Attacker activity
Rapid7 Labs has observed a significant uptick in malicious RDP activity since the release of CVE-2019-0708 (A.K.A. “BlueKeep”).
Figure 1 shows the total daily connections from known, non-benign sources. Current levels of malicious RDP activity are levels unseen since Rapid7 Labs deployed Project Lorelei back in 2015 and are well above the levels seen at this same time last year.
There were spikes just before the release of the CVE from both known adversarial internet IPv4 ranges and new sources that have a scanning profile consistent with nation state vulnerability assessment activity (those are not marked as “benign”).
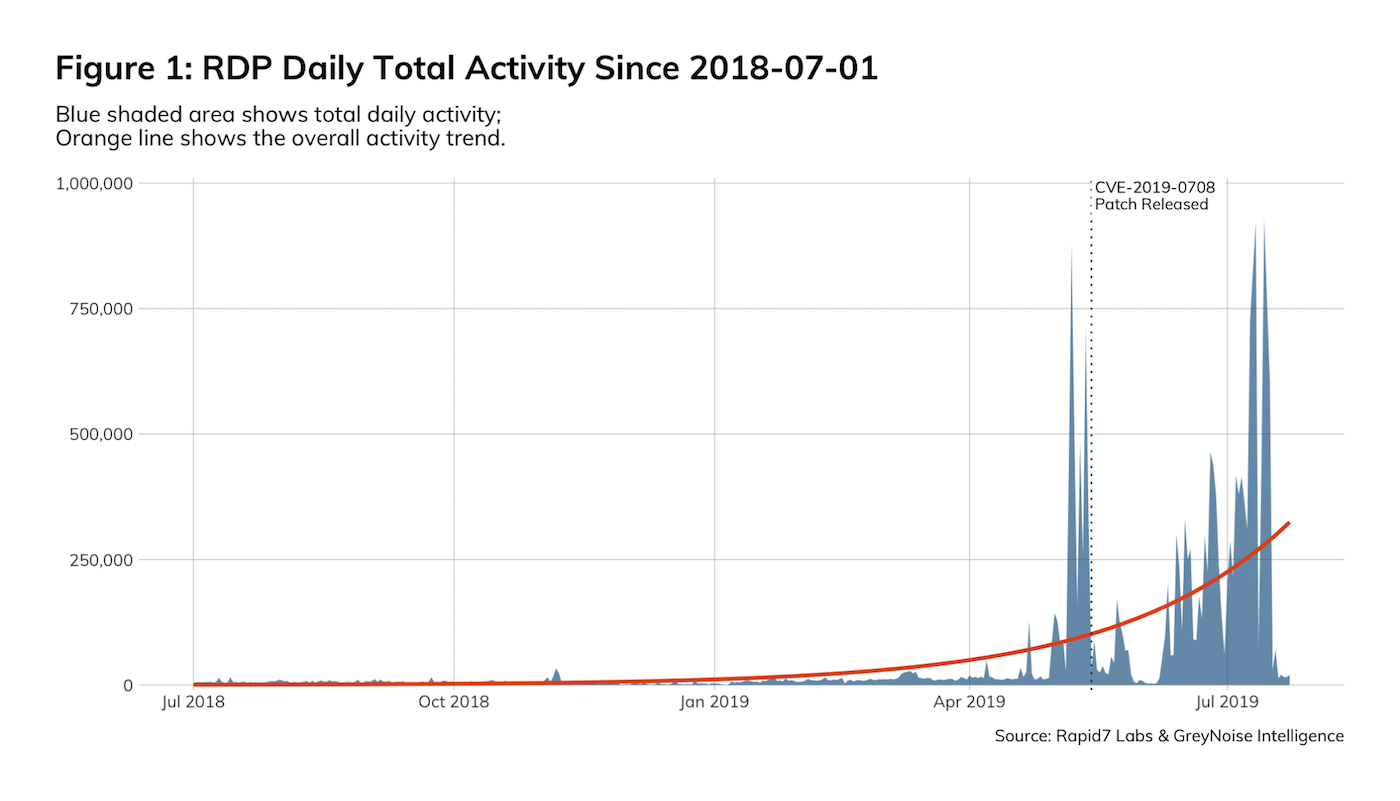
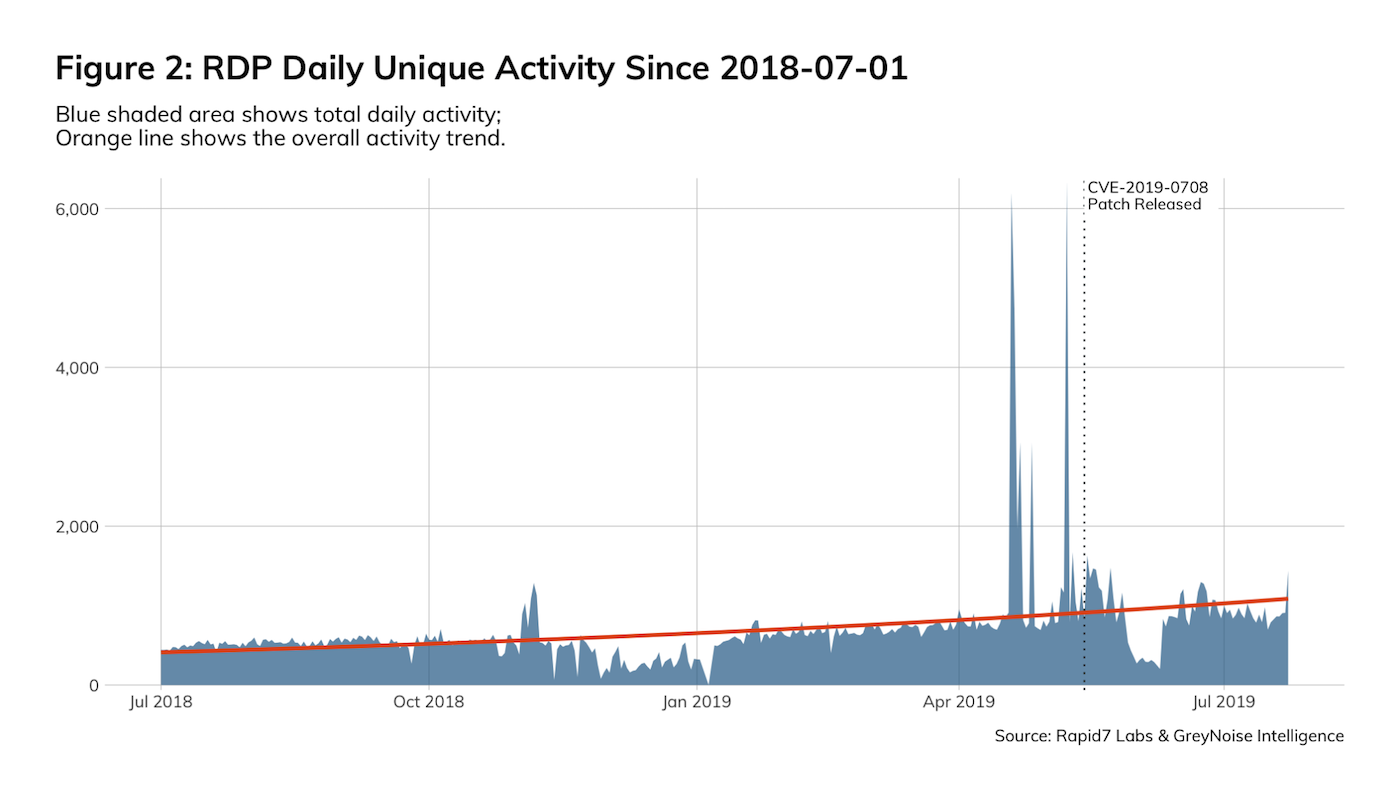
Figure 2 shows the daily unique sources. The spikes are related to the previously mentioned activity and are now a “new normal” for daily unique source activity.
There are three profiles to this RDP activity:
- Inventory scans, where attackers are taking stock of where RDP is on the internet and what flavor of RDP is there. Presently, Rapid7 Labs Project Sonar sees just under a million non-NLA RDP endpoints and over 3 million NLA endpoints on the default RDP port (3389) as of the latest July 2019 RDP studies. The spikes tend to be associated with inventory scans, but not all spikes are inventory-related.
- Traditional RDP exploits; while not nearly as profound, since new attackers have established an inventory we see them trying to use older exploits for older flaws.
- Credential stuffing; we’re used to seeing credential stuffing attacks but not nearly at these levels. The activity in the July time is mostly related to credential stuffing. Again, newer attackers have some fresh inventory to play with so they’re just biding time and trying their best to work with what they have.
As of last week, there is at least at least one known, working, commercial exploit for CVE-2019-0708. The Metasploit team is currently collaborating with community contributor zerosum0x0 on an exploit module to help defenders and penetration testers demonstrate and validate risk. Metasploit has had a remote scanner module for BlueKeep since May 2019. The scanner module was contributed by zerosum0x0 and JaGoTu.
We are also closing in on three months (77 days as of July 30, 2019) since the release of the patch. If past is prologue, this is within the window when we begin to see active exploitation of complex remote code execution vulnerabilities (it takes more time to produce a “bulletproof” exploit for the more complex situations). Combined with the upcoming Black Hat/DEF CON/BSides conferences, which will be pulling security resources away from organizations for a non-insignificant period of time, we suspect this could be the perfect opportunity for attackers to begin overt exploitation campaigns.
Recommendations to Defend Against the RDP BlueKeep Vulnerability
- Remove RDP servers from direct internet connections (i.e., place them behind a VPN).
- Deploy the patch for CVE-2019-0708 as soon as possible and switch to Network Level Authentication.
- Set up internal and external monitoring for RDP connection activity and have response plans in place for any anomalies.
- Do not believe obfuscation will save you. We’ve seen attackers look for RDP on almost every port in the 3000-5000 range and have also found internet-facing RDP on “nearby” ports. This obfuscation will not save you.
- Patch all your RDP servers. We regularly see the use of EternalBlue exploits internally after successful phishing campaigns. Your internal servers are absolutely at risk, especially if they haven’t seen patching and secure configuration attention.
