Many security blogs will say that when it comes to pinpointing weak links on your network, users are No. 1. For instance, user accounts can often get exploited due to poor company policies such as mismanaged access network controls, or when the accounts of departed employees are neglected and not shut down after they leave the company (making them a welcome mat for attackers).
That is why having a process in place to automatically provision and deprovision user accounts across your company’s technology stack is so important. It’s vital to stay on top of this regardless of your company size, especially in a time when employees are changing jobs more frequently. Unfortunately, most companies can’t keep up with the tasks needed to do this manually. That’s where security orchestration and automation comes in. As we explain in our recent Security Orchestration and Automation (SOAR) Playbook, some of these tedious (yet important) tasks can be built into automated workflows, making the process more scalable.
Here are three ways security orchestration and automation tools can streamline the user provisioning and deprovisioning process:
1. Seamless onboarding: Automating the provisioning of new accounts
Your HR team worked hard to acquire a new hire, and now it’s your job to ensure they have the right level of access at the right time. Growing companies could have 10, 20, or sometimes even 50 new employees starting on any given week, and each will require different access levels to different tools and systems. Tediously adding users to each system one by one puts a drain on productivity and competes with more significant, meaningful work.
With a SOAR tool, you can easily connect with tools such as Okta or Active Directory and automate the process of creating user accounts that grant users the right level of access.
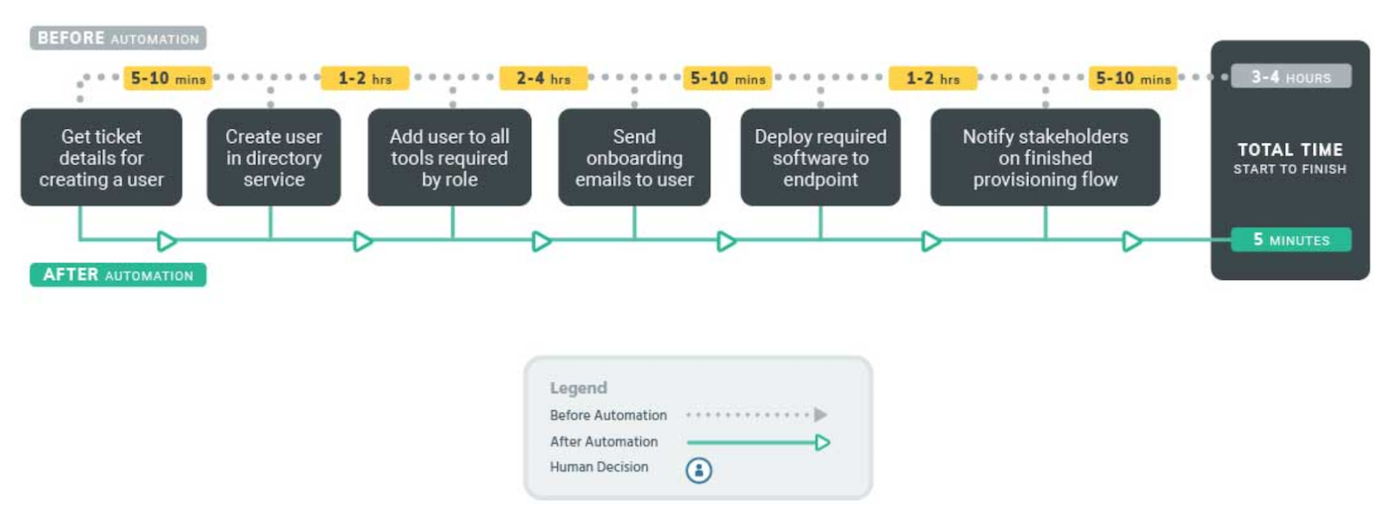
2. Locking the doors: Automating the deprovisioning of departing employees
Whether an employee is kindly asked to leave or puts in their own notice, it’s a security best practice to revoke their access to all tools and systems as quickly as possible. Unfortunately, this rarely happens, and more often than not, accounts are left open for weeks, months, or even years before being shut down.
With SOAR tools, you can create workflows to automatically begin the process of deprovisioning departed users when triggered.
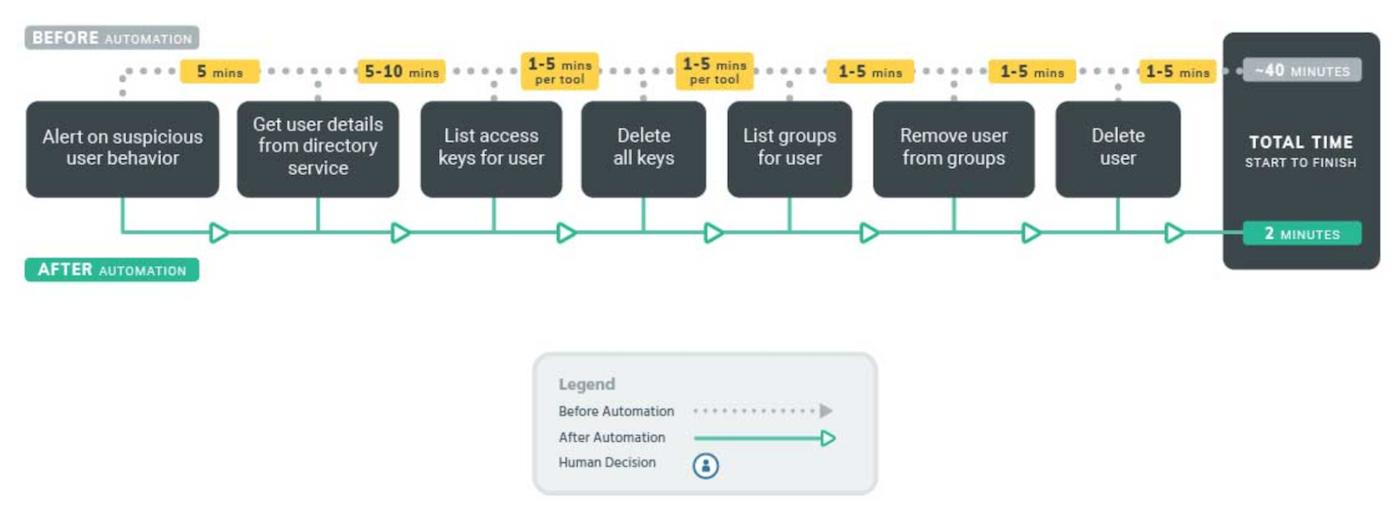
3. Mitigating account exploitation
You also need the ability to deprovision a user account immediately to mitigate further damage in the event of a security incident. This is especially common in phishing attacks; however, most teams can’t shut down the affected account fast enough. While most enterprises have a process in place to respond to a threat, those processes can be long and complex, including:
- Gathering relevant log data
- Tracing the timeline of an event
- Quarantining systems to prevent the attack from persisting any further
- Pinpointing and deprovisioning affected or suspicious user accounts
When an incident occurs, SOAR processes can immediately and automatically deprovision exploited user accounts, remove user access from key systems (such as AWS), and revoke permissions as needed until the threat is contained. This single process ensures that damage can’t be done to major infrastructure.
Getting started with security orchestration and automation
Security orchestration and automation is designed to help teams improve their security posture and create efficiency—without sacrificing control of important security and IT processes. Our new playbook highlights some of the most common use cases for security orchestration and automation, including user provisioning and deprovisioning, as well as useful tips on how to get started.