There are a lot of fixes this month: Microsoft's updates include patches for 76 separate vulnerabilities, including two critical Adobe Flash Player remote code execution (RCE) vulnerabilities.
In fact all of this month's critical vulnerabilities are browser-related. This is not surprising considering web browsers are a major attack surface on modern Windows workstations, and are an obvious vector for malicious code. Even so, with the sheer volume of vulnerabilities patched this month there's still plenty to worry about as far as other Windows and Office products go. Server administrators in particular should note the many privilege escalation vulnerabilities being fixed in SharePoint Server. Exchange Server is also getting fixes for privilege escalation and information disclosure bugs.
Back on the client side, there are a few other nasty ones to look out for. CVE-2018-0883 (Windows Shell) and CVE-2018-0903 (Microsoft Access) are both RCE vulnerabilities that simply require a user to open a maliciously crafted file. CVE-2018-0907 is a security feature bypass where Excel fails to enforce macro settings on certain documents. This doesn't allow RCE on its own, but could be used in conjunction with other flaws to develop more reliable exploits. This is especially true of the many kernel information disclosure vulnerabilities patched this month, which can help attackers bypass Address Space Layout Randomization protections.
One important note regarding CVE-2018-0886, a flaw in the way the Credential Security Support Provider protocol (CredSSP) validates certain requests that could lead to remote code execution. A simple software update is not sufficient to protect against this. In order to avoid introducing connectivity problems, a Group Policy setting (or registry-based equivalent) must also be applied and the machine rebooted to actually mitigate the issue. Complete instructions are available here.
Lastly, Microsoft has been keeping a steady pace of revisions and updates related to the infamous Spectre and Meltdown vulnerabilities. This month finally sees them release mitigations for Windows Server 2008 and Server 2012, as well as additional Meltdown protections for the 32-bit editions of Windows 7 and Windows 8.1.
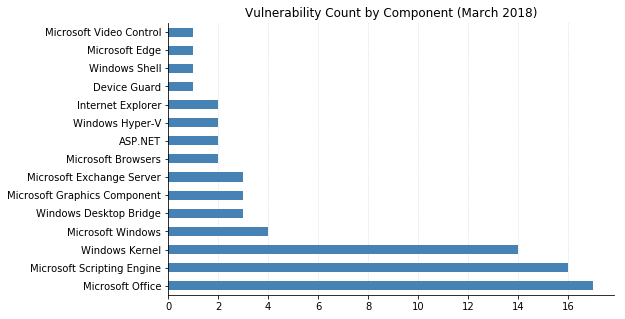
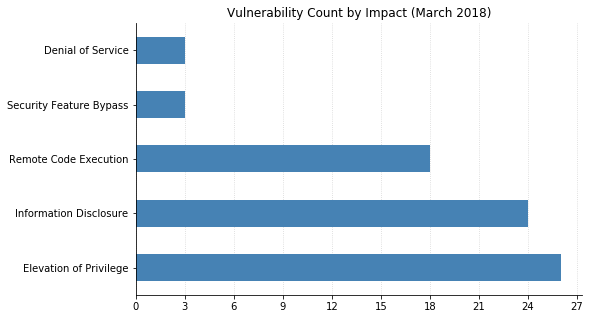
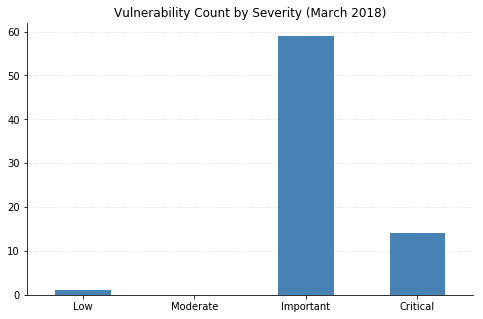
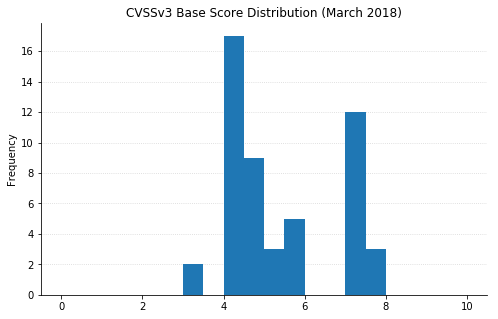
(Note: Not all CVEs had CVSSv3 data available at the time of writing.)
