Hot on the heels of the release of our second annual “Under the Hoodie: Lessons from a Season of Penetration Testing” report, we’re continuing to examine the data gathered from 268 penetration testing service engagements we conducted between September 2017 and June 2018. Software vulnerabilities are at the core of penetration testing, so for companies looking to prioritize their vulnerability management efforts based on real exploits, oversights, and security holes, the report provides insights and advice one can only get in the trenches.
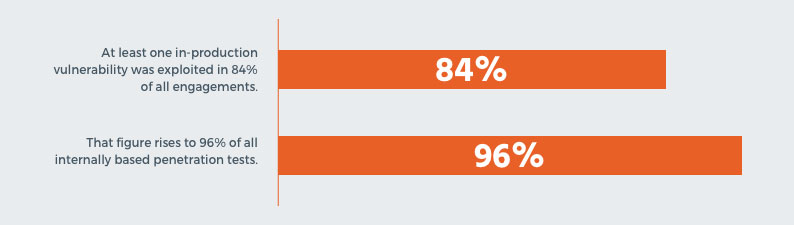
So, let’s dive in. In this year’s report, we saw a significant increase in the rate that software vulnerabilities are being exploited in order to gain control over a critical networked resource.
Security vulnerabilities are (still) the easy way in
Modern-day environments challenge the way we’re managing and scanning for vulnerabilities. Between sprawling attack surfaces that include both physical and virtualized environments, complex web applications that change by the hour, and the flood of alerts that all of these produce, it’s no wonder vulnerabilities continue to stack up while you try to juggle all of your tasks. Furthermore, as code and systems get more complex and more interconnected, the likelihood of introducing vulnerabilities in a networked environment increases to the point of (near) inevitability.
As explained in “Under the Hoodie,” when vulnerabilities are exploited, they allow the attacker to bypass a security control. This can lead to information leaks (the attacker gaining access to otherwise private information), privilege escalation (the attacker gaining exclusive rights that are otherwise unavailable), arbitrary code execution (the attacker running code on the target computer, thus subverting the vulnerable software), and various other types of cybersecurity attacks.
While last year’s report saw about a 68% rate of vulnerability exploitation, it rose a remarkable amount since, leading us to conclude that software vulnerabilities are still the easiest way in for most attackers.
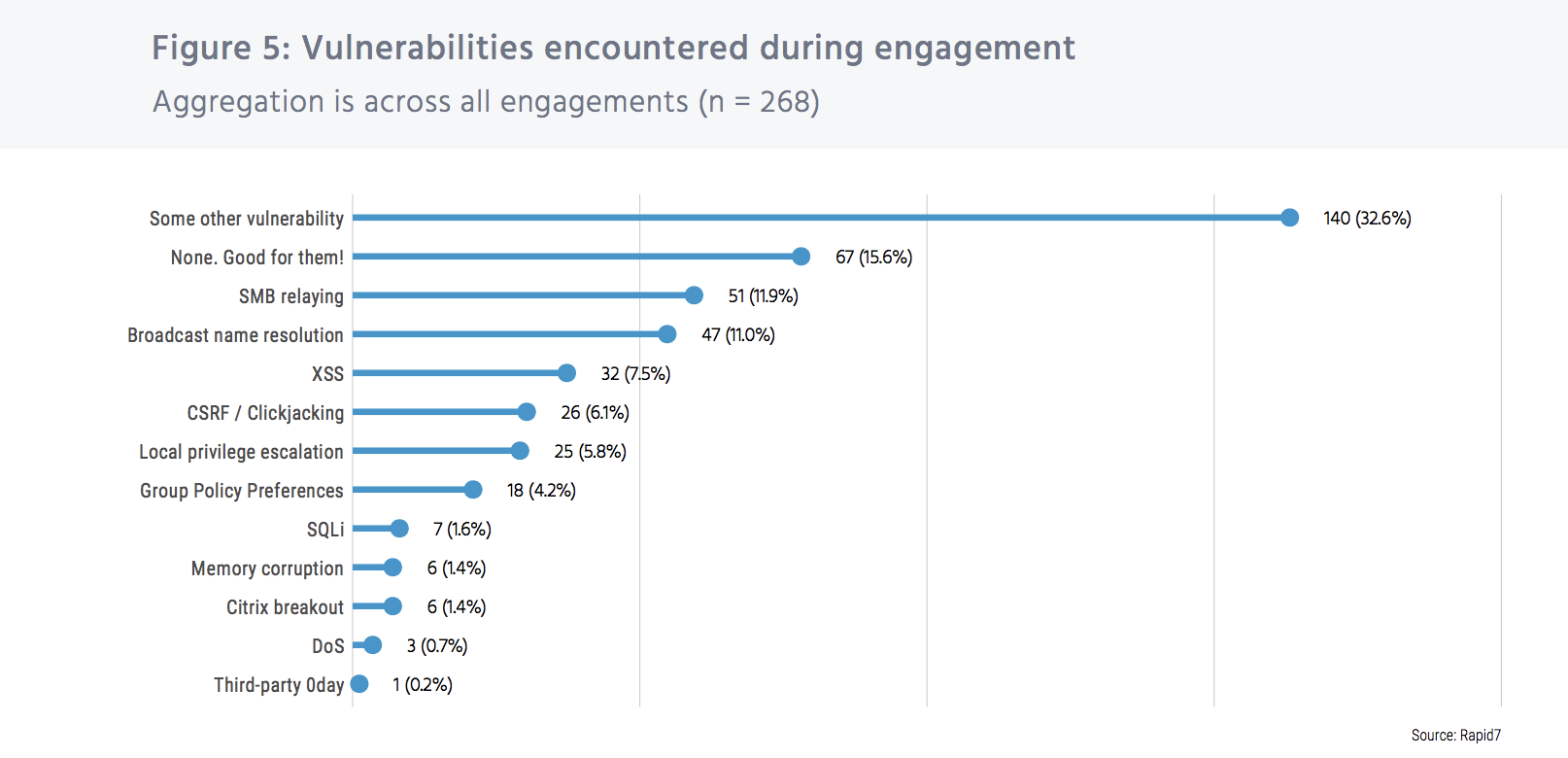
These common vulnerabilities are the main culprits
So, what kinds of vulnerabilities are we dealing with here? The breakdown is as follows:
Since “Under the Hoodie” is a compilation of both internal and external penetration testing, it’s worth observing how vulnerabilities differ between the two. Here’s what we found:
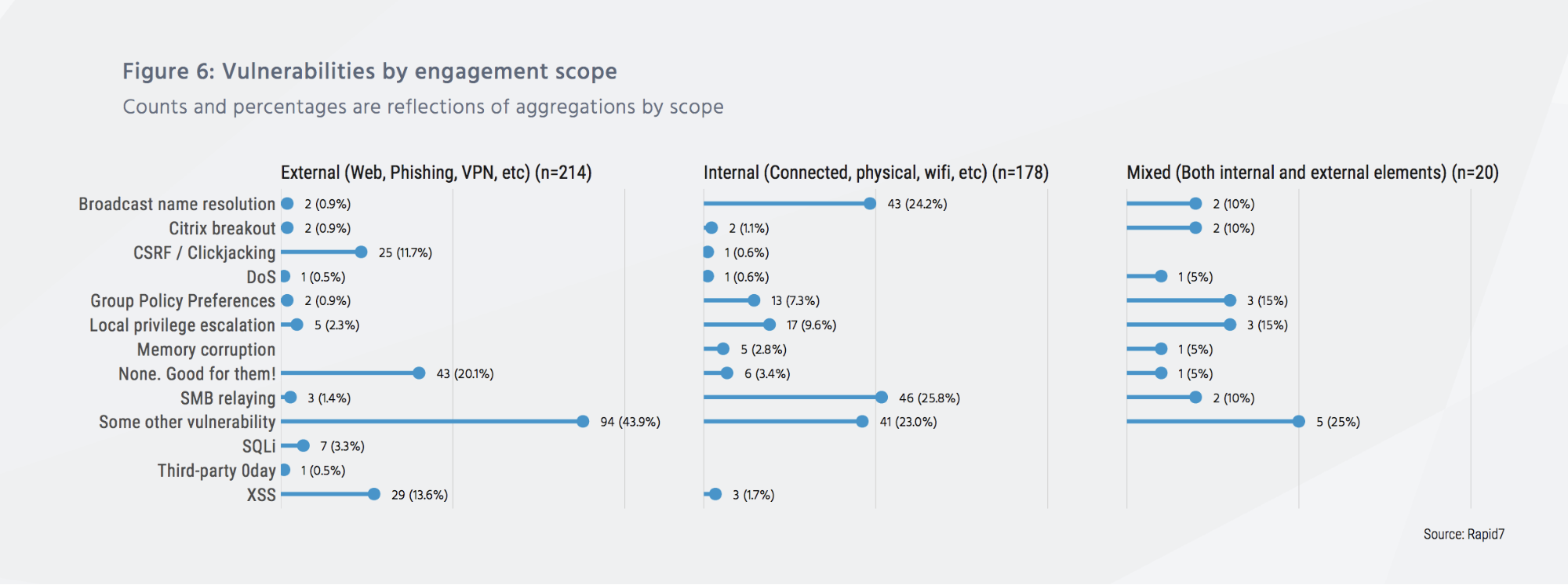
Do you see what we see? Another interesting data point is the lack of third-party, zero-day vulnerabilities encountered and exploited in our testing. And the single reported case of zero-day use was in combination with cross-site scripting (XSS) and “some other vulnerability,” meaning the zero-day was only part of the engagement’s success. This means…
Competent attackers do not need newly discovered, unreported vulnerabilities in order to successfully compromise a site.
Known third-party vulnerabilities—sometimes in combination with site-specific vulnerabilities—are often enough to gain significant control over a network.
Identifying vulnerabilities across a modern environment
Adversaries operate from the same intel we do—the moment a vulnerability is disclosed, they start actively hunting, knowing that most companies simply can’t keep pace. This means that as defenders, we not only need the ability to detect vulnerabilities faster, but also the ability to patch them quickly. And it goes without saying at this point, but monthly scanning is no longer enough, considering that modern environments change every minute. But for many resource-strapped security teams, lag time is simply a reality they’ve had to deal with.
This is where Rapid7 InsightVM comes in. A highly scalable way to gain full visibility of your ecosystem, it integrates directly with cloud, containerized, and virtual services such as AWS, Azure, and VMware to help you continuously identify and understand risk. InsightVM bypasses traditional silos, as it’s built to enable collaboration with IT operations, security practitioners, and developers—a practice we like to call SecOps. (Did we mention it supports over 50 technology integrations, and has a fully documented RESTful API?)
The more complex your environment, the more difficult it can be to spot vulnerabilities with conventional techniques, which is why more and more companies are turning to solutions like InsightVM that are built for expansive, continuously changing environments.
Prioritizing critical vulnerabilities
Finding vulnerabilities is the first challenge, and knowing which ones to prioritize is the next. That’s why we built InsightVM to not only be able to detect modern-day vulnerabilities, but to also prioritize these vulnerabilities based on which ones are the greatest threat to your business right now. InsightVM’s Real Risk Score goes beyond the capabilities of CVSS by leveraging attacker-based analytics, aka real-world intel about which actions and movements are most indicative of an adversarial presence.
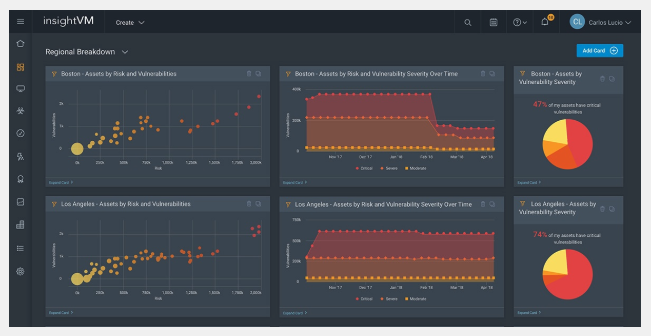
Along with the complementary threat feeds, this empowers you to know which vulnerabilities attackers are most likely to leverage, and therefore put your company at the greatest risk. Effective prioritization ensures you can patch the highest-severity ones first, closing the doors on a potentially crippling exploitation.
Next, InsightVM also streamlines remediation with remediation projects that help power SecOps at your organization; they break down the silos between security and IT by automatically correlating the context and urgency of a vulnerability, providing recommended remediation steps, assigning it to the correct owner, tracking progress, and then validating it has been fixed—all within IT’s existing workflows and tools.
While “Under the Hoodie” pointed out some glaring holes in the existing vulnerability management “establishment,” our hope is that by 2019, this number will be far reduced as more and more companies modernize the way they do vulnerability management. Once you have full visibility across your environment, you can prioritize which vulnerabilities to address based on real threat data, and even begin automating some of the remediation steps. The potential outcome? Vulnerabilities can be patched much faster, narrowing the window in which attackers can get to them and turning your company into one of the positive data points on next year’s report.