Let's start off talking about CVE-2020-0688 from last month -- the Microsoft Exchange Validation Key RCE vulnerability. At the time it was published February 11, 2020, the vulnerability had not seen active exploitation. As of March 9, 2020, there were increasing reports of activity happening on unpatched Exchange Servers surrounding this vulnerability. If you hadn't had a chance to act on that, I would give it a bit of love over the whopping 115 new vulnerabilities brought forth by Microsoft this March 2020 Patch Tuesday. It's worth noting that Metasploit has a module out already to help detect this, as does InsightVM.
The focus on bringing CVE-2020-0688 in line gives a general feel of what this month's Patch Tuesday is like. While 115 vulnerabilities are not something to just brush aside, especially given the wide breadth of products and components patched up this month, we do get to enjoy the fact that almost all the vulnerabilities can be remediated simply by patching. Our outlier vulnerability this month (when it comes to straight-forward remediations) is CVE-2020-0765. This information disclosure vulnerability against their deprecated Remote Desktop Connection Manager (RDCMan) product has no planned fixes. The best course of action is to find a replacement or adjust processes to avoid a scenario where an attacker is able to read arbitrary files after convincing an authenticated user to open a specially crafted RDG file. As stated (nearly) monthly, good security hygiene will always help mitigate these risks.
With that oddity aside, patching your operating systems immediately closes the door against 78 vulnerabilities. For those that follow the monthly-rollup track of patching systems, it would include browser fixes which brings our remediation count to 96 vulnerabilities. That's over 80% of vulnerabilities published by Microsoft remediated from a "single patch"! From a software remediations perspective, this month may be grounds for celebration by this relatively straight-forward track to follow: patch up CVE-2020-0688 (from last month) if you have Exchange Servers, then patch this month's operating system patches, then Microsoft Office and SharePoint.
An interesting, yet potentially confusing, aspect to Patch Tuesdays lately is the continued reporting and fixing of obsolete operating systems Windows 7, Windows Server 2008, and Windows Server 2008 R2. Previously, unsupported operating systems of this nature would be left off of old MSRC bulletins, but there's a clear pattern in Microsoft providing these patches so far. If you're wondering how you would obtain those patches, be sure to follow the instructions set in KB4522133 after having purchased Extended Security Update licenses.
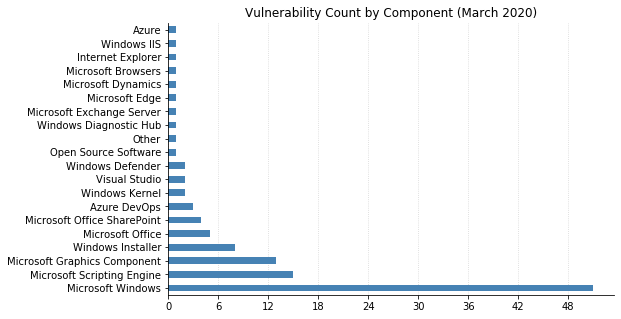
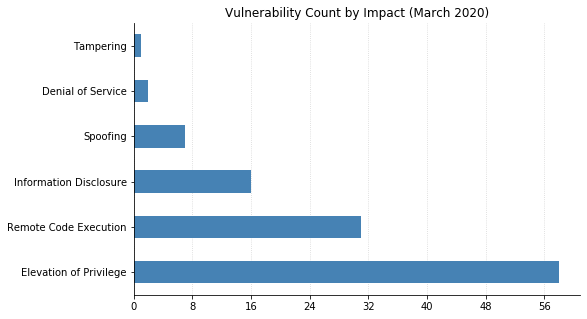
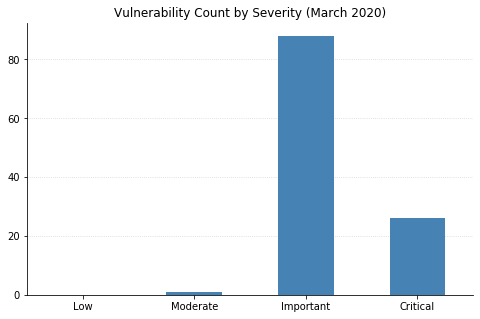
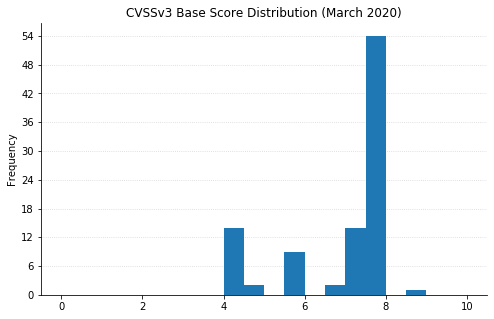
Note: Graph data is reflective of data presented by Microsoft's CVRF at the time of writing.
