We are now living in challenging times due to the COVID-19 outbreak as we work from home, self-isolate, and protect the vulnerable. I must say a big thanks to my employer, Rapid7, for having a robust system that enables working from home. Our IT teams have worked around the clock to expand services for remote workers so that we can continue to deliver value for our customers. Well done, all!
Still, as IT and network security staff around the world hurry to roll out more and more VPN and remote access services, it’s important to recognize that security or operational issues can arise. For example:
- Employees and contractors may use personal computers to connect to the workplace. These may be unpatched or contain malware.
- Opening ports/services on firewalls may result in unexpected behavior/traffic.
- Load balancing may not work as expected. Without visibility as to what is happening, it will be impossible to tell whether certain ingress/egress points are overloaded.
- It’s more difficult to spot suspicious users and activity if the number of connections suddenly ramp up. Who is connecting into the network and what are they accessing/downloading?
Don’t lose visibility into what is happening on your network
With the rush to roll out extended remote access services, we need to be careful about not leaving our networks open to attack. A rushed change to open up more connectivity through a firewall could leave a network vulnerable.
Mistakes with firewall changes are not uncommon. I remember working with a customer some time ago who had questions about an inbound network traffic report. Within the report, there was activity reported over TCP port 1433. Clients from a number of countries were trying to connect to MSSQL servers hosted within their network. The customer claimed that it was not possible. I checked the report, which was also backed up by a number of Intrusion Detection System (IDS) events that suggested that someone was trying to brute force the database SA account. I asked the customer to double-check their firewall tables, and they found that someone did leave port 1433 open. An external contractor had requested access, and instead of only allowing access to them, the change left it open to anyone.
It’s important to note that while COVID-19 dominates the news right now, there are lots of other infosec issues worth keeping an eye on. An example of this is the newly detected vulnerability with the SMBv3 protocol. Rapid7 recommends blocking TCP port 445 at all points of network ingress and egress to prevent SMB traffic to or from the internet. Make sure you have visibility of network traffic going to and from your firewalls in case a port such as TCP 445 gets opened accidentally as part of a firewall change request.
Network traffic analysis
One method to gain visibility on your network, including home users, is to monitor network traffic going to and from your ingress/egress points. Rapid7 recently announced an Open Preview program for Network Traffic Analysis in InsightIDR, our SIEM solution. Rapid7’s proprietary Deep Packet Inspection data transforms packet capture into human-readable and actionable insights—avoiding the complexity and overhead of full packet capture without compromising detail. What’s unique about this feature is that it is application-aware, so you can see which applications are in use.
The image below shows an example of what you should be watching out for. Here we can see a number of applications in use where the client initiating them is outside the network. The actual query used was: where(direction=INBOUND) groupby(app_protocol_description)calculate(sum:total_bytes).
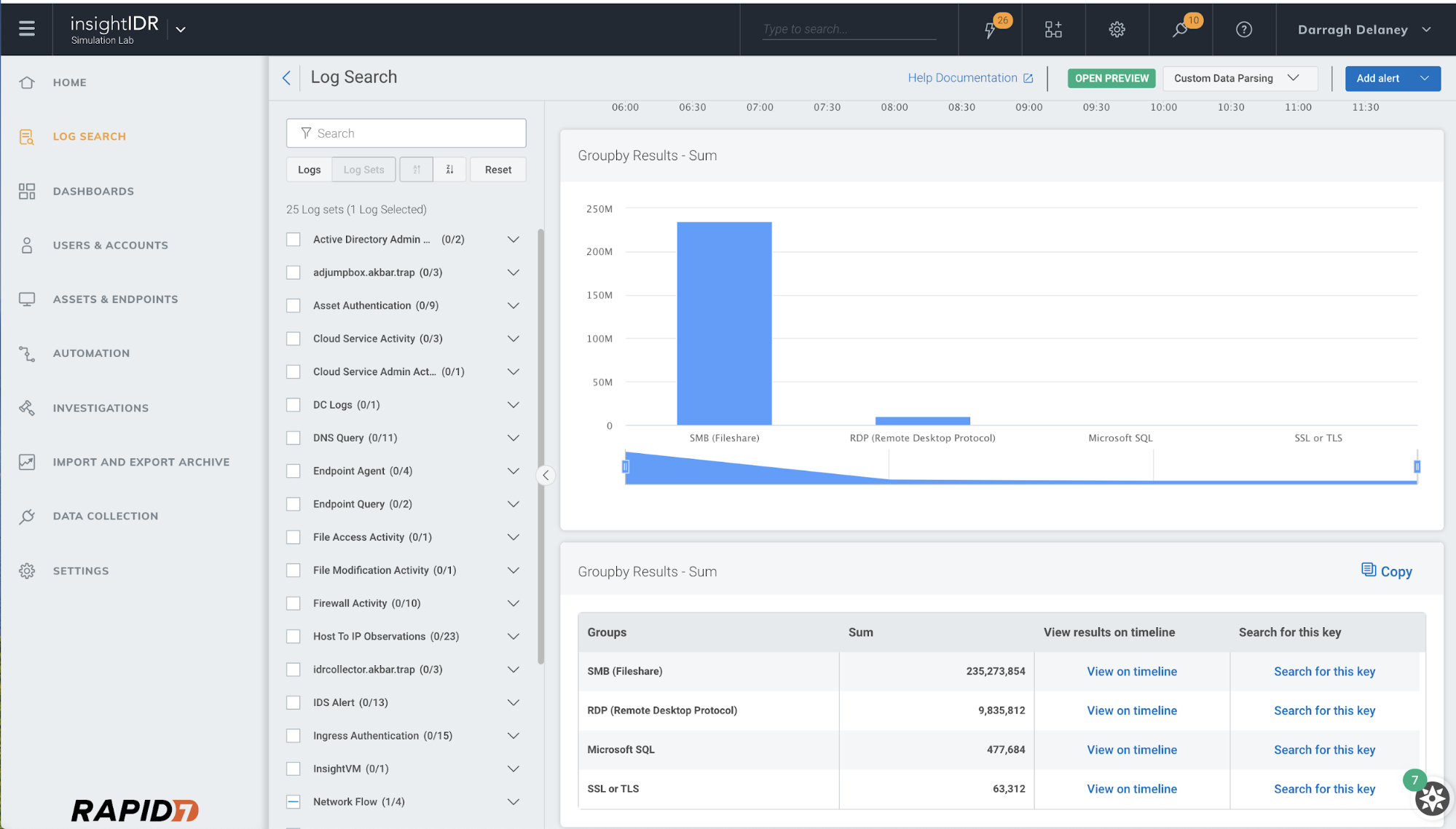
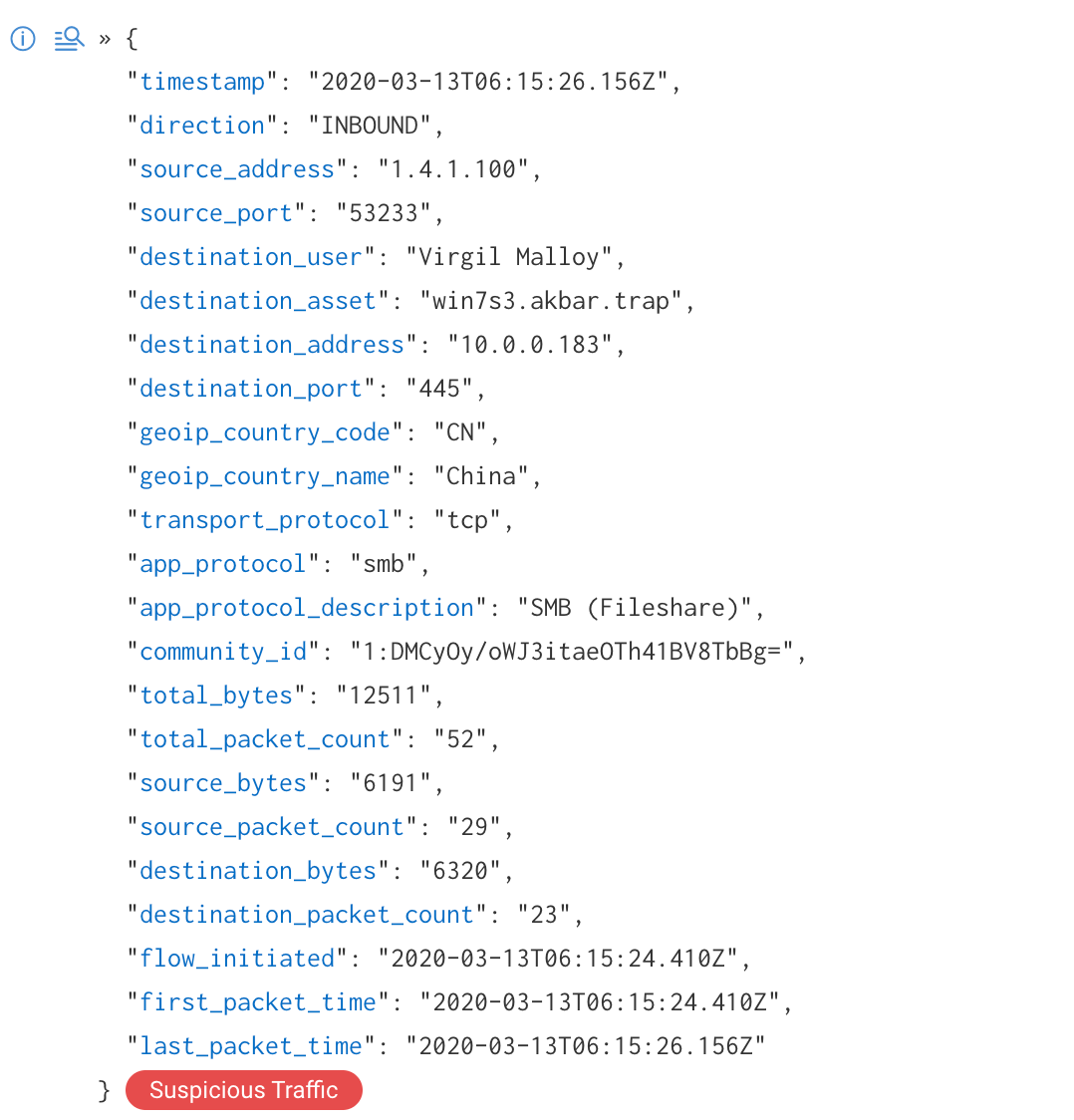
Drilling down on this, we can reveal more about what was targeted. Here, we can see the destination asset that was connected to, plus the user associated with this system.
While times are challenging right now, simple steps like gaining real-time and historical visibility as to what traffic is entering and leaving our networks have the potential to save us a lot of time in the future and keep our assets and employees safer. If you are an InsightIDR customer, you can download an Insight Network Sensor today. When installed, check out the dashboard card library, where you can quickly build a north/south perimeter-focused dashboard.