I am Root
An exploit module for Nagios XI v5.5.6 was added by community contributor yaumn. This module includes two exploits chained together to achieve code execution with root privileges, and it all happens without authentication. A single unsanitized parameter in magpie_debug.php enables the ability to write arbitrary PHP code to a publicly accessible directory and get code execution. Privilege escalation happens through the combination of a command injection vulnerability in the autodiscover_new.php file and the ability to execute that same file with sudo without supplying a password.
Enumerate all the Things!
Our very own asoto-r7 contributed three modules to enable enumeration of useful Amazon Web Services (AWS) information. With an ACCESS_KEY_ID and a SECRET_ACCESS_KEY handy, you will be able to find EC2 instance information, IAM user accounts, and S3 bucket info.
SilentCleanup UAC Bypass
Community contributor cbrnrd added a Windows exploit module that returns an elevated session. The SilentCleanup task in the Windows Task Scheduler executes a file whose path contains a user-controlled environment variable all while running with elevated privileges. The environment variable can be changed to a new value, thus enabling the execution of arbitrary code with elevated privileges.
A New Diary Entry
Dear diary,
Today I had unauthenticated remote root with a side of Ghidra reversing.
Last quarter we introduced a new series called the Metasploit Development Diaries. Dev diaries shed light on how vulnerabilities and exploitable conditions (whether true bug, feature, or foreverday) turn into full-fledged Metasploit modules. In this quarter’s development diary entry, William Vu takes a deep dive into the exploit and underlying vuln for a buffer overflow in the Cisco RV130 VPN router. The write-up even includes some reversing with Ghidra. Earlier this year when this vulnerability was first announced, Rapid7 Labs’s investigated the exposure of affected Cisco devices and found nearly 12,000 affected devices exposed:
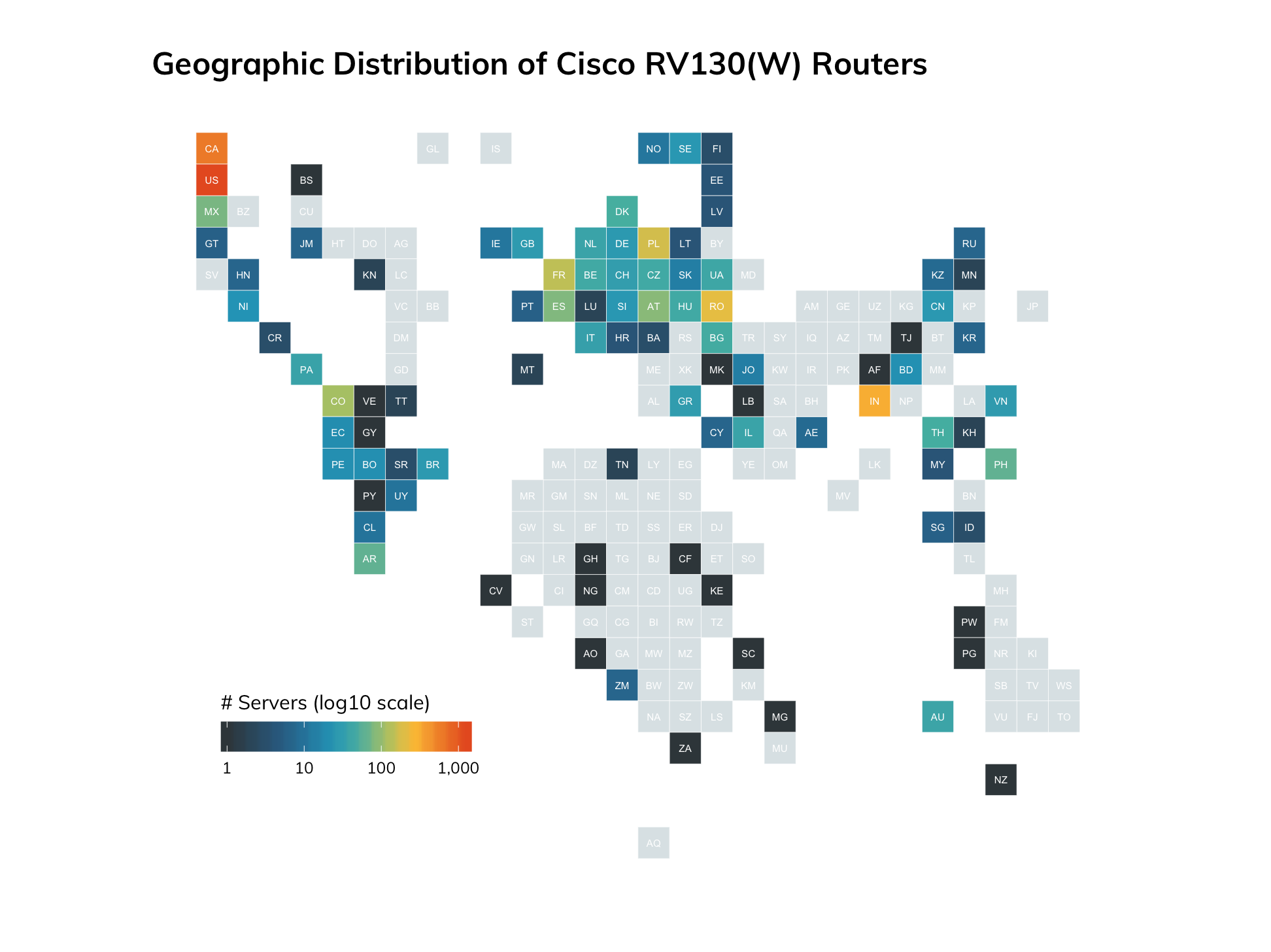
Read this quarter’s dev diary and more Rapid7 research here.
New modules (5)
- Nagios XI Magpie_debug.php Root Remote Code Execution by Chris Lyne and Guillaume André
- Windows Escalate UAC Protection Bypass (Via SilentCleanup) by Carter Brainerd (cbrnrd), enigma0x3, nyshone69, and tyranid
- Amazon Web Services EC2 instance enumeration by Aaron Soto
- Amazon Web Services IAM credential enumeration by Aaron Soto
- Amazon Web Services S3 instance enumeration by Aaron Soto
Enhancements and features
- PR #12008 by egypt ignores the response code returned while checking for the vulnerability in the exploit/multi/http/struts2_content_type_ognl module. This allows for more vulnerable targets to be detected.
Bugs fixed
- PR #12017 from community contributor aushack fixes an issue in exploit/unix/http/xdebug_unauth_exec that prevents a nil error in the case that HTTP headers aren’t returned in a response.
- PR #12013 by wvu-r7 ensures that the SRVHOST option in exploit/multi/http/confluence_widget_connector is a valid callback address.
Get it
As always, you can update to the latest Metasploit Framework with msfupdate and you can get more details on the changes since the last blog post from GitHub:
We recently announced the release of Metasploit 5. You can get it by cloning the Metasploit Framework repo (master branch). To install fresh without using git, you can use the open-source-only Nightly Installers or the binary installers (which also include the commercial editions).
