Since it’s impossible to absolutely prevent all threats, it’s important to have the ability to detect threats across your environment. In addition to thinking like an adversary, security analysts need to be creative in how their team monitors rapidly evolving cloud and on-premises environments, and ultimately how to achieve more with less. There’s one constant that continues to serve as a guiding light: It is increasingly critical to find and mitigate threats as early as possible in the attack chain.
“The time from the attacker’s first action in an event chain to the initial compromise is typically measured in minutes. Conversely, the time to discovery is more likely to be months.”
— 2019 Verizon Data Breach Investigations Report
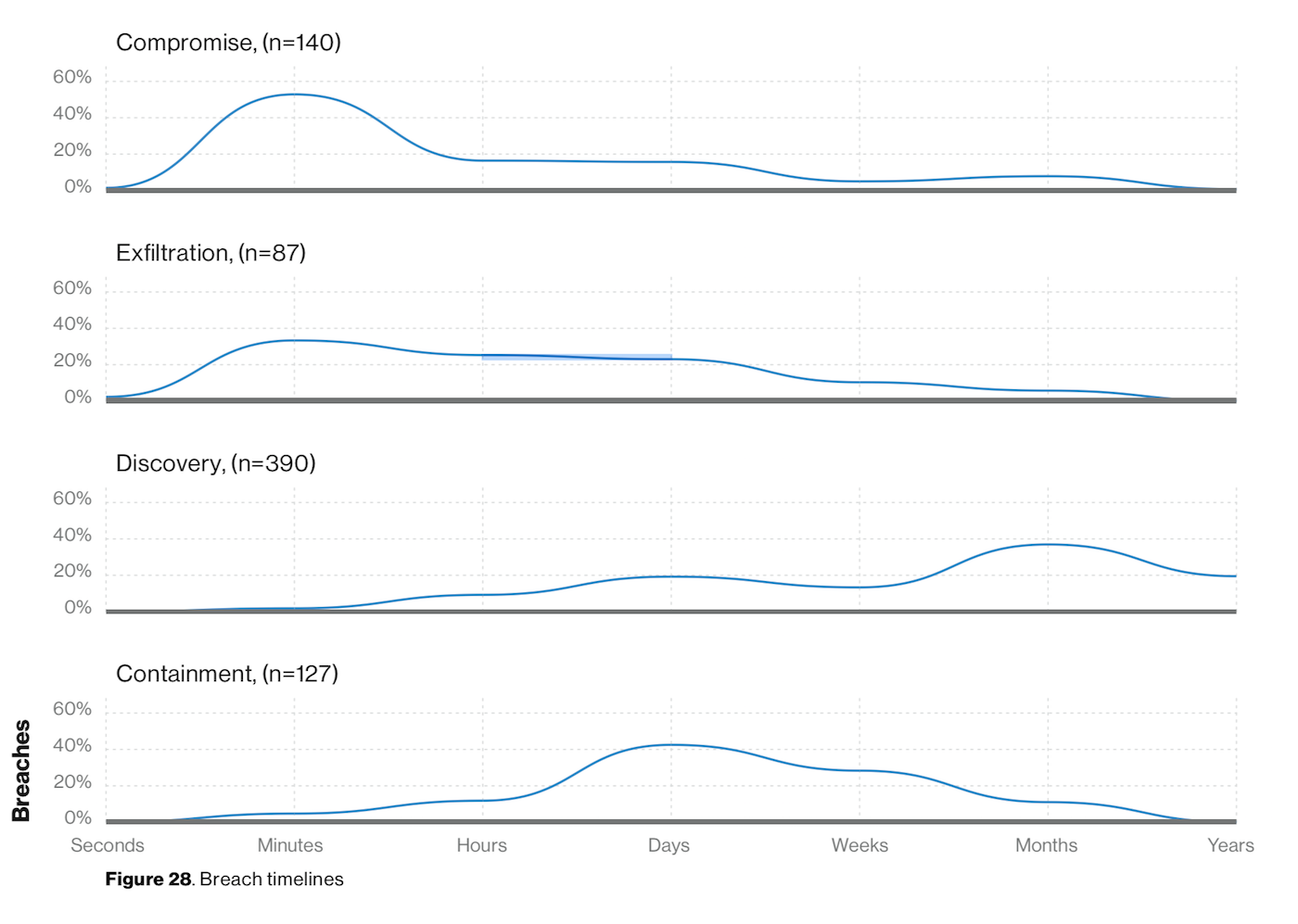
Source: 2019 Verizon Data Breach Investigations Report
The importance of detecting attacks early in the attack chain
Stolen credentials continue to be the top method attackers use to gain initial access to an organization—gaining access to privileged credentials is a common goal and directly leads to lateral movement toward prized assets. In fact, the most recent Verizon Data Breach Investigations Report notes an increase in cybercrime targeting senior executives. Even if a compromised executive account doesn’t have admin privileges, further phishing from that account can lead to more credentials and/or shells via lateral movement.
For these reasons, monitoring user behavior, securing privileged credentials, and identifying attacks leveraging privileged access is more essential than ever. To help address this growing need, we’re thrilled to be teaming up with CyberArk to integrate its Privileged Access Security Solution with our cloud SIEM, InsightIDR. Shared customers now can get consolidated visibility of privileged access activity in a single interface.
How the InsightIDR/CyberArk integration works
Once CyberArk audit logs and alerts are forwarded to InsightIDR, they can be automatically structured, making it easy to search, visualize, and build custom alerts for your organization’s privileged access activity. The combined context of the CyberArk Privileged Access Security Solution and InsightIDR User Behavior Analytics offers rich details and depth for investigating suspicious behavior and protecting these valuable accounts. The joint solution offers enterprises the ability to take a risk-based approach to the most critical happenings and alerts within the network by introducing remediation capabilities including:
- Automatic credential rotation, and real-time rotation for risky accounts
- Continuous scanning of the environment to detect and onboard unmanaged access
- Programmatically suspend or terminate sessions where risky commands and/or
- anomalous behavior is occurring
- Kill malicious processes and quarantine infected endpoints
There are thousands of alerts that the Security Operations Center (SOC) receives every day. This enables the SOC to not only detect risky activities, but also take automatic action based on requirements and/or policy, further permitting them to focus on the most critical activities and not
spending time sifting through endless amounts of logs, data and alerts.
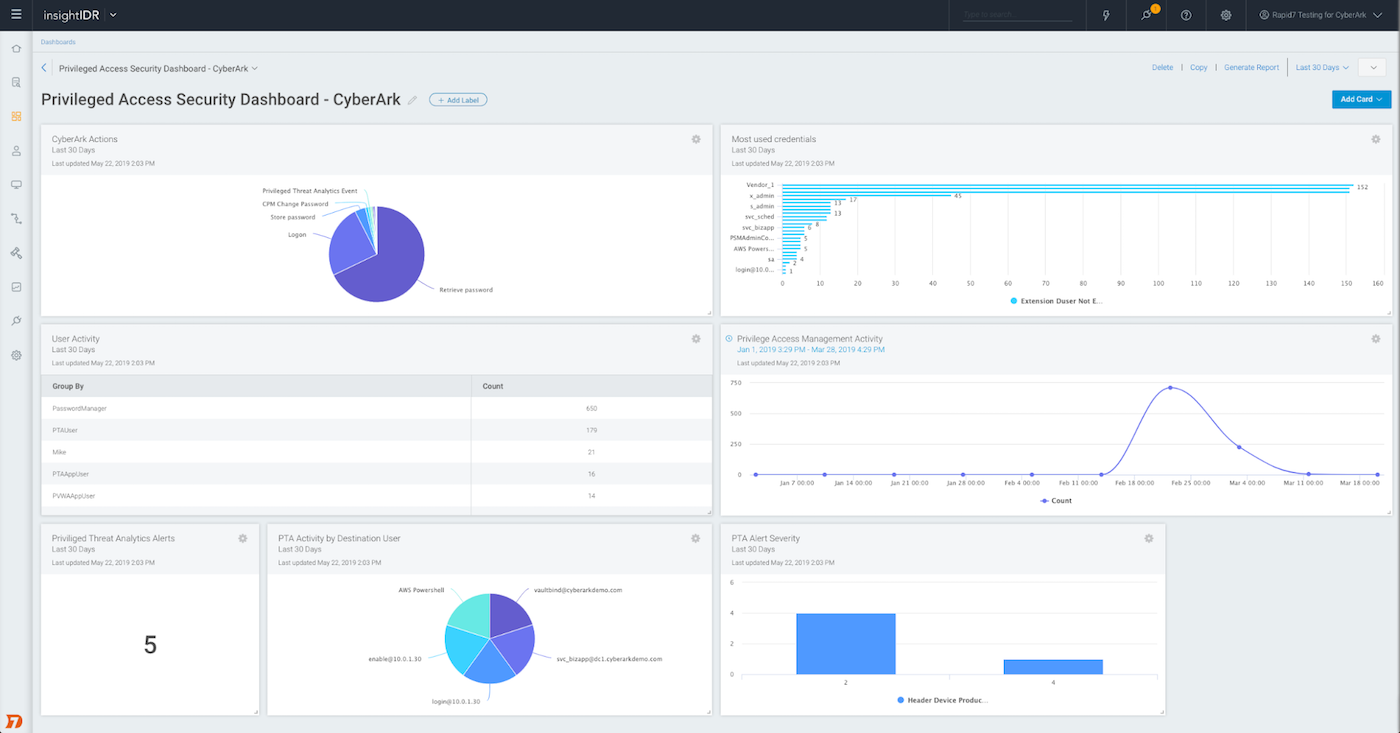
CyberArk data on privileged access presented as visual dashboard cards in InsightIDR.
It’s also worth noting that this automatic log structuring is available to apply to any JSON and CEF logs you may be forwarding to InsightIDR, to help you get the most from your data. For example, automated log structuring can be leveraged for parsing Windows event codes and other event data, to help more easily query on these logs, or create custom alerts or visualizations.
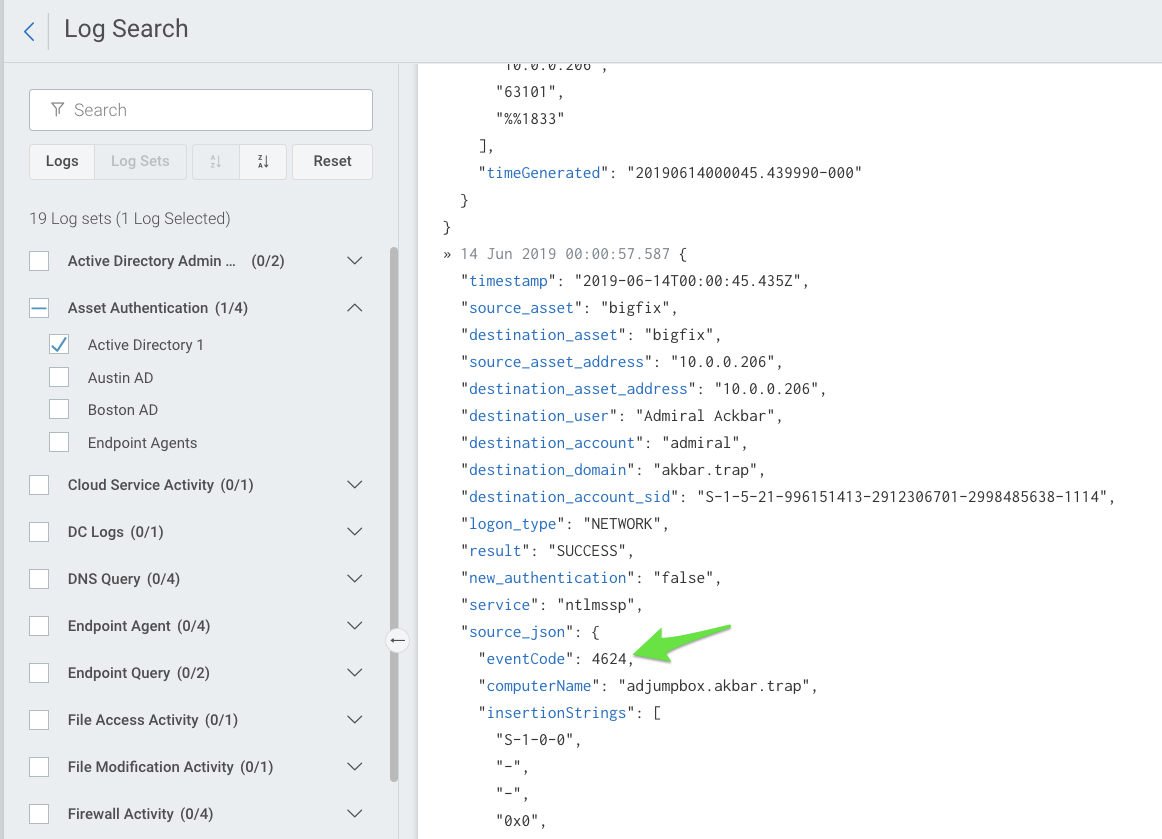
To leverage this feature, simply navigate to settings within InsightIDR, then on the Automatic Log Structuring tab, toggle the feature to “on.”
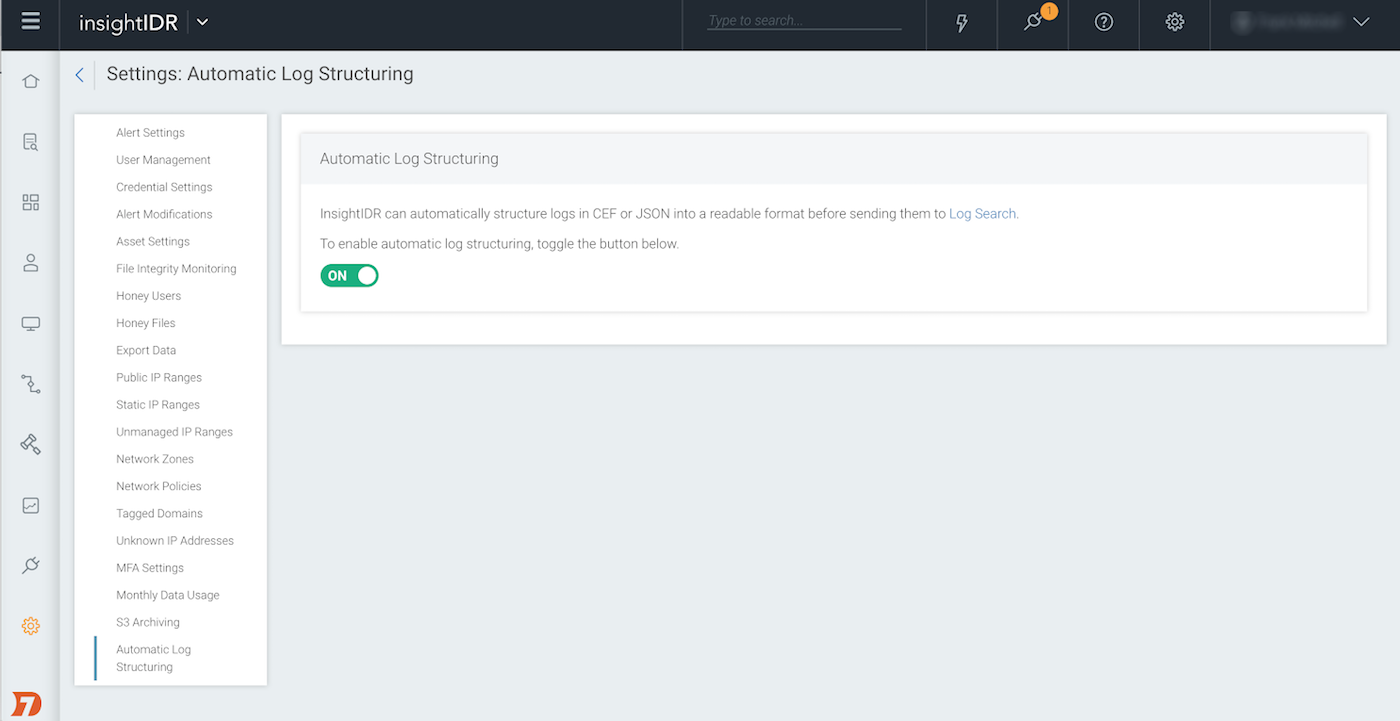
See more on leveraging automated log structuring here.
We look forward to your feedback on these exciting new capabilities. Also, be sure to check out our recent blog on InsightVM’s integration with CyberArk and how it can help your organization better block user access to vulnerable assets.