Spring is here, and along with the flowers and the birds, the pollen and the never-ending allergies, we bring you 2018’s first Quarterly Threat Report! For the year’s inaugural report, we pulled an additional data set: significant events. While we like to look at trends in alerts over time, there is almost never a one-alert-per-incident correlation. Adversary actions involve multiple steps, which generate multiple alerts, and after analysis, tell the story of what actually happened in the incident. This additional analysis contributed to some of the more significant findings of the quarter, including an increase in threats targeting the healthcare sector.
This quarter’s report covers three main areas of concern for the modern IT defender:
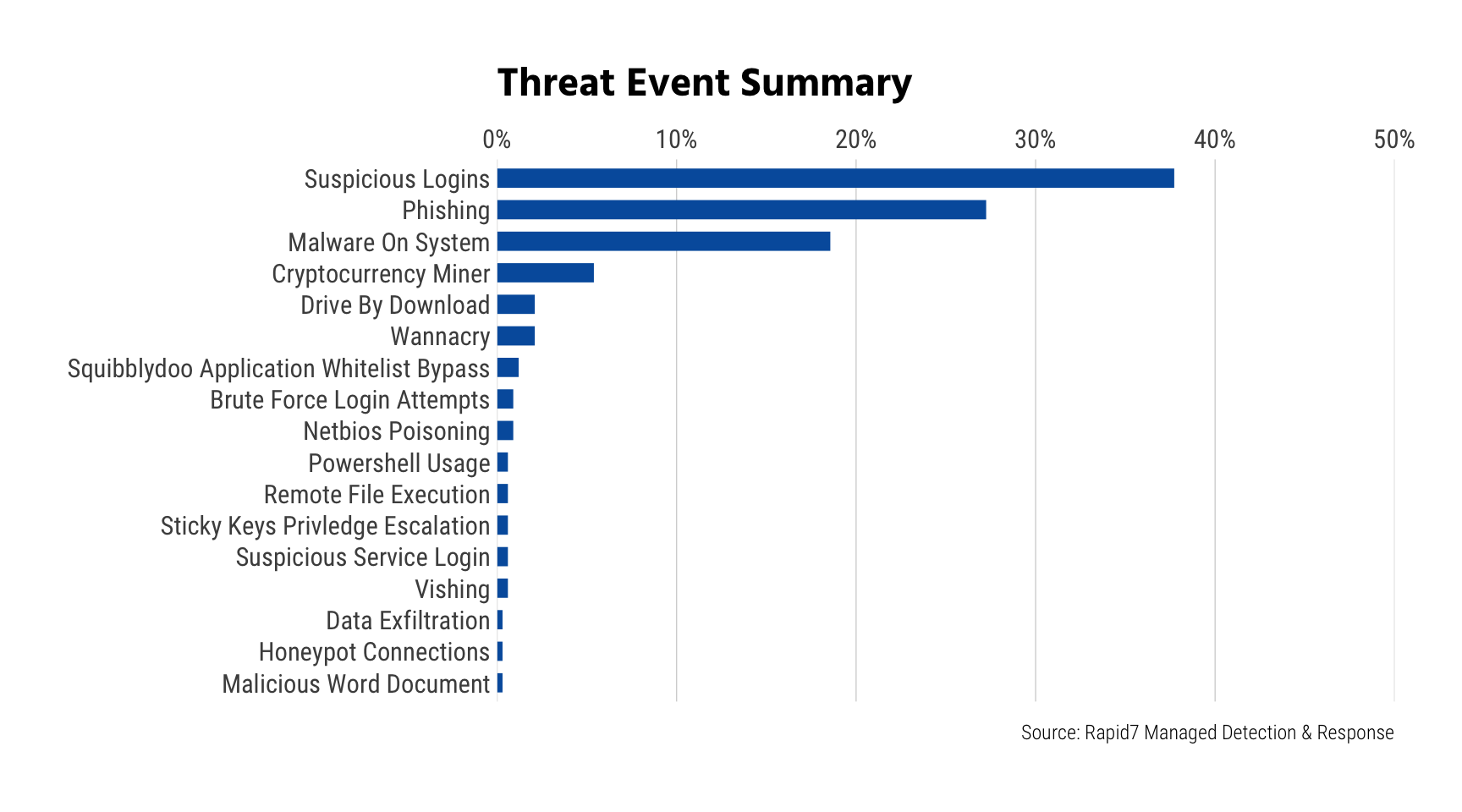
Credential Threat, Reuse, and Suspicious Logins
Credential theft, reuse, and subsequent suspicious logins are—today—the most commonly reported significant incident we’re seeing across both small and large organizations, and with good cause. In addition to the nearly constant stream of username and password dumps, more and more phishing attacks are specifically designed to steal the recipient’s credentials as opposed to getting them to run malware on their system, imitating everything from spoofed One Drive login pages to cell phone provider webpages. In this past quarter, suspicious logins and phishing threats both far surpassed malware on a system.
DDoS Attacks
DDoS attacks just got a lot more interesting with the debut of a new technique using misconfigured—and plentiful—memcached servers. Starting in January 2018, Rapid7 Labs began detecting what can only be described as “inventory scans” across eight amplification DDoS ports. When an attacker has a solid inventory of systems they can abuse in order to carry out their attacks, it is not difficult for them to amass an army to carry out denial of service attacks at will. We have previously reported on Distributed Reflective Denial of Service (DRDoS) attacks leveraging NTP vulnerabilities and UDP Amplification Vulnerabilities, and in this quarter’s threat report we dive into the use of misconfigured memcached servers, and how this activity will continue to shape the threat landscape.
SMB and Cisco SMI Attacks
Finally, we take a look at the increasing levels of SMB and Cisco SMI attacker probes and attacks, where the former continues to define the “new normal” level of background malicious behavior around Windows networking, and the latter begins to bring shape to this lucrative attack vector targeting core router infrastructure.
From attackers taking advantage of leaked and stolen passwords, to attackers taking advantage of misconfiguration in core routing devices, this quarter’s threat report sheds light on how defenders can protect their networks and detect the tactics that adversaries are using time and time again.
Read the 2018 Q1 report in its entirety for more of our key takeaways and some ‘spring cleaning’ tips.
