Series co-written with Jeremiah Dewey, Rapid7 Director of Incident Response.
Part 1: Drafting the Plan
Any organization that interfaces with sensitive data needs to detect and respond to security incidents. Turning to an outside party only during a critical time of need is a risky strategy. Creating and testing an incident response (IR) plan will mitigate risk: Help your organization perform at its best by preparing it for the worst.
An incident response plan serves as your master blueprint when navigating the challenges of a serious infosec incident. In this four-part series, we’ll walk through building and testing an IR plan, sharing the lessons we’ve learned over thousands of engagements. In this post, you’ll learn all of the components that comprise an effective incident response plan.
Gather the Troops
Since every part of your organization may be impacted by a cybersecurity incident, you’ll need to involve all of the players when drafting the plan.
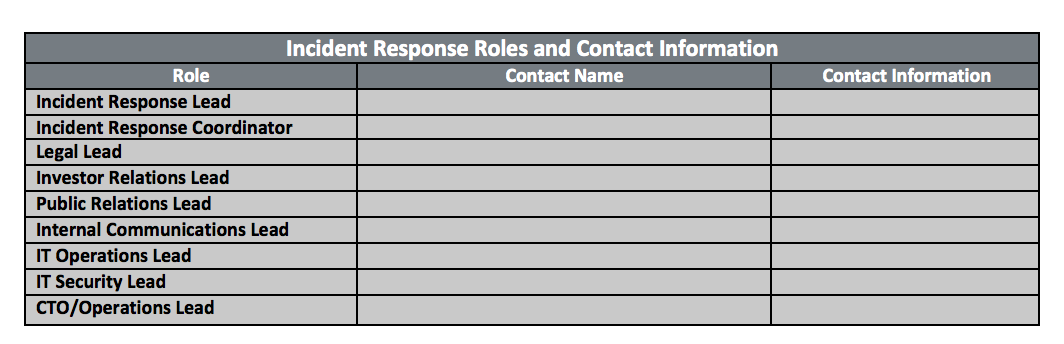
Along with the usual IT and security suspects, bring in legal and PR, as well as senior leadership. Don’t stop there—you should also include vendors such as internet service providers, outside IT firms, and any consultants who could be impacted by a cybersecurity event. This is a good time to confirm contact info and contractual agreements with your vendors. Don’t wait until an incident occurs to discover your SLAs are inadequate for a timely response!
Having all of these stakeholders on board will ensure that everyone who may be affected by a breach knows what to do and what implications may ripple outward from the IT department, including to those concerned with compliance and other regulations.
Get the Lay of the Land
Next, to get a good understanding of the assets that may be affected by a breach, map out your network infrastructure, including interconnections with other organizations.
That will give your team a clearer understanding of the present state. Attacks on networks largely take advantage of three categories: vulnerabilities, misconfigurations, and weak/stolen credentials. Taking stock of your network, including remote workers and cloud services, can help identify room for improvement, such as network segmentation or privileged access management. Remember to include assets that are owned or controlled by outside parties in addition to your corporate-owned assets.

Next, map out your prevention and detection capabilities, including any findings that were covered in past penetration tests. Bonus points if you’re already simulating attacks or internal red teaming. Tangibly showing the result of a successful attack will bridge the technical conversation usually involved with prioritizing vulnerabilities. This all helps build the business case of devoting resources to craft and test your incident detection and response plan.
Document Your Weaknesses
Now that you know what you have and what you need to protect, consider your organization’s ability to identify potential or actual compromises. Having a clear, repeatable investigation workflow means that the team can clearly determine the extent of an incident and quickly loop in the right parties.
Start by listing known limitations around isolating and remediating assets. These may include personal devices or outside vendor assets that don’t fall under the umbrella of your security infrastructure.
Then, put on that fashionable black hat (or hoodie). What are the most promising targets for an attacker? What assets and users have access to those targets—what happens if key credentials are compromised? Knowing this in advance can help you track the extent of an incursion later.
Plan for Contingency
If critical assets go down, or need to be shut down, what are the options available to maintain business continuity? Mapping out failover and backup options will help you decide how to address compromised data and systems. This is where discussion with business stakeholders in addition to IT will pay dividends.
Finally, as you are drafting your incident response plan, have your organization’s communications teams create templates for explaining the impact of escalated incidents to customers as well as to employees and need-to-know parties. Having drafts for these comms will go a long way toward calming jangled nerves both inside and outside the company.
Once you’ve drafted your incident response plan, it’s time to review it and get buy-in from all departments involved. We’ll cover this in detail in the next post, so stay tuned.
To learn how Rapid7 can help improve your detection capabilities and incident response program—or take care of the whole thing for you—explore our SIEM solution that allows you to detect and respond to attacks in-house. We also have Managed Detection and Response Services if you would like to consult with our team of highly-trained professionals.