2017 is nearly at an end, and most of the cybersecurity world is glad to see it go. We've been plagued with a myriad of vulnerabilities, misconfigurations and attacks that have kept many of us working harder than Santa's elves on December 23rd to ensure our systems and networks were not in harm's way.
The attacks may be over, but 2017 is not done "giving" just yet.
Earlier this year, the Google Chrome team announced their intent to deprecate and remove trust in Symantec-issued certificates due to a series of questionable website authentication certificates issued by their corporation’s PKI (Public Key Infrastructure). There are many sub-brands impacted by this decision, including:
- Thawte
- VeriSign
- GeoTrust
- RapidSSL
Mozilla, the makers of Firefox, have also decided to align with Google on the plan for certificate trust deprecation and removal and agreed to match whatever timetables Google decided upon.
In September, Google clarified the timeline and deprecation procedures. We’ve summarized that below:
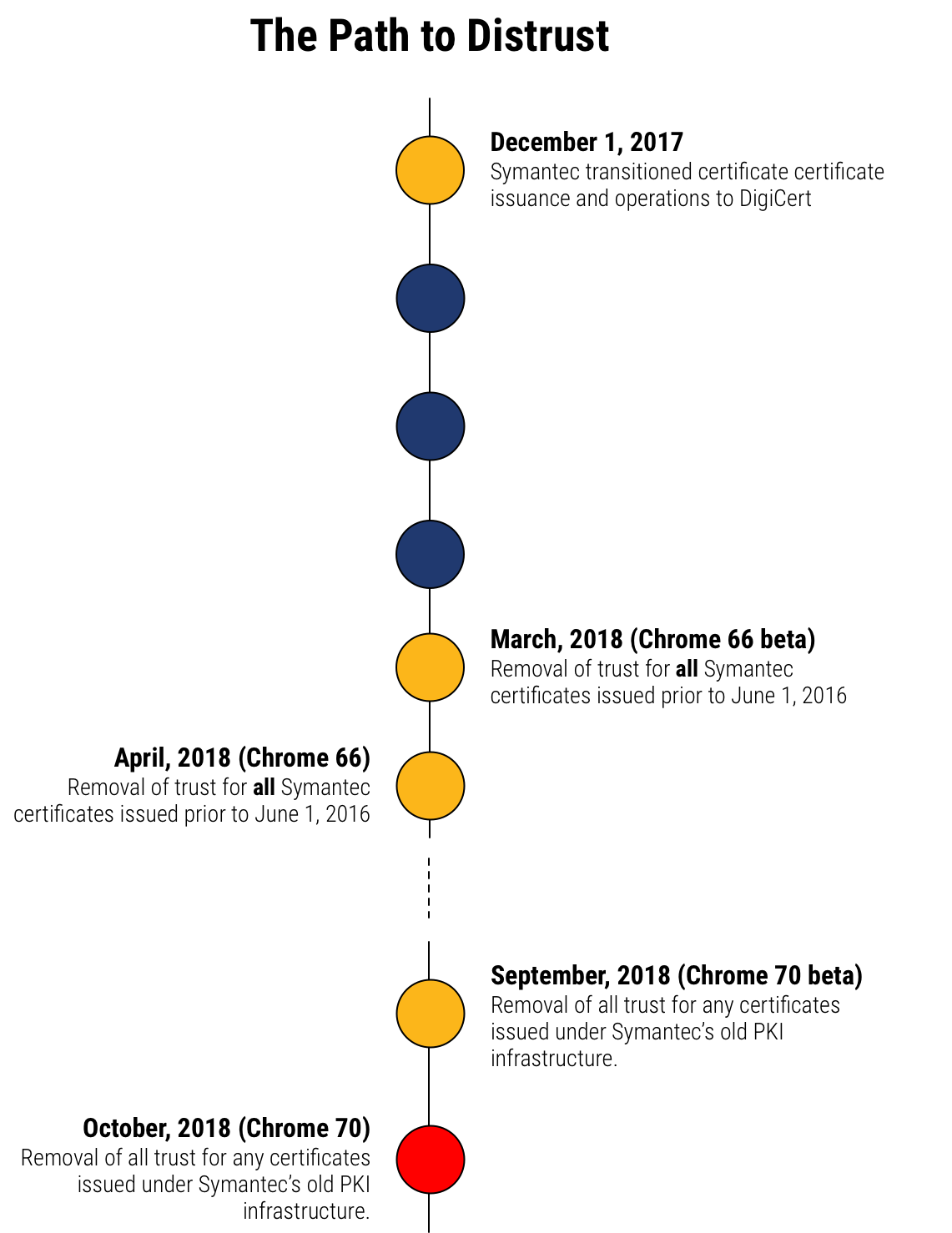
Neither Apple nor Microsoft has publicly commented on their plans.
Are Chrome and Mozilla Being Grinches?
Mozilla has a crafted a pretty thorough wiki entry on all of the issues that led up to this situation.
They aren't the only certificate authority (CA) to have problems, though:
Back in 2011, a large Dutch certificate authority, DigiNotar, ended up going out of business due to poor oversight of their PKI operations.
WoSign (a Chinese CA) and StartCom—a noted provider of free certificates—both had their certs distrusted recently as well.
When a CA is compromised or engages in activity that enables misuse of higher-level certificates it makes it possible for thieves and attackers have malicious websites, mail servers, and other internet services look legitimate and be trusted by browsers and applications. In the case of Symantec, the browser teams at both Google and Mozilla believe that the lack of care in handling certificates put users at enough risk for both deception (i.e., you think you're going to a safe site but really aren't) and information disclosure to warrant distrust.
You can read more about how certificate authorities and browsers work together over at the CA/Browser Forum.
Finding Your [Certificate] List And Checking It [Nice!]
You can get a preview of this forthcoming distrust if you point Chrome at https://stackoverflow.com. You should see something similar to:
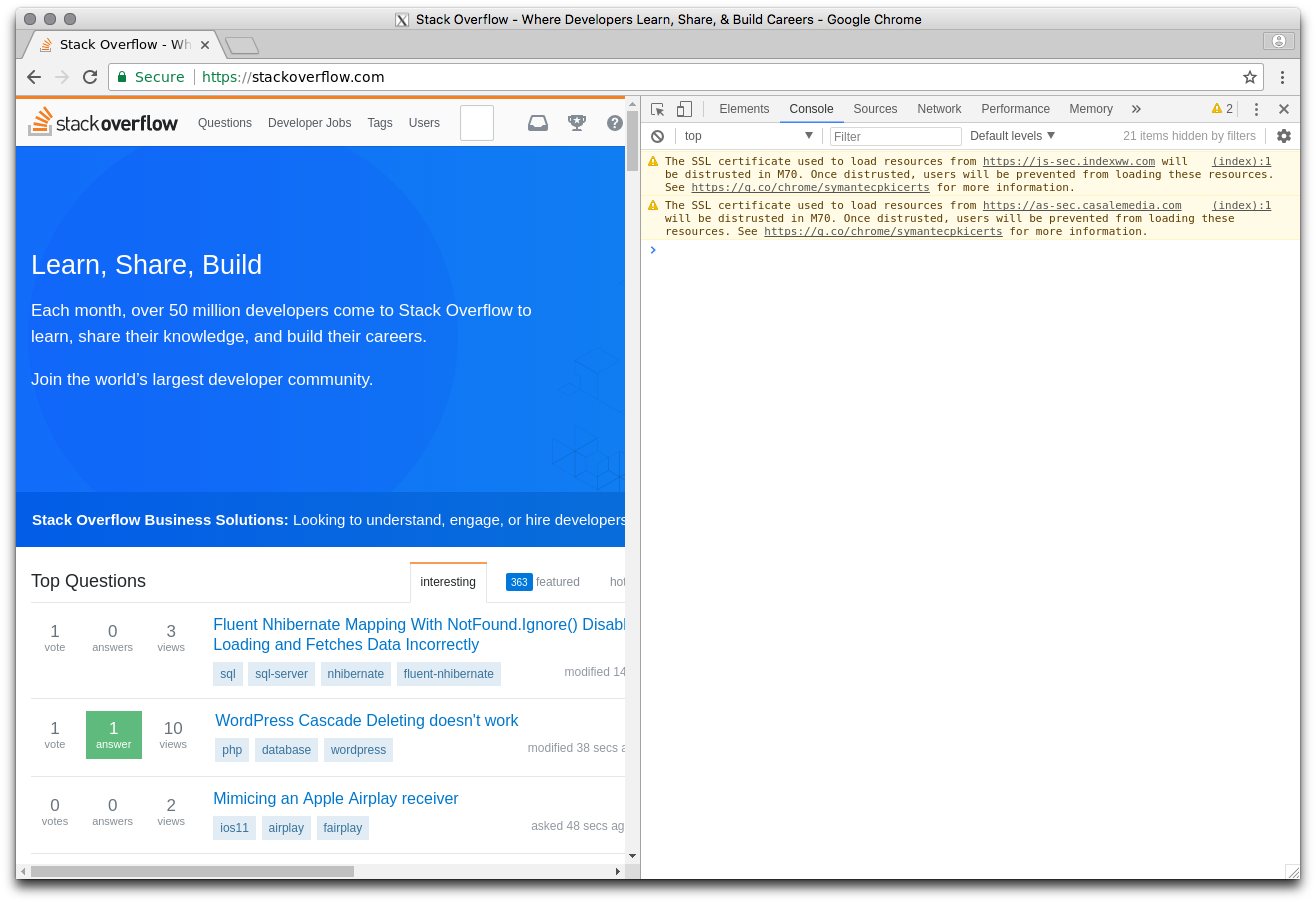
If you head on over to one of your organization's certificate-laced pages and see something similar, you've got some TODOs come 2018.
Nexpose and Metasploit both have tools to help you collect and report on certificate information on systems that you own.
A quick glance at one of our most recent Project Sonar HTTP GET scans on port 443 (SSL/TLS) shows around 250,000 already expired Symantec (et al) certificates.
Of the still "valid" ones, the vast majority have either Symantec (~4.5 million), GeoTrust (~2 million) or RapidSSL (~770 thousand) as the certificate issuer Common Name (CN).
There are nearly 525,000 certificates in danger of being fully distrusted in the March/April 2018 first cutoff round, with organizations in the United States and China leading the pack:
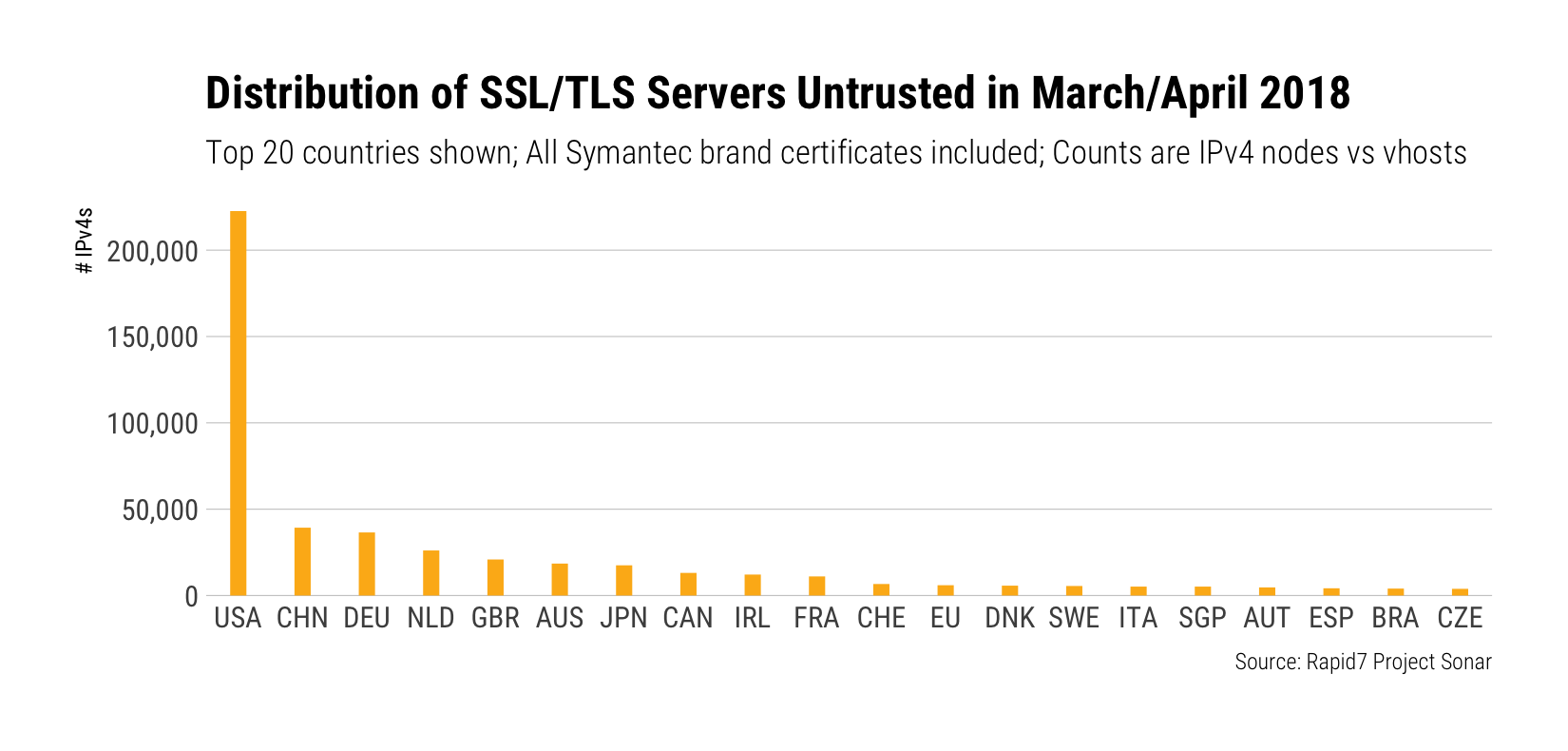
The landscape changes a little bit for the October distrust-a-palooza, but the U.S. is still in pole position:
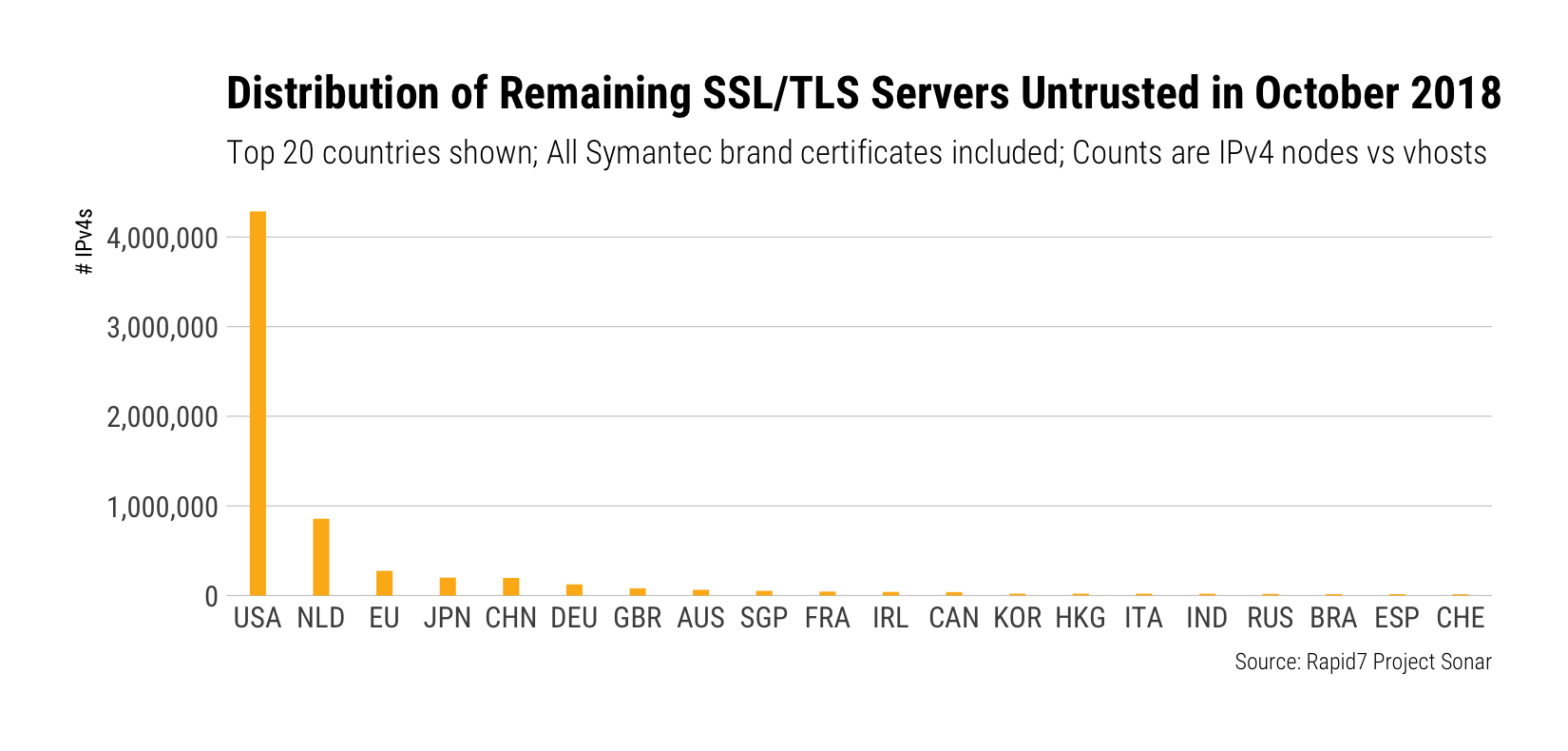
Now, we just scan on IPv4 ranges vs perform a full vhost scan so, if anything, these numbers are low estimates for the potential impact.
Expiring in the (St) Nick of Time!
On the plus side, the vast majority of the certificates we found all expire before the cutoff date:
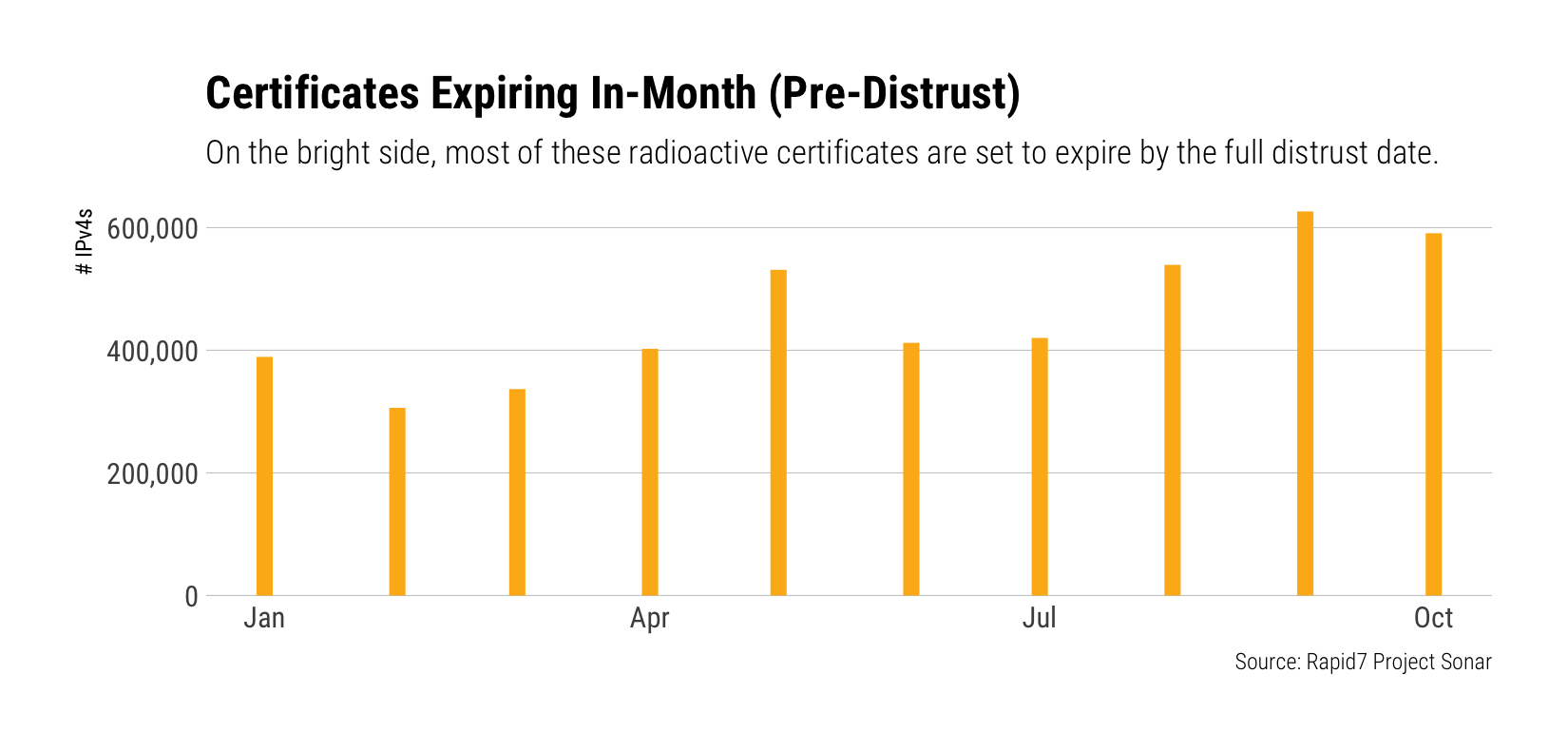
Hopefully, your organization has both a full inventory of the SSL/TLS certificates you use and where they're deployed, and a solid process for ensuring timely updates on expiration. If not, it's time to scan, catalogue, and get those processes in place well before the October deadline. NOTE: You'll need to do this internally as well since many organizations used internal certificates signed by Symantec CAs.
We'll keep monitoring as each deadline approaches and provide more snapshots on the progress organizations are making.
Now…where did I put that eggnog?
“Gift card envelopes” banner by Sarah Pflug (photo used CC-BY-SA)
![Forget The Presents: HaXmas Is All About The [Gift] Certificates](/_next/image/?url=https%3A%2F%2Fwww.rapid7.com%2Fcdn%2Fassets%2Fblt0300e8212a5a61df%2F683de28b30073ea09aeb18f6%2Fhaxmas-gift-certificates.png&w=3840&q=75)