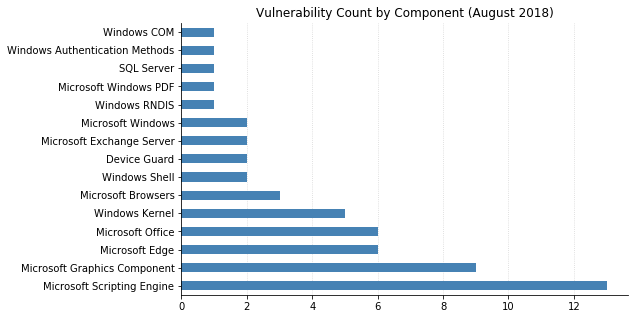
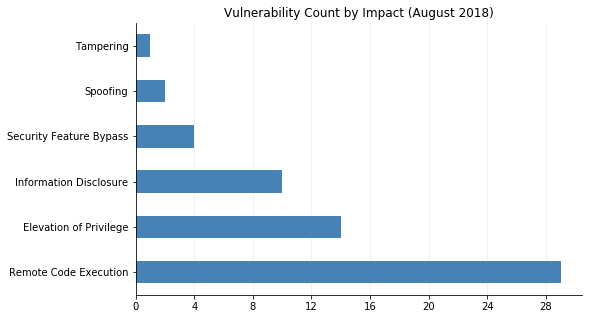
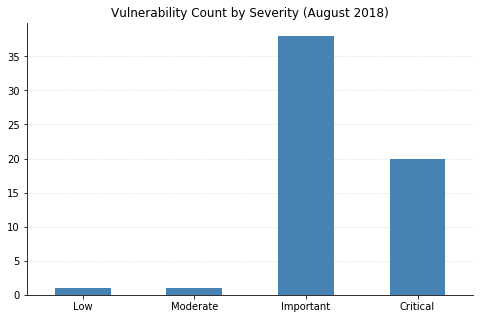
Microsoft's updates this month address over 60 vulnerabilities, 20 of which are classified as Critical. As usual, most of this month's fixes are browser-related, and nearly half of the flaws could lead to remote code execution (RCE). Patches for Exchange, SQL Server, and Microsoft Office were also released.
Two of this month's vulnerabilities have already been seen exploited in the wild. CVE-2018-8414 is an RCE in Windows Shell that affects Windows 10. Exploitation would require an attacker to convince a user to open a maliciously crafted file. CVE-2018-8373 affects Internet Explorer, and its impact could also be RCE via a malicious website or a document with an embedded ActiveX control.
Today Intel also released a security advisory describing "L1 Terminal Fault" (L1TF, originally named "Foreshadow" by the researchers), a new speculative execution side-channel attack akin to the Spectre and Meltdown flaws disclosed earlier this year. We can expect to see more of these in the future as security researchers further explore this new class of vulnerabilities. Microsoft has published guidance in their ADV180018 document, which contains detailed instructions for mitigating L1TF. Security teams should review which processors are in use across their enterprise, as well as instances where Virtualization Based Security (VBS) is being used. If you needed to protect any systems against CVE-2017-5715 (Spectre variant 2), you will also need to enable mitigations for L1TF. Many Windows client systems will be able to get away with regular software updates, though microcode updates and other changes will be required for some configurations (e.g. those using Hyper-V or VBS). L1TF affects several different attack scenarios, across different operating systems. Users and administrators should consult any relevant advisories published by their hardware and OS vendors.
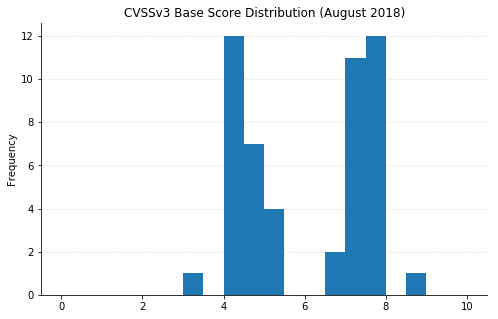
Note: not all CVEs had CVSSv3 data available at the time of writing
