Cisco has noted a whopping 34 vulnerabilities across two of its remote access and network inspection devices on May 6, 2020. While it is important to patch all of them, there are a dozen that require your immediate attention, with an especially concerning duo of vulnerabilities that we’ll cover first:
- CVE-2020-3187: An unauthenticated, remotely exploitable path traversal in the web services interface of Cisco Adaptive Security Appliance Software (ASA) and Cisco Firepower Threat Defense (FTD).
- CVE-2020-3529: Another unauthenticated, remotely exploitable vulnerability in both ASA and FTD that can be used to retrieve the contents of the device active memory.
The vast majority of the 12 more urgent vulnerabilities will result in a denial-of-service (DoS) condition on these devices. Given the recent significant increase in the percentage of remote workers in most organizations, it is inadvisable to postpone patching DoS weaknesses as you may have in the past. What previously may have been a minor, temporary disruption may now turn into a significant interruption in service and, even worse for their paired disclosure weaknesses, a breach of confidentiality.
Overview of the two major Cisco vulnerabilities
Cisco claims the weaknesses associated with CVE-2020-3187 only enable attackers to traverse the web application side of ASA and FTD devices, where they are then able to read or delete files. The latter action can lead to a denial-of-service condition, but a reboot will replace any deleted files. The former can enable attackers to retrieve sensitive device- and organization-specific secrets that may enable them to perform additional actions.
The weaknesses patched in CVE-2020-3529 allow attackers to use a simple GET request (if they craft the right HTTP path specification) to grab the content of device memory, which will invariably contain usable confidential information as well.
Exploiting the Cisco vulnerabilities
There is no known, public proof of concept (PoC) code for either vulnerability, but it’s fairly trivial for attackers to gain access to ASA and FTD virtual images to start looking and it is only a matter of time—likely very short, as has been the case for many remotely exploitable vulnerabilities in security-oriented services in 2020—before knowledge of the specially crafted, memory dumping path spec is disclosed.
Attackers can use the DoS component to disrupt already strained processes in organizations and use either or both of the deadly duo to gain secrets that are secret for a reason. It is conceivable that the directory traversal issue in CVE-2020-3187 can even aid attackers in crafting the right path to exploit the weaknesses in CVE-2020-3519.
Guidance on remediating the Cisco vulnerabilities
Rapid7 is strongly urging all organizations with affected systems to patch today or this weekend. You can use this link to determine whether the configuration of your version of ASA or FTD is vulnerable.
As you are working with your operations and network teams to triage and implement the patches, you should configure your logging and monitoring systems to watch for excessive and/or unusual behavior in the access logs of the ASA and FTD devices. This may require configuring more detailed logging, but will be a great way to get a heads-up on any attacker reconnaissance or exploitation-attempt activity. If you are unable to reconfigure logging to gain this visibility, you can use packet capture or NetFlow infrastructure to monitor for abnormal connection sources or connection patterns to these devices.
Cisco has set up a special page for all 12 vulnerabilities rated as “High,” and we’ve provided AttackerKB links to all of them below:
| Cisco Security Advisory | CVE ID | CVSS Base Score |
|---|---|---|
| Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software IPv6 DNS Denial of Service Vulnerability | CVE-2020-3191 | 8.6 |
| Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Malformed OSPF Packets Processing Denial of Service Vulnerability | CVE-2020-3298 | 8.6 |
| Control Protocol Denial of Service Vulnerabilities | CVE-2020-3254 | 8.6 |
| Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software OSPF Packets Processing Memory Leak Vulnerability | CVE-2020-3195 | 8.6 |
| Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software SSL/TLS Denial of Service Vulnerability | CVE-2020-3196 | 8.6 |
| Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Web Services Information Disclosure Vulnerability | CVE-2020-3259 | 7.5 |
| Cisco Adaptive Security Appliance Software Kerberos Authentication Bypass Vulnerability | CVE-2020-3125 | 8.1 |
| Cisco Firepower 1000 Series SSL/TLS Denial of Service Vulnerability | CVE-2020-3283 | 8.6 |
| Cisco Firepower Threat Defense Software Generic Routing Encapsulation Tunnel IPv6 Denial of Service Vulnerability | CVE-2020-3179 | 8.6 |
| Cisco Firepower Threat Defense Software Packet Flood Denial of Service Vulnerability | CVE-2020-3255 | 7.5 |
| Cisco Firepower Threat Defense Software VPN System Logging Denial of Service Vulnerability | CVE-2020-3189 | 8.6 |
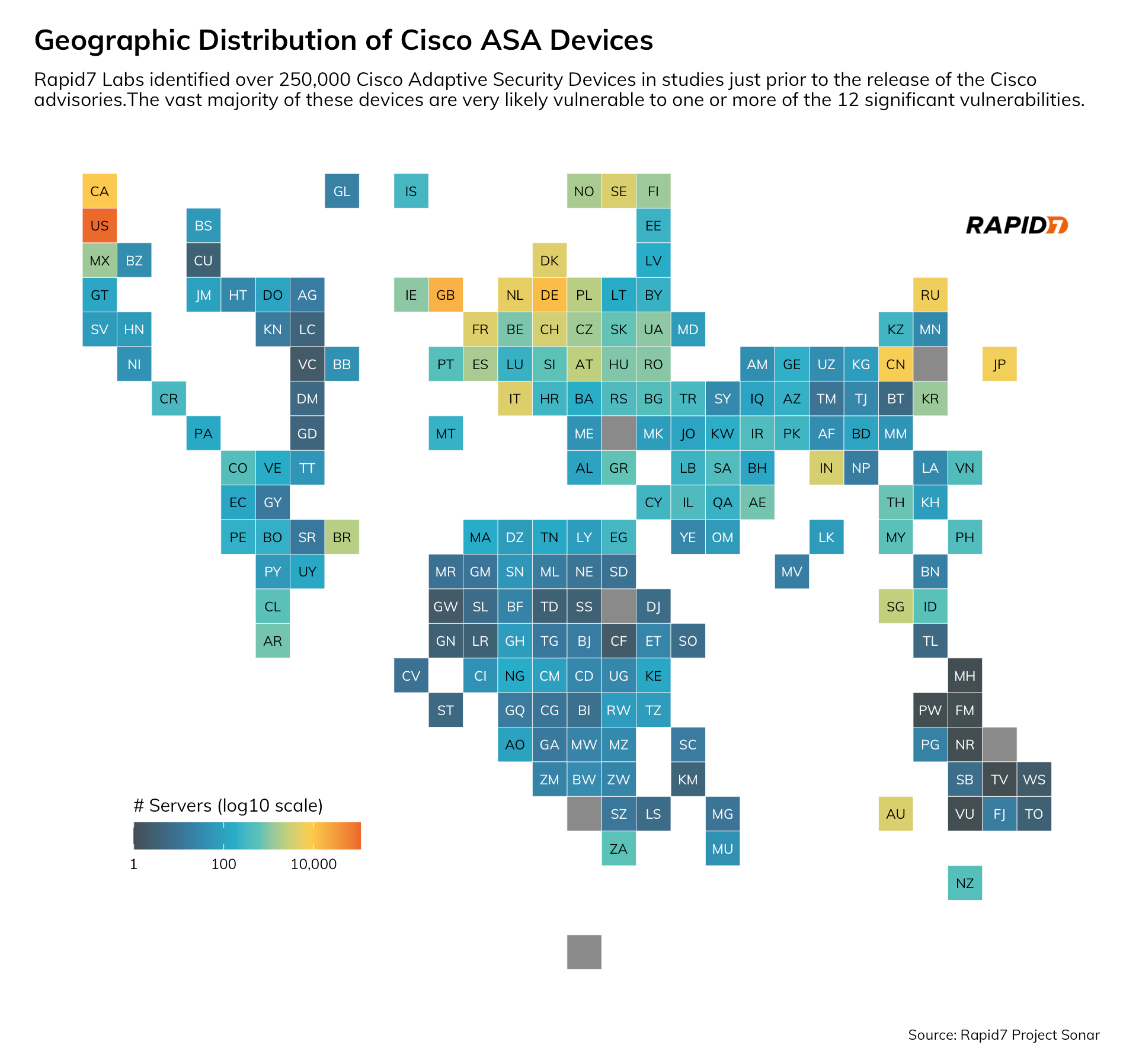
There are technical conditions associated with the remaining 10 that require existing internal knowledge, good guesses, or proper timing and volume to execute, but this does not make them any less important to patch. As noted below, they have over 250,000 ASA targets to practice on, with over 43% of these exposed devices residing in U.S.-homed networks.
Rapid7 Labs is monitoring for unusual activity in Project Lorelei and is on the lookout for proof-of-concept code releases. We will update this post with new detection, mitigation, and remediation as it becomes available.
