2017 was a trying year for information security. The Shadow Brokers brought sophisticated vulnerabilities and exploits into light with publication of alleged NSA-leaked tools and techniques. A parade of high-profile vulnerabilities graced news feeds: WannaCry, Samba, NotPetya, Apache Struts (twice). If that weren’t enough, Microsoft kicked off the year by changing how they issue security updates while AWS re:Invent attendance matched that of RSA Conference (hint: 43,000).
Sometimes, it seems change is the only permanent thing in information security. To help deal with change on your terms, we set out to help maintain visibility to your environment as it is presented to you. How? By efficiently collecting vulnerability data at scale. Here are a few examples:
Live Monitoring with Agents
Earlier in the year, InsightVM, our vulnerability management solution, added live monitoring with Agents for Windows, MacOS and major Linux distributions. Rapid7 Insight Agents conduct vulnerability assessment from within an asset. Instead of performing a full network vulnerability scan of a device, Agents collect an initial baseline and then just the changes from that baseline to understand variations in vulnerability exposure. This approach allows Agents to be lightweight, unobtrusive, and continuously vigilant. Try out Agents to collect vulnerability data from:
- Assets that are rarely or never connected to your network
- Assets that cannot or should not be scanned
- Assets in the cloud
Whether deployed across your enterprise or just on a selection of devices, Insight Agents provide visibility with a minimum of effort and administration.
Securing your modern infrastructure
While the form factor of components of your infrastructure have remained relatively stable for the past decade (think: firewalls, switches, and servers), the way your infrastructure is delivered has changed dramatically in just a few years. With public cloud infrastructure spending on the rise and set to eclipse on-premise spending by 2020, the trend is clear: your investments in infrastructure are likely to include cloud infrastructure and the technologies that go along with it.
For security teams, this turn of events presents yet another new technology to secure. Fear not: throughout 2017, Rapid7 has consistently invested in vulnerability management for your modern infrastructure.
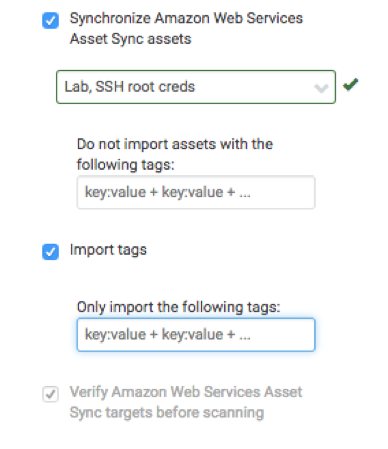
InsightVM provides unique ways to maintain visibility to risk in your cloud infrastructure. With easy-to-configure discovery connections for Microsoft Azure and Amazon Web Services, you can:
- Discover assets as they appear
- Synchronize asset tags for simpler reporting
- Automatically remove assets as they are destroyed
Once you have visibility to assets, use automated actions in InsightVM to eliminate manual effort: set up discovery connections to trigger automated assessment while the asset exists.
To simplify deployment of InsightVM within your infrastructure Rapid7 offers pre-built Scan Engines and Security Consoles within the AWS Marketplace and Azure Marketplace.
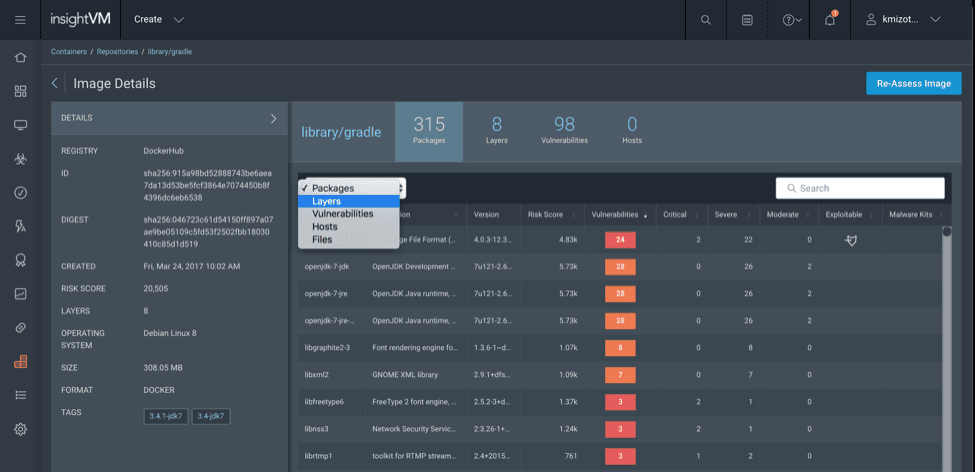
Container security
As DevOps continues to grow as a discipline, container technology like Docker has risen as a tool of choice for new application workloads. As an enabling technology in the DevOps toolchain, containers make it simpler to build, deploy and maintain applications.
While DevOps teams are often tasked with incorporating security measures for their own applications, there may be many DevOps teams advised and supported by Security. Each DevOps team may opt for a different tool, making obtaining a single view of your risk challenging to say the least.
For security teams, containers present—you guessed it—yet another new technology to secure. Consider the following questions:
- Do you know where containers are deployed in your environment?
- Do you know what containers are deployed in your environment?
- Do you know the risk associated with containers deployed in your environment?
In order to answer these questions, you need to be able to collect security data from your container environments. InsightVM gives you the ability to secure your containers with:
- Discovery: Identify container hosts in your environment and container images deployed
- Assessment: Understand vulnerabilities associated with a specific container image and secure configuration of the host.
- Automation: Automatically assess container images where they live, in public or private registries.
Learn more about how InsightVM can help you secure your containers.

Interested in learning more about the only solution in the market offering this combination of capabilities in 2017? For more detailed information on using these capabilities in InsightVM, see our help page. And of course, if you haven’t done so already, get a trial of InsightVM today and start collecting!