This post was co-written with Wade Woolwine, Rapid7 Director of Managed Services.
What three categories do attackers exploit to get on your corporate network? Vulnerabilities, misconfigurations, and credentials. Whether the attack starts by stealing cloud service credentials, or exploiting a vulnerability on a misconfigured, internet-facing asset, compromising an internal asset is a great milestone for an intruder.
Once an endpoint is compromised, the attacker can:
- Access sensitive data available to that asset.
- Eavesdrop on network traffic, steal credentials from memory, and even abuse trusted communication protocols (e.g., with the [popular tool Responder).
- Attempt lateral movement to other, more privileged assets on the network.
For this reason, when investing in the technology that supports Rapid7’s Managed Detection and Response (MDR) service, we prioritized the native collection of endpoint data, specifically over layering advanced analytics to network data (e.g., netflow, full packet capture).
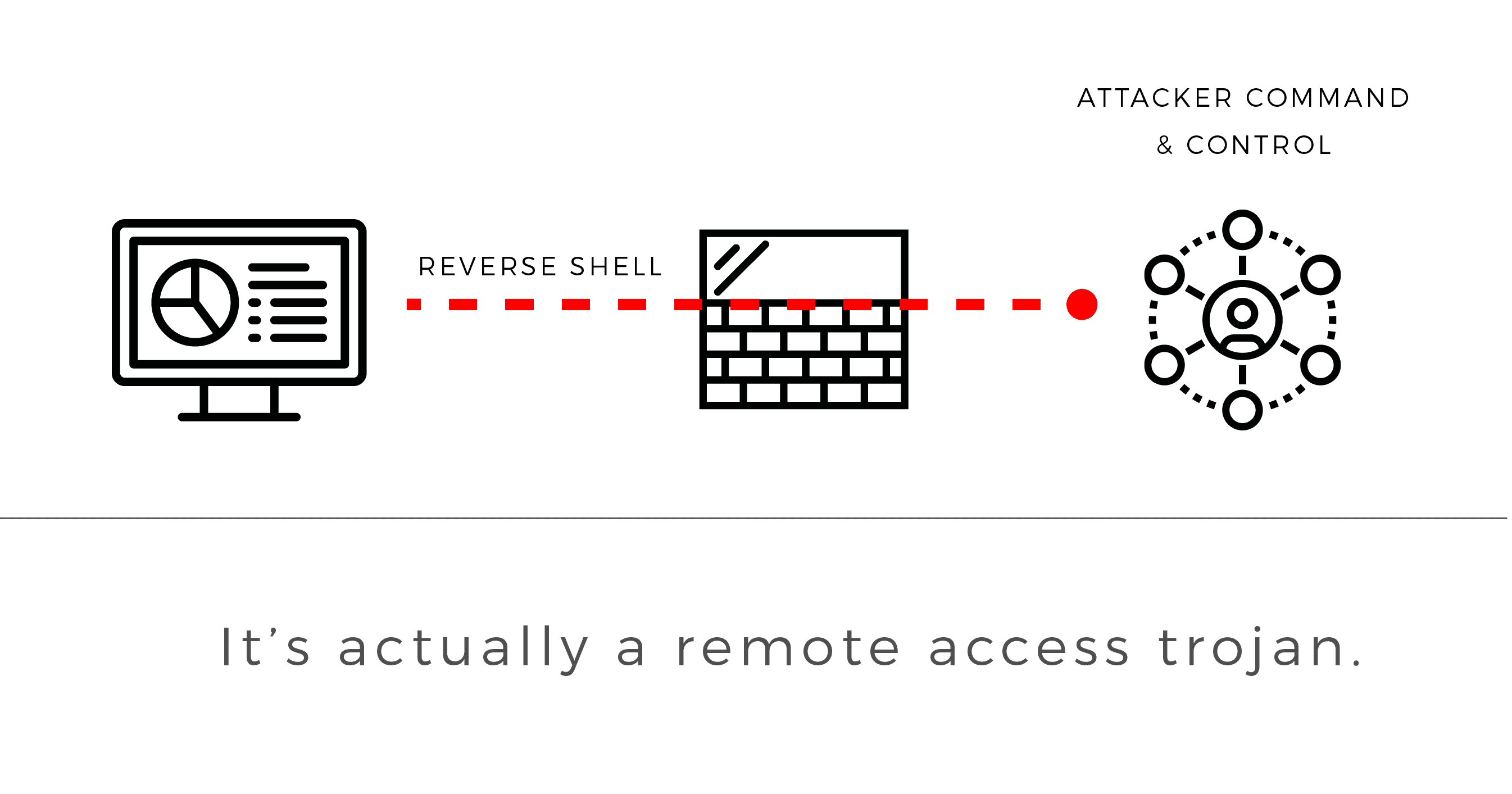
In this post, we’d like to share the benefits of this approach. Let’s walk through a simple malware attack that allows the intruder to communicate with the endpoint over encrypted channels.
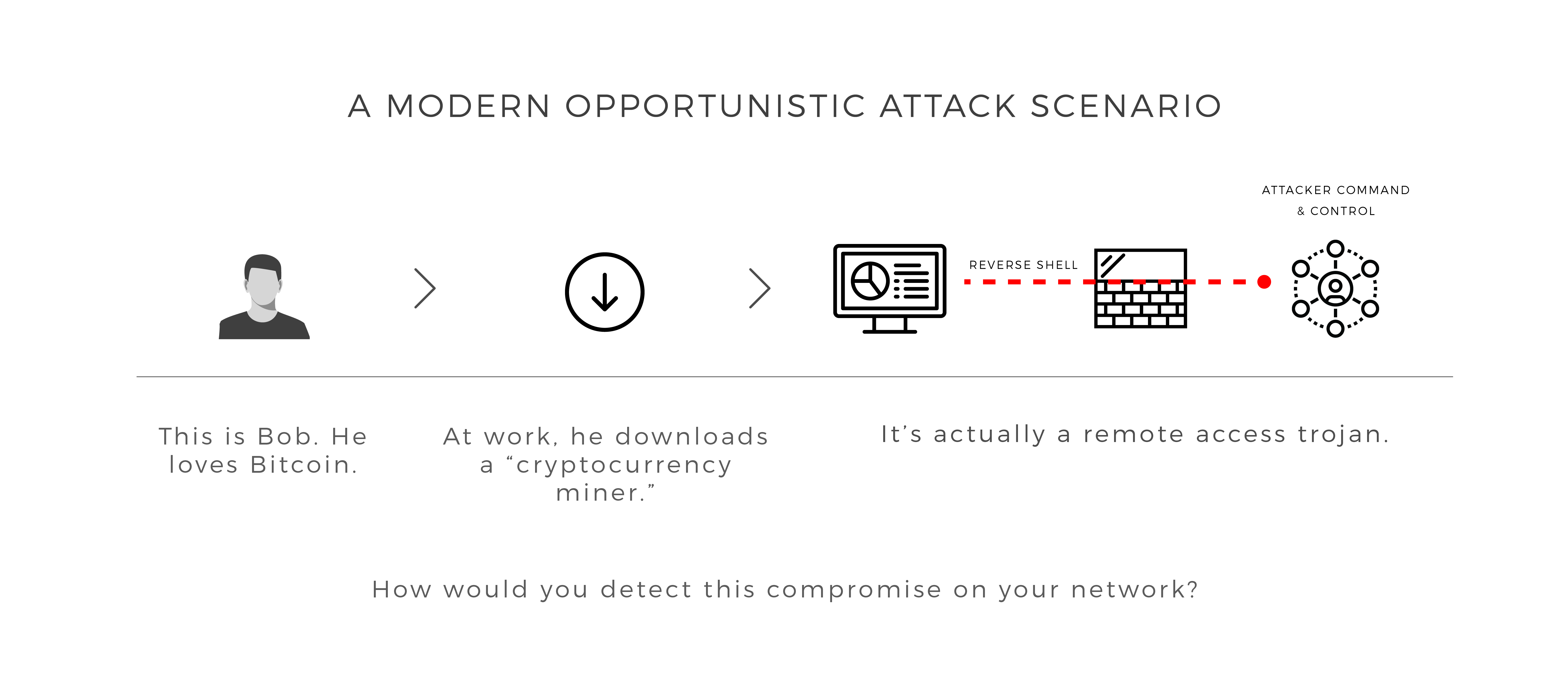
“Bob in marketing has been an avid fan of Bitcoin since buying some at $18,000. As the price plummets, he grows increasingly uneasy, looking for a side hustle to supplement his losing investment. On his work asset, he downloads a “cryptocurrency miner,” which allows his computer to contribute computational power in exchange for payment in a digital asset. Unbeknownst to him, this is no miner, but a trojan that provides an attacker remote access to the now compromised endpoint…”
While this scenario is tongue-in-cheek, opportunistic compromise is very real, given the recent wave of malicious browser extensions, more Adobe Flash 0-Days, and supply chain attacks on trusted, beloved software like CCleaner.
From a network analysis perspective, our hypothetical heroes have only a few opportunities to catch the attack:
- Have existing threat intelligence that flags a known Command & Control IP or domain.
- Flag anomalous parameters used to establish the encrypted session.
- Identify anomalous network traffic volume from the compromised asset to the attacker’s IP address.
If Bob works remotely or is frequently on the road, detection increasingly relies on faithful usage of VPN services. This is because network monitoring usually takes the form of appliances that connect into on-premise network infrastructure.
With our MDR service, it’s a different story. By collecting and analyzing the right types of endpoint data, our team has multiple ways to catch the attack. Our Insight Agent securely streams endpoint data to our Insight platform to run computationally demanding analytics. Close attention to running processes (especially parent-child relationships) and anomalous behavior on the asset opens up not only better detection, but faster, more thorough incident investigations.
Here’s how different types of endpoint data reveals both opportunistic and targeted attacks:
-
Malware installation: there are differences in the way that malware is installed vs. normal software.
Example: Command line activity spawning from Excel. -
Malware persistence: there are only a finite number of ways that malware can persist on a system.
Example: Registry keys modified to maintain persistence. -
Attacker issues commands: attackers tend to interface with a target system using the OS terminal.
Example: Encoded commands passed to PowerShell. -
Attacker steals credentials: prior to lateral movement, the attacker will need credentials.
Example: The command line OR binary metadata contains MimiKatz. -
Attacker downloads additional tools: attackers typically bring a toolkit with them.
Example: HTML Applications (mshta.exe) can bypass Application Whitelisting and execute malicious code. -
Attacker moves laterally to other assets.
Context: Endpoint logs, Active Directory, and LDAP each only have a slice of the authentication story. This is why we ingest all three, and then baseline employee activity with our User Behavior Analytics core.
While our MDR team monitors for all of the above, we don’t start and end with the endpoint. Our veteran analysts use Rapid7 InsightIDR, our SIEM solution that comprehensively integrates with your security and network stack.
Managed detection and response services that only sensor the endpoint will not only miss attacks, but they’ll lack context on “who does what” in the company. Unlike your internal team, third-party analysts don't know who's regularly on the road, or who requires anomalous privileges for their job. For example, I have to expose myself to interesting extensions when delivering webcasts with third-party providers. I would not be happy if my asset was “contained” mid-demo...
For that reason, we pair your team with an assigned Customer Advisor, who will promptly notify you of findings—but only for the true items that require investigation. Our job is to tell you exactly what happened, and that includes:
- How did the attacker get in?
- What tools did the attacker use?
- Where did the attacker move to?
- What credentials were used?
- What data did the attacker have access to?
- What data was stolen?
- Is the attacker still in the environment?
- What specific steps can you take to remediate?
- What can you do to prevent these kinds of attacks from happening in the future?
While some of the above can be answered with network data, thoughtful endpoint data collection captures authentication, file system, process execution, and forensic artifacts critical across the entire incident response lifecycle.