The biggest question in vulnerability management is always, “Where do I start?” Every security practitioner today is trying to get their arms around their ecosystem by determining what the most dangerous vulnerabilities are and how to take action on them quickly. Traditionally, this has been done using CVSS scores, which rate vulnerabilities on a scale of 0–10 (with 10 being the worst ones). But for companies with thousands of potential vulnerabilities flying in every day, there can be a lot that are scored as an 8, 9, or 10, leaving the task of prioritizing and responding to them just as much of a hassle.
What I love as a practitioner is Rapid7’s Active Risk Score, which is a feature inside InsightVM that enriches CVSS data to provide a more precise risk score, giving you a multi-dimensional look at each vulnerability. As an education specialist for Rapid7, I love teaching people how these risk scores are calculated and what this enables you to do as a practitioner. Once you understand where the number comes from, you can make better decisions.
Gain the insights you need to boost your vulnerability management program with a free trial of InsightVM today.
Get StartedIn this post, I’m going to provide a first-hand look at how we quantify the Active Risk Score and how this is helping practitioners worldwide address the top vulnerabilities in their ecosystems.
A multi-factor approach to risk quantification
How dangerous or threatening a vulnerability is depends on multiple factors, all which should be taken into account when developing a risk score. The first factor, of course, is knowing what the CVSS from NIST actually means. NIST evaluates each vulnerability according to the following factors:
- Access vector
- Complexity
- Authentication mode
- The CIA triad (confidentiality, integrity, and availability)
Let’s examine access vector as an example. If NIST determines a particular vuln can only be exploited by an attacker physically touching a machine, the score would be lower than a vuln that can be exploited via SQL injection (SQLi) or buffer overflow over a network. Gaining access to a single machine is much harder to achieve than an SQL injection, which makes it less of a threat.
InsightVM’s Active Risk Score not only takes into account the equation behind the CVSS of each vulnerability, but also the Metasploit modules that could be launched against you, the malware kits detected, and even how old the vuln is. The last one is important because the older a vulnerability is, the more likely it will be exploited. This is why InsightVM leverages CVSS versions 2 and 3, as these are the vulnerabilities we see most often exploited.
Combined, these factors offer a more robust picture of the threat a vuln poses to your organization. It also gives you insight into what access vector an attacker would use to execute the vuln, as well as the impact to the enterprise.
Metasploit modules are my favorite way to analyze a vulnerability. Not only can they tell me which vulnerabilities I have, but also how likely they are to be exploited. For example, novice attackers will typically use prewritten Metasploit modules, so if a vuln with a matching Metasploit module is detected in your ecosystem, you absolutely need to know about it so it can be addressed.
[Solution Brief] Quantifying Vulnerability Risk with InsightVM
Download NowKnow your top 25 vulnerabilities
In IT, 80 percent of the problems you have are caused by 20 percent of the vulnerabilities or misconfigurations in your ecosystem. So, if you can remediate the top 20 percent of vulns, that can provide a massive lift to your entire security posture.
Addressing these top issues often remediates the most threatening vulnerabilities to your organization. A report within InsightVM called the “Top 25,” shows you the top vulns broken down by site, domain, and asset group, as well as how many assets and machines the vulnerabilities affect. This helps you understand their potential impact and why they’re of highest priority to address. The report also includes remediation actions, many of which can be executed with the click of a button. For example, many older vulnerabilities can be addressed just by updating your Mozilla or Microsoft products. If you fix these two things, the Top 25 report will show you how much risk you’d address.
From there, you can get more granular with your prioritization of the remaining vulnerabilities. Because Active Risk Score uses a scale of 0–1,000, you can filter by score with much more granularity than you can with the CVSS scale of 0–10. For example, you can filter vulns with a Active Risk Score of 792–950 (a much more specific range than a CVSS of 7–9), allowing you to better identify vulnerabilities that meet a certain threshold.
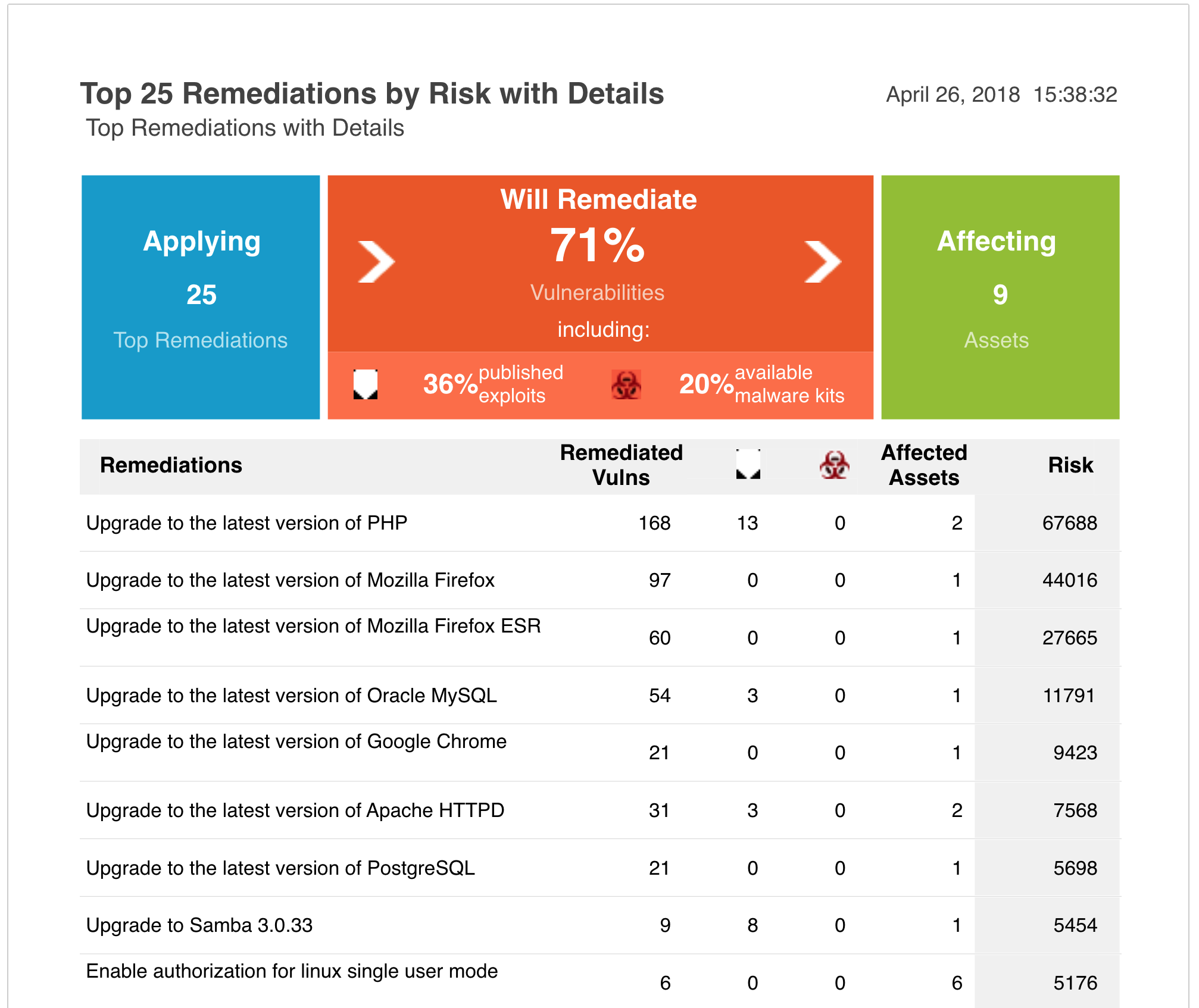
As a former frontline defender who ran daily vulnerability scans, it would have saved me an incredible amount of time and made my organization almost instantly more secure if I’d had this report a decade ago. In fact, I hear Rapid7 customers say all the time that this report alone makes InsightVM one of their most valuable tools. With an easy way to act on each of the vulnerabilities, you can watch your risk score trend in the right direction—providing instant gratification as a practitioner and a great way to show the impact of your work to the larger organization.
Pivot to address vulns you care about most
InsightVM also allows you to filter vulnerabilities based on the CIA triad: confidentiality, integrity, and availability. Depending on which of those is most important to you, you can see which vulnerabilities would be most pertinent to address. If availability is of utmost importance, you can search for vulns that match this criterion so you can address vulnerabilities that could lead to a DDoS attack, for example.
You can also take factors such as PCI compliance into consideration. InsightVM allows you to calculate risk based on which vulnerabilities would prevent you from meeting PCI compliance. If you have an upcoming audit, you can filter and address vulns that impact passing PCI.
Because InsightVM allows you to configure searches based on your priorities, you can switch modes at any point. Let’s say you finish a PCI audit and want to then focus on your Top 25 Active Risk Score. InsightVM will re-calculate your overall risks across your ecosystem to address those. And, if you’re like me and like to search for Metasploit modules as an indicator of high-priority vulnerabilities, you can do exactly that. This allows you to easily pivot focus and address what’s of highest priority in the moment.
A straight path forward
If you know where you’re coming from, you can better gauge where you’re headed. Having a better understanding of how risk is calculated can help you better understand the vulns in your environment and why certain ones are higher-priority. With a precise risk score in hand, you can quickly and accurately answer the big question, “Where do I start?” Active Risk Score gives practitioners a fantastic starting point, allowing you to think both strategically and tactically about your vulnerabilities.
Today, IT is not just part of the business, it is the business. With more and more data and systems moving online and integrating, it’s up to us as security practitioners to keep these environments safe.
