This post is part one of a two-part blog series on policy customization in InsightVM.
Note: Since the original publish date of this post, Custom Policy Builder has been made generally available to all InsightVM customers.
To properly guard against security threats, maintain compliance, and incorporate security upgrades into software, organizations need to continuously monitor and enforce how their computer systems and applications are configured. However, because every organization has unique elements in their environment, they need to be able to set up different configurations.
That’s why we’re excited to announce that Custom Policy Builder is now in Open Preview in Rapid7’s vulnerability management solution, InsightVM. (Note: As of 7/1/2020, Custom Policy Builder is generally available to all InsightVM customers.) With Custom Policy Builder, you can improve your secure configuration assessment program by creating and editing custom policies that meet the unique needs of your environment.
This enhanced secure configuration assessment and policy compliance feature offers you a better holistic security view, helping you achieve more effective security outcomes.
Custom Policy Builder provides our customers with greater flexibility to create custom policies and edit existing policies in various domains like CIS, DISA, USGCB, and others.
In today’s policy customization post, we’re going to focus on Center for Internet Security (CIS) policies. Additional blog posts in this series will cover topics like checking for existence of files and specific patterns in a file.
CIS benchmarks: A great starting point
The top 20 Critical Security Controls from CIS cover a majority of policy and compliance needs for a variety of industries and organizations.
The recent 2020 Verizon Data Breach Investigations Report (DBIR), one of the most respected publications in the field of cybersecurity, walks through the importance of each security control for every industry depending on the breaches targeting that industry. The report categorizes 16 different industries across four different world regions, and maps the top 20 CIS Critical Security Controls to remediations based on identified breaches. This report highlights that enterprises can improve their security posture by continuing to increase their adoption in top 20 Critical Security Controls.
Enforcing CIS benchmarks can be a challenging undertaking. It requires a tremendous amount of work from many teams, such as the IT/systems engineering team that has to build group policies to harden their systems, and the security compliance team that has to continuously validate the security control against a hardened system. In addition to these efforts, enterprises typically have complex environments that make it difficult to follow the standard CIS benchmarks.
When policy customization becomes a necessity
While the standard CIS benchmarks are, by default, great for an organization to follow in its initial stages of its policy and compliance program, these benchmarks may not meet the unique requirements of growing and more mature organizations. Security analysts at these more mature organizations have no other option but to start customizing policies by navigating through XCCDF and OVAL files, which form the SCAP standard. Security analysts go through great pains (hats off to them) working through complicated XML files, which are both tedious and error-prone.
Customization of policies is done for a variety of reasons. It can be as simple as editing or disabling rules that don't apply to a specific platform, or as complicated as building a policy from scratch containing shell commands that check for a specific regex pattern in a file. We’re now going to deep-dive into a specific use case to illustrate the benefit of Custom Policy Builder.
Use case: How to enable the InsightVM Scan Engines to assess security controls on the latest version of an OS
Enabling InsightVM Scan Engines to assess security controls on the latest version of an operating system should be a straightforward process. But here’s the catch: It typically takes somewhere between six to nine months for CIS (and other standards organizations) to release a new benchmark for an updated version of operating systems. Enterprises that would like to be on the bleeding edge cannot wait six to nine months to conduct their policy assessments.
Editing Common Platform Enumeration (CPE) of a policy
Let’s say an organization wants to conduct policy compliance scans on the latest edition of macOS, but CIS has not yet released a new benchmark for their version of macOS. Even though CIS has not released a new benchmark yet, there are only a few changes that need to be made, whereas the majority of the rules from their previous version are applicable to the latest platform.
All that needs to be done in this case is to modify the CPE check in OVAL/XCCDF XML files. Directly dealing with XML files is, as mentioned, tedious and error-prone. So, here is where InsightVM’s Custom Policy Builder comes to the rescue.
If you want to assess the existing OSX 10.13 version policy on 10.15 version of the operating systems, here are the steps that need to take place:
- Copy the existing version of macOS policy. Let's say OSX 10.13.
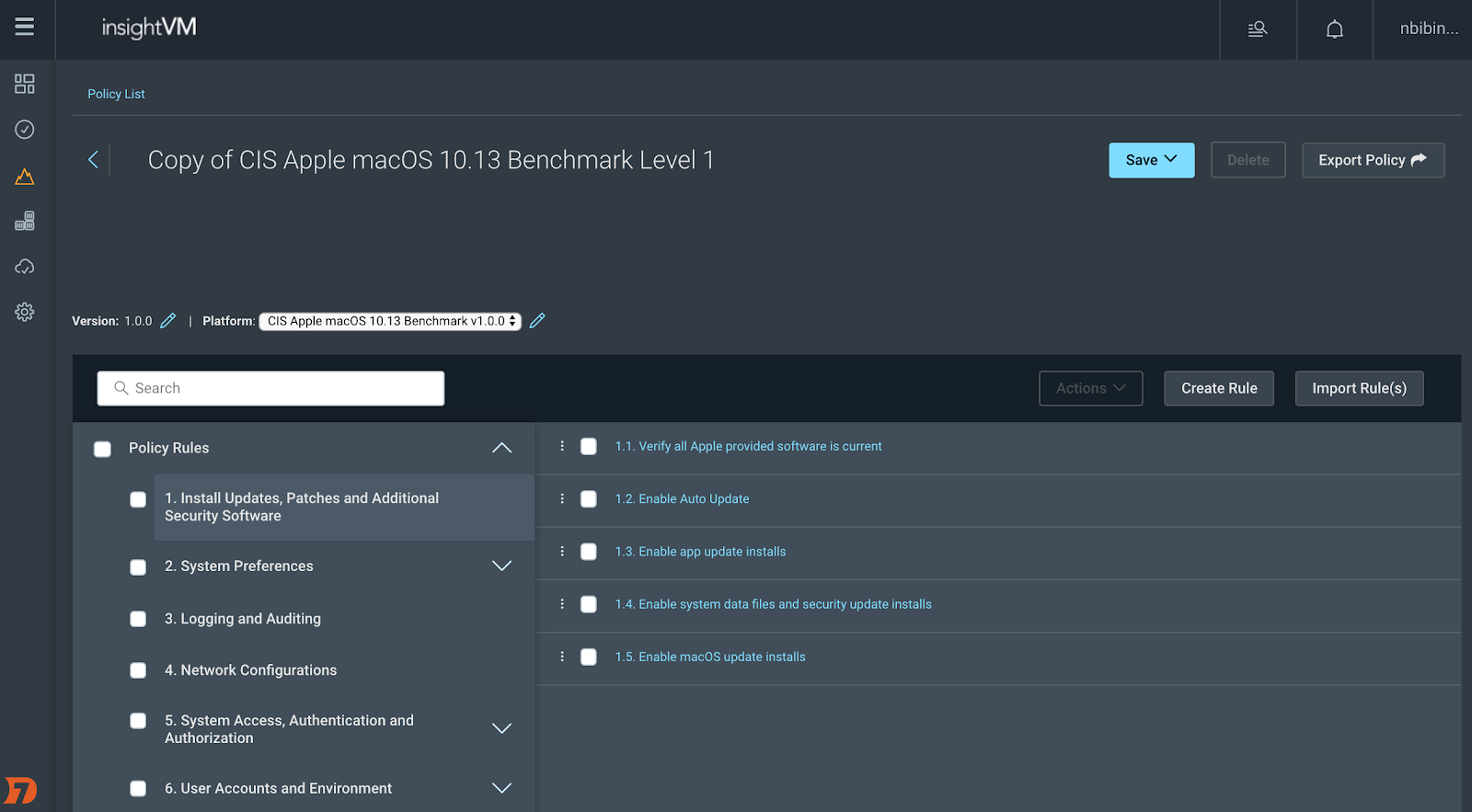
2. Check out the CPE section in the platform specification, as shown below.
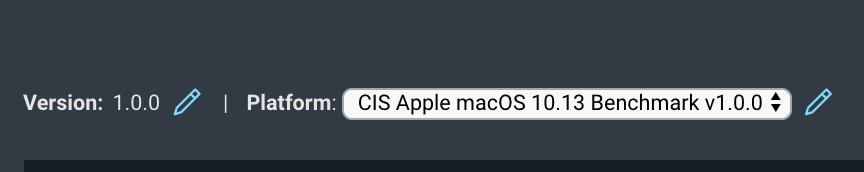
3. Click on the pencil button to edit the CPE. Proceed to edit the CPE on the following screen.
4. The CPE check is a shellcommand_test type that uses a shell command and a regex pattern match to check for the OS.
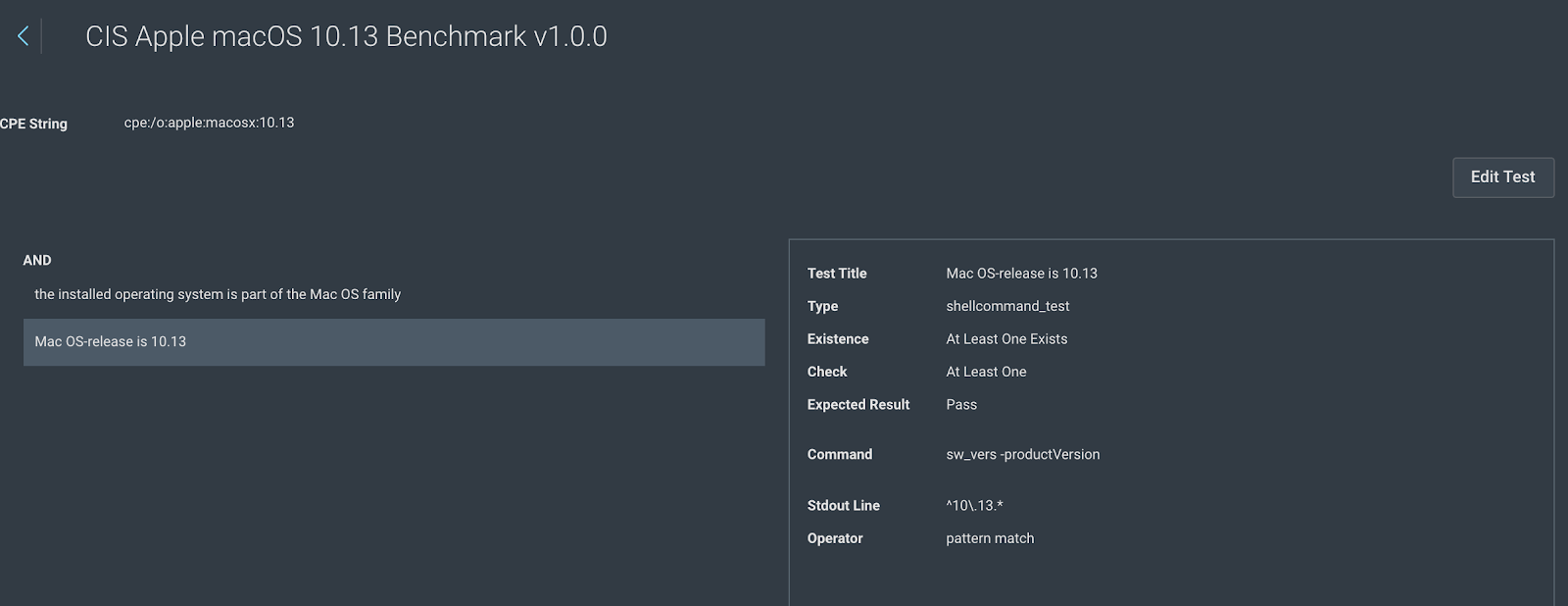
5. Click on “Edit Test” to make all test fields editable, and change the “Stdout Line” to ^10\.15.*
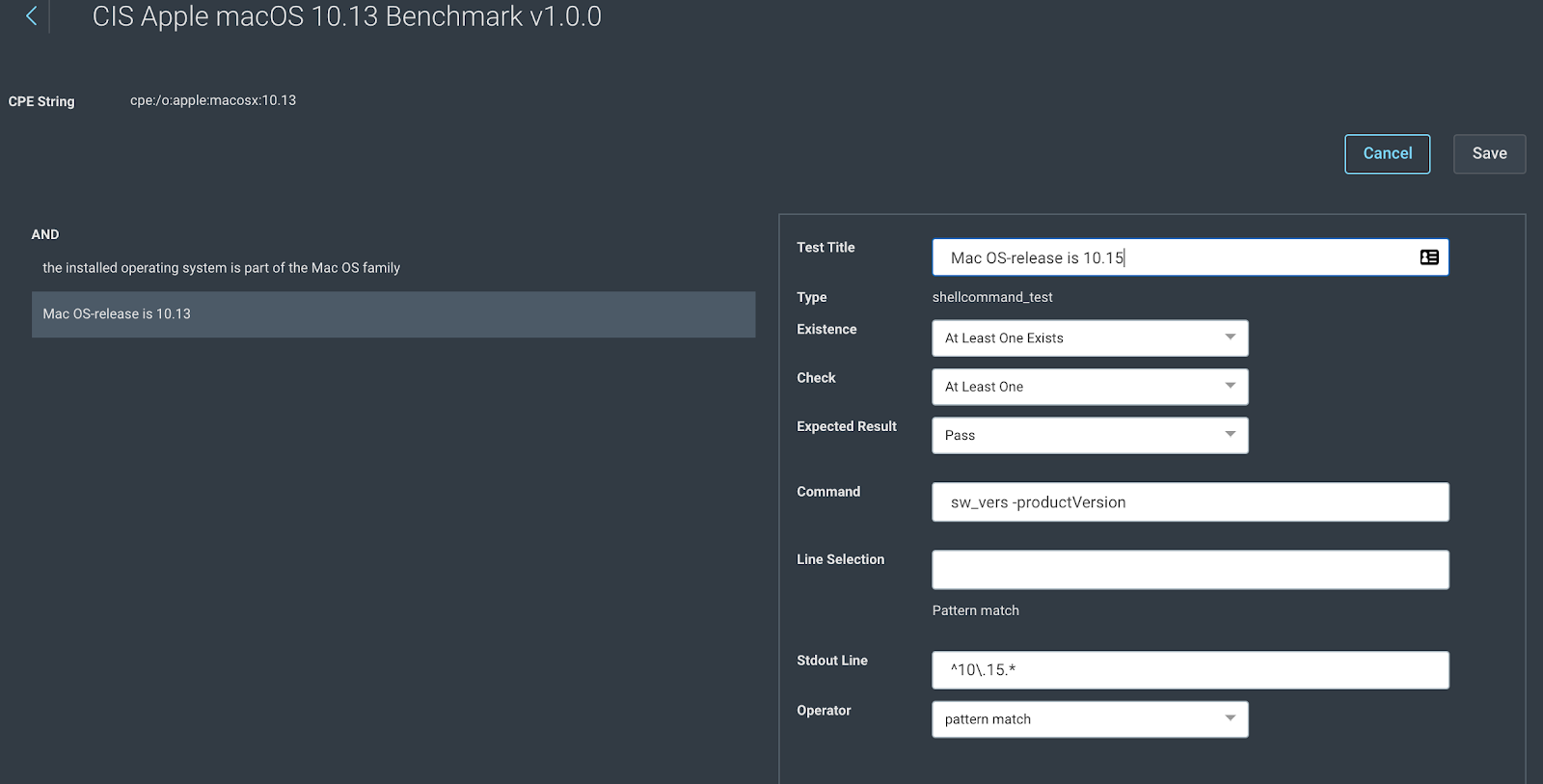
6. Save the test and save the policy.
This custom policy can now be run on a Macbook with OSX version 10.15, and all included rules will be assessed against the 10.15 asset. This use case is just one among many that Custom Policy Builder supports. Need additional help? Check out our help documentation on Custom Policy Builder.
