If you feel anxious about the amount of time it takes your organization to remediate vulnerabilities or find yourself spending significant time trying to influence your peers who perform the remediations, you’re not alone. These worries are extremely common among security professionals. Fortunately, effective vulnerability remediation is possible with the right collaboration strategies in place—and Rapid7 InsightVM can help.
What is vulnerability management, and who is responsible for it?
Vulnerability risk management programs encompass five steps. First, there’s visibility. You need to be aware of what’s happening on all your assets, from virtual machines to remote laptops and IoT devices. Next, you assess risk across all those assets in a way that provides continuous information as your environment evolves.
While everyone wishes they had the time and resources to remediate any discovered vulnerabilities, that’s not usually realistic. The third step in vulnerability risk management is prioritizing risk. It’s not enough to consider CVSS scores—you need to take actual attacker behavior into account to determine which vulnerabilities are most likely to be exploited.
All the work of the first three steps would be for nothing if you didn’t then work to remediate the risk. This is where you get results, where patches are installed and code is updated. And, once you’ve remediated your target vulnerabilities, you get to move onto the fifth step: tracking and reporting. This step is how you ensure leadership gives you the budget you need to continue being effective at this work.
Why collaboration matters for vulnerability remediation
The five steps of vulnerability management can be divided into two parts. Visibility, assessment, and prioritization are usually completed by the security team, who are laser-focused on improving their organization’s security posture.
However, the security team isn’t usually in charge of the nuts and bolts of remediating vulnerabilities. That task falls to IT or Development teams, who have a lot to think about that has nothing to do with security. They’re upgrading and maintaining existing systems, deploying new ones, and dealing with outages—and yes, somewhere on their to-do list is remediating the vulnerabilities that the security team handed over.
This difference in priorities can create friction. Fortunately, the right tools can help keep everyone on the same page. As a solutions provider and partner, Rapid7 wants to help bridge the gap between the people trying to understand risk (security) and the people tasked with reducing it (IT/Development).
How Rapid7 InsightVM can help your team drive risk remediation
InsightVM, Rapid7’s vulnerability risk management offering, has several features that help with vulnerability remediation-focused collaboration:
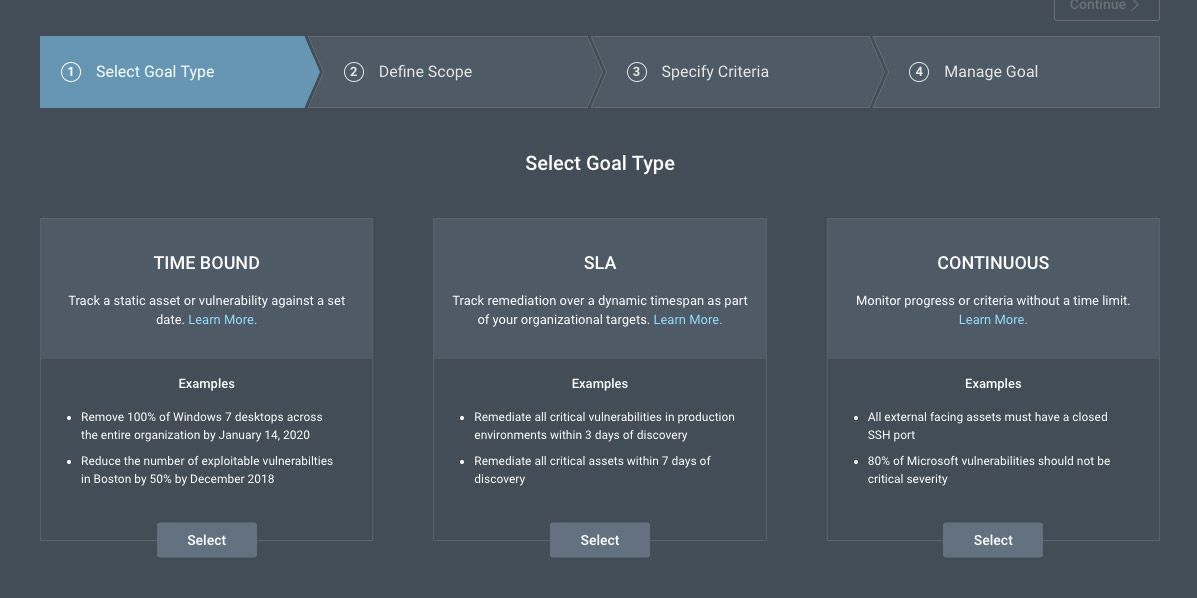
The first is Goals and SLAs. This feature lets you track remediation efforts by identifying goals and identifying metrics to measure against those goals. To help you view your progress, you can add goal cards to your dashboard.
The most common use case among InsightVM customers is for Service Level Agreements (SLAs) between a security team and the IT/Development team. The remediation target is defined in terms of the number of days allocated to remediate a specific group of assets. For example, you might set a goal that all vulnerabilities on Windows 2010 assets must be remediated within 10 days.
Another common type of goal involves monitoring progress on a certain metric without necessarily setting a time limit. For example, if you need to keep port 22 closed on all assets, you can create a continuous goal to monitor whether any assets have port 22 open.
Remediation Projects
Once you’ve set your goals, you want to be able to efficiently assign work to a team member. To do that, you can create a Remediation Project in InsightVM. Remediation Projects allow security teams to assign and track vulnerability remediation duties in real time, providing continuous visibility into how well issues are being fixed. The IT or Development team member executing the remediation doesn’t even need to have access to InsightVM—you can assign tickets through ServiceNow, Jira, or a tokenized URL.
Custom dashboards focused on vulnerability remedation progress and prioritization
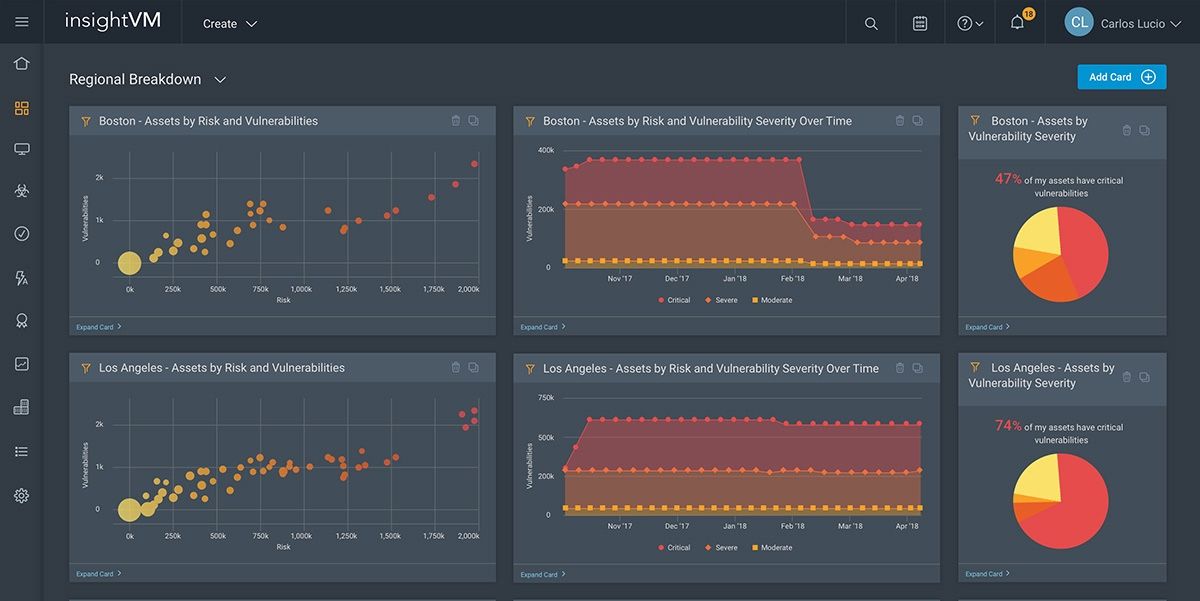
Another helpful feature is InsightVM’s live, custom dashboards. The dashboards allow your team to get a broad view of how the organization is performing. You can filter your view to show only what you care about and drill down for deeper details. One of InsightVM’s most popular dashboards is the Threat Intelligence Feed, a dynamic view that shows you which threats are most relevant to your environment.
While live dashboards are ideal for your team, you probably have stakeholders who need to see a static report. InsightVM can generate a number of useful PDF reports, including one that suggests the top 25 remediations you can undertake to achieve the greatest risk reduction, as well as an Executive Summary report.
Query Builder
InsightVM’s Query Builder isn’t a remediation tool per se, but it does help teams be more efficient by providing easy access to and analysis of your data. You can use Query Builder to quickly pivot between asset and vulnerability results using the same query, perform faster queries than those conducted with the Security Console, and export your data to a CSV file.
Security, IT, and Development teams should never feel like they’re working against each other. Rapid7 InsightVM ensures that everyone is working toward the same goals in the most efficient way possible.
