One prominent area where security programs often struggle is when the security team must demonstrate the business outcomes achieved for the organization. While framing each security conversation around security outcomes can gain buy-in from across the business, how can security teams actually defend that value?
The lack of connection between traditional business performance standards and those employed by many security teams results in underfunded and undervalued capabilities that only get attention when the worst happens: a data breach.
When the spotlight is finally turned on the security program after a breach, individuals typically pay the price because business leadership assumes they were ineffective at their jobs. In fact, many breaches occur in organizations that have invested heavily in technology and people but disregarded focusing on, reporting on, and delivering business-level outcomes.
So, today, we’re taking a step back and evaluating the categorization of 97 Detection and Response (D&R) program outcomes and 73 Attack Surface Management (ASM) outcomes that Rapid7’s User Experience (UX) research and surveying uncovered for us.
First, you might be asking what we mean by “outcome”. In short, it’s the desired result that someone must achieve in a certain period of time and can be measured by a quantifiable or qualitative value. More specifically, each outcome is structured like this:
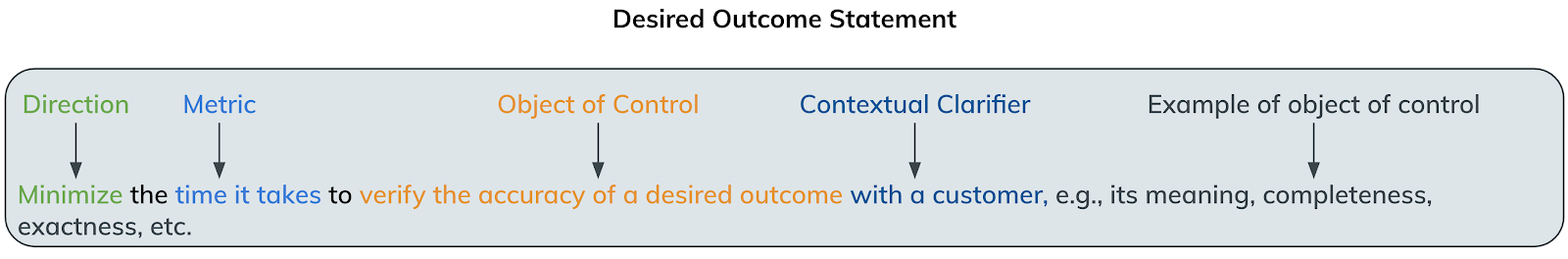
Next, we classified all the outcomes according to three categories we feel represent the core measurements of business:
- Value: What is it that the organization is doing that is generating value (and that customers are paying for)?
- Effectiveness: What are we doing to be the best at the value we’re generating (and that customers are paying for)?
- Efficiency: How are we spending as little as possible to deliver the best value?
Make money, be No. 1, and minimize costs—the recipe to any successful business.
The results
Value
The top three outcomes from D&R and ASM that respondents valued most when delivering value from their programs are as follows (and include their overall rank in either D&R or ASM):
Top 3 D&R Outcomes - Delivering Value

Top 3 ASM Outcomes - Delivering Value

The first thing to note was that value was the No. 1 outcome for D&R programs but fell to No. 2 for ASM, where efficiency (measured by the reduction trend over time) earned the top spot. We might be reading too much into this, but if value is not the No. 1 goal of any aspect of your security program, it either needs to be eliminated or priorities need to be rearranged.
The second thing that jumps out is that the top outcomes of both D&R and ASM point to the other for achieving the other outcomes. This shows how interdependent attack surface management and detection and response programs are.
Finally, I feel like these priorities are largely in line with what I hear day in and day out when speaking to security program team members. Please drop a comment if you feel differently.
Effectiveness
The top three outcomes from D&R and ASM that respondents valued most when building effectiveness for their programs are as follows (and include their overall rank in either D&R or ASM):
Top 3 D&R Outcomes - Building Effectiveness

Top 3 ASM Outcomes - Building Effectiveness

The first takeaway here is that we seem to see effectiveness prioritized too low in the overall ranking for ASM. The order we presented value, effectiveness, and efficiency is intentional. These typically inherently build on each other and represent the standard path in which businesses are built and matured. By not having a balanced approach to value, effectiveness, and efficiency, you cannot effectively manage your attack surface (primarily a technology cost) and could wind up incurring more costs in detection and response (primarily a human cost).
The second takeaway is the focus on awareness, education, and knowledge. If we consider that effectiveness is born from knowledge and capability, the priorities are in the right order. Far too often, security programs forgo the (often free) opportunity for the security team to educate the company on how to better protect what matters most to the organization. Consider for a minute that a significant portion of the data breaches in the past year involve unsecured sensitive data on publicly accessible assets. Technology can’t solve that—only people who care about protecting what matters can.
The last takeaway for the “effectiveness” top three is that issues of visibility and issues of threat awareness only appear once. We already established that we require knowledge and capability to create effectiveness, but visibility and threat awareness create knowledge. You can’t find what you can’t see, and you can’t identify what you don’t know.
Efficiency
The top three outcomes from D&R and ASM that respondents valued most when building efficiency for their programs are as follows (and include their overall rank in either D&R or ASM):
Top 3 D&R Outcomes - Building Efficiency

Top 3 ASM Outcomes - Building Efficiency

We included a bonus ASM since one of those is clearly for Rapid7 as a solutions provider to the customers who participated in the UX research exercise.
Our first observation is that ASM has two of its top three in the “efficiency” category. As discussed in the previous section, efficiency should be the third step in your journey to achieve value, effectiveness, and efficiency. By prioritizing efficiency over effectiveness, you open yourself to missing key findings that could lead to a threat bypassing your security measures.
Second, the outcome tied to efficiency in almost all cases is directly linked to value. ASM 1 and 6 and D&R 7, 11, and 12 aim to improve the speed with which we can deliver value back to the organization. This really goes to validate that the respondents are focused on squeezing efficiency out of the outcomes they feel deliver value to their organizations.
Last, in all but one case, the metric to measure success is around time. Time is a very tricky metric to measure, as there are often multiple times within a process and selecting the ones that best represent the outcomes is a judgement call. Additionally, automatically tracking state changes in processes is not always feasible, which makes it difficult to aggregate and track the metrics. Nonetheless, time is efficiency, so investing the time in creating the time records and tracking the information is still the best way to show efficiency.
We’d love to know how the idea of categorizing outcomes in business terms like “value,” “effectiveness,” and “efficiency” ring with your experience running your own security program. Do you think this simplifies how you communicate with the business or better shows how you serve your organization? Let us know in the comments!
