InsightIDR customers now have an ever-evolving library of attacker behavior detections automatically matched against their data. Read on to learn how Rapid7 SOC and threat intel teams investigate a constant rumbling of attacker behavior and transform it into actionable threat intelligence.
Locard's exchange principle shares that a criminal will always bring and take something from a crime scene. Based on this principle, Edmund Locard penned the idea that "Every contact leaves a trace." For us, blue team defenders, this idea is crucial in the incident detection and response world. As long as we collect the right types of data, and apply the right analytics and intelligence to that data, it is possible to detect and respond to any type of attack.
Over the past three years, our Managed Detection and Response (MDR) analysts and threat intel teams have worked hand-in-hand to create Attacker Behavior Analytics (ABA): new detections that find unknown variants of validated attacker behavior. If you subscribe to Rapid7’s MDR, you’re already benefiting from the combination of ABA, user behavior analytics (UBA), monthly threat hunts, tailored threat intelligence, and deception technology monitoring your network 24/7.
Our managed threat detection service monitors hundreds of organizations—big, small, and across every industry vertical. Across the 300,000+ endpoints under our watch, our analysts identify and investigate malicious behavior hundreds of times a day. These investigations thoroughly analyze attacker tactics, techniques, and procedures (TTP), and with our detailed Findings Reports, arm our customers with the confidence to recover from an attack and harden their attack surface.
But we can, will, and have gone deeper. This continuous stream of attacker behavior helps us answer larger questions:
- What was the attacker going after? Who is their next target?
- How did we detect the threat? Can we simplify threat detection and ensure customers are confident around remediation and mitigation?
As part of the investigative process, our SOC and threat intel analysts collaborate to extract key behaviors from threats identified in our customer environments. After performing research on related attacks and behaviors, we craft new ABA detections. These are then deployed across all MDR customers to simplify and accelerate detection and reduce the time to remediation.
And now...we’re proud to share that InsightIDR customers have access to the pre-built Attacker Behavior Analytics that our SOC and threat intel teams create and use every day.
What are Attacker Behavior Analytics?
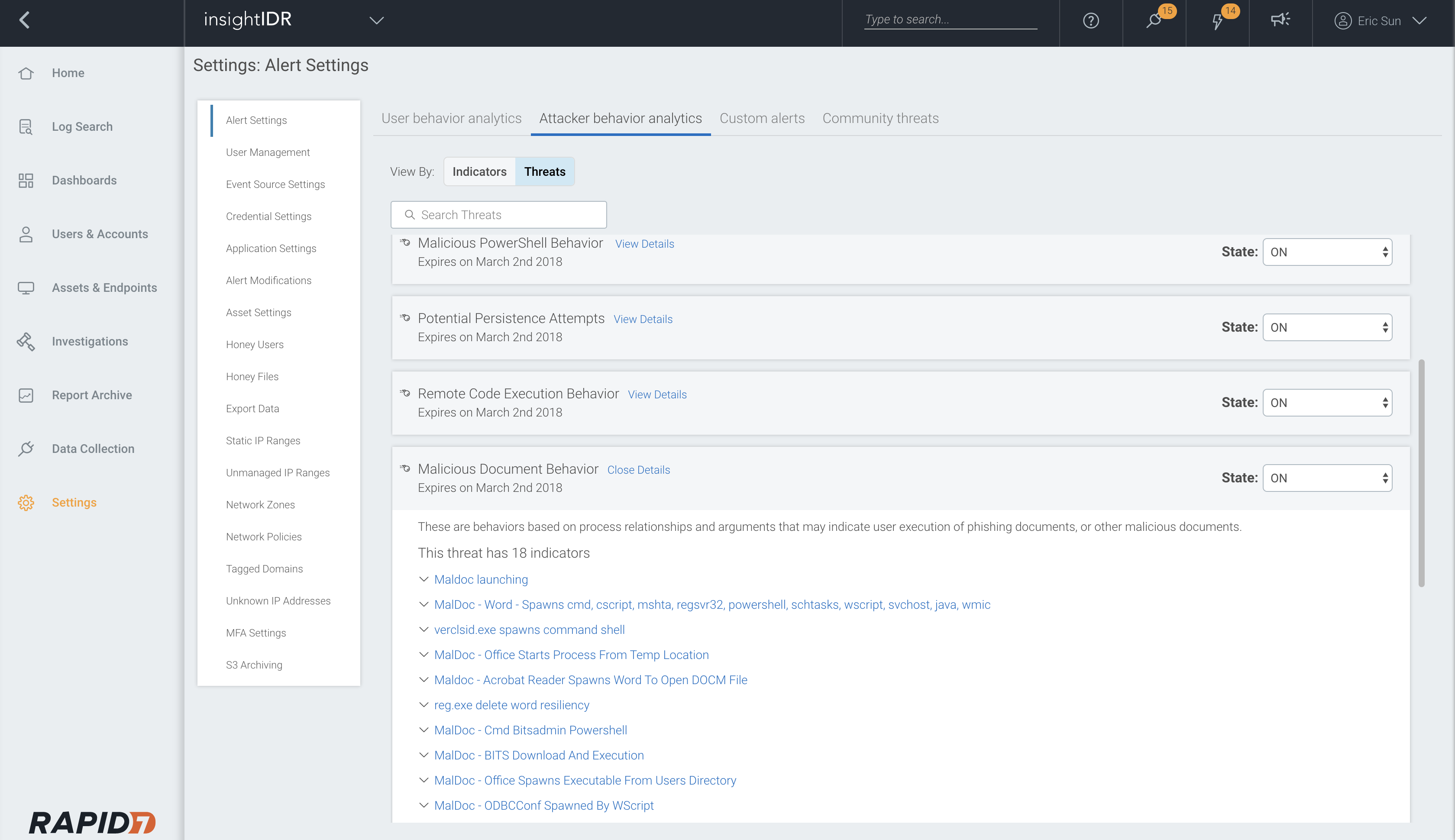
Attacker Behavior Analytics are pre-built detections modeled around our wide array of threat intelligence. ABA is the first benefit of the direct conduit between our global security operations centers (SOCs) and the Insight platform. If our analysts identify a novel attacker technique, they can contribute an ABA detection and push it out to be matched against your data the very same day.
Here are some of the ways that Rapid7 researches attackers:
| Source of Threat Intelligence | How is it useful? |
|---|---|
| Metasploit | What are attackers capable of doing today? |
| Project Lorelei, our honeypot network | What are attackers doing today? |
| Project Sonar, our internet-wide scanning project | Where will attackers strike next? |
| Managed Detection and Response customers | What are attackers doing in real environments? |
| Incident Response engagements | What have attackers done in real environments? |
| InsightIDR customers sharing intel | What attacks are InsightIDR customers concerned about? |
| Rapid7’s threat intel team & community (e.g., Cyber Threat Alliance) | What is the broader industry concerned about? |
We now maintain a structured, scalable Threat Intelligence Core that enables contributors to translate their investigative findings and expertise into Attacker Behavior Analytics.
Key differences in our approach with ABA:
- Behaviors, not signatures: If command line activity spawns from a running Word or Excel process, that isn’t good. Armed with high-fidelity endpoint data, we can identify novel variations of this attacker technique.
- Context to take action: Indicators of compromise don’t fix themselves just by being detected. Alerts include context from our analysts and threat intel teams, so you can make better decisions.
- Threat intelligence ages quickly: Whenever possible, the alert will detail known, recent adversary groups using a similar technique in a confirmed attack.
Attacker Behavior Analytics doesn’t just provide more detections, it shares the expertise of our analysts through curated threat intelligence and investigation recommendations.
What Do These New Detections Cover?
Attacker Behavior Analytics expose the finite ways attackers gain persistence on an asset, and send and receive commands to victim machines. This identifies:
- Malware, malware droppers, maldocs, and fileless malware (opportunistic & targeted)
- Cryptojacking: Stealing CPU cycles to mine cryptocurrency
- Pen testing & attack tools
- Suspicious persistence
- Anomalous data exfiltration
- New attacker behavior
This augments the user behavior analytics & deception technology you rely on in InsightIDR today. With ABA, you get faster detections that take full advantage of our comprehensive data collection and added context direct from our analysts fighting the same good fight.
How Does This Affect My InsightIDR Experience?
Each ABA detection hunts for a unique attacker behavior, which you can toggle to an alert, whitelist, or track as notable behavior. All of our pre-built detections, including ABA alerts, will surface notable user and asset behavior on the visual timeline.
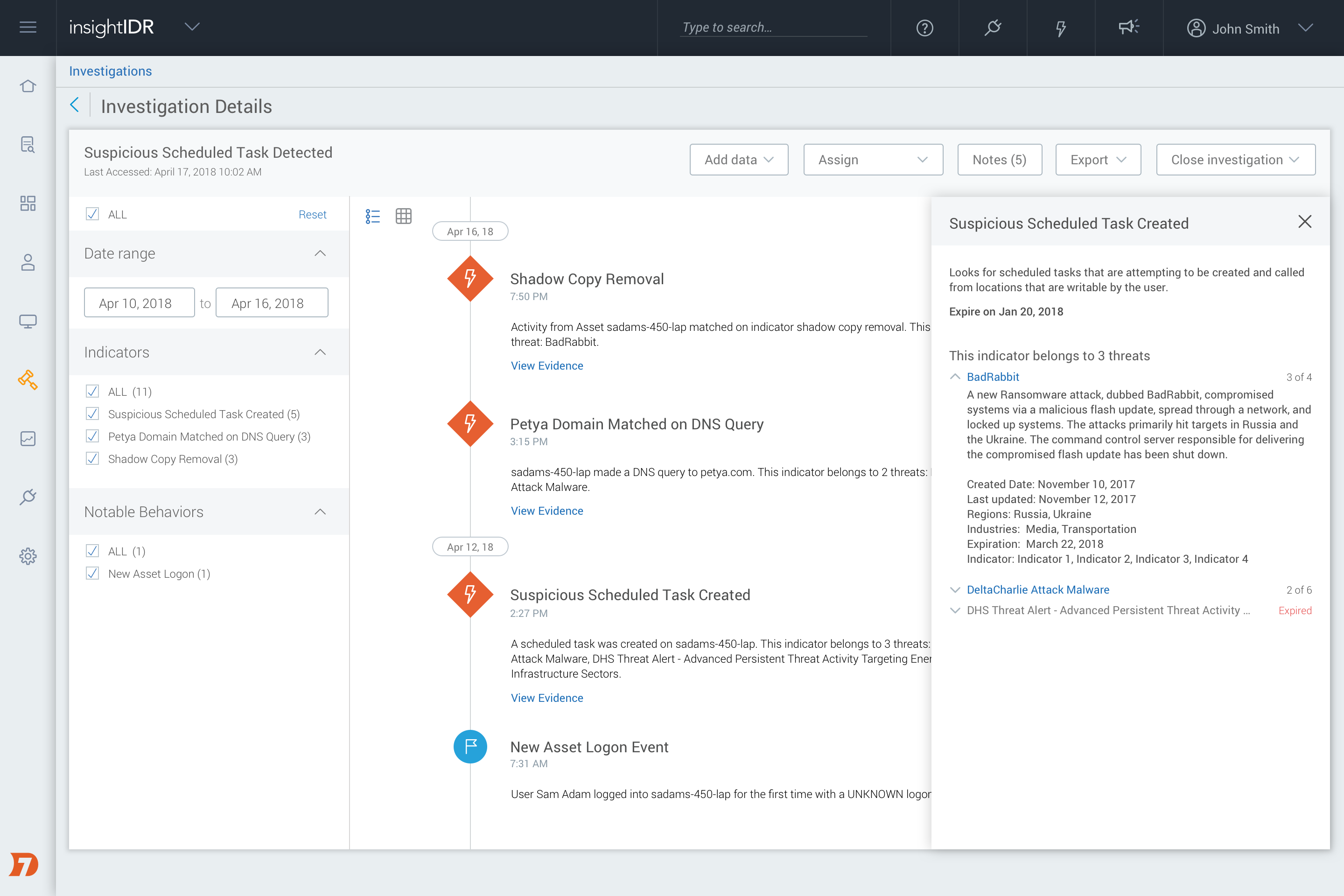
Each new detection is continuously refined by our analysts, and matched against historical data to ensure low-noise and high-fidelity. You have the full flexibility on how these behaviors are tracked in your own environment. To see the full list, head to the Settings tab > Alert Settings > Attacker Behavior Analytics: