INTEL-SA-00086 vulnerabilities? What’s Up?
(Full update log at the end of the post as we make changes.)
Intel decided to talk turkey this week about a cornucopia of vulnerabilities that external (i.e. non-Intel) researchers — Mark Ermolov and Maxim Goryachy from Positive Technologies Research — discovered in their chips. Yes: chips. Intel conducted a comprehensive review of their Intel® Management Engine (ME), Intel® Trusted Execution Engine (TXE), and Intel® Server Platform Services (SPS) and verified systems that run ME Firmware versions 11.0/11.5/11.6/11.7/11.10/11.20, SPS Firmware version 4.0, and TXE version 3.0 are impacted.
That impact list becomes a bit more interesting when you itemize the chips at-risk:
- 6th, 7th & 8th Generation Intel® Core™ Processor Family
- Intel® Xeon® Processor E3-1200 v5 & v6 Product Family
- Intel® Xeon® Processor Scalable Family
- Intel® Xeon® Processor W Family
- Intel® Atom® C3000 Processor Family
- Apollo Lake Intel® Atom Processor E3900 series
- Apollo Lake Intel® Pentium™
- Celeron™ N and J series Processors
There are 8 vulnerabilities identified:
- CVE-2017-5705
- CVE-2017-5706
- CVE-2017-5707
- CVE-2017-5708
- CVE-2017-5709
- CVE-2017-5710
- CVE-2017-5711
- CVE-2017-5712
Why are the INTEL-SA-00086 vulns important?
Intel’s review indicated that attackers could gain unauthorized access to systems using Intel® ME feature, and 3rd party secrets protected by the Intel® Management Engine (ME), Intel® Server Platform Service (SPS), or Intel® Trusted Execution Engine (TXE).
This includes scenarios where a successful attacker could:
- Impersonate the ME/SPS/TXE, thereby impacting local security feature attestation validity.
- Load and execute arbitrary code outside the visibility of the user and operating system.
- Cause a system crash or system instability.
A review of the CVEs can place the vulnerabilities into two camps: those impacting Intel’s “Management Engine” (ME) directly and those impacting Intel’s “Active Management Technology” (AMT) which runs on top of Intel ME.
AMT/ME are powerful components, enabling remote administration, remote display viewing/scraping, injecting human interface device (HID) events, disabling the secure boot configuration and a host of other operations that do not require the main operating system to be running or even the main system to be powered on (just plugged in).
So far, these do not appear to be trivial vulnerabilities to exploit and local system access is required for most of them. Unfortunately, remote attackers that are in the right place on poorly-designed networks may be able to access some of these Intel AMT components. If the “management” ethernet port is exposed, attackers may be able to combine older vulnerabilities along with features in the newly discovered weaknesses to access the ME/AMT components without being directly on the impacted systems.
Once attackers develop repeatable exploits, they will be able to (fairly easily) elevate privileges, run arbitrary code in a powerful context, crash your systems, eavesdrop on communications and call into question the integrity of virtually every bit of data or computation that is handled by a system that still has these vulnerabilities in place.
But, remember, there are no known, active, malicious exploits for these vulnerabilities at this time.
This means you've got time prepare your defenses and action plan.
What systems are vulnerable?
Any system using one of those chips is vulnerable, which translates to most enterprise hardware and very high-end Windows and Linux laptops. Those number in the millions.
Intel identified Lenovo as one of the first manufacturers to release fixes for these vulnerabilities but not all devices have patches available.
You will need to contact the organizations in your supply chain that provide your servers, desktops and laptops and work with them to gain an understanding of what patches are or will be available. You must stay on top of this. It is only a matter of time before there are malicious exploits in the wild for this.
So, What can I do?
Intel released a detection tool that runs on Windows and Linux systems (Apple desktops and laptops appear to be not at-risk). The tool(s) generate registry entries and/or XML files, making them very useful in orchestrating the identification of vulnerable systems.
You cannot — in any practical sense — disable the Intel ME component. While it is possible (in some systems) to do so, it requires a physical firmware flash and will ensure your devices are out of warranty afterwards.
You absolutely need to:
- use your network scanners to gain a thorough inventory of your systems. You need to scan every segment. Start working on those change control tickets now.
- run the utility Intel provided and create a comprehensive database of impacted systems
- finally create that “management network” you’ve been asking for funding for and segment off the remote management ports with a internal VPN using multi-factor authentication (or pat yourself on the back if you’ve already done that)
- watch for when your vendor(s) provide updates and patches. This may take a while since Intel just completed their review and it's a holiday week in the United States.
- once you have patches, create a schedule for rolling patch deployments and reboots
- then, create validation workflows to ensure you’ve got all your bases covered
If you have devices you can’t patch, you need to budget for new devices and allocate project time for new deployments. You cannot let systems on your network with these weaknesses in place. If you must, you need to monitor them more closely and segment them off as much as possible. Some of the segmentation techniques mentioned above may help isolate potentially impacted systems. You should also scan for open Intel ME/AMT remote management ports that are accessible outside secure management enclaved. Intel provides a handy reference for all the ports they use in this context.
This is not something you can wait to do until January 2018. You need to start operations planning now. Literally, today.
The View from Rapid7 Labs
Jon Hart from Rapid7 Labs dug into the data from our internet-scale reconnaissance. While we're still processing some of the scans performed today, here's a view of what we're seeing on the opportunistic scanning side via Heisenberg Cloud:
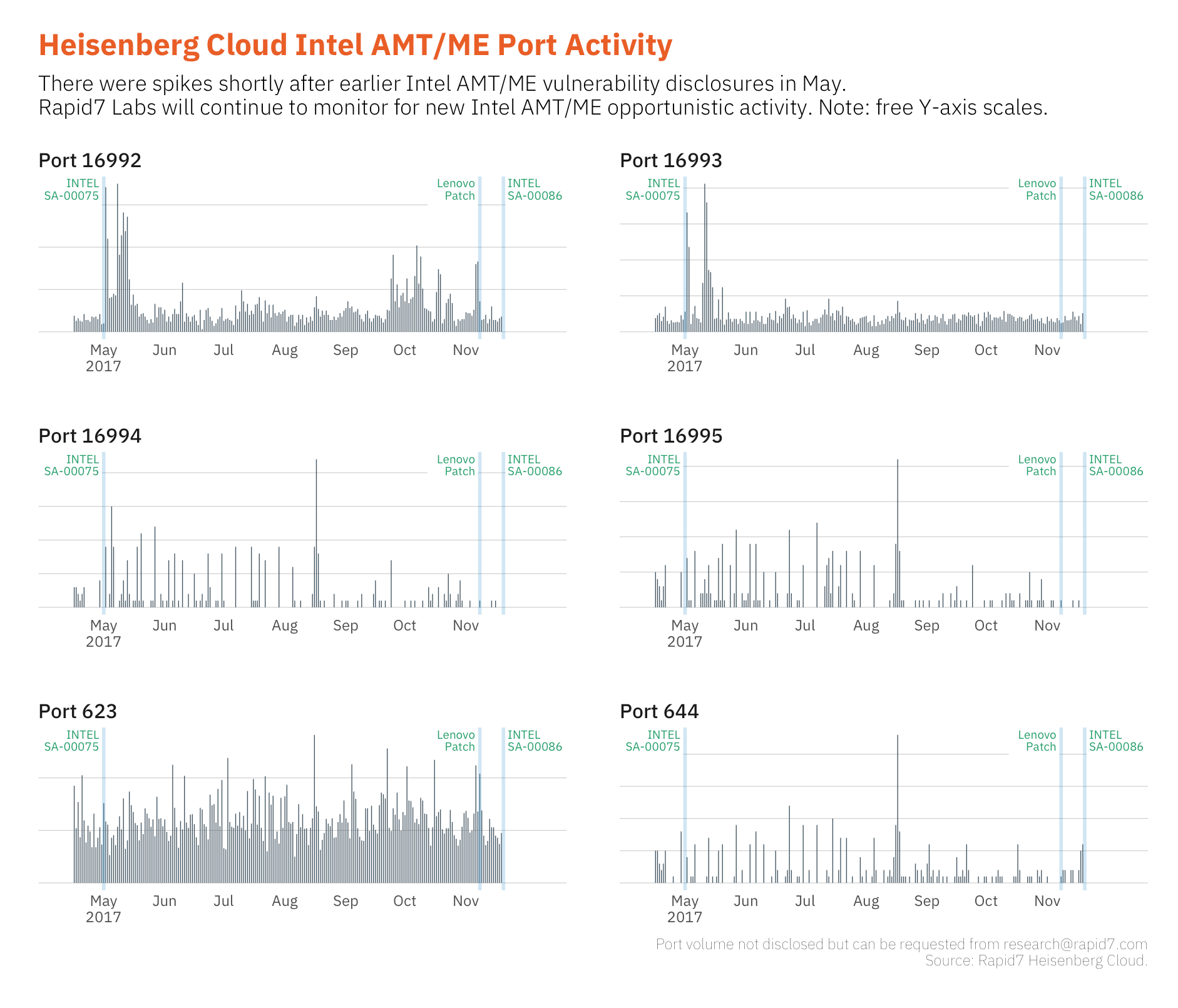
We haven't seen the same large spikes but we'll keep an eye out and update the post as things change.
These scans do find things as our scan results from an Intel AMT/ME exposure analysis on port 16992 today show:
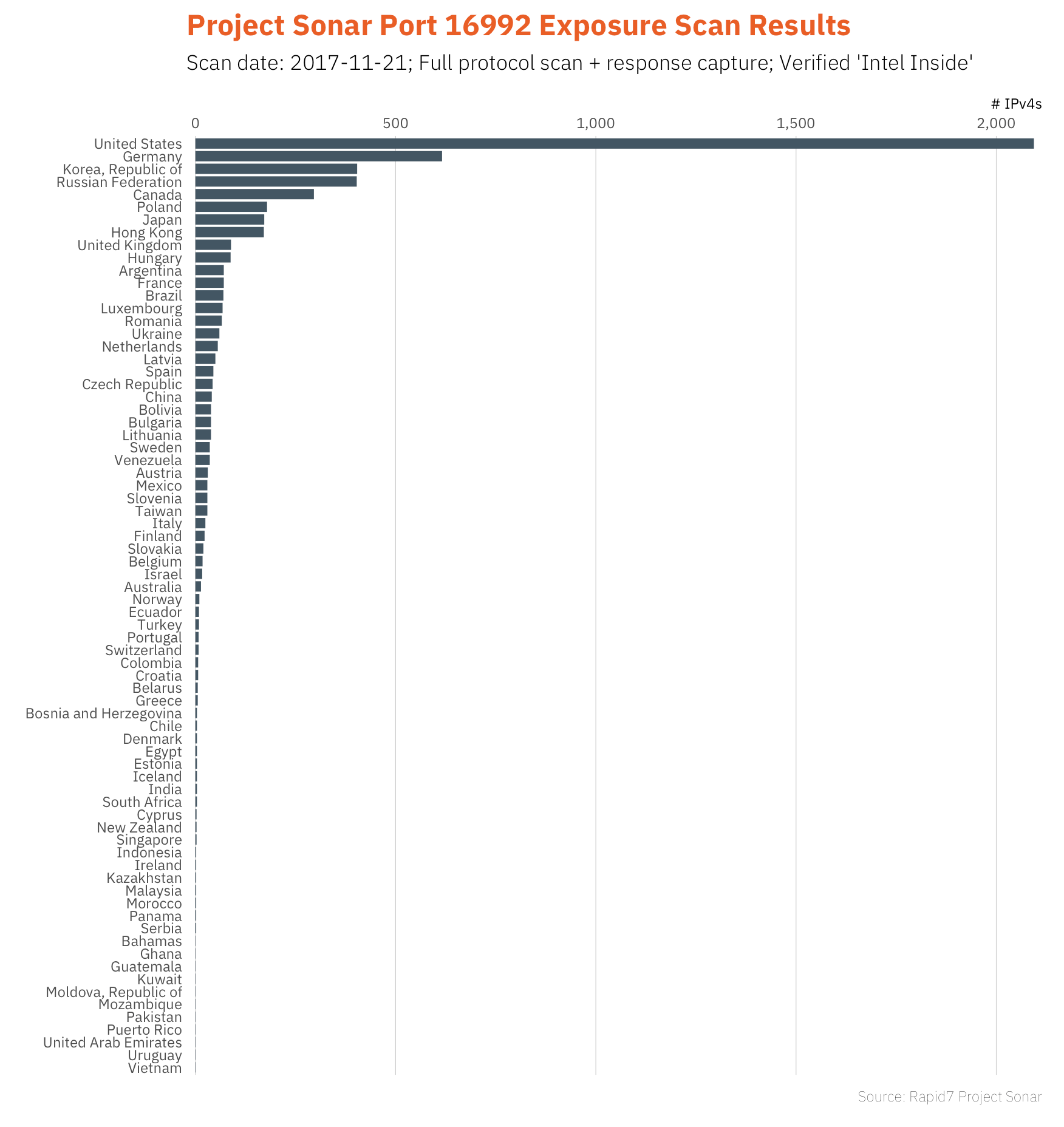
Jon found just under 6,000 devices claiming to have "Intel inside". Some of those could be honeypots but many are real systems that are completely exposed to attackers.
Stay tuned
Intel has set up a separate tracking page that will be updated as each vendor with vulnerable Intel chips inside releases patches and tools to perform said patches.
So far, Lenovo, Dell and Intel-proper have all issued guidance and/or patches.
Banner image from Vecteezy used CC-BY-ND.
Update Log
- 2017-11-21 Added Rapid7 Labs Sonar & Heisenberg Views + updated vendor patch/information availability list
