Over 70 vulnerabilities have been fixed this month, including 6 in Adobe Flash (APSB18-08).
At a high level, there's nothing too out of the ordinary. Unfortunately, that means the majority of the patched vulnerabilities are once again of the worst variety: Remote Code Execution (RCE). Web browsers (IE and Edge) are seeing most of the fixes, which is also par for the course. None of this month's vulnerabilities have been seen exploited in the wild, although CVE-2018-1034 (a Microsoft SharePoint Server privilege escalation bug) was publicly disclosed. Several Microsoft Office issues have been patched, many of which also affect SharePoint Server. Also of note to backend administrators are two Denial of Service (DoS) vulnerabilities: CVE-2018-0956 and CVE-2018-0967, in HTTP.sys and the SNMP Service respectively. Several Kernel information disclosure bugs were fixed, which can be useful for attackers wishing to craft more reliable exploits by bypassing Address Space Layout Randomization protections.
The ongoing Spectre/Meltdown saga continues to illustrate the complexity involved with trying to work around hardware vulnerabilities via software. Microsoft has issued yet another Spectre patch today: KB4093112 mitigates CVE-2017-5715 for Windows 10 version 1709 systems running on AMD processors. By default, applying this update will only protect against some attack scenarios. To prevent a malicious application run in user mode from being able to disclose the contents of kernel memory (user-to-kernel), the Indirect Branch Prediction Barrier must be enabled by adding certain registry keys and restarting. This may negatively impact system performance, which is why it is not automatically enabled. Process-to-process and virtualized guest-to-host mitigations are enabled by default.
And in case you missed it: the original Meltdown fix for Windows 7 and Server 2008 R2 in January actually introduced a new, even more severe vulnerability that was quietly patched as part of the March updates. It was made public as Total Meltdown on March 27, after which the March fix was found to be incomplete. This led Microsoft to release an out-of-band update on March 29 for CVE-2018-1038. This patch should be applied immediately if you have any affected systems in your environment.
Another update that may have slipped under the radar when the fix came out last week was for the latest RCE vulnerability in Microsoft's Malware Protection Engine, CVE-2018-0986. We've seen quite a few of these come to light over the last year or so, mostly thanks to Project Zero, and they're nasty in that they execute in a highly privileged context and don't require any user interaction. Thankfully the patch should also get applied without having to take any action.
A somewhat unusual fix published today is for Microsoft's Wireless Keyboard 850. CVE-2018-8117 is a security feature bypass vulnerability, whereby an attacker able to extract the encryption key from a keyboard could then wirelessly send and/or read keystrokes, potentially reading sensitive data such as passwords or issuing malicious commands to a connected system.
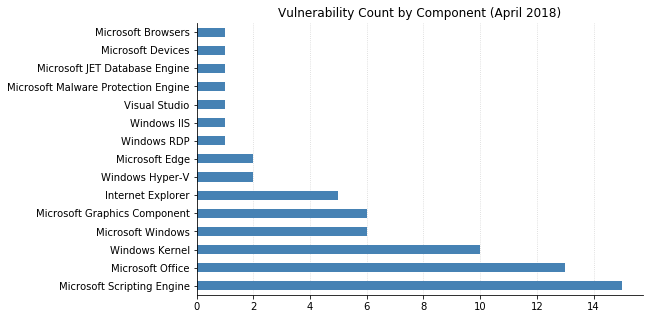
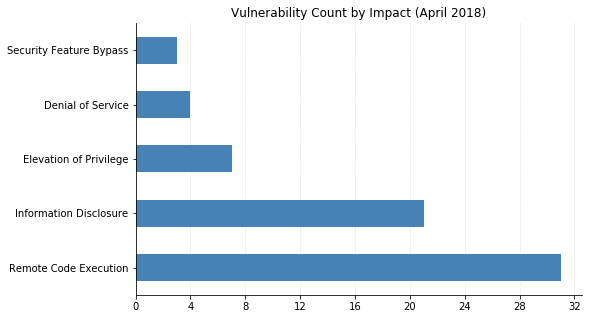
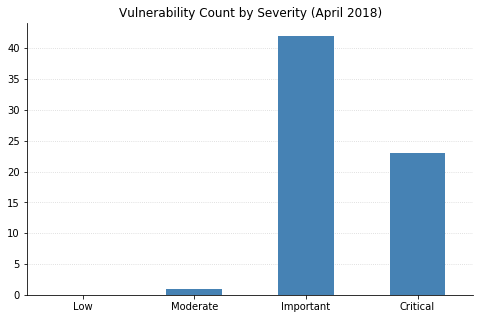
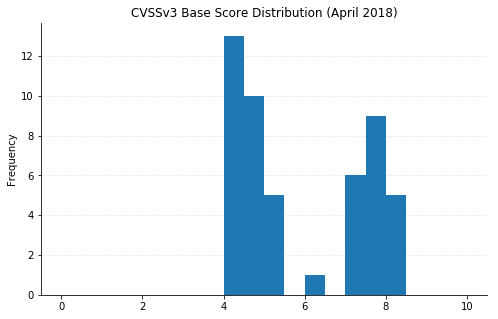
(Note: Not all CVEs had CVSSv3 data available at the time of writing.)
