Welcome back! In Part 1 of the CMMC series, we introduced the Cybersecurity Maturity Model Certification (CMMC) and the concept of Practices and Processes within. Let’s take a deeper dive into some of these concepts to gain a better understanding of how the framework is designed.
First, let’s revisit the key terms of CMMC:
- Domain: Categories of security controls
- Capabilities: Abilities within each domain
- Practices: Specific activities that must be performed to meet capability requirements.
- Processes: Primarily documentation, management, and governance of activities you perform
More practice
CMMC requires the implementation of Practices. There are a total of 171 practices mapped across the five levels for capabilities and domains, organized in tree-like fashion: Domains → Capabilities → Practices.
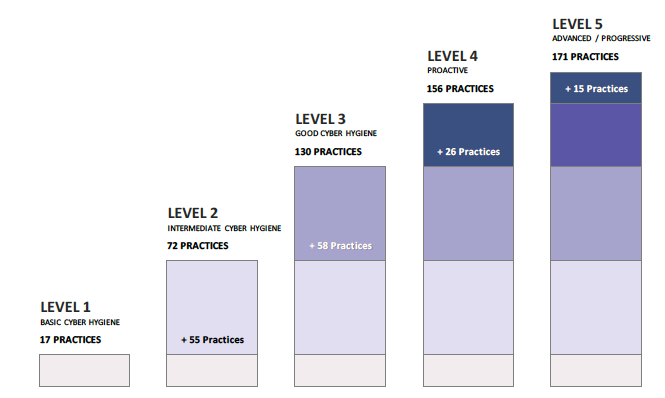
- Level 1 aligns with Safeguard Federal Contract Information (FCI)
- Level 2 serves as a transition step to Level 3
- Level 3 aligns with Protect Controlled Unclassified Information (CUI)
- Levels 4 and 5 protect CUI and reduce the risk of advanced persistent threats (APTs)
Remember that each level encompasses the requirements of the preceding level. In addition, to achieve a particular level certification, both the processes and practices must meet the requirements of that level—otherwise, certification will be at the lower of the two levels.
The practices are tagged with identifiers that list the domain, level, and specific practice. For example:
[DOMAIN].[LEVEL].[PRACTICE]
AC.1.003
Access Control Domain, Level 1, Practice 003
Verify and control/limit connections to and use of external information systems.
The full list of practices can be found on page 12 of the CMMC v1.02.
Are you capable?
As mentioned earlier, each domain consists of a set of capabilities (and practices) across five levels. There are a total of 43 capabilities within the 17 domains. For example:
Access Control (AC) Domain:
The four Capabilities within the Access Control Domain include:
- Establish system access requirements
- Control internal system access
- Control remote system access
- Limit data access to authorized users and processes.
The full list of capabilities can be found on page 8 of the CMMC v1.02.
To illustrate, to meet Access Control (AC) Capabilities, for example, the following practices would have to be implemented:
| Capability | Level 1 | Level 2 | Level 3 | Level 4 | Level 5 |
|---|---|---|---|---|---|
| C001: Establish system access requirements | AC.1.001 | AC.2.005 AC.2.006 | |||
| C002: Control internal system access | AC.1.002 | AC.2.007 AC.2.008 AC.2.009 AC.2.010 AC.2.011 | AC.3.017 AC.3.018 AC.3.019 AC.3.012 AC.3.020 | AC.4.023 AC.4.025 | AC.5.024 |
| C003: Control remote system access | AC.2.013 AC.2.015 | AC.3.014 AC.3.021 | AC.4.032 | ||
| C004: Limit data access to authorized users and processes | AC.1.003 AC.1.004 | AC.2.016 | AC.3.022 |
Putting It All Together
Let’s look at one example of CMMC Levels 1–3 to illustrate how all the concepts work together. We’ll continue to use the Access Control Domain (AC) in our example.
The Access Control (AC) Domain has a total of 26 practices spread across the five levels of maturity.
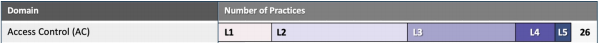
Level 1
Level 1 practice maturity means implementing the following four AC practices (reference table above):
- AC.1.001
- AC.1.002
- AC.1.003
- AC.1.004
Note that there are no maturity processes assessed at Level 1 maturity. This means organizations must perform the Level 1 practice but do not have any institutionalization requirements. If all four practices are implemented, your organization is deemed to be performing the process at a maturity Level 1 (Performed) level.
CMMC Level 1 for AC would thus be Practices (Basic Cyber Hygiene) and Process (Performed).
Level 2
Level 2 practice maturity means implementing the four (4) level 1 practices above plus ten (10) additional level 2 Access Control (AC) practices:
- AC.1.005
- AC.1.006
- AC.1.007
- AC.1.008
- AC.1.009
- AC.1.010
- AC.1.011
- AC.1.013
- AC.1.015
- AC.1.016
Process Maturity Level 2 (Documented) would require that a policy is established for Access Control (AC) domain and that the practices are documented to implement the policy. This includes the 14 total practices for Level 1 and Level 2 practice maturity combined.
CMMC Level 2 for AC would thus be Practices (Intermediate Cyber Hygiene) and Process (Documented).
Level 3
Level 3 practice maturity means implementing the four Level 1 practices, the 10 Level 2 practices, plus eight additional Level 3 Access Control (AC) practices:
- AC.3.017
- AC.3.018
- AC.3.019
- AC.3.012
- AC.3.014
- AC.3.020
- AC.3.021
- AC.3.022
Process Maturity Level 3 (Managed) would require the Level 2 (Documented) processes plus the establishment, maintenance, and resourcing of a plan that includes access control.
CMMC Level 3 for AC would thus be Practices (Good Cyber Hygiene) and Process (Managed).
Needless to say, there’s a lot to consider and keep track of in the CMMC, even if you feel you have been adhering to FAR Clause 52.204-1 and/or NIST Special Publication (SP) 800-171. We know many of you have been self-assessing for years under DoD requirements, but that internal eye can be blinded.
How Rapid7 can help
If you recall from Part 1, organizations can no longer self-assess to be awarded DoD contracts. This means, like it or not, you are going to need to be visited by a CMMC third-party assessment organization (C3PAO) auditor at some point in the near future. When was the last time you had an outside expert review of your security program? You likely don’t want the C3PAO to be the first set of independent eyes to review your program and find deficiencies. Rapid7 has the experience and expertise to review your program, and help you quickly understand weaknesses or deficiencies in security controls and processes, and provide a path forward by providing a Plan of Action & Milestones (POA&M).
Be aware that, as of late April, the CMMC Accreditation Body has not yet certified any CMMC Third Party Assessment Organizations (C3PAO). As such, neither Rapid7 nor any other third party can currently provide a CMMC certification. Organizations can (and should!) prepare for an official CMMC assessment by evaluating their cybersecurity programs against the DoD’s CMMC model. The recommendation of both the DoD and the CMMC-AB is to perform an independent review of your security program prior to being visited by a C3PAO.
