You’ve hired the best of the best and put up the right defenses, but one thing keeps slipping in the door: phishing emails. Part of doing business today, unfortunately, is dealing with phishing attacks. Few organizations are immune to phishing anymore; it’s on every security team’s mind and has become the number one threat to organizations. 80 percent of confirmed breaches to date have been attributed to weak, stolen, or default credentials.
Phishing emails attack your users in different ways, with social engineering, malware, and drive-by downloads being the most common methods. Your defense ultimately relies on how effective your users are at detecting phishing emails, links, and attachments. Attackers know this, which is why they’ve become quite savvy at duping users with believable pretext (e.g. sending an email from a fake CEO’s account) or a false sense of urgency (e.g. requesting a “mission-critical” expense be paid). If even one user’s account is compromised, an attacker can then send a legitimate corporate email to anyone in the company, which can magnify clicks and the chance of a real breach.
But phishing is an issue you can combat. Since your employees are your first line of defense against phishing, an effective strategy needs to both arm users and have countermeasures in place should that fail. In this post, we’ll explain the components of an effective phishing program:
- Block the obvious stuff
- Empower and test your employees
- Detect compromised users
Three components of an effective phishing program
Phishing attacks can spread quickly, so to protect against them, you need more than just security training or two-factor authentication. You should have the ability to:
1. Proactively block malicious emails—especially the obvious ones.
While it’s impossible to preemptively block all phishing attempts, it still makes sense to try and prevent the simple stuff. Secure email gateways, for example, can reduce your exposure to commoditized, opportunistic campaigns, and can also come with features to help identify data leakage and support compliance.
In a similar vein, there should be an easy way for your users to take action on a suspected phishing email. This comes in the form of reporting. If your users have an easy, seamless way to report a suspicious email or link, they’ll be much more likely to do so. Put a complicated reporting process in front of them, however, and the chances that they will do so will drop to near-zero. (Ignorance is bliss, remember?) Rapid7’s InsightPhishing can empower your users to report suspected phishes with a one-click report button embedded directly in their email clients.
2. Provide user awareness, training, and simulations.
When you combine phishing awareness and training with an easy way to act on that knowledge, you empower users to become your best security advocates. Phishing is a human problem, so to make your people more resilient, you need to have phishing awareness training in place. This can be done through a two-step process of education, then simulated testing to measure who clicks on the mock phishing emails. Campaigns should be sent out soon after training occurs and then periodically throughout the year—this keeps users on their toes and gives you enough data points to measure long-term training effectiveness.
Over time, you’ll be able to assess how your users are faring at phishing identification and reporting. If you send 100 simulated emails, are you getting 25, 50, and 75 percent more people reporting over time? Ideally you should be, but if not, that may be a sign you need to revisit your training program. With metrics in hand, you can demonstrate training progress to leadership, which can help validate training efforts and highlight improvement across the organization.
3. Detect users compromised by a phishing attack.
It's inevitable that at some point, one of your users will fall for a phish… if they haven’t already. In order to stop an attacker from accessing sensitive data, you need to know who they duped and what happened. When investigating an incident, it’s essential to know each step an attacker took between user accounts, endpoints, and your network to ensure that remediation is thorough and avoid rebreach.
However, even with automated alerting, phishing investigations take too much manual effort, even if they’re just to confirm that a suspected phishing email is benign. That’s where SIEM technology comes in, giving you the network-wide visibility required to identify compromises across your environment, right down to the exact users who were affected. Together, SIEM and phishing technology can provide you with a defense-in-depth approach.
User reporting + threat detection: A defense-in-depth phishing strategy
Having the capability to identify compromised user accounts and credentials is the biggest challenge for nearly every company today. That’s why fusing together user reporting with detection capabilities can give you complete end-to-end visibility.
Employee reporting is the most common method for discovering a breach.
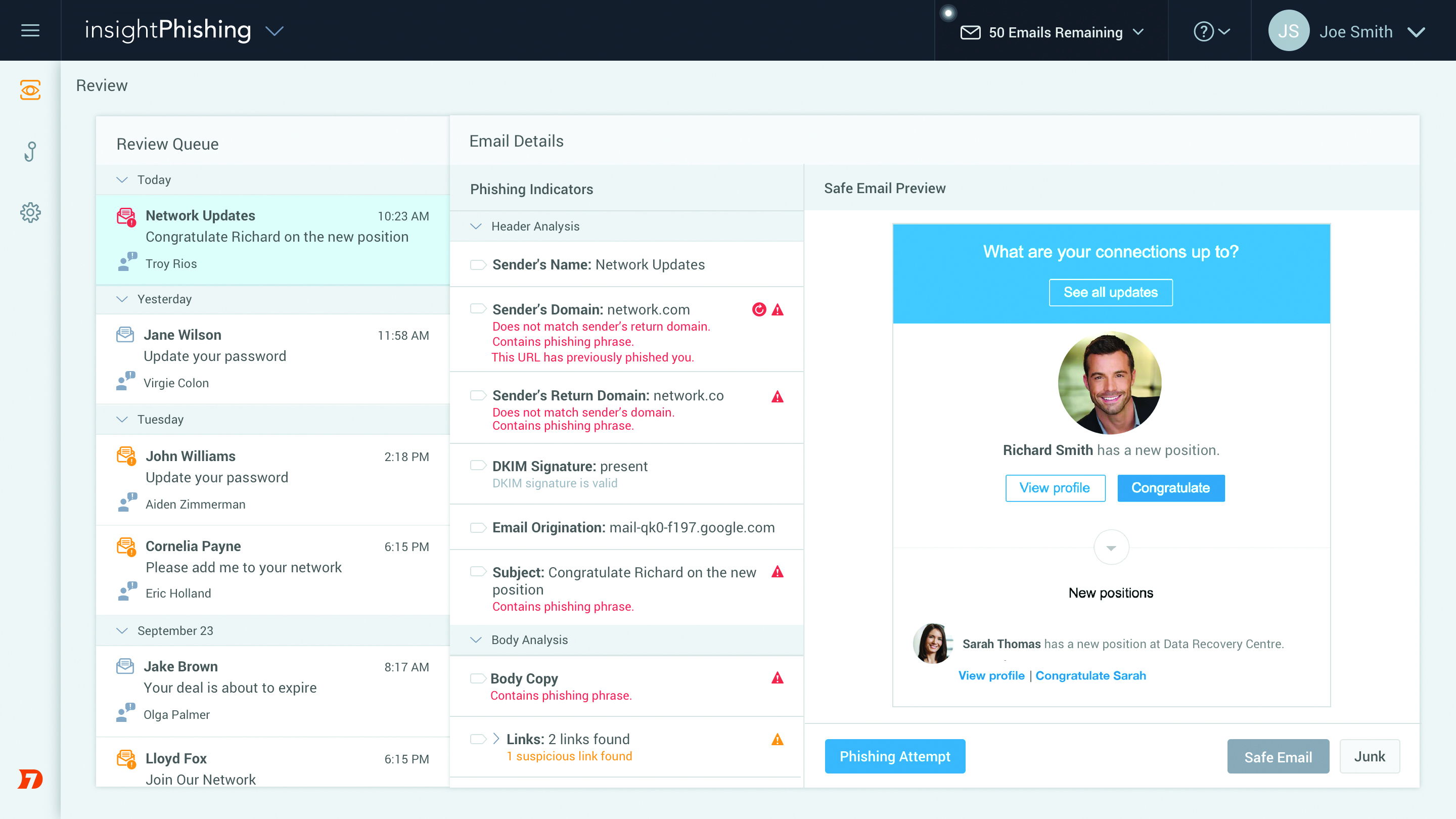
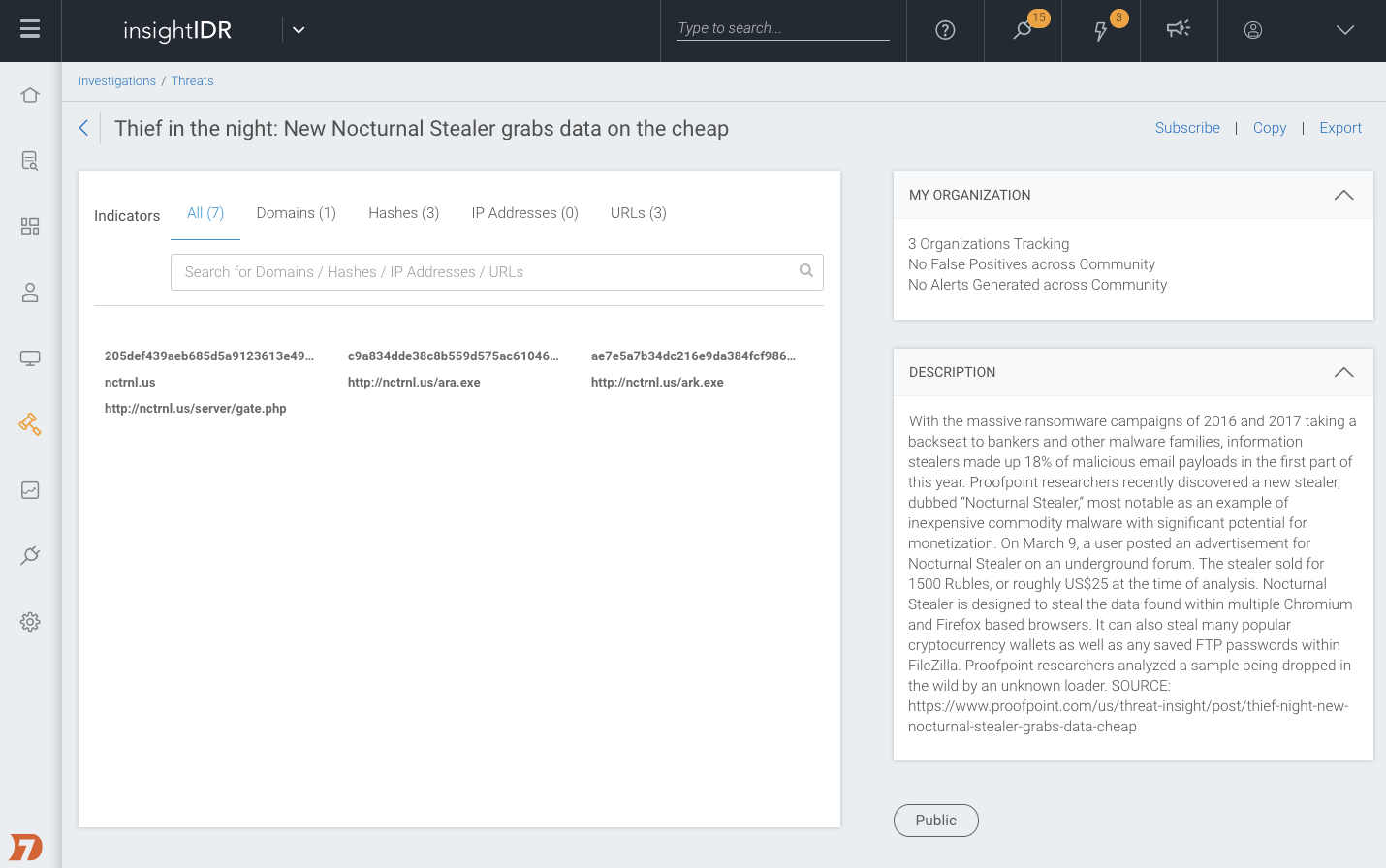
Any of these indicators can be added to a custom phishing indicator database for your organization so that your team can leverage the insights from past investigations. The more you train InsightPhishing, the better it gets. If you identify a malicious phish, you can use a SIEM like Rapid7's InsightIDR to scope out affected users, gain additional context, and improve your defenses. InsightIDR applies two layers of analytics to your data to find attacks: user behavior analytics (UBA) to find users exhibiting behaviors indicative of compromise, and attacker behavior analytics (ABA) to hunt the underlying techniques attackers use time and time again.
Any malicious URLs can be added to InsightIDR, which will then automatically match against future DNS, firewall, web proxy, and other user data. If a user accesses that URL in the future, InsightIDR can automatically alert you or track the action as a notable user behavior. After all, the key to preventing future compromise lies in translating your investigation findings into threat intelligence, and feeding that back into your proactive defenses.
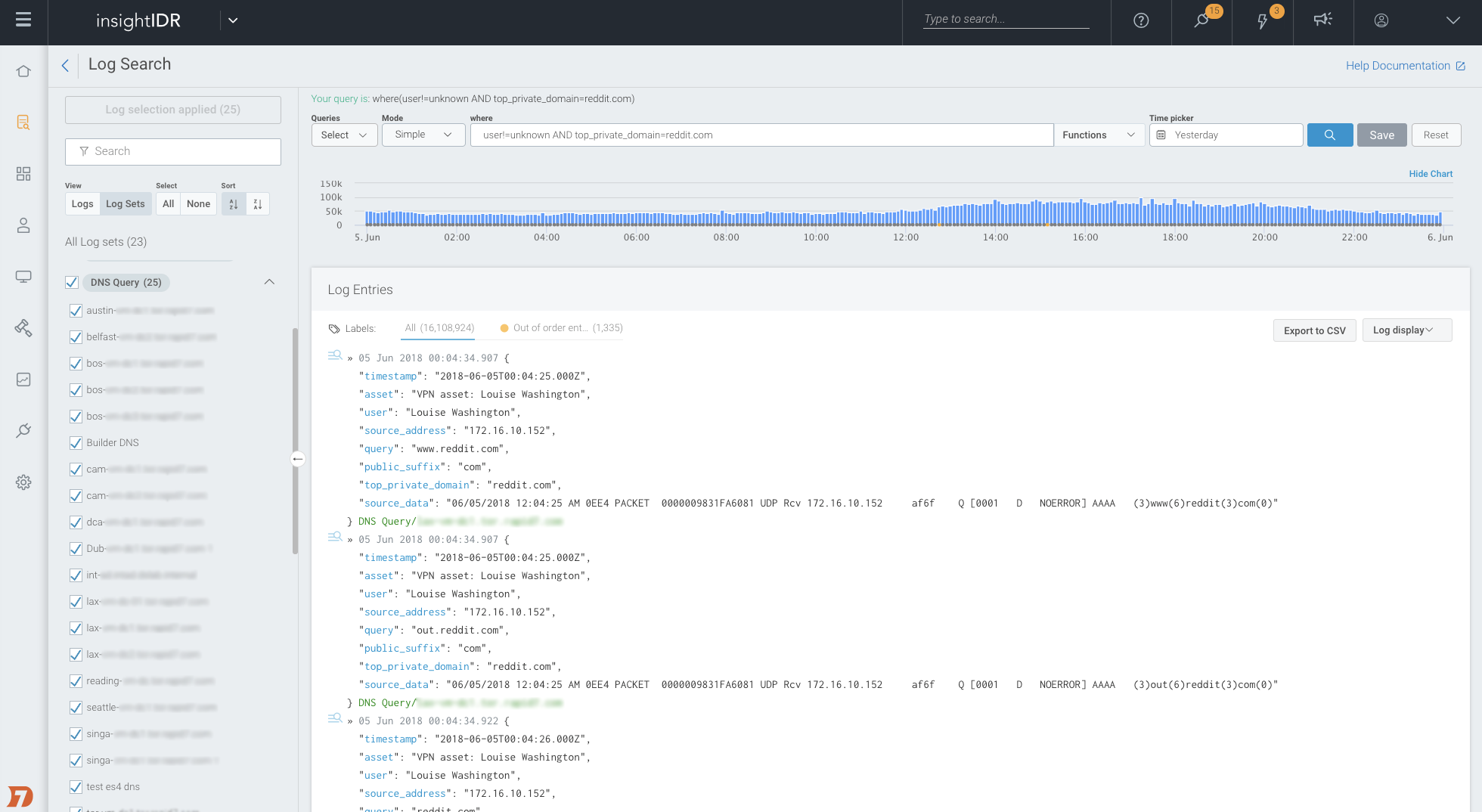
During an investigation of a phishing attack, you can also search through the logs within InsightIDR to see other users who accessed the URL at any point in time. If an attacker sends a phishing email to the entire organization, the log data will tell you the exact users who clicked on it so you can take appropriate action (e.g. change a password, deprovision an account).
Additionally, you can correlate the phish with other alerts generated by InsightIDR around the same time (e.g. new malware installed, unusual user account activity, new processes running, vulnerabilities exploited, etc.) to better inform remediation. This level of intel allows you to patch a vulnerability, shut down a process, or lock out an account to keep confidential assets or data safe.
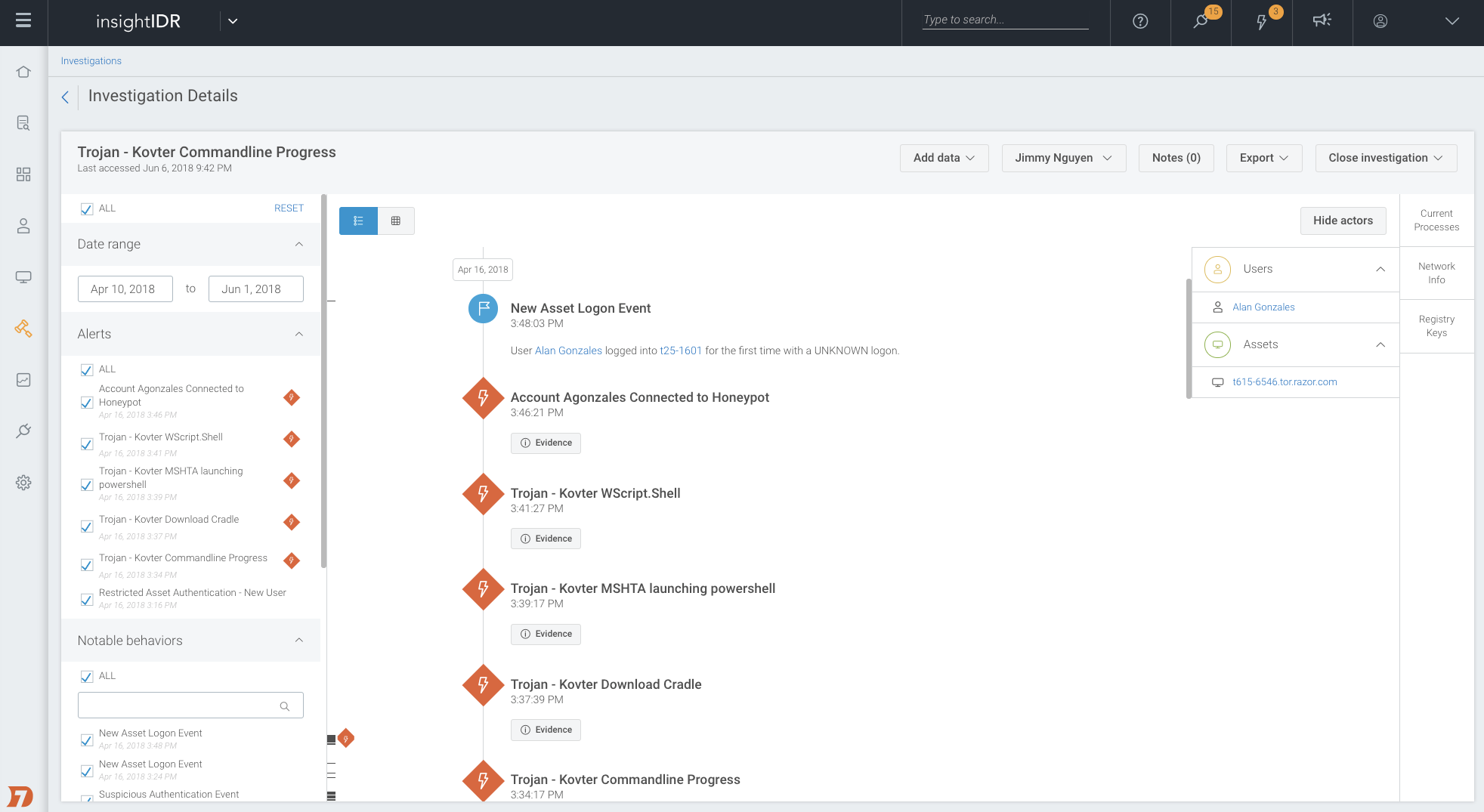
Together, InsightPhishing and InsightIDR are a complementary duo. Findings from one layer inform other layers in your defenses, creating true defense-in-depth.
