does the first character, of the first row, in the user’s column start with ‘a’?” On a true response, the transaction values would be returned, indicating that the first character does indeed start with ‘a’. On a false reply, no data would be returned, and the automated system could move on to the next character. This could continue until the full username has been discovered, as well as the password.
As an example, Figure 4 shows the tool SQLmap being used to extract the column names for table DBA_USERS in database SYS through SQL injection in the SmartVista interface:
The specific command provided to SQLMap can be seen in Figure 5:
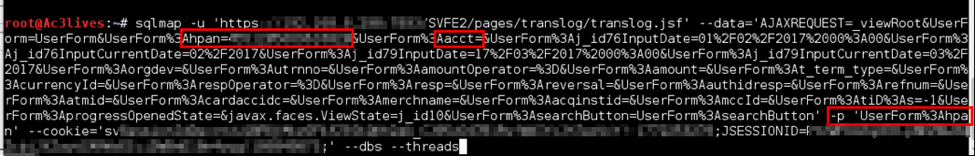
Addition details on SQLMap options:
- -u : The full URL to the vulnerable page
- --data : Structures the HTTP POST data to be send, identical to what is sent when a user clicks the ‘search’ button on the application.
- ‘hpan’ is the associated parameter with the Card Number field
- ‘acct’ is the associated parameter with the Account Number field
- -p : specifies which parameters to conduct SQL injection against
- --cookie : specifies the cookies to be used, as this vulnerability requires valid authentication as a standard user to exploit.
- --dbs: indicates to enumerate DBMS database information (can be changed to other parameters, to enumerate content from any database table).
- --threads: indicates to use threading, speeds up the extraction process
Remediation - Updated 2017/10/19
This vulnerability only impacted SmartVista Front-End version 2.2.10, revision 287921, which had very limited distribution. A patch was released on Jul 19, 2017. No other versions of SmartVista Front-End are affected.
To help limit exposure to similar issues, the following steps are advised. Access to the management interface of SmartVista should be as limited as possible, and audits of successful and failed logins should be performed regularly. A web application firewall (WAF) can help mitigate, or at least complicate, exploitation that relies on common SQL injection techniques.
Disclosure Timeline - Updated 2018/01/25
- Apr 2017: Issue discovered by Rapid7 researcher
- Wed, May 10, 2017: First attempt to contact vendor
- Mon, Jul 11, 2017: Disclosed to CERT/CC
- Wed, Jul 19, 2017: Vendor released patch
- July - Aug, 2017: Additional attempts to contact vendor by CERT/CC, SwissCERT, and Rapid7
- Wed, Oct 11, 2017: Public disclosure
- Tue, Oct 17, 2017: Response from vendor received clarifying impact version, distribution, and patch status.