Today we come to the end of 2019's monthly Microsoft Patch Tuesday (also known as Update Tuesday). This Christmas, Microsoft presents us with 36 vulnerabilities (that's two less than this time last year!) and no new vulnerabilities from Adobe for Adobe Flash.
Unfortunately, despite a light month, there's still action to be taken. CVE-2019-1458, an Elevation of Privilege vulnerability has been detected as something actively being (or has been) exploited. Due to a flaw in how the Win32k component handles objects in memory, an already logged in user could be tricked into running vulnerable code, allowing an attacker to install programs and/or create new accounts under elevated privileges.
Outside of the one exploited vulnerability, the next set of vulnerabilities of interest are the two marked Critical (not actively exploited, though): CVE-2019-1468 and CVE-2019-1471. Both of which are remote code execution vulnerabilities that require some sort of phishing aspect to get a user to complete an action, such as clicking on a specific link or opening an e-mail attachment. With this in mind, the more critical vulnerabilities disclosed this Patch Tuesday can be resolved by applying the latest set of Operating System patches.
On the Microsoft Scripting Engine (browsers) front, we are graced with a single vulnerability (CVE-2019-1485). Although it has a lower CVSS score than the previously mentioned vulnerabilities, Microsoft has regarded this vulnerability as one that is more likely to be actively exploited. With CVE-2019-1485, an attacker would need to convince a user to visit a website or could exploit this vulnerability via embedded ActiveX controls within an application (or Microsoft Office documents) that hosts the IE rendering engine.
As a surprise move (to this author, at least), an advisory has been put out for CVE-2019-1489, another Remote Desktop vulnerability with extra light details. This Windows XP Service Pack 3 vulnerability gets to remain unpatched with the official remediation being "Microsoft strongly recommends upgrading to a supported version of Windows software". That being said, being on supported software is always where we strive to be when practicing good security hygiene.
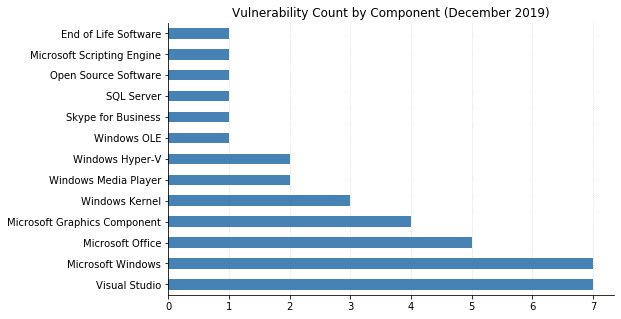
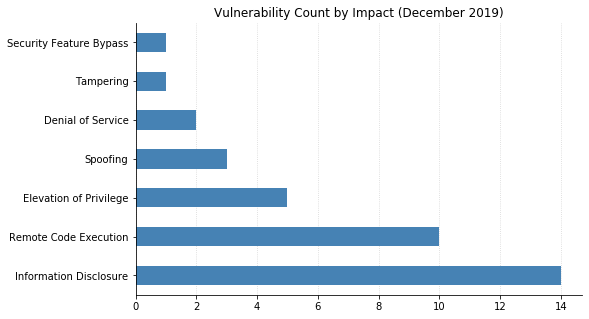
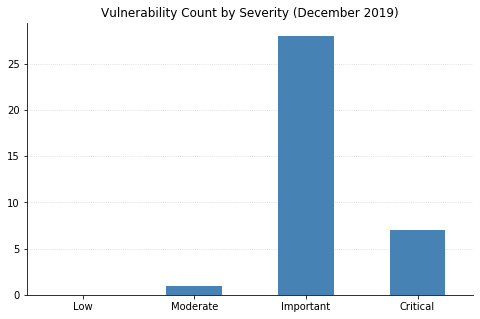
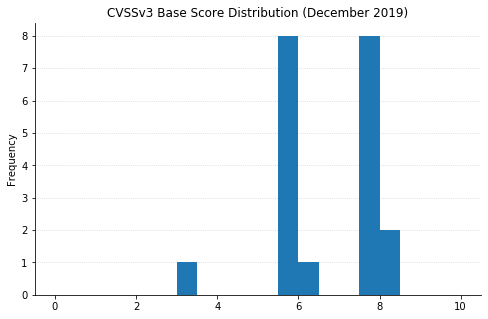
Note: not all CVEs had CVSSv3 data available at the time of writing
