Managing an effective, sustainable security operations program today is challenging. Threats continue to evolve, resources are constrained across the board, and processes need to be built, tested, and reported on to a wide variety of audiences ranging from management to compliance auditors to security-aware customers.
That’s why at Rapid7, our mission is to help you break down legacy siloes, whether between IT, development, or external audiences, with sustainable processes and connected tools. From a technology perspective, we’ve focused on three major areas:
- Visibility into your modern, ever-changing network
- Analytics (such as user behavior analytics) to find credential-based threats
- Automation
As part of our webcast series, “Get Sh!t Done with Automation,” Rapid7 security solutions engineer Hannah Coakley and I explained earlier this month how companies can accelerate across their entire threat detection and response lifecycle by leveraging thoughtful automation. Read our brief recap below:
Modern threat detection and response
Between today’s diverse range of threats and the spectrum of data that comprises your modern corporate network, the base requirements for effective visibility, analytics, and automation have shifted:
1. Visibility: Data collection, correlation, and analysis
The first challenge companies need to address is collecting the right data from the right sources, from endpoints, to cloud services, to infrastructure-as-a-service (IaaS). Then, it’s a matter of making that data easily accessible, searchable, and digestible across infosec, IT, and development teams.
2. Analytics: Meaningful alerts and threat intelligence
Once you have the data, you need to know whether it can help you find anomalies and active threats across users and assets within your ecosystem. Nearly all threat detection solutions today spit out a high quantity of false-positive alerts lacking important context, which makes it both tedious and frustrating to understand what really happened. Security teams need to demand a better approach to help them find and respond to the events that deserved focused investigation.
3. Automation: Investigations and incident response
Once risky or malicious activity is detected, you need to be confident that it’s legitimate and be able to trace everything the adversary did from initial access to your internal network to lateral movement and persistence across other company assets. Once you contain and remediate a threat, your risk of rebreach is minimized and that new threat intelligence is added to your prevention defenses.
How InsightIDR can help
Our detection-focused SIEM, InsightIDR, addresses these three areas in order to address the needs of modern security teams.
It works by first unifying security data, collecting it from endpoints, networks, and your cloud services, then automatically tying those disparate events to their respective users and assets. From a single real-time map, you can see all ingress to your internal network across VPN, cloud services, and FFF. Along with our wide range of alerts for stolen credentials generated by our user behavior analytics, it makes it easy to spot why there are Office 365 accounts authing in from Nigeria, for instance.
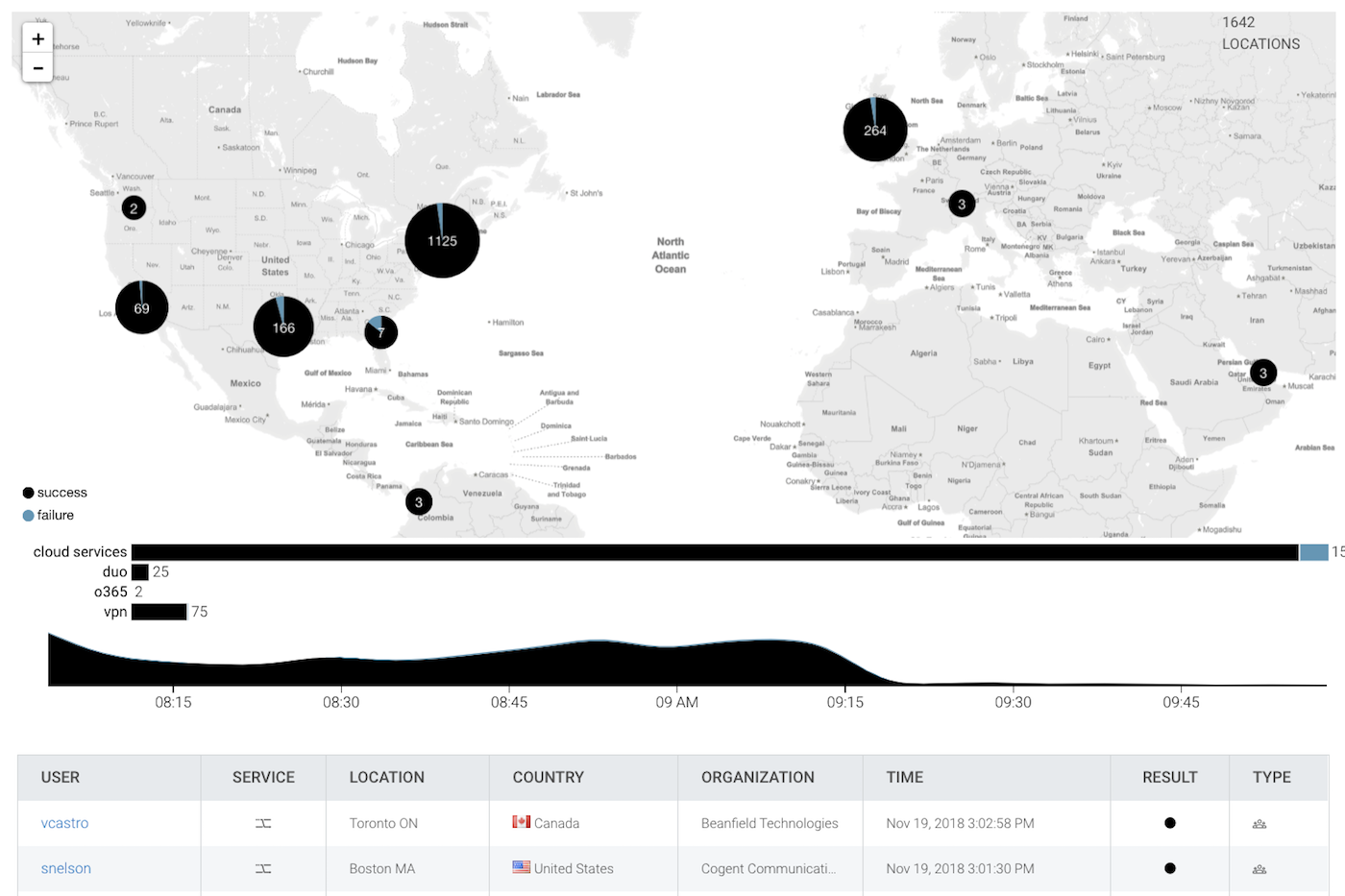
InsightIDR is delivered exclusively as SaaS-SIEM, which means you don’t need to worry about data storage, scaling, or infrastructure. You get full access to your data with a powerful log search and pre-built compliance dashboards, with a configurable retention length to align with your business needs.
Because InsightIDR is focused on holistic detection, unlike other SIEMs, endpoint detection and response is included with our Insight agent. We maintain one agent across the Rapid7 portfolio, so you can also gather asset vulnerability data if you have Rapid7 InsightVM.
Armed with this data, InsightIDR identifies the top behaviors linked to confirmed breaches—phishing, malware, and the use of stolen credentials
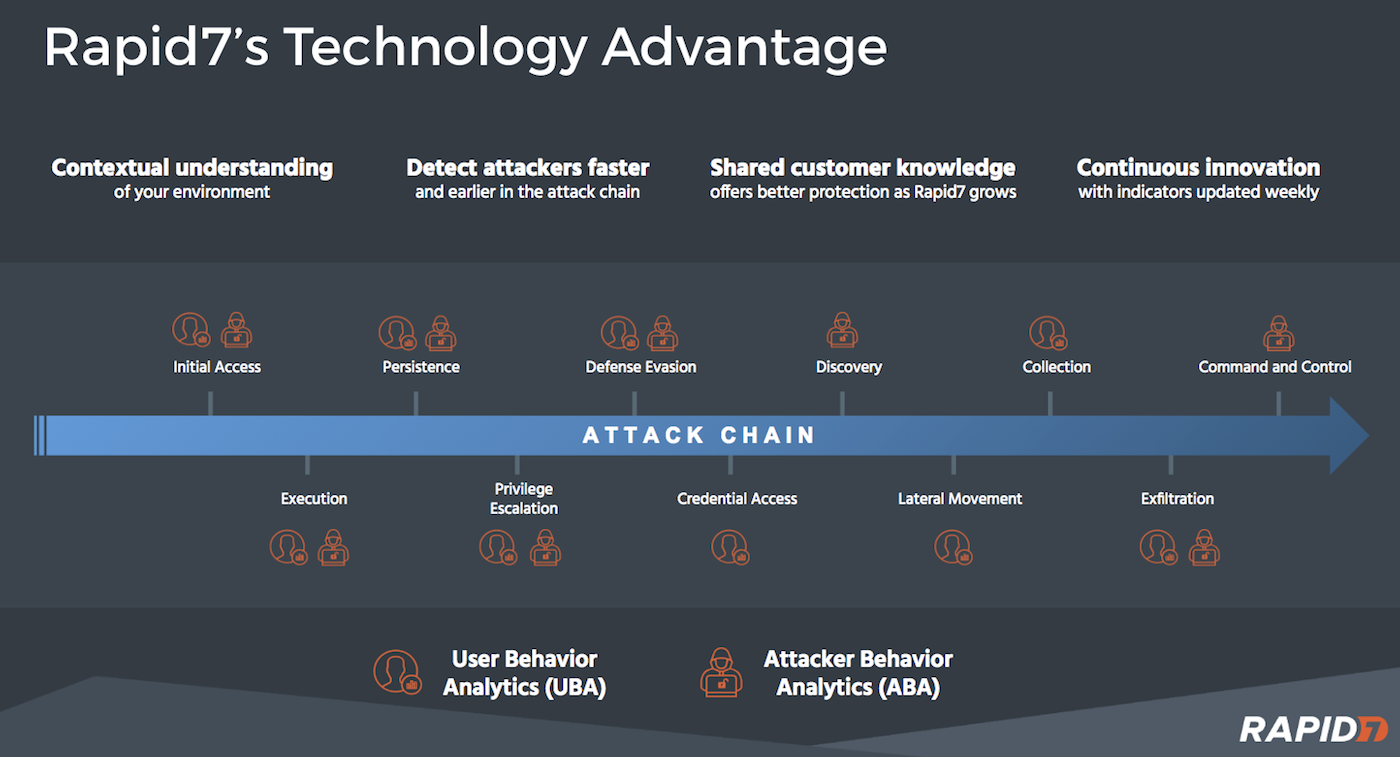
If you’re familiar with the MITRE ATT&CK framework, InsightIDR has hundreds of pre-built detections to find dangerous behavior at each stage of the attack chain. This ranges from email accounts exposed in public data breaches to suspicious persistence techniques (e.g., PowerShell spawned from Word), to east-west lateral movement, to privilege escalation and event log deletion.
Whenever InsightIDR surfaces a threat, relevant events are presented in a visual timeline. From there, it can automatically sync with ticketing systems such as Jira or ServiceNow to ensure the right stakeholders are in the loop. From within the investigation interface, you can also take direct action to contain a threat, including disabling an account in Active Directory or Okta, killing a process, or quarantining an asset with the Insight agent.
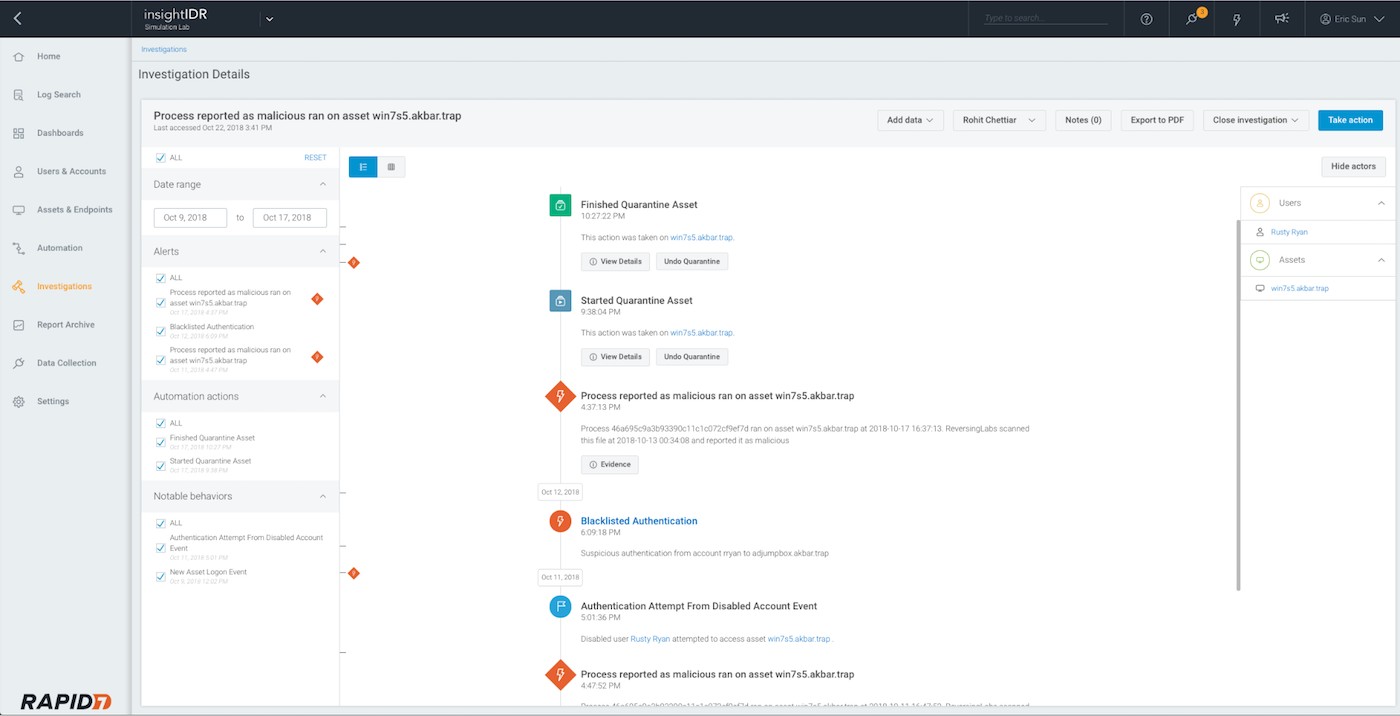
A two-pronged, layered approach to behavior analytics—user behavior analytics and attacker behavior analytics—is what makes InsightIDR particularly unique. It’s already a crucial element of modern detection and response programs for hundreds of companies spanning across the S&P 500 to midmarket companies with underserved security staff.