Chess is the oldest skills game in the world, dating back to the 6th century AD. Because the mindset you use to win at chess is the same one you should strive for as an information security professional, you can learn a lot by examining the rules, players, and strategy behind this game. After all, the main goal of vulnerability management is to protect your assets in the same way you maneuver your chess pieces around the board to protect your king.
In our latest webcast, we teach you how to think strategically about your information security and vulnerability management program as you would a chess game so you can win against your adversaries. Below is a brief recap.
Protecting the king in your vulnerability management program
In the game of chess, the king is the most important piece—if you lose him, you lose the game. That’s why it’s your goal to protect the king at all costs. Ask yourself who the king is in your environment. Is it your data? Your infrastructure? Think about what could bring down your business if it were compromised. That is your king and what attackers are targeting.
Your queen serves as the protector of these targets. In vulnerability management, you as an information security professional are the queen.
The three phases to a vulnerability management strategy
The game of chess is divided into three distinct phases: the opening, middle, and end. Each phase requires a different strategy. In some cases, a game can move straight from the opening to the end, which is what attackers aim for. You need three things in place at the opening of the game to succeed: strategy, controls, and to shelter and protect the king.
Take the cyber kill chain as a model for this. Originally implemented as a military concept and adopted for information security purposes, it’s a way to model intrusions on a computer network. By understanding the steps an attacker takes to compromise your “king,” you can take proactive steps to keep it safe.
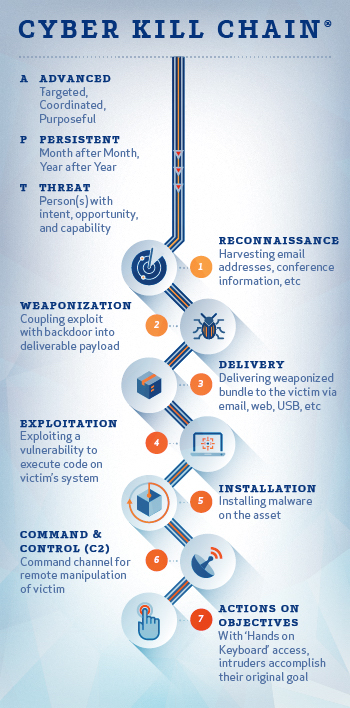
Following this chain of events, adversaries identify a vulnerability in your environment, develop “weapons” to exploit those vulnerabilities (e.g., malware and viruses), and deliver the weapon to execute the exploitation. A user falls victim, the weapon is installed, and attackers finally attempt to extract your data. If they succeed, they can call “checkmate.”
As a defender, you need to do the following to win at information security:
- Detect: Identify whether there’s someone suspicious snooping on your network.
- Deny: Prevent information disclosure by disallowing people from gaining access.
- Disrupt: Change how someone can gain access to information.
- Counterattack: Interfere with command and control to block them.
The roles you’ll need to assess and manage vulnerabilities
There are 16 total pieces on a chessboard. We’ve already defined the king and queen, but there are two other important roles to consider: the bishop and the knight.
The bishop provides protection, learning from others’ mistakes so you can make good decisions without having to make those same missteps. Your bishop could be threat intelligence from the infosec community, employees with past security experience, and even the security maturity model.
The knight is responsible for getting you the support you need, advocating for you and providing defense. Your knight could be support staff, security software, and so on.
With the proper roles defined, you can effectively mobilize your security and defenses and position yourself to win.
Threatening moves to watch for
Because chess is all about strategy, it can evolve (much like cyber-threats). There are also a multitude of moves to be aware of. In security, you have to be prepared for internal threats, external threats, IoT vulnerabilities, nation-state attacks, compliance requirements, and employee churn, among other elements. All of these can pose a security challenge and must be on your radar. At any given moment, one of these can make a strategic move to compromise or challenge your vulnerability management program.
Following the CIS Controls is a good way to be prepared for all of these. These controls help you continuously identify, remediate, and minimize the window of opportunity for attackers. Because we’re in a state of constant information, the controls help you get a handle on everything from software updates to patches to threat monitoring so you can stay ahead without drowning.
If you don’t know it exists, you can’t protect it
Especially with a sprawling, constantly expanding environment, it can be hard to determine what data is most important and which threats are worth pursuing. InsightVM, Rapid7’s vulnerability management solution, can help you gain visibility by showing you the IP address, hardware, host type, operating system, and when an asset was last scanned so you have a handle on everything that’s out there. It will also show you your Active Risk Score, which is calculated by taking into account CVSS but then going much further to to add critical context such as how exploitable a vulnerability is, how old it is (the older it is, the more likely it will be compromised), whether Metasploit modules or malware kits are available to take advantage of it, and the criticality of the asset to your business. The higher the score, the more urgent it is to remediate. This alone can go a long way toward helping you make the right moves to protect your king.
Having the ability to know where your data is and who can access it, log all activity, guard your perimeter, reduce access, and stay on top of vulnerabilities are crucial for winning at the game of cybersecurity.
