Welcome to Rapid7’s Q4 report, featuring our first annual threat report wrap-up!
2017 Quarterly Threat Report: Q4 and 2017 Wrap-Up
Get the Full ReportWe could not have picked a better year to start doing this, as 2017 was one for the books. While we spent most of the year falling headfirst into a world where nation-state tools are available for anyone to use, the worm re-emerged (now evolved as a ransomworm), vulnerabilities were exploited more quickly, those exploits were added to exploit kits faster, and critical infrastructure received its fair share of attention from adversaries. It was not just a year for attackers, however. Defenders upped their game as well, and we saw new ways to detect malicious behaviors, new levels of rapid triage and information sharing, and new ways to reach out and inform end users of the threats facing them. While there is no doubt that adversaries will continue to challenge us in 2018, defenders are well poised to learn from and adapt to those challenges.
In our annual wrap-up, we cover some of the trends we identified throughout the year. The top pattern we saw was consistent malicious activity during weekdays and business hours of the targeted organizations. This speaks to how professionalized network intrusions have become, as well as how adversaries continue to rely on interaction from users to enable their attacks.
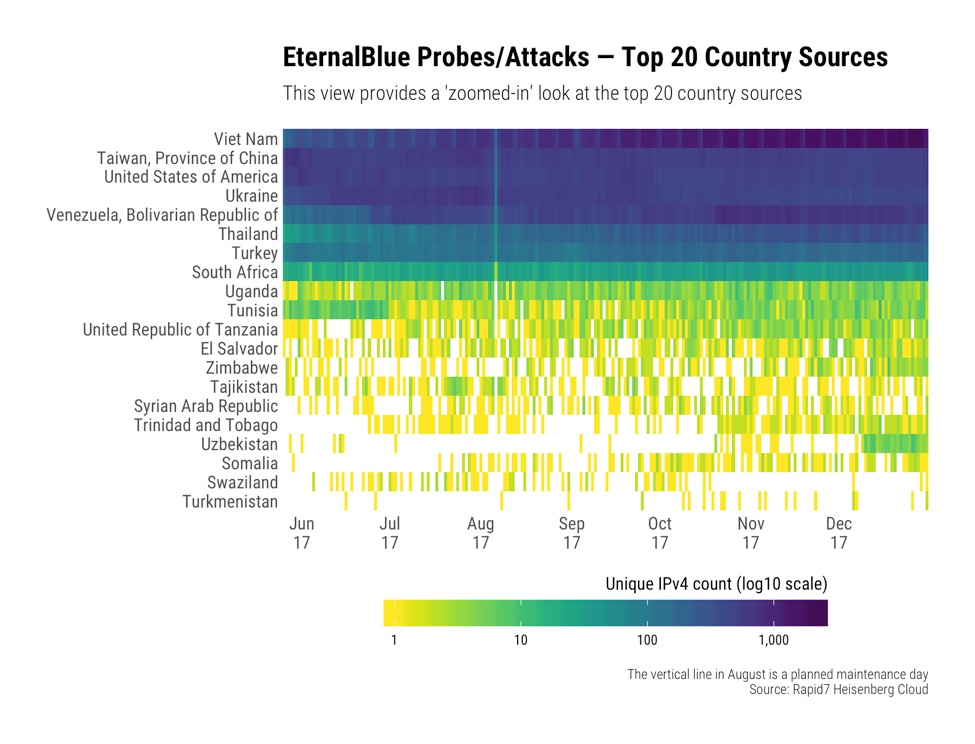
While some things stay the same, many things changed: we saw a drastic change mid-year in initial attack vectors. For the first few months of 2017, there was a lot of shuffling among the top attack vectors, but by mid-year, remote access became the consistent number one attack vector. This directly correlates to the Shadow Brokers leaks in late April, which saw the release of multiple remote access tools that targeted protocols and systems many organizations seemed to have forgotten. We have been interested in the way that these tools were being used since they were first leaked, and we have been collecting data since shortly after they were released. This iteration of the threat report provides a deep-dive on EternalBlue—the exploit that changed the ambient noise level of the internet.
We also saw a change in industry targeting. While the financial sector continues to see a large amount of malicious activity directed their way, both in volume and in variety, we saw a marked increase in activity directed against the real estate and construction verticals. These sectors also deal with financial data, though often in different ways than we see with the financial sector.
Critical infrastructure has seen its fair share of threats this past year, too; the threat alert released by DHS last week came out in 2018, but it detailed activity that has been ongoing for the past several years. While the threats against critical infrastructure range from opportunist activity against systems with accidental exposure or misconfigurations to years-long campaigns run by dedicated and capable adversaries, 2017 changed our view of what is at stake and how we can protect the systems we rely on.
Regardless of your industry or your defensive capabilities, 2017 was full of lessons about adversaries and their intent, their capabilities and opportunities, and (perhaps most importantly) how we can defend against them.

