“Where are the logs we are forwarding to InsightIDR, and what can we do with them?”
If you have been asking yourself this lately, this three-part blog series on finding answers with InsightIDR Log Search is for you. In this series, you’ll get our curated list of tips on how to be successful in running powerful queries in the least amount of time.
In this first installment, we’ll cover the three most important basics of Log Search:
- Selecting your logs
- Deciding which mode to use
- Setting your log view
Then, we’ll run through a few common Simple Mode searches.
Selecting your logs
To get started, log in to your own InsightIDR instance so you can follow along. Once you’re logged in, find and select the Log Search section on the left-hand side of the page.
Before you can run a search, you first need to configure Log Search as desired for your queries. The first thing to consider is which view you want to use to find your event sources: Logs or Log Sets. The Logs view shows all the event sources from which you are collecting logs, while the Log Sets view shows the incoming logs grouped into the main categories for investigative searches.
You can switch between the two views by clicking on the Logs/Log Sets buttons:
Using the modes
It’s easy to search through logs in InsightIDR, regardless of your level of tech-savviness. There are three modes for log search within InsightIDR.
- Simple: In this mode, the user interface assists you with creating queries. This is often used when searching for single items like a specific user or asset. We’ll show you the basic syntax to use to do this in the section below.
- Advanced: This is for users who want to create search queries themselves and control the search parameters.
- Visual: If search queries are a foreign language to you or you’d rather be shown the way, the visual search in InsightIDR gives you charts and graphs of activity for easy viewing.
Find a view
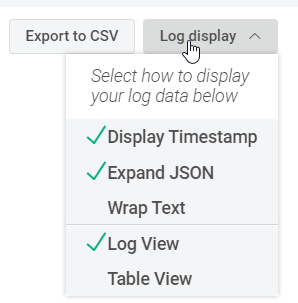
A handy feature of InsightIDR is the ability to change how the log entries are displayed on the page. Use the Log Display dropdown to change the view to whatever you like best. We recommend using Log View with Expand JSON selected. If you haven’t yet used this option, select it now and notice how it displays one field of parsed data per line. As you get accustomed to Log Search, this view can help you quickly identify which fields of data have been parsed from the logs.
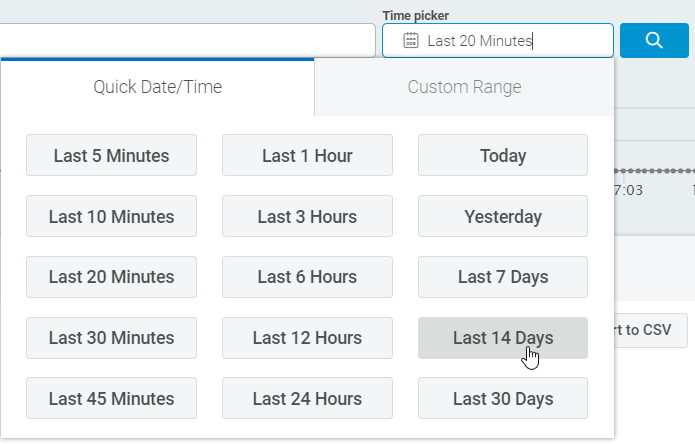
Finally, use the Time Picker to select an appropriate time for your search.
Perform a search
Let’s put this together and perform a search using Simple Mode. With Simple Mode, you can just type what you want to find into the “What would you like to search for?” box. For example, let’s look for what time a user logged in today.
Start with the Log Sets view, and select your Asset Authentication data set.
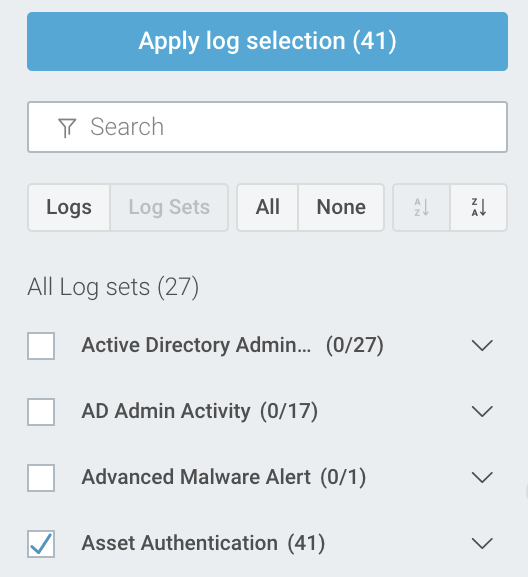
Set the mode to Simple, and use Time Picker to select how far back you want to search.
In the “What would you like to search for?” box, enter in what you want to search for. Here are some common search options to try with Asset Authentication, although many more options are available:
| Log Entry Query | Result |
|---|---|
| name | All logs that contain the string ‘name’. Please note that the search is case-sensitive. This will match: "name" and "name.domain.com" |
| /name/i | All logs that contain the string ‘name’ using a case-insensitive search. This will match: "name", "name.domain.com", "NAME", and "Name", etc. |
| NOT string | All logs that do not contain “string”. |
| 192.168.0.1 | All logs containing the specified IP address. |
| result=SUCCESS | All logs where the specified field contains the specified value. |
| result!=SUCCESS | All logs where the specified field does NOT contain the specified value. |
| hostname AND logon_type!=NETWORK | All logs containing both the string ‘hostname” AND where the specified field does NOT contain the specified value. |
To see this all in action, I made a four-minute video in which we search to find out the last person who logged onto a particular server:
Putting it all together
Now that you know how to perform some simple queries in InsightIDR, let’s answer a common question that you’ll likely be asked at some point: “When did a particular user log in yesterday?” As you examine your Asset Authentication logs, you might notice two similar fields:
destination_user and destination_account.
destination_user is the full name pulled from Active Directory, whereas destination_account is the ID that the user actually enters to log in. You can use either of these fields for this search. For example, I’ll use this as my query:
destination_account=ldiaz
Next, let’s say we need to find out who unlocked a particular account. Let’s change our Log Set selection to Active Directory Admin Activity, and then run this query:
ACCOUNT_UNLOCKED
We can narrow this search further by adding AND and target_account to the query:
ACCOUNT_UNLOCKED AND target_account=ldiaz
For this log type, target_account denotes the account that was unlocked.
As you can see, getting started with Simple Mode queries in Log Search is easy and provides many options for digging into the details of your log data. The best way to get started with Log Search is to roll up your sleeves and start running some queries! Try different Log Display options so that you can find what you like best, and be sure to select different Log Sets so that you can see exactly what is stored in each group. Looking for a head start? Here are some of the more popular queries we see our customers running.