We all love spending our weekends in a variety of ways—it reveals who we are and what we care for. At Rapid7, we have a lot of passionate folks who love to explore the unknown. During one such weekend meetup, we took part in the South Bay (SB) WASP, a cybersecurity lab meetup that delves deeply into technical concepts and hands-on skills. It’s a great learning atmosphere, where you only need a ready-to-learn self and a decent laptop to participate, and group members are always happy and willing to set you up for hands-on web application exploitation and network penetration testing.
This week, we're going to talk about a Capture the Flag (CTF) with a special blue-team element. Much like the game of our youth, this CTF had two opposing teams ransacking each other's environment for flags.
The blue-team technology was InsightIDR, our for modern detection and response. Red-team contestants knew that InsightIDR was monitoring the network but were unfamiliar with the product. InsightIDR has behavioral detections (MITRE ATT&CK mapping available under NDA) but also has some deception technology—including honeypots, honey files, and honey credentials—that add novel detection opportunities.
Related blog: How InsightIDR’s deception technology detects intruders in the attack chain
In this post, we’ll analyze the CTF and judge what InsightIDR was able to spot!
The rules
Red team skills
- Knowledge of common vulnerabilities in the wild and how to scan a network
- Laptop with Kali or similar OS prepared with appropriate tools
- Curiosity and willingness to find the holy grail
Blue team skills
- InsightIDR analyzing user and endpoint data (including Insight Agent)
- Deception technology deployed (honeypots, honey credentials, honey files)
- Range of Rapid7 staff experienced with red teaming, security analytics, and SIEM
CTF objectives (attack scope)
- A /24 subnet was provided to the attacker or red-team group prior to the engagement. Within this IP range lay obstacles that can ensnare attackers, including honeypots intermingling between web servers. The Insight Agent, honey files, and honey credentials were also active in the environment.
Act 1: InsightIDR detects reconnaissance
To kick things off, an attacker needs to enumerate this network to find the services and target hosts available for the taking. Available tools included Nmap and Masscan. Defenders can gain visibility here with honeypots—in this case, a virtual appliance (.ova) file easily stood up in the vSphere.
With scan results, the attacker understands the responsive hosts and services and can prioritize where to go next. Defenders are alerted to this activity with honeypots feeding into the cloud SIEM. You can see NMap triggering the honeypot below. Even at this early stage, responders can take appropriate action:
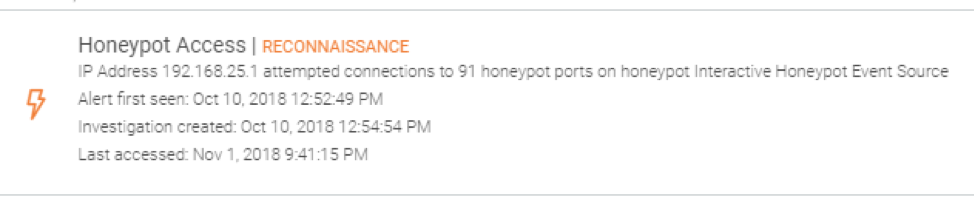
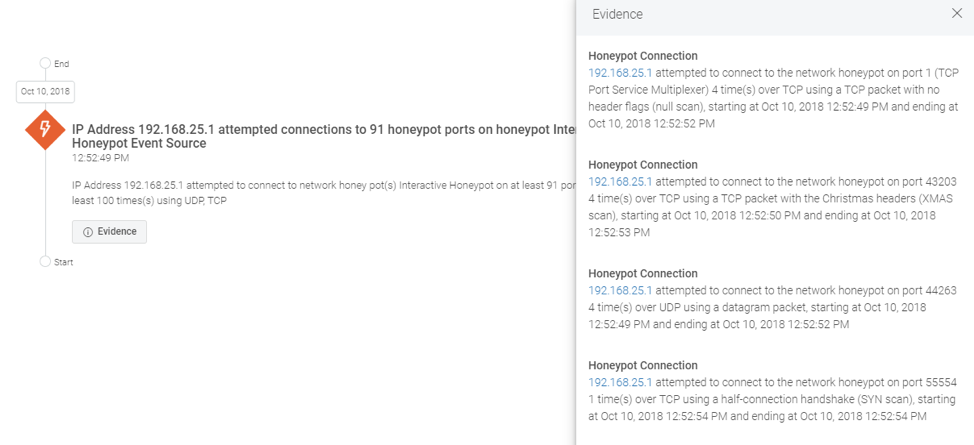
Act 2: InsightIDR detects lateral movement
Attackers found an IP address with port 80 open, leading them to a running web server. Once it was discovered that port 80 was running the latest version of Apache, folks started scanning and enumerating to find more. This included tools like the web content scanner DIRB and the brute-forcing Gobuster.
From the cloud SIEM, plenty of alerts were firing, informing potentially malicious behavior on the network and . One of the servers was a trap, unbeknownst to the attacker, of course. When users attempt to connect to it, it simply shows a 404 error response. Since we want to know whenever this 404 takes place, InsightIDR tails this server's log files and fires on the custom alert we created identifying this pattern.
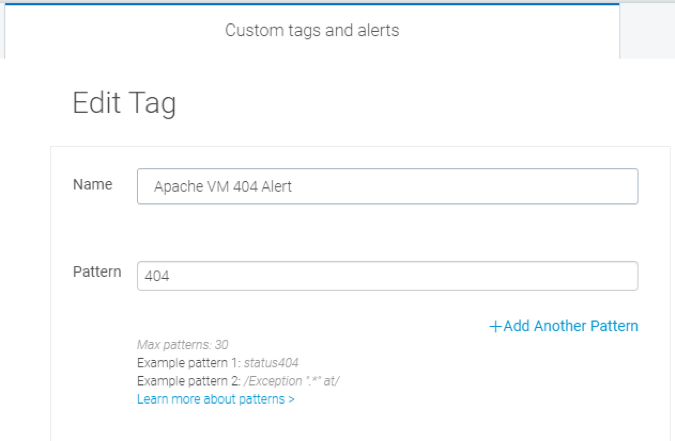
Custom alert: When HTTP response code “404 error” appears in a specific web server log, open an investigation.
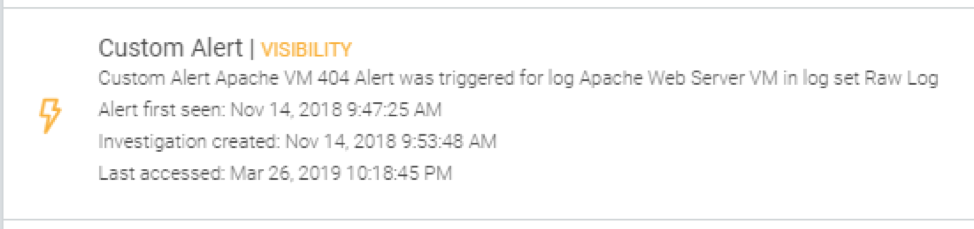
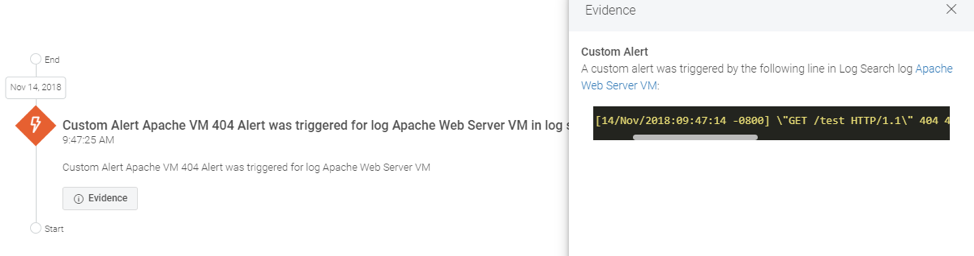
At this point, the blue team can quarantine the asset—even from within the cloud SIEM. But, let’s assume the worst and let the attacker continue to traverse the network. What will happen next?
Act 3: InsightIDR detects brute-force attempts
The next set of tracks revealed by InsightIDR were brute-force attempts against port 3389, which had open login pages on several web servers. Several folks began brute-forcing the SMB shares. The Insight Agent, which supports Windows/Mac/Linux, highlighted this activity, as well as anomalous file-level activity on the endpoint.
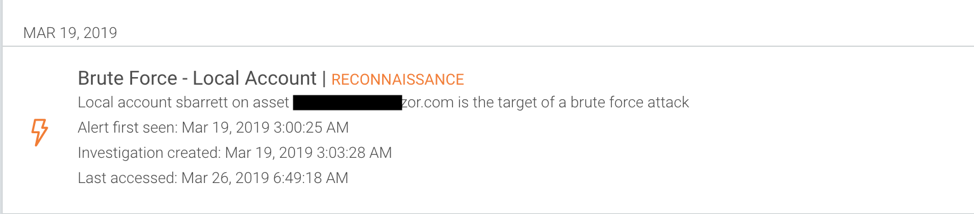
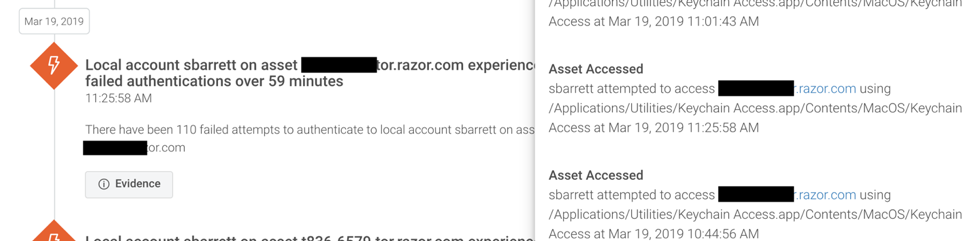
Act 4: InsightIDR detects data collection
Attackers found many accessible directories on the web server, and thus began the search for PII, passwords, and/or more valuable targets. The holy grail, the ultimate treasure, is of course Domain Admin-level credentials with which to pwn the network.
The blue side has added monitoring opportunities to catch these highly anomalous behaviors with features like honey files, honey credentials, and honeypots. Since several servers were honeypots, those alerts fired, but honey files also played a hand in capturing these smooth criminals.
Here’s one of the honey file alerts and presented evidence:
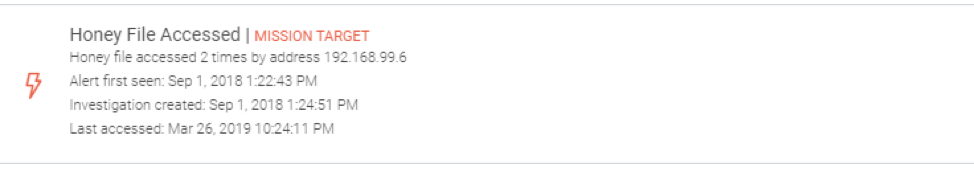
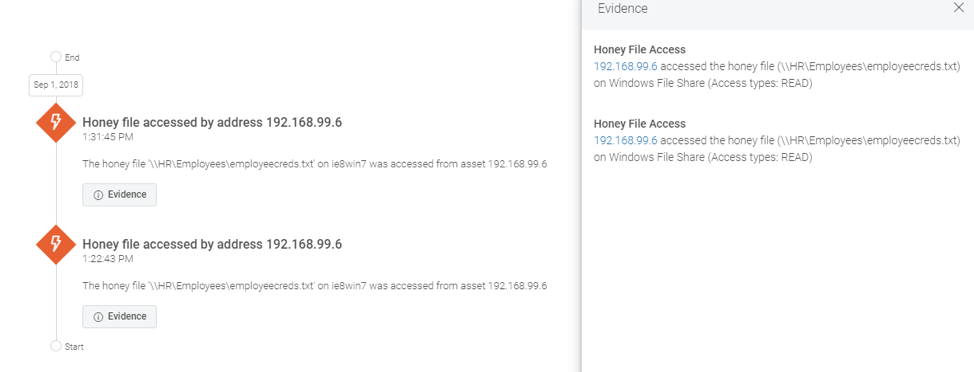
Final results
If someone tripped up a certain number of alerts within InsightIDR, they were prodded to hightail it out of there, disconnecting from the network and traversing any fences necessary to escape the compound. Deductions were given for scored flags that triggered alerts.
Overall, most red teamers were unable to make it through all of the obstacles and landmines set by the defenders. One of our established engineers, who also co-organizes the SB WASP meetup, shared great lessons learned, CTF advice, thoughts on attacker behavior, and how InsightIDR can help. In the end, the winners were everyone who participated, as its purpose was learning, understanding the tools of the trade, and understanding what attackers think when traversing through the network.
Have you participated in a red-team exercise with an active blue-team component? Would you be interested in attending one? Share your thoughts in the comments.
