Today’s installment of the 12 Days of HaXmas is about 2017’s 12 months of Patch Tuesdays. Never mind that there were only eleven months this year, thanks to Microsoft canceling most of February’s planned fixes. This coincided with when they’d planned to roll out their new Security Updates Guide, meant to replace the traditional MSYY-NNN bulletins.
We saw the last of those bulletins in March when MS17-006 through -023 were published. From April onwards, the vulnerability information Microsoft provided was more CVE- and KB-centric, accessible via their Security Updates Guide interface instead of the bulletins which used to aggregate CVEs by software component.
Later in this post I’ll use the CVRF data from Microsoft’s Security Update API, which was introduced alongside the Guide, to summarize the 686 vulnerabilities that were patched in Redmond this year. But first, a reminder about some of the higher-profile ones.
Notable Microsoft Vulnerabilities in 2017
Microsoft malware protection engine
Remote code execution without user interaction in a system-level process is bad news. After Project Zero published their discovery of CVE-2017-0290 in May, eleven additional CVEs followed (two of which were patched just a couple weeks ago). Thankfully, these fixes are applied automatically alongside Windows Defender malware signature updates, so most users should get patched quickly without having to take any action. Of course it never hurts to double check.
WannaCry and Petya
WannaCry… what an appropriate name 😿. So many other codenames to keep track of as well: EternalBlue is the exploit for MS17-010 (specifically CVE-2017-0144). DoublePulsar is the backdoor/implant often delivered via EternalBlue, which is used to load additional malicious code onto systems.
And there are plenty more codenames and exploits to be found in the Shadow Brokers leak these came from. The ramifications were so serious that Microsoft ended up releasing patches for operating systems that had gone out of mainstream support.
Over-the-air Vulnerabilities
A collection of various Bluetooth vulnerabilities was ~~marketed~~ published with the name BlueBorne. Only one of these, CVE-2017-8628, affects Windows systems and allows an attacker to perform a man-in-the-middle attack.
Another Name Brand™ collection of vulnerabilities that came out in 2017 was KRACK. CVE-2017-13080 is a flaw in Windows’ implementation of the WPA and WPA2 protocols that an attacker could exploit to replay broadcast and/or multicast traffic on wireless networks.
Windows Subsystem for Linux
Being able to natively run common Linux tools like sed, awk, or grep, as well as other popular Linux-first tools (Ruby, Python etc.) on Windows is great, but it does expand the attack surface of Windows 10. Three vulnerabilities were patched in 2017: two DoSes and an elevation of privilege.
IE Printer Bug
And the award for most revisions goes to… CVE-2017-8529, an information disclosure vulnerability in Internet Explorer and Edge. Microsoft patched it in June, which broke printing in IE. They released KB4032782 the next week, which fixed the printing issue, but reintroduced the vulnerability. It was finally patched properly in September. What a headache for users, administrators, and vulnerability management content authors.
CVRF Analysis
There were a fair number of complaints from people when Microsoft’s new security guide was rolled out. This was partly due to unfamiliarity with the new interface, but it also made certain workflows less efficient. One nice thing it did bring with it, though, is an API that can be queried to obtain the vulnerability data in a structured format (the Common Vulnerability Reporting Framework, available in XML or JSON flavours). At the time of writing this data goes back to April 2016, but as befits this time of year I thought I’d use it to summarize the Patch Tuesday vulnerabilities from 2017.
Month-by-month
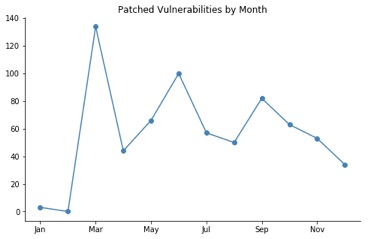
The year started off slow, with only four non-Adobe vulnerabilities patched in January and the planned Valentine’s Day Massacre being called off at the cost of a heavy March.
Wikipedia tells us, with no fewer than three citations, that “Microsoft has a pattern of releasing a larger number of updates in even-numbered months, and fewer in odd-numbered months.” This pattern did not hold in 2017. This may have been due to unplanned delays, unexpected disclosures from the NSA, or unbeknownst to us shifts in product release cadence. Regardless, it is inadvisable to base sysadmin staffing levels for Patch Tuesday on the parity of the month number.
Vulnerabilities by Component
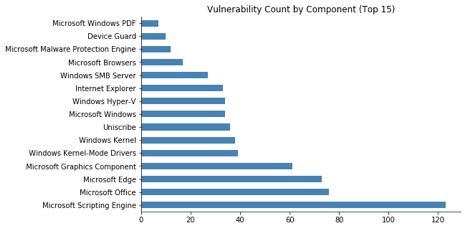
It’s clear from the chart above that web browsers represent the largest attack surface on a modern Windows system.
Vulnerabilities by Impact
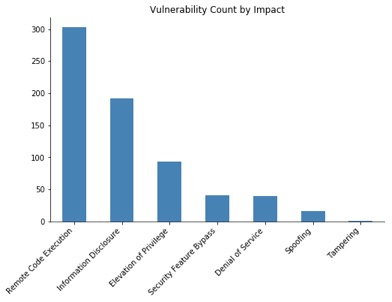
We can see here that RCE vulnerabilities are the most common, which is rather unfortunate given that they’re also the most severe.
Vulnerabilities by Severity
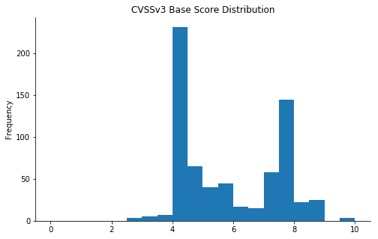
The spikes at 4 (Moderate) and 7 (High) correspond with CVSSv3’s qualitative rating scale boundaries. Thankfully there isn’t a large peak at 9 (Critical), but three vulnerabilities do have a base score of 9.8:
- CVE-2017-8589, remote code exection (RCE) in Windows Search, affecting all versions of Windows
- CVE-2017-8686, RCE that affects DHCP Servers running in failover mode
- CVE-2017-11767, RCE in ChakraCore (the scripting engine used by the Edge browser)
The vulnerabilities that caused the most havoc this year, such as those related to the Shadow Brokers leaks, hover a little lower in terms of base score. Using a single scalar value to represent something as complex as the risk represented by a software vulnerability can help with initial patch triage, but it's important to remember that the impact is very dependent on available exploits, network environments, and so on. Context matters.
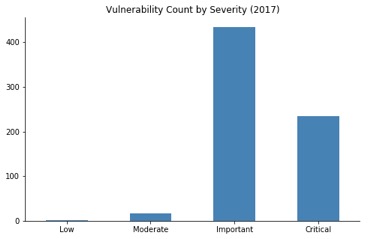
It’s also worth noting that Microsoft’s severity categories differ from the ones defined by CVSSv3. According to Microsoft a Critical vulnerability is one “whose exploitation could allow code execution without user interaction.” Over a third of the vulnerabilities patched in 2017 fell into this category:
Final Thoughts
2017 marked a major change in the way Microsoft provides information about vulnerabilities in their software. They also patched more vulnerabilities this year than in any year prior with 686 distinct CVEs addressed, up from 454 in 2016 (2015 was the previous record holder with 501 CVEs).
The above summary, although rather basic, was much easier to do thanks to the data provided by Microsoft’s new API. Previously, compiling the data would have required scraping their web pages. (They do provide Security Bulletin data in Excel and XML formats but it is not as complete or convenient as what is available from the API.)
There is also plenty of information in the API that I didn’t touch on here, such as more granular product-level detail and exploitability assessments, which could lead to some interesting analysis such as comparing the likelihood of exploitation between the latest releases of affected software and legacy versions.
The shift to the new system has had some hitches, and there can be inconsistencies in the data. The UX of the Security Update Guide also leaves something to be desired. But I expect that these issues will continue to be smoothed out in 2018 and helpful tools may spring up that take advantage of the flexibility of the API.
One thing is certain: there will still be plenty of vulnerabilities found for Microsoft to patch next year. Many of these will also affect Vista and Office 2007, both of which went out of mainstream support in 2017 and so won’t have patches available. Keep your software up to date, folks.
Get more HaXmas here.
