On the evening of July 8, 2019, security researcher Jonathan Leitschuh posted a disclosure on Medium, "Zoom Zero Day: 4+ Million Webcams & maybe an RCE? Just get them to visit your website!." However, it looks like the issues at play are a little more subtle then what this headline might suggest.
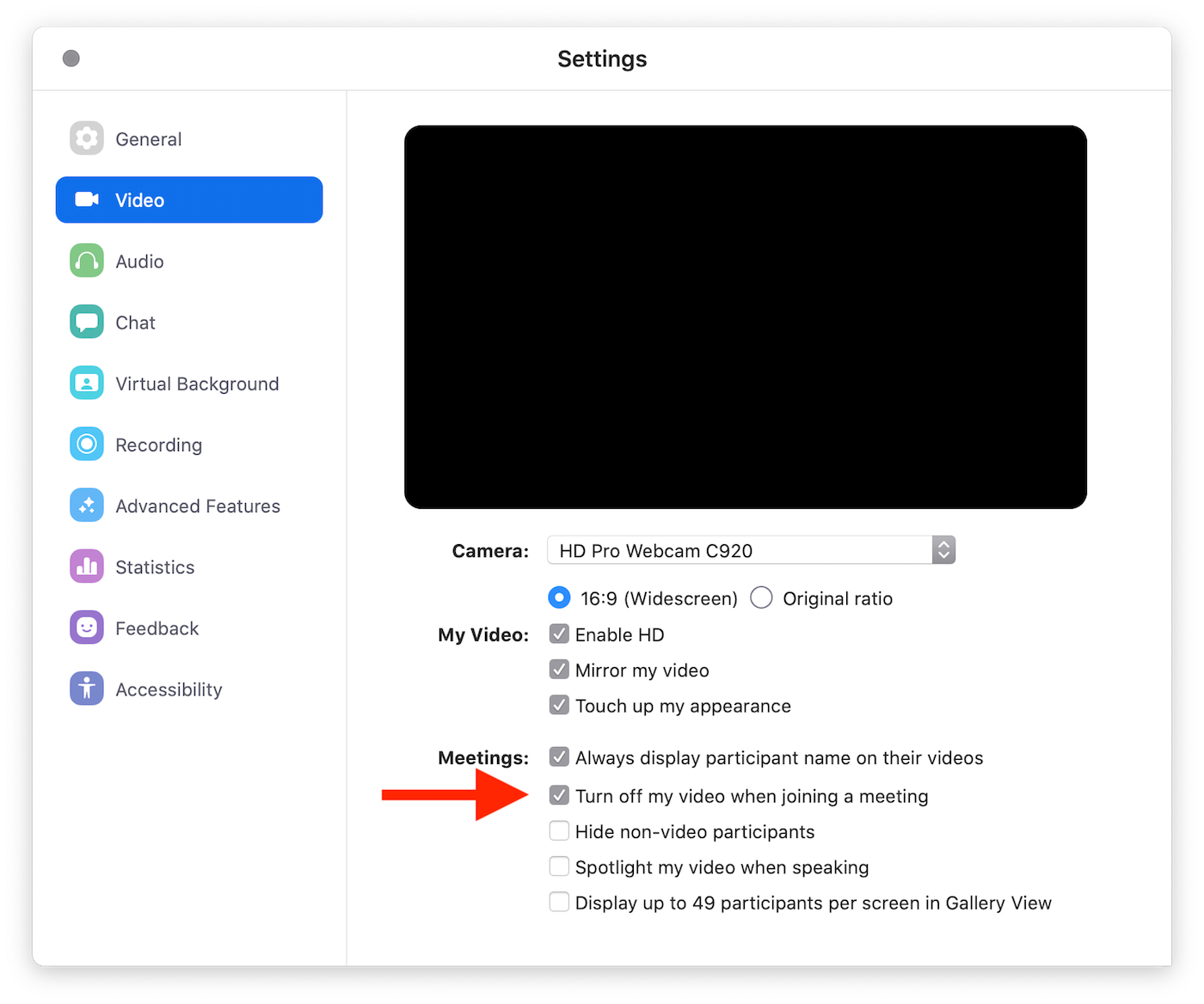
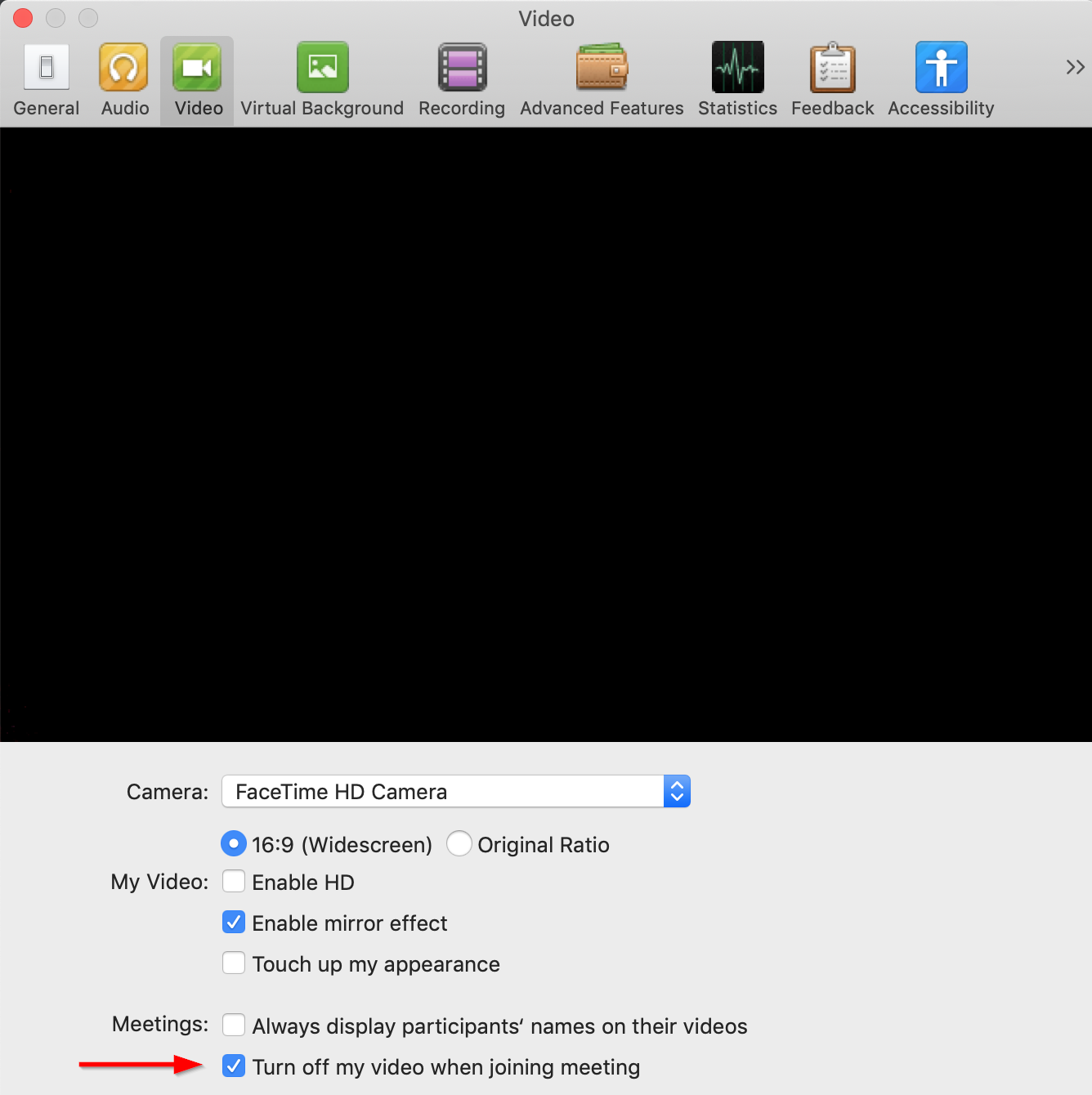
Here's the short story: On your Mac OSX, hit ⌘, (Command-comma), Video, then select "Turn off my video when joining a meeting." This will keep your webcam from firing up if someone tosses a Zoom meeting link at you through an iframe or javascript or something. Also, no, there's no (demonstrated) remote code execution (RCE) vulnerability. Also also, update your client.
The configuration screen will look something like this:
Or this:
The Zoom security flaw explained
The most exciting finding that Jonathan posted was that an attacker-controlled website can reach down into the localhost-bound web server and kick off a Zoom video conference without any practical interaction from the user, thanks to (in the case of Firefox and Safari) a relaxed Cross-Origin Resource Sharing (CORS) implementation, and (in the case of Chrome), a tricky way to bypass CORS. This sounds pretty bad, but this smells more like "surprising behavior" than a "vulnerability." Joining a meeting from such a link will kick Zoom into the foreground, so the attack isn't particularly subtle. Also, the webcam status light will be activated, so there's that indication that you're being watched. Finally, you can configure your way out of this with the Zoom client preferences, so I'm not even sure this video camera hijacking even qualifies as a "bug," but Jonathan did get a CVE ID for it, CVE-2019-13450, so the difference between "surprising behavior" and "security vulnerability" is pretty thin and ultimately academic at this point.
Less exciting is the denial-of-service (DoS) condition, where the Zoom client can continuously steal focus when a user browses to a specially crafted web page. That's CVE-2019-13449, and has been fixed in the latest version of the OSX client.
Middlest exciting is the fact that uninstalling the Zoom client leaves behind the localhost web server, running merrily away and listening on localhost:19421. This is where that "maybe an RCE?" part of the headline comes in—while Jonathan doesn't actually document or demonstrate a remote code execution (RCE) vulnerability, he does link out to a prior finding from Tenable that might have been used along with this sneaky localhost webserver business. As of this writing, though, this hasn't been demonstrated by anyone, and it's unclear right now what the link between CVE-2018-15715 (Tenable's bug) and CVE-2019-13450 (Jonathan's bug) might be.
All that said, leaving behind a running webserver is no bueno. Even if it's bound only to localhost (and thus, can't be reached directly over the local network or over the internet), left-behind cruft like this invariably increases attack surface, so that's not great. However, Zoom has indicated in their response that this will also be fixed in the next update. In the meantime, you can delete it yourself after uninstalling Zoom with a quick rm -rf ~/.zoomus from the Terminal.
Update
As of about 20:00 Boston time, Zoom is rolling out an update with the following release notes:
Release notes of 4.4.53932.0709
- Remove local web server. We are discontinuing the use of a local web server on Mac devices. Following the update, the local web server will be completely removed from the Zoom installation.
- Option to uninstall Zoom. Zoom users can now uninstall the Zoom desktop application and all of its components through the settings menu.
Well, that settles that, then.
Update (Again)
As suspected, there's RCE in there after all. The short story is, if you've uninstalled Zoom for Mac OSX (or any of its whitelabeled friends), but not totally uninstalled it, you may be vulnerable to CVE-2019-13567. This only affects OSX clients that had partially uninstalled Zoom. Functioning Zoom clients on appear to be unaffected by this vulnerability.
This bug was discovered privately back in March by the Assetnote team, and subsequently rediscovered by a few people since. More importantly, Apple's Malware Removal Tool (MRT) now automatically removes the vulnerable, lingering web server. So, if you're reading this after July 10, 2019, you're probably okay, regardless of the state of your Zoom installation (or uninstallation).

