What Are SYN packets?
During a meeting with a network security specialist at a university, a network issue popped up, and he said to me, “Our firewall is triggering SYN packet alerts. Is there anything you can do to help?”
SYN packets are normally generated when a client attempts to start a TCP connection to a server, and the client and server exchange a series of messages, which normally runs like this:
- The client requests a connection by sending a SYN (synchronize) message to the server.
- The server acknowledges this request by sending SYN-ACK back to the client.
- The client responds with an ACK, and the connection is established.
This is called the TCP three-way handshake, and it’s the foundation for every connection established using the TCP protocol. In the past, attackers could bring down a firewall by sending lots of SYN packets, this is also known as a SYN flood attack. Each SYN packet would use up firewall resources and eventually, it would stop accepting new connections. This can result in a massive business problem now that so many applications are cloud-based and need fast and reliable internet access.
A SYN alert could be the sign of attacker reconnaissance
Modern firewalls are able to deal with SYN attacks better by limiting the rate of SYN requests, among other things. However, they still retain their alerting features so if something unusual is spotted, they will trigger an alarm. Not all SYN alerts are attacks designed to bring down your firewall. This was the case with the customer I mentioned earlier. In summary, they were getting a lot of connections from a host in China that was trying to find any systems running SSH services. This is very common—attackers often seek out SSH servers, and once found, they try to do a dictionary attack against the root or other accounts. If they are successful, they have full access to the LAN segment that the SSH server sits on.
How to get visibility at the network edge
If you want to see what is hitting your firewall, you need to monitor network traffic hitting the outside network interfaces. Typically this is done by setting up a SPAN or mirror port on the network switch that connects to the external interfaces.
The image below shows a typical setup. Network packets destined for the LAN or DMZ are analyzed by a traffic analysis tool connected to the network switch that connects devices together outside the LAN firewall. Most servers located here will have a public IP address and so would be open to network scanning activity. You can also detect SYN packet rates at this point to see what is hitting your main firewall.
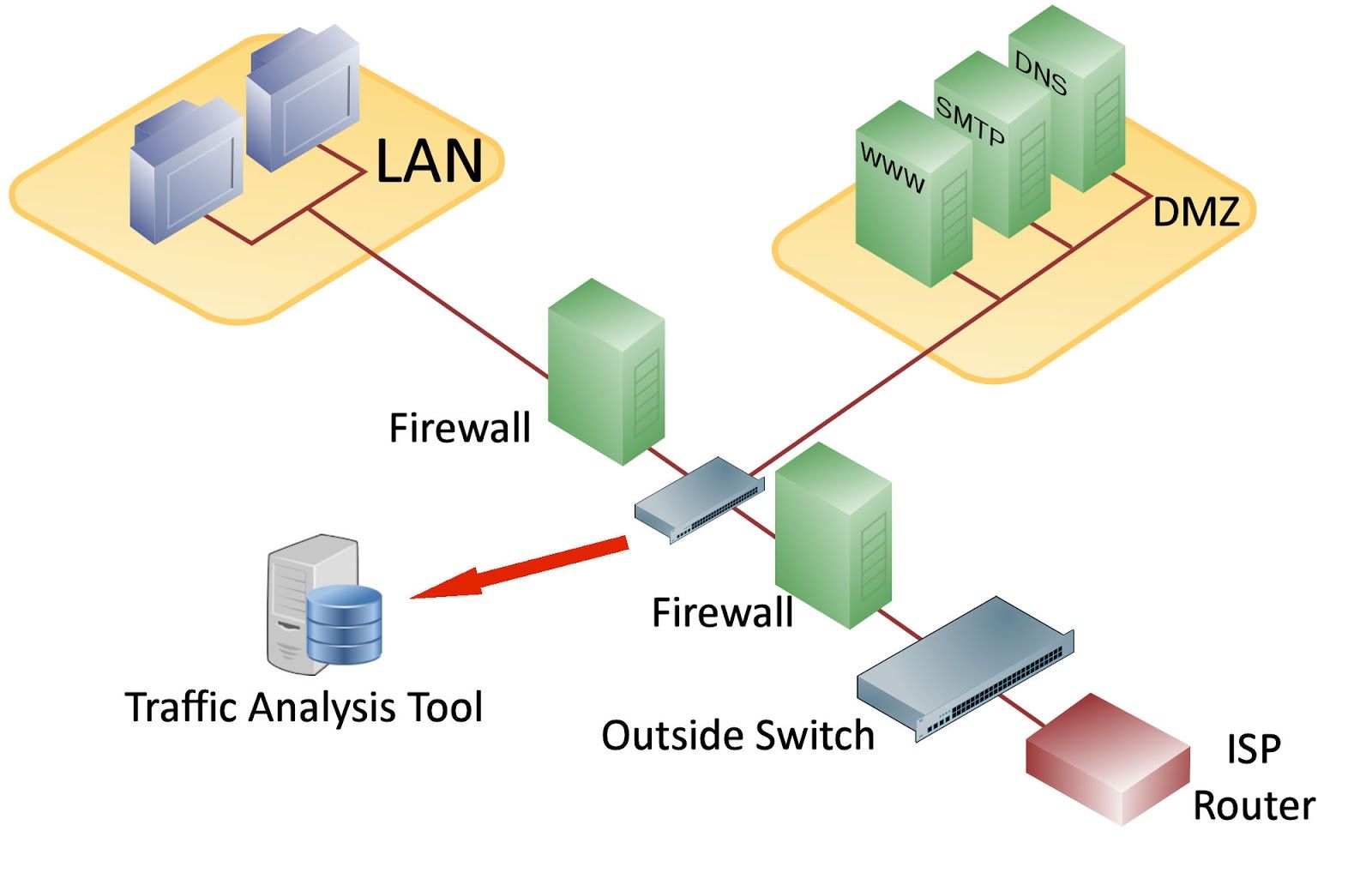
One of the main things I watch out for in the DMZ is the rate of connection attempts. This is similar to detecting SYN attacks, but as I mentioned, most of this activity is associated with reconnaissance and attackers trying to find a backdoor into your network. Some of the firewalls I looked at will trigger SYN attack alerts when they start receiving around 10,000 connection attempts per second, but this can vary.