As a security company, there’s a lot of interest around our security operations. What tools do we use? What do our processes look like? Do we use our own products?
Today, we’re diving into a day in the life of a Rapid7 security operations center (SOC) analyst, specifically around threat detection and response. Since we monitor a complex environment with many assets, balancing visibility, smart threat detection, and security automation is a top priority.
Here are three challenges we’ve focused on solving with smart technology:
- Manually collecting, normalizing, and correlating events
- Sorting through alerts and gathering intelligence one threat at a time
- Speeding up incident investigations and time to contain/respond
With the help of InsightIDR, our MITRE ATT&CK-focused SIEM, these issues are addressed with automation and behavioral analytics. Let’s walk through a typical investigation to highlight how InsightIDR makes our incident response lifecycle both precise and scalable.
Using InsightIDR as a Rapid7 SOC analyst
Since all of our security log data is centralized and retained in the cloud-based Insight platform, our team can avoid expensive and ever-scaling hardware and database deployments. And, because we don’t need to worry about “running” InsightIDR—configuring hardware, or log collection—our energy is focused on interpreting what InsightIDR outputs in alerts and dashboards, and using that information to improve our security posture.
Step 1: Threat detection via user and attacker behavior analytics
The first step in our investigation process is to understand what happened. Many modern SIEMs today offer user behavior analytics (UBA), which identifies anomalous user behavior across your environment. This can include suspicious websites visited, malicious document downloads, or actions that indicate an adversary may be impersonating a company employee. While this is critical to finding unknown attacks, malicious use of credentials, and lateral movement, UBA typically identifies threats further down in the kill chain.
Therefore, the SOC teams created a wide range of detections to specifically find attacker behaviors, which have been added as attacker behavior analytics (ABA) to InsightIDR. Attacker behaviors include signature- and process-based attacks, specific attacker tools, PowerShell patterns, Meterpreter sessions, and more. These are all indicators of malicious intent and help us quickly narrow in on real threats, sifting out the false positives.
This combination of user and attacker behavior analytics, along with traditional threat intelligence and deception technology, gives us monitoring opportunities at each stage of an attack.
And, since the Insight agent can be deployed on endpoints and servers across our entire network, InsightIDR obtains 24/7 coverage of users no matter where they are. InsightIDR also pulls in data from Active Directory, DHCP, LDAP, and DNS, and gathers events from our firewalls, IDS, IPS, and so on. It then correlates this information back to specific assets and users both on and off the network. All of this information comes to us as condensed alerts filled with actionable context.
Step 2: Gathering threat intelligence
The next step is gathering more information about an event to effectively determine what we’re dealing with and the best course of action. Our SOC team works closely with our managed detection and response (MDR), threat intelligence, and incident response services teams to continuously identify new threats and the behaviors associated with them. We feed that intel directly into InsightIDR so that our SOCs, and those of our customers, can gain access to that intel from within their investigations.
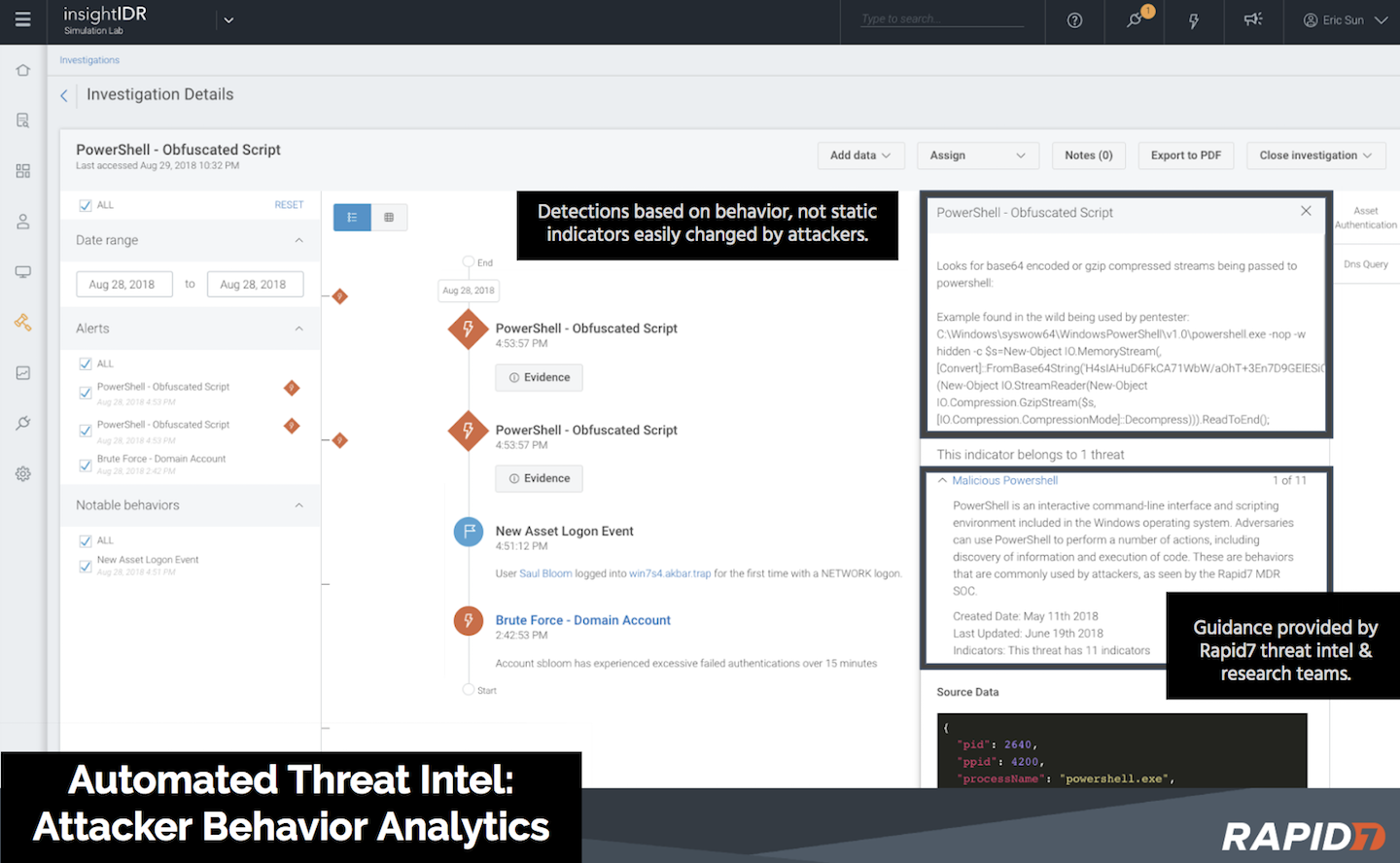
During investigations, we can pivot through log data with the built-in search to see what happened in the surrounding timeframe. Since log search, endpoint forensic jobs, and user context are all available within InsightIDR, we save time by avoiding jumping between multiple tools.
Step 3: Correlating events
Combined with threat intelligence, UBA and ABA offer rich information that helps our SOC team better detect and respond to threats. But if there is no way to correlate all of these details, it can be a long and grueling process. This is another feature built right into InsightIDR.
We can skip creating pivot tables and timelines in Excel with the user attribution and data enrichment automatically performed by the UBA in InsightIDR. Every employee at Rapid7 has a prebuilt user page that details notable user behaviors, asset information, remote authentications, and even known vulnerabilities from InsightVM scan data.
Step 4: Responding to threats with speed
Armed with information on user activity, network, and the endpoint, the final steps are to contain and respond to the threat. We launched additional automation capabilities to the Insight platform on Oct. 1. Now, InsightIDR alerts can be fed into designated automation workflows directly from an investigation, making routine tasks like phishing investigations, malware containment, and even disabling user accounts simple to move forward automatically. This saves our SOC team from spending hours each day on important but ultimately repetitive and tedious tasks.
As a result, we have more time to spend on threat hunting, responding to threats, and continuously improving our own processes.
End-to-end investigation workflow
Whenever InsightIDR generates an alert, it creates an open investigation that includes important user and asset context. The information is sorted into a clear timeline so you can see how the issue started, what assets were affected, and the evidence (e.g., DNS queries, firewall traffic, etc.)
With built-in automation in InsightIDR, we can kick off various workflows to take immediate actions, getting us closer to completing the investigation and moving on to the next one. This process allows us to truly magnify our impact, and get to the bottom of threats faster.
Conducting incident detection and response at scale
Having visibility across our entire network, no matter where an asset or user is, has been key for us. Without any rules to write, and leveraging threat intelligence from Rapid7’s team of security experts, our team can operate at great scale. Our customers have access to the exact same solutions and intelligence out-of-the-box with InsightIDR. In fact, our customers benefit from everything we as a company do to improve our own processes and outcomes.