What do I need to know about the Drupal remote code execution vulnerability?
On Wednesday, Feb. 20, 2019, the Drupal Core team provided an early-warning update for the third Drupal Core Security Alert of 2019, which has been assigned CVE-2019-6340.
The vulnerability lies in the lack of field sanitization from non-form sources, which can result in arbitrary remote code execution on the Drupal server. The Drupal Core team has identified a certain set of conditions necessary for a successful exploit:
- The site has the Drupal 8 core RESTful Web Services (rest) module enabled and allows PATCH or POST requests, or;
- The site has another web services module enabled, like JSON:API in Drupal 8, or Services or RESTful Web Services in Drupal 7.
They further indicate that “The Drupal 7 Services module itself does not require an update at this time, but you should still apply other contributed updates associated with this advisory if Services is in use.”
NOTE: If you are running a version of Drupal older than 8.5.x, you must upgrade to 8.5.11 or 8.6.10 to fix this vulnerability.
What can I do to secure my Drupal servers from CVE-2019-6340?
The Drupal Core team advises that:
- If you are using Drupal 8.6.x, upgrade to Drupal 8.6.10.
- If you are using Drupal 8.5.x or earlier, upgrade to Drupal 8.5.11.
They further indicate that Drupal site owners should make sure to install any available security updates for contributed projects after updating Drupal core. No core update is required for Drupal 7, but several Drupal 7 contributed modules do require updates.
A super-quick remediation is to disable all web services modules, or configure your web server(s) to not allow PUT, PATCH, or POST requests to web services resources.
Is this vulnerability present in your environment? Find out with a free InsightVM scan.
Get StartedHow big is the attack surface?
Rapid7 Labs’ Jon Hart crafted Sonar HTTP studies of the Alexa Top 1m looking for both Drupal headers and the presence of CHANGELOG.txt to help identify the scope of the issue on the internet’s top sites. Unsurprisingly, the versions are all over the place, but when summarized at the main version (4–8), most identified sites seem to be running version 7.
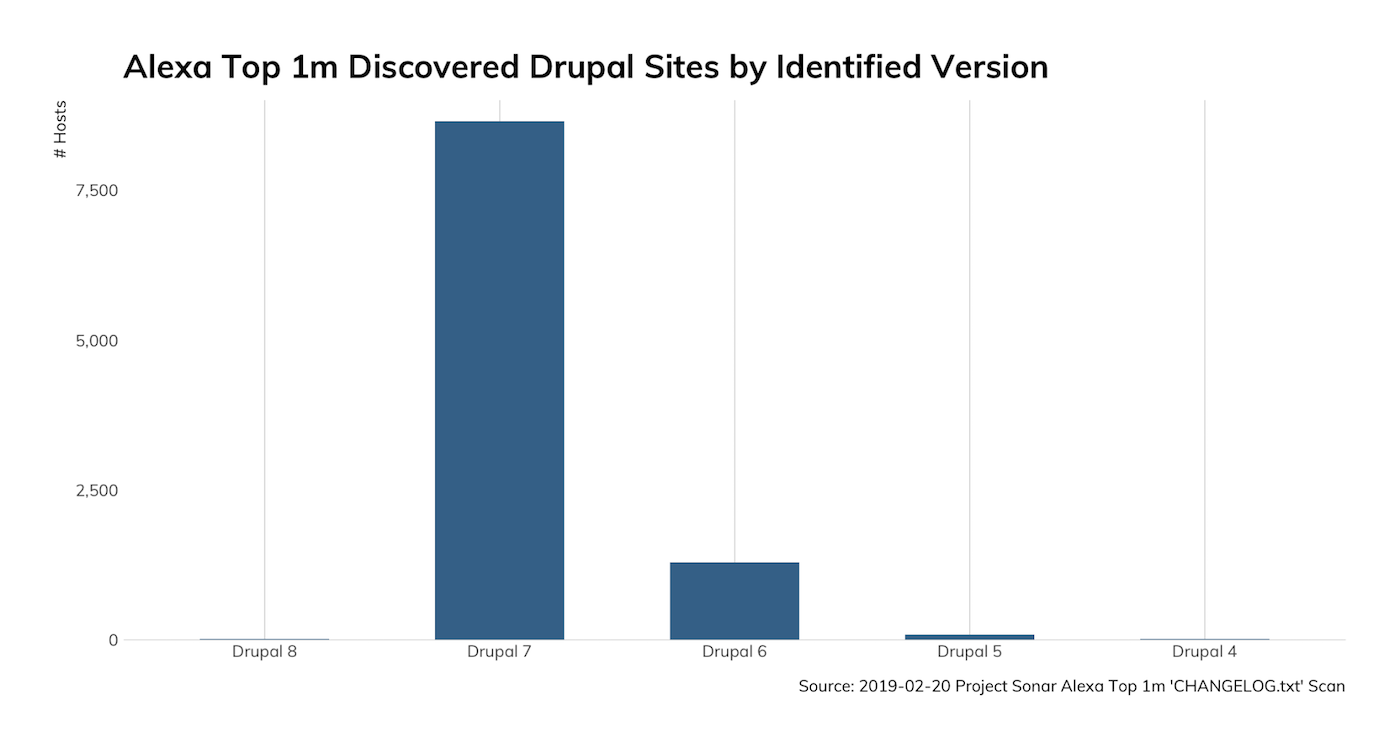
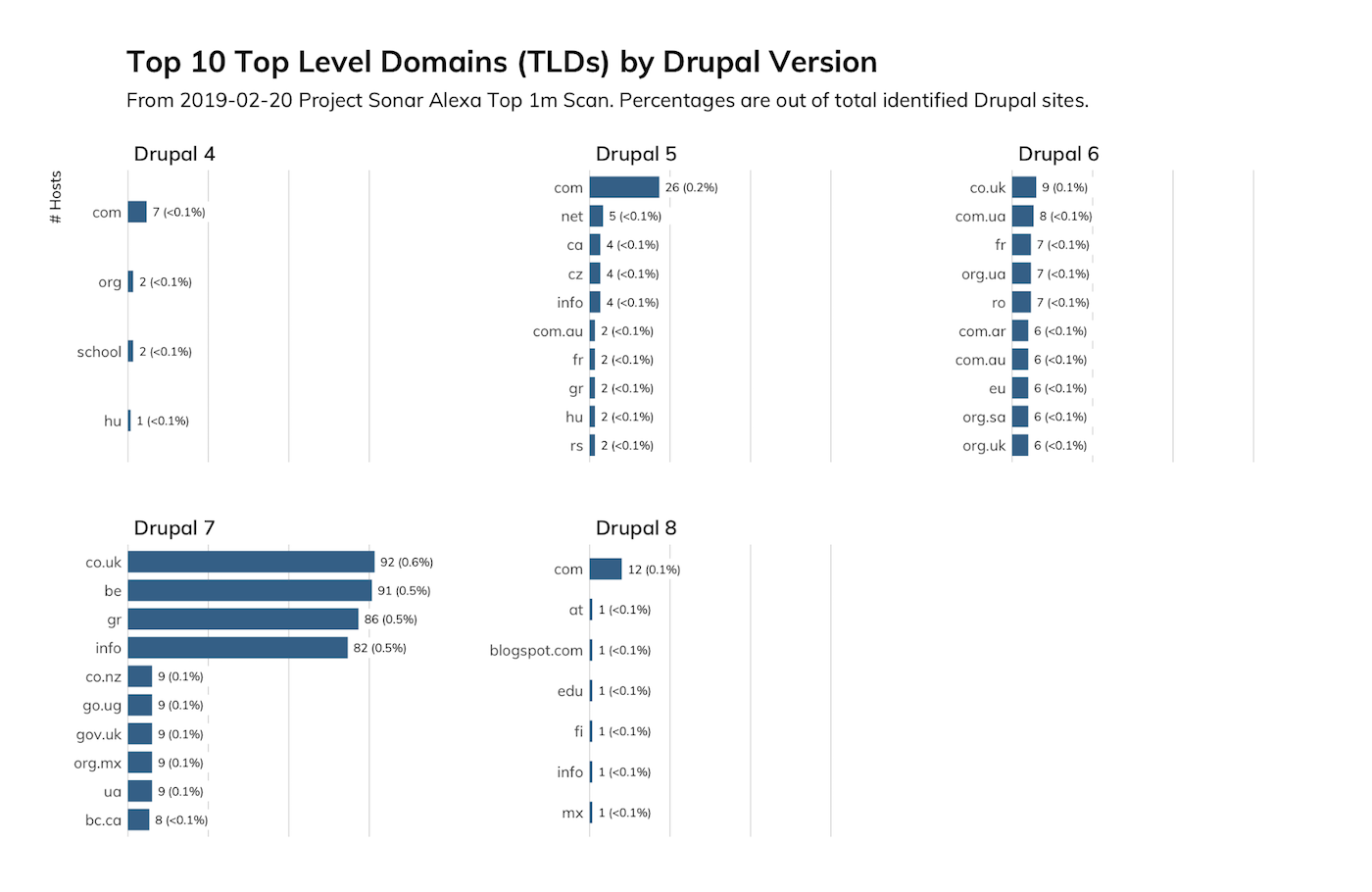
Remember, this uses headers and an exposed CHANGELOG.txt file, so there could be more sites running Drupal in the Alexa Top 1m than identified here.
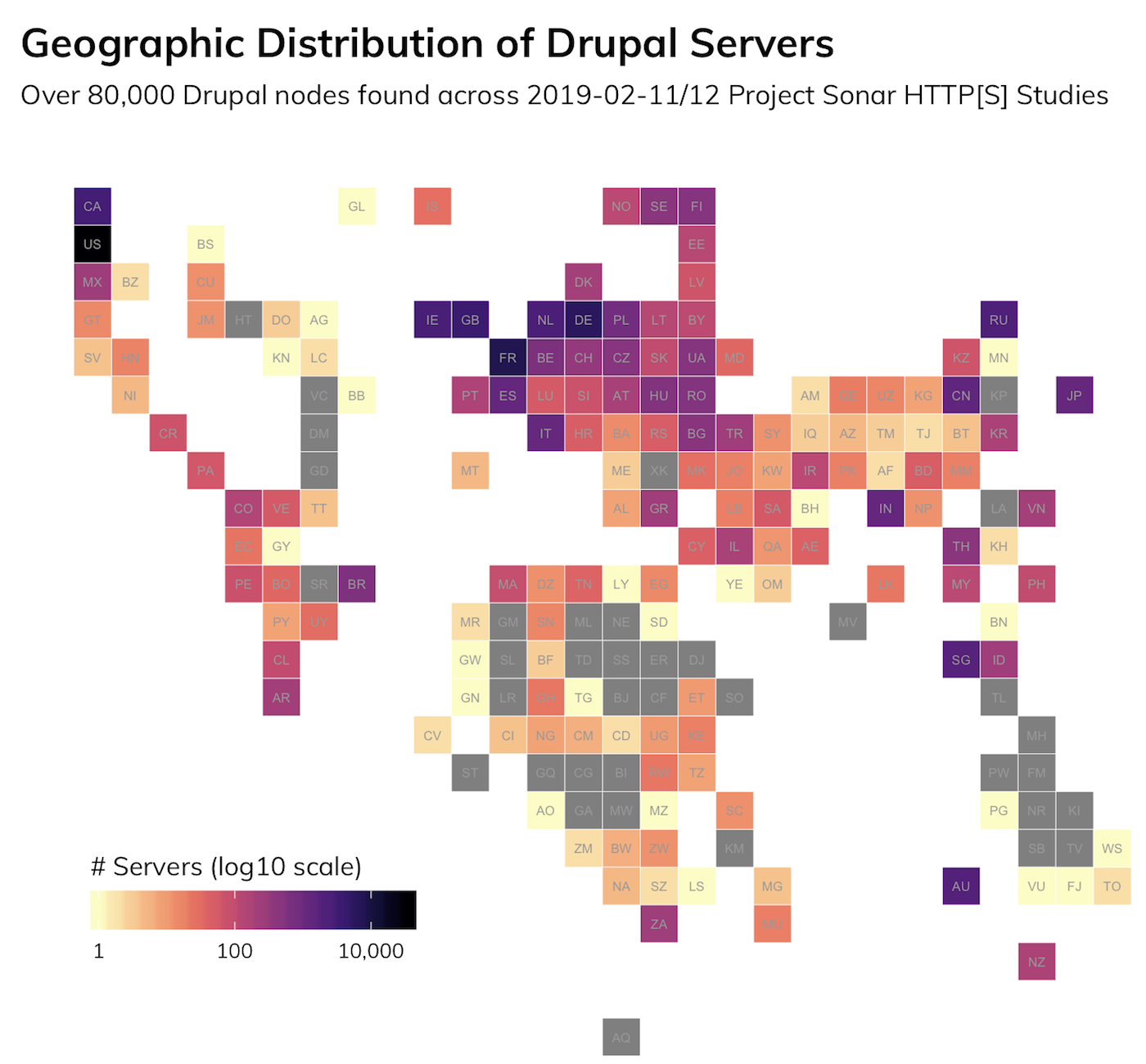
When we loosen the search to all likely Drupal nodes in Project Sonar ports 80 and 443 studies from earlier in February, we find over 80,000 servers scattered across the internet.
Rapid7 Labs has not seen any Drupal-related PUT/POST/PATCH activity since the release of the patch.
Is there InsightVM coverage?
We will be releasing a vulnerability check in our vulnerability management solution, InsightVM, for CVE-2019-6340 in the Thursday, Feb. 21, 2019 VM content release.
Is this vulnerability present in your environment? Find out with a free InsightVM scan.
Get StartedImage source: Ixis IT / Flickr
