Collecting data from the endpoint can be tedious and complex (to say the least). Between the data streaming from your Windows, Linux, and Mac endpoints, not to mention remote authentication and the processes running on these assets, there is a lot of information to gather and analyze. Unless you have a deep knowledge of operating systems to build this yourself—or additional budget to add these data streams to your SIEM tool—it may not be feasible for your organization. Or is it?
In this post, we’ll show you how Rapid7's SIEM platform makes monitoring your endpoints easy with a range of built-in endpoint detection and response capabilities, giving you threat detection and visibility into your users without requiring complex incident response know-how or another siloed tool.
Your users did what, where?
Can you say with confidence that you know exactly what your users are doing right now? Between authentications across VPN, network, and cloud services, and their behavior on the network, users complete hundreds to thousands of actions each day. Ensuring that none of that activity is coming from malware attacks, a compromised account, or an insider threat can feel like a tall task.
To get ahold of what’s going on across user accounts, InsightIDR correlates multiple data sources, including Active Directory, our universal Insight Agent, and cloud services.
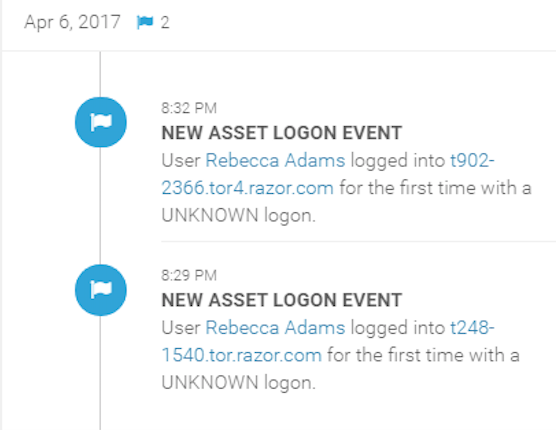
With InsightIDR, you can see if users are accessing unauthorized assets, logging in from multiple geographically impossible locations (such as Boston, MA and Singapore), or authenticating into a machine or service they shouldn’t have access to. All of these actions are indicative of compromise and, when viewed in context with the other data InsightIDR collects from across your IT environment, they enable you to quickly pinpoint account compromise, malware, or other nefarious behavior.
To determine if a user account is compromised, it’s important to have visibility into the context surrounding that activity. By using the Insight Agent, which collects real-time data for vulnerability management and detection and response, InsightIDR knows which assets a user has authenticated into, as well as their cloud service usage. It can also show authentication locations, VPN usage, and vulnerabilities when integrated with Rapid7 vulnerability management. If suspicious activity is detected, it could be that an attacker is impersonating a legitimate employee to move around the network.
To help you make quick sense of this data, InsightIDR tracks notable behavior for every user on the network, which can assist in quickly validating alerts generated or parsed by InsightIDR.
A bird’s eye view into your assets
Equally as important as being able to dive into user activity is having visibility into each asset. InsightIDR makes this easy by displaying a page for each asset with user login data, account usage, and recently used IP addresses. Gathered from Active Directory, DHCP data correlation, and data collected from the Insight Agent, this page will show everything going on and indicate whether activity could be malicious or not.
This information is especially useful if your team is distributed across offices or around the world. A user logging into an asset from Singapore may not be suspicious if one of your employees resides or is traveling there, but the only way for a SIEM solution to know this is by correlating endpoint data to determine normal versus abnormal behaviors. Making sense of this data on your own can be tedious, but with the capabilities in InsightIDR to correlate IP addresses with user activity and asset access, suspicious activity can be determined with high accuracy.
Even more, if you use InsightVM or Nexpose, InsightIDR can ingest vulnerability scan results and share that context across the solution. For example, if Nexpose identifies an asset as 'critical,' it can be automatically tagged as 'restricted' in InsightIDR for more sensitive alerting.
Drill down into unique processes
Finally, any threat detection solution needs to carefully monitor the processes running on your assets. Even today’s commoditized attacks, such as Ransomware-as-a-Service, are combining multiple obfuscation and defense evasion tricks to execute and persist undetected. For this reason, InsightIDR collects and analyzes full process tree data and command line activity to detect fileless malware, misuse of built-in IT tools (e.g. Powershell), and stealthy, newer trends, such as cryptojacking. This library of detections comes directly from a collaboration between our Managed Detection and Response analysts and our threat intel team. (Learn more about our teams and how they create Attacker Behavior Analytics.)
InsightIDR automatically matches all running process hashes against the wisdom of 50 virus scanners. It also helps you spot processes running that are unique (running on only one endpoint) or rare (spotted on less than 10 percent of all assets).
Once you spot a rare or unique process, you can see all the users and assets running the process with one click. InsightIDR provides a detailed page on each process so you can quickly see hash and signature details to help you assess the risk. InsightIDR also builds a timeline of activity per process so you can see when it appeared on the network and how it progressed. This information is crucial to the incident response process.
Faster threat detection and response
Endpoint data provides the missing link that most SIEMs neglect (or only offer at a premium). Without this data, you lose granular visibility that can give meaning to threat intelligence and help you pinpoint true threats faster. With InsightIDR, you get complete detection and investigation capabilities across every endpoint with minimal setup and no additional expertise required.
Check out our interactive product demo to see it all in action. To experience firsthand how quickly InsightIDR can expose threats across your environment, begin a free 30-day trial.
