As IT environments continue to sprawl and organizations accumulate more and more technology without a change in security teams and budgets, understaffing is inevitable and good attack hygiene is no longer enough to protect organizations from potential breaches.
To get ahead of attackers, security teams are increasingly moving from prevention-only ideology into focusing on early detection and accelerated response. Catching and stopping attackers as soon as possible allows security teams to eliminate threats before they ruin an organization’s infrastructure. In order to implement this strategy, teams need the right level of visibility to capture actionable insights—without drowning in too much data.
Enter the Security Operations Center (SOC) Visibility Triad, a network-centric approach to threat detection and response, as described by Gartner in 2019.
The three pillars of the SOC Visibility Triad
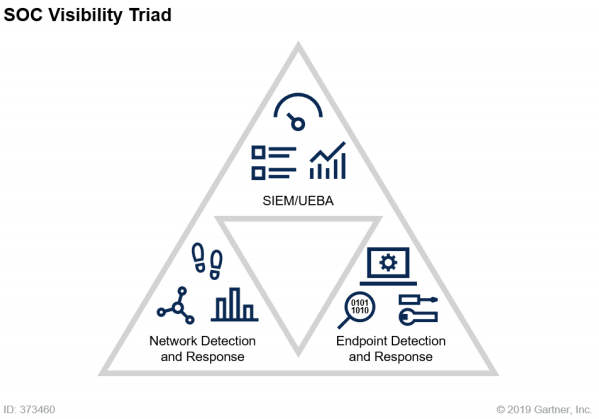
The SOC Visibility Triad model leverages data from three core pillars:
- Logs/user and entity behavior through security information and event management (SIEM)
- Network traffic through network detection and response (NDR)
- Endpoint detection and response (EDR)
Gaining comprehensive visibility into these three pillars of security operations makes all the difference in enabling a security team to catch attacks early on.
Here is a breakdown of each pillar, the data it offers, and how it adds to the overall visibility of security threats across the technology environment.
Stop malicious behavior in its tracks with User and Entity Behavior Analytics (UEBA) and Logging Data
In 2019, 80% of hacking-related breaches were due to compromised credentials, according to Verizon’s 2019 Data Breach Investigations Report. Whether it’s poor passwords or credentials stolen through phishing or other means, user data comes up as a top security issue year after year. Baselining normal user behavior in your environment allows you to more quickly recognize abnormal behavior, such as potential bad actors, so you can identify compromises early on.
Today’s SIEMs should offer features such as visual log search, auto log structuring, and intuitive log parsing capabilities to make it easy to investigate and triage incidents and create custom alerts when needed.
Find threats early with network traffic analysis (NTA) data
Continuously monitoring network traffic is a great way to detect intrusions across the network and minimize an attack’s reach. But knowing which alerts the team should focus on is easier said than done. The key to NTA is reducing the data volume while maintaining access to critical data so that investigations, forensic activities, and custom rule creation can all take priority. With the right system in place, analysts can ensure they maintain continuous visibility across the network while gaining the ability to recognize compromises quickly and being able to trace potential attackers’ steps across systems and applications.
Recognize the first signs of an attack with endpoint detection and response (EDR) data
Endpoint compromises give attackers access to sensitive information in addition to potential protocols or credentials that can give them further access to the network or more privileged accounts. In order to identify which assets were specifically targeted in an attack, your team needs endpoint scanning and alerts. Real-time endpoint detection and response is a critical piece of getting the visibility to recognize an attack at its first sign.
Unfortunately, there are several obstacles security professionals have to overcome to achieve visibility in all three pillars. Many point solutions may fall short of providing full visibility or cloud the data with extra noise or complexity. Some SIEM software providers require tedious configuration and alert tuning, meaning they can’t provide the visibility necessary without more time and work, which most SOCs simply don’t have.
