*This is the second in a three-part series discussing common threats, key data sources, and how the Rapid7 portfolio can help you secure cloud environments.
As your company expands its investment in cloud hosting and services, it’s easy for your team to want visibility, threat detection, and oversight. In this blog, we will talk about threat detection for the world’s most popular cloud host, Amazon Web Services (AWS).
Here are a few examples of attacks that target companies building on AWS:
- Steal AWS console credentials, secretly provision machines for cryptomining
- Steal sensitive data from exposed or compromised S3 buckets
- Compromise and use cloud hosts as an attacker pivot (e.g., DDoS or to obfuscate origin)
In previous posts, we’ve touched on the three categories of risk that underlie every successful breach: vulnerabilities, misconfigurations, and credentials. As cloud providers like AWS share responsibility on the operating system layer, the risk of vulnerabilities is reduced, as only up-to-date operating systems are used and the attack surface is minimized when using DevOps innovations such as containers and serverless computing.
Eliminating misconfigurations in cloud-based environments continues to be a challenge, especially in multi-cloud environments, where security staff need to understand multiple ever-changing consoles that power business- and mission-critical applications. If a host is misconfigured, there isn’t a high margin for error: from our Project Lorelei honeypot research, we’ve seen that internet-facing cloud hosts are probed by outside entities within seconds of deployment. It is increasingly important that permissions and network settings are configured correctly prior to first provisioning.
Finally, credentials, credentials, credentials. Given the cloud flexibility of anywhere, anytime access, it’s crucial to monitor credential usage and admin activity to detect compromised accounts as early as possible. To reduce the risk of breach, gaining visibility into AWS logins and actions is a great first milestone.
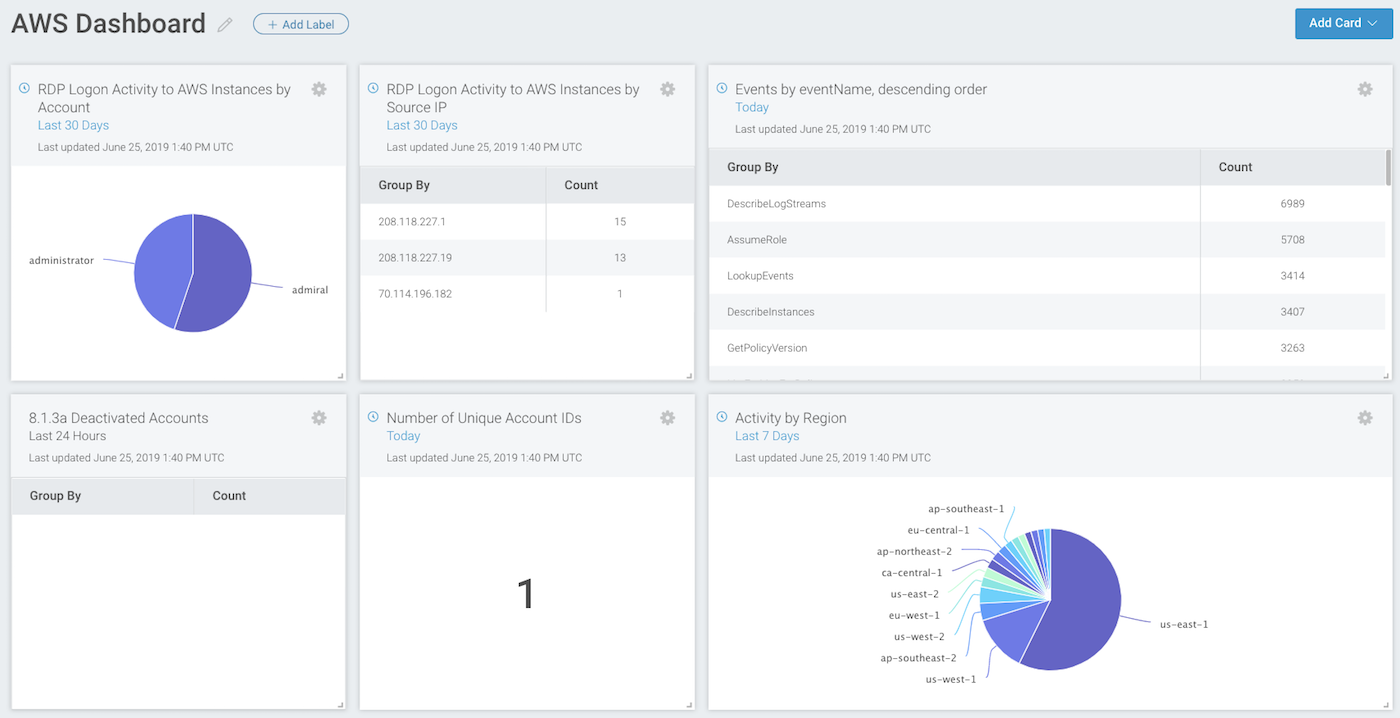
The most valuable source of truth to know who is doing what on AWS is AWS CloudTrail. This service can log activity including:
- Who is authenticating to the AWS console (including API calls)
- Which AWS regions and services are being used
- Compute resource provisioning
- File-level access into S3 buckets
Here are some other log sources that provide valuable investigative context and can feed into detection:
| Log Source | What It Tracks | Security Benefit |
|---|---|---|
| AWS CloudWatch | Application and infrastructure performance monitoring. “What is happening on AWS?” (as opposed to who). | Deeper visibility into applications, infrastructure utilization, and custom monitoring use cases. |
| Virtual Private Cloud (VPC) Flow Logs | IP traffic going to and from Amazon EC2 network instances in your VPC. | Identify intra-VPC port scanning, network traffic anomalies, and known malicious IP addresses. |
| DNS logs | Domain and subdomain queries that are routed through Amazon Route 53. | Match against threat intelligence to identify known-bad and quickly spreading threats. |
Securing AWS and multiple clouds with Rapid7
If you’re looking to simplify the complex and reduce your risk across vulnerabilities, misconfigurations, and credentials, we can help. InsightVM, our vulnerability management solution, helps you identify and remediate risk across your modern network—this extends beyond vulnerabilities to misconfigurations as well.
InsightIDR, our cloud SIEM, gives you centralized log management, detection for common and targeted threats, and the ability to directly respond with the context you need. This includes detecting the use of stolen and weak credentials, which continues to be the top attack vector across all confirmed breaches.
New behavioral detections in InsightIDR
We’ve just released three new detections that leverage our user behavior analytics engine to expose anomalous activity:
- New Region Usage: If you typically use us-east-1&2, you’ll get an alert on new activity happening in ap-southeast-1 or eu-west-2.
- New Service Usage: Alerts if a new AWS service (e.g. Lambda, CloudFormation, or any of the hundreds of services available) is being used for the first time.
- New Compute Usage: InsightIDR will alert you if a new type of virtual machine resource is provisioned, such as one optimized for mining cryptocurrency.
As a quick note, you can find and modify these alerts under Alert Settings → User Behavior Analytics. There is a two-week baselining period before these alerts fire in your environment.
These new detections are in addition to the existing user behavior analytics that gives you high-level ingress visibility and proactive identification of compromised credentials.
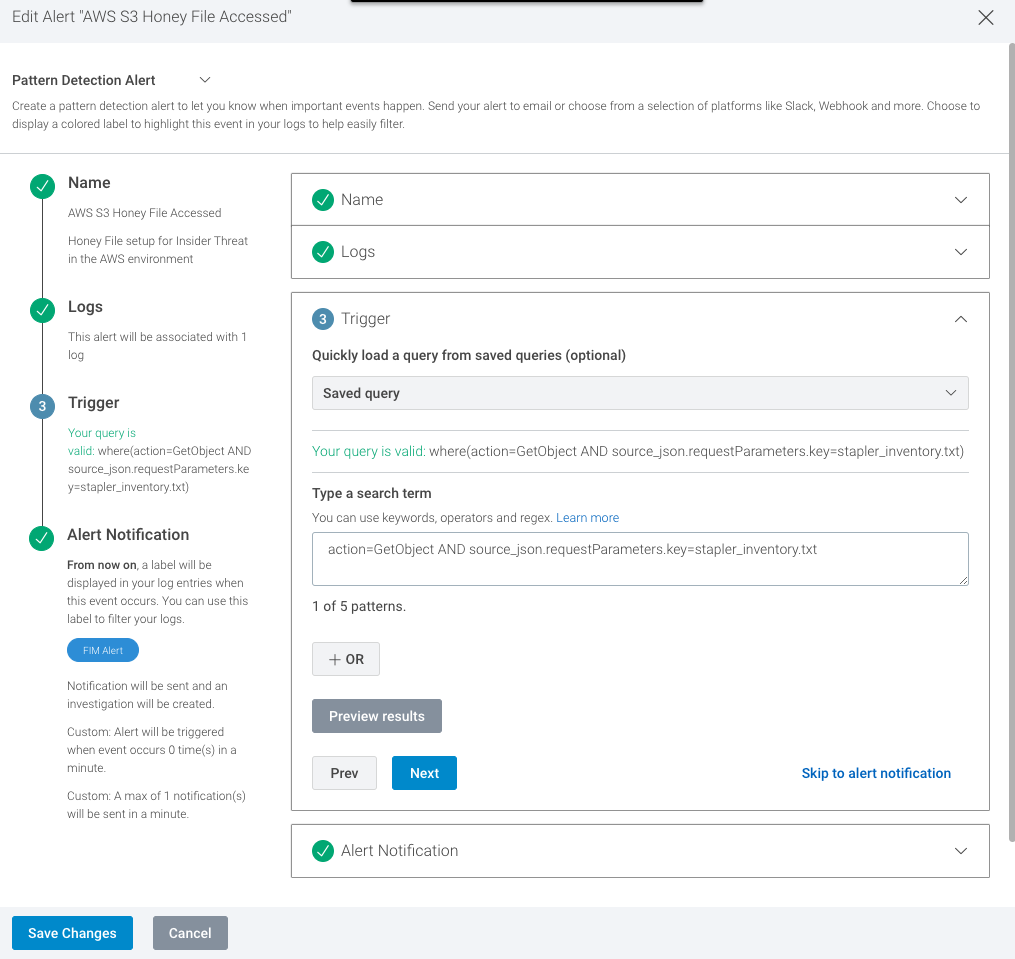
Outside of InsightIDR’s pre-built detections, you can build flexible custom alerts on AWS CloudTrail activity. For example, if you enable object-level API auditing for an individual S3 bucket, you can create a custom alert to notify if an object has been accessed, modified, or removed inside the bucket.
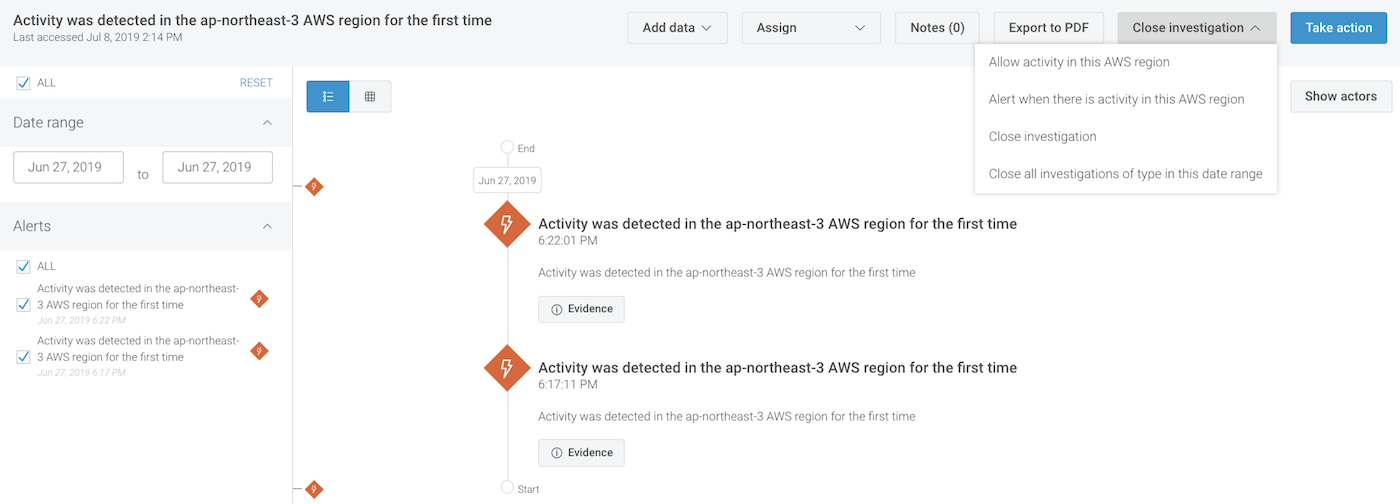
Finally, if you use AWS GuardDuty, those alerts can be fed into InsightIDR for a unified investigation and case management experience.
Therefore, if you’re building on AWS, send your CloudTrail data into InsightIDR! You’ll not only get log search and dashboard visibility, but also proactive detection for common cloud-based threats, including stealthy attacks that only use credentials.
