Rapid7 chief data scientist Bob Rudis, threat intelligence team member Charlie Stafford, and VRM engineering manager Brent Cook also contributed significant data and analysis to this blog.
During this week’s Patch Tuesday (March 10, 2020), the security community noticed that Microsoft published and then immediately deleted information about CVE-2020-0796, a critical remote code execution vulnerability in the SMBv3 protocol. Researchers took note, and shortly thereafter, Microsoft published a formal advisory about the vulnerability, which was unpatched as of yesterday (March 11, 2020). This morning, Microsoft released patches that correct how the SMBv3 protocol handles specially-crafted requests.
Vulnerability description
Microsoft’s advisory states that a crafted SMBv3 packet could be used to achieve remote code execution on a vulnerable SMB Server. Exploitation of an unauthenticated SMB Client requires the victim to have connected to an SMBv3 server controlled by the attacker.
Affected versions:
- Windows 10 v1903
- Windows 10 v1909
- Windows Server v1903
- Windows Server v1909
Patches are available as of March 12, 2020. For users who are unable to patch immediately, Microsoft’s guidance is to disable SMBv3 compression and block TCP port 445 on firewalls and client computers as a workaround.
Rapid7 Analysis
Rapid7 rates this vulnerability as being high value for attackers, but it is not known to be actively exploited in the wild as of time of writing.
Since Windows 10 v1709 and Windows Server v1803, Microsoft randomizes memory allocation of processes by default. This randomization significantly increases the difficulty of successful exploitation of memory corruption vulnerabilities such CVE-2020-0796. Rapid7 researchers expect that there will be at least some delay before commodity attackers are able to produce usable RCE exploit code for this vulnerability.
The research team at Kryptos Logic has published a denial of service (DoS) proof-of-concept demonstrating that code execution is possible. A DoS is often a precursor to more impactful exploitation, such as full remote code execution (RCE).
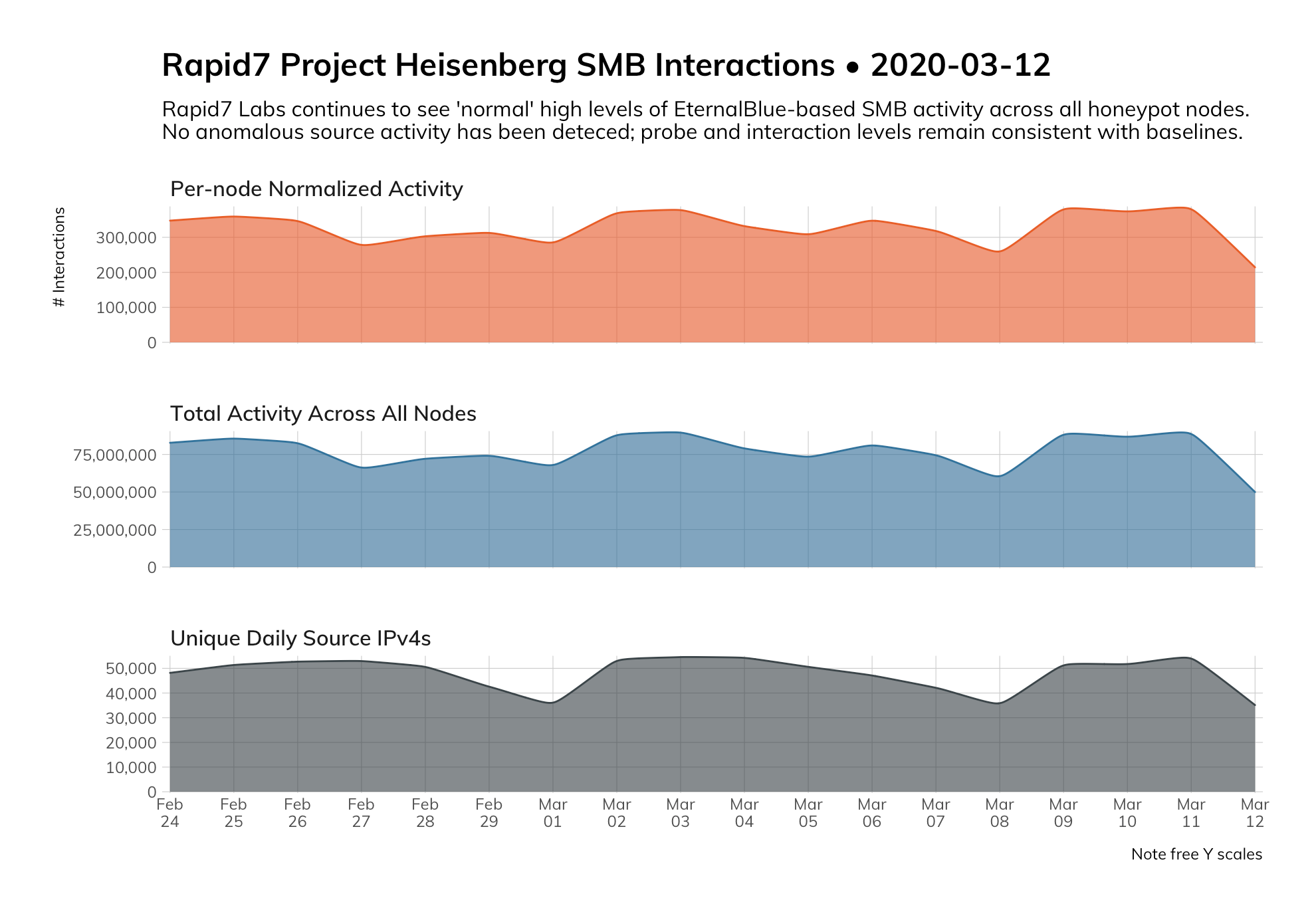
Rapid7’s Project Lorelei honeypot systems have not identified any indication of an anomalous spike in SMB scanning (Figure 1) to date. SMB scanning remains at the same elevated baseline level our Labs team has observed for some time.
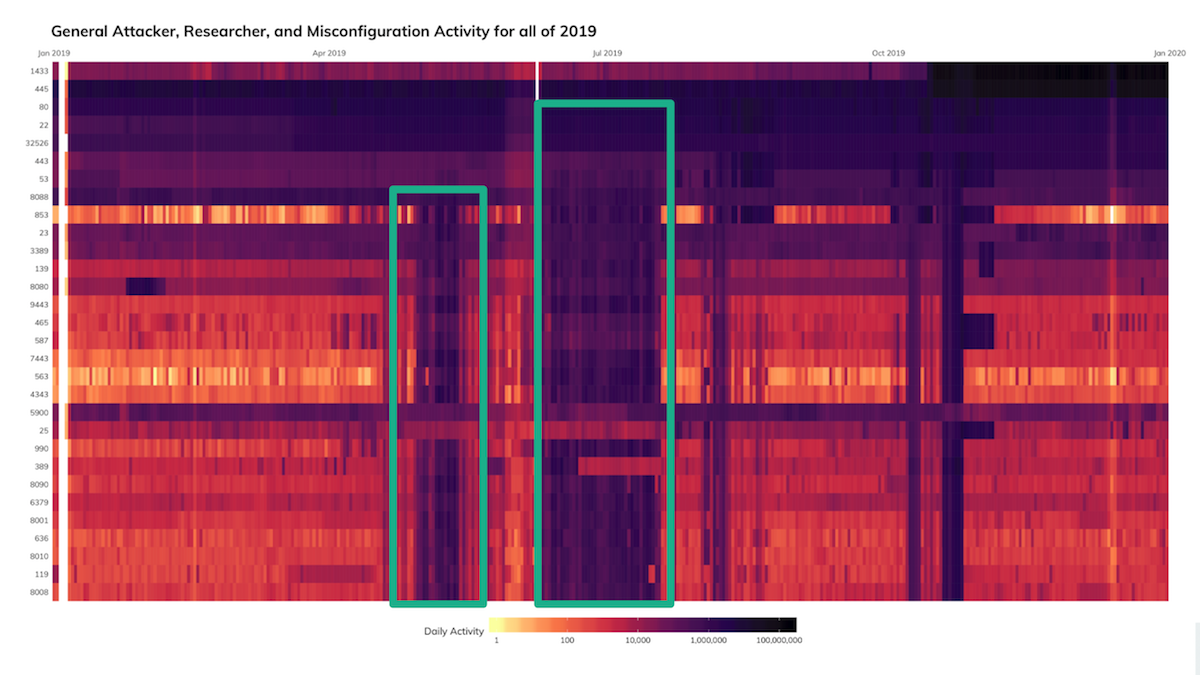
To put this information into perspective, Figure 2 shows the prevalence of SMB scanning infrastructure throughout 2019. The high baseline of SMB scanning (TCP/445) across the internet are currently associated with WannaCry/EternalBlue infrastructure.
Rapid7 Customers
As of March 11, 2020, Rapid7 customers can use an authenticated check to identify whether SMB compression has been disabled. Rapid7 recommends blocking TCP port 445 at all points of network ingress and egress to prevent SMB traffic to or from the internet. Additionally, we recommend internal network segmentation and disallowing desktop-to-desktop SMB connection attempts to prevent lateral movement.
Disabling SMBv3 compression will prevent exploitation of vulnerable SMB servers. To disable SMBv3 compression, the following command can be run in PowerShell:
Set-ItemProperty -Path
"HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters"
DisableCompression -Type DWORD -Value 1 -Force
Rapid7’s research and threat intelligence teams will continue to assess this vulnerability and provide updates on any changes regarding active exploitation or new security content for customers.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe