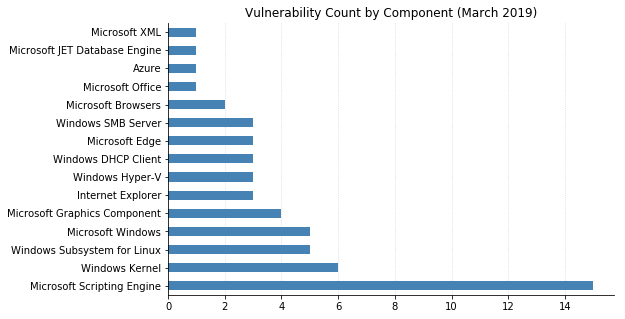
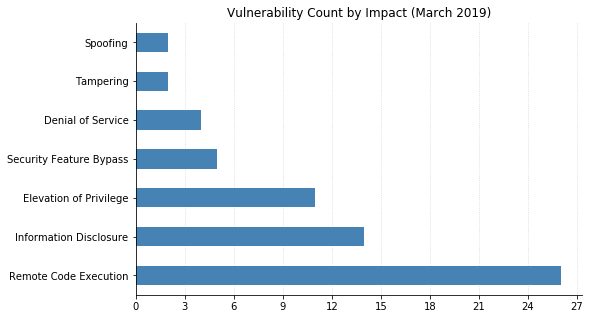
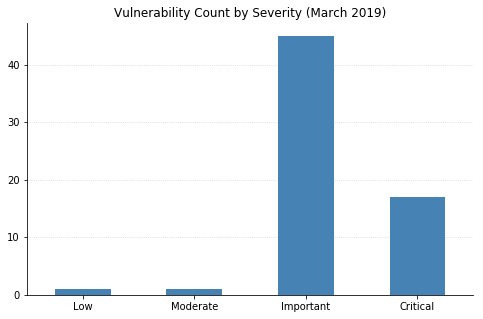
Today Microsoft released updates that resolve over 60 different vulnerabilities. As usual, Windows, web browsers, and SharePoint Server are all affected. Office gets off relatively lightly with only a single vulnerability fixed (CVE-2019-0748, a remote code execution (RCE) vulnerability in the Access Connectivity Engine of Office 2010).
Notably, this month's Adobe Flash update does not contain any security fixes. Microsoft still published ADV190008, which references the Adobe advisory APSB19-12. Apparently Microsoft is so accustomed to pushing out security updates for Flash every month that they created a security advisory out of habit. (More likely: it's an automated process.)
Three critical flaws in the Windows DHCP client that could allow RCE have been fixed (CVE-2019-0697, CVE-2019-0698, and CVE-2019-0726) and should take immediate priority for patching. Any systems running Windows Deployment Services TFTP Server should also be patched against CVE-2019-0603 as soon as possible.
There are two vulnerabilities that have been seen exploited in the wild, both of which allow elevation of privilege on Windows systems (CVE-2019-0797 and CVE-2019-0808). Although not as severe due to requiring local access, they could be used in conjunction with an RCE exploit in order to take full control of a system.
Four of the vulnerabilities patched today were previously disclosed prior to today's releases. Two are of particular interest to developers:
CVE-2019-0809 (Visual Studio Remote Code Execution Vulnerability, affecting the Visual Studio C++ Redistributable Installer) and
CVE-2019-0757 (a NuGet Package Manager Tampering Vulnerability, which affects installations on Linux and Mac). Also relevant to developers (among others) are the numerous privilege escalation vulnerabilities in the Windows Subsystem for Linux.
The other two publicly disclosed vulnerabilities are CVE-2019-0683 (Active Directory Elevation of Privilege Vulnerability) and
CVE-2019-0754 (Windows Denial of Service Vulnerability).
Microsoft also released important updates for older versions of Windows (Server 2008, 2008 R2, and Windows 7) that do not directly address vulnerabilities, but add SHA-2 code signing support. Without the patches published under the ADV190009 advisory, systems will no longer be able to receive security updates later this year.
Microsoft currently signs their product updates using both the SHA-1 and SHA-2 hash algorithms. These are meant to be one-way transformations that can be used to validate that the updates came from Microsoft and were not tampered with by a third party. Over the last several years, cryptography researchers have found various weaknesses in SHA-1 that make it easier to find "collisions" -- opening up the potential for someone to craft a different, potentially malicious update file that looks legitimate to Windows Update. To safeguard against this, Microsoft will start using SHA-2 exclusively after July 2019.
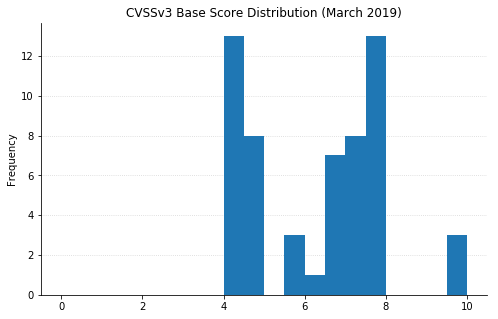
Note: not all CVEs had CVSSv3 data available at the time of writing
