This post is part two of a two-part blog series on policy customization in InsightVM, Rapid7’s vulnerability risk management solution.
In the first blog post of our Custom Policy Builder series, we learned about how to edit the Common Platform Enumeration (CPE) of a policy in InsightVM. In this post, we are going to focus on commonly used customizations for password policies by our customers.
Password Policy Use Case 1: How to change the default minimum password length for a Windows operating system
Windows Server 2019 Level 1 CIS policy has a default setting of 14 for the rule “1.1.4. (L1) Ensure 'Minimum password length,'” but many enterprises have their minimum password length set to be greater than 16 characters. Many of our customers take advantage of editing this password policy to align with their organizations’ minimum requirements.To modify the password length with Custom Policy Builder in InsightVM, follow the steps below:
- In InsightVM’s “Policy” section, open the Windows 2019 policy that needs to be modified. In our example, we are going to open Windows Server 2019 Level 1 Policy, as shown in the screenshot below. Navigate to the password rule 1.1.4 by opening the password policy group available in the account policies.

- The search feature can also be used to go to rule 1.1.4 by simply searching for either the rule number or “password,” as shown in the below screenshot
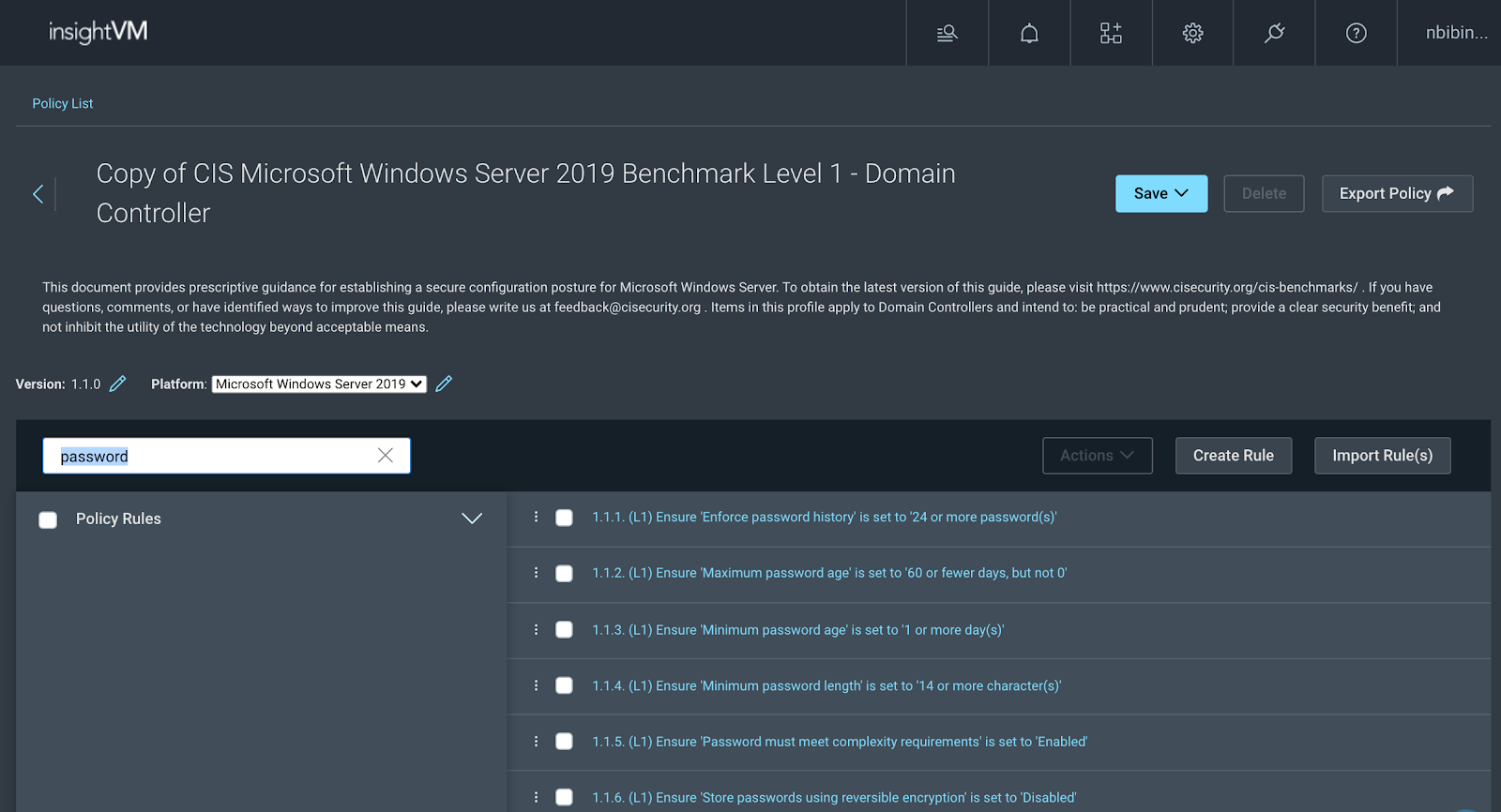
- Clicking on rule 1.1.4 opens the rule for further modification. Identify the value field with “14” characters and change it to 16 or more, depending on your organization’s configuration. It is also advisable to change the test title and value detail (if applicable) fields to maintain consistency.
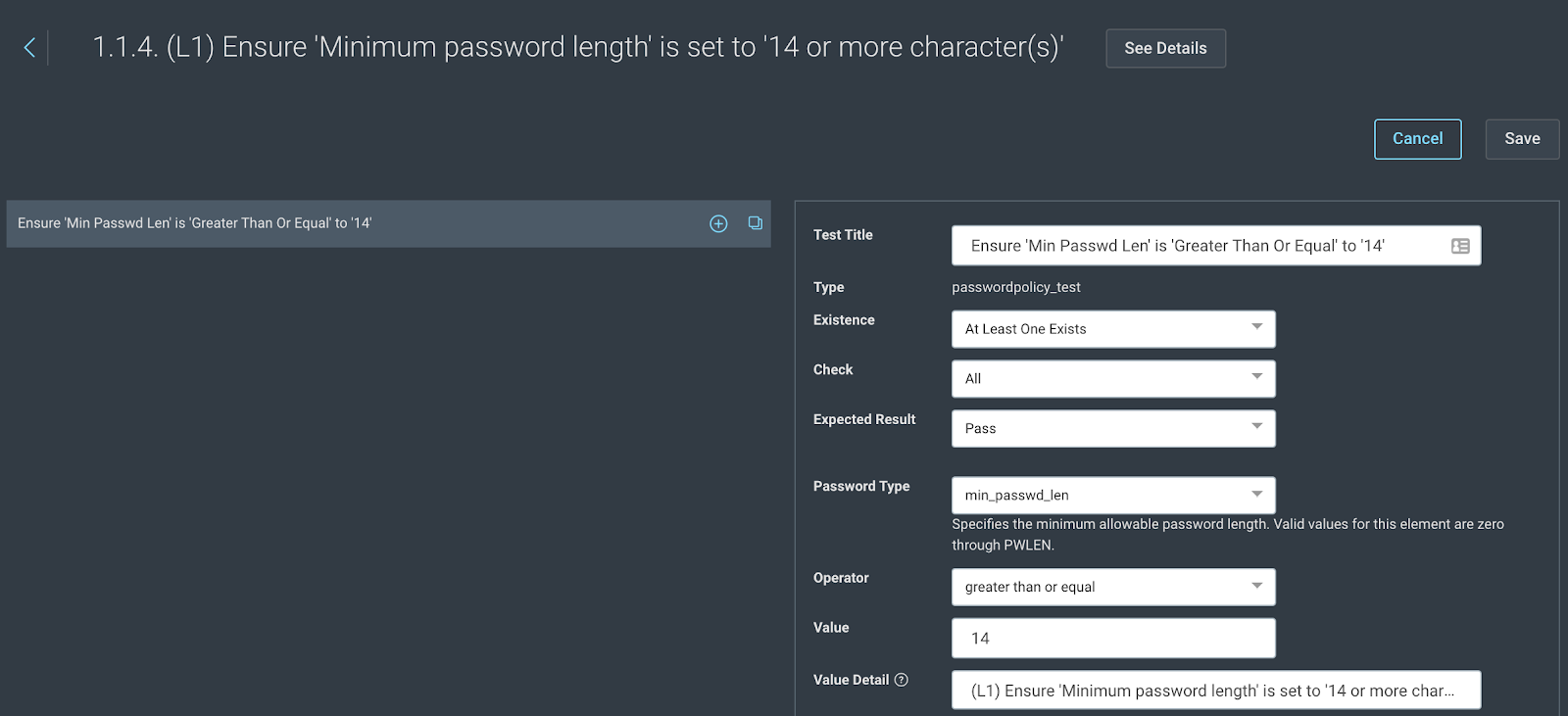
- Finally, save the changes to the test.
Password Policy Use Case 2: How to change the maximum password age according to your security posture
We all know how frustrating it is to follow a 60-day password rotation mandate. Research shows that the password age mandate actually does more harm than good because users almost always tend to game the password policies by setting passwords that follow a certain pattern (albeit a complex one!). Due to this and many more reasons, SANS already calls for a death to password expiration rules. Enterprises are moving toward multi-factor authentication and encouraging the use of password managers to build strong passphrases.
If you are ready to customize the maximum password age by increasing to more than 90 days, follow the below steps:
- Open the Windows 2019 policy that needs to be modified. In our example, we are going to open Windows Server 2019 Level 1 Policy, as shown in the screenshot below. Navigate to the maximum password age rule 1.1.2 by opening the password policy group available in the account policies.

- Clicking on rule 1.1.2 opens the rule for further modification. Notice that the rule contains two different tests, and both must pass. For this change, we are only going to modify the first rule “Ensure 'Max Password Age' is 'Less Than Or Equal' to '5184000'” which amounts to 60 days in seconds. Identify the value field and change it to 7776000 to amount it to 90 days in seconds. It is also advisable to change the test title and value detail (if applicable) fields to maintain consistency.
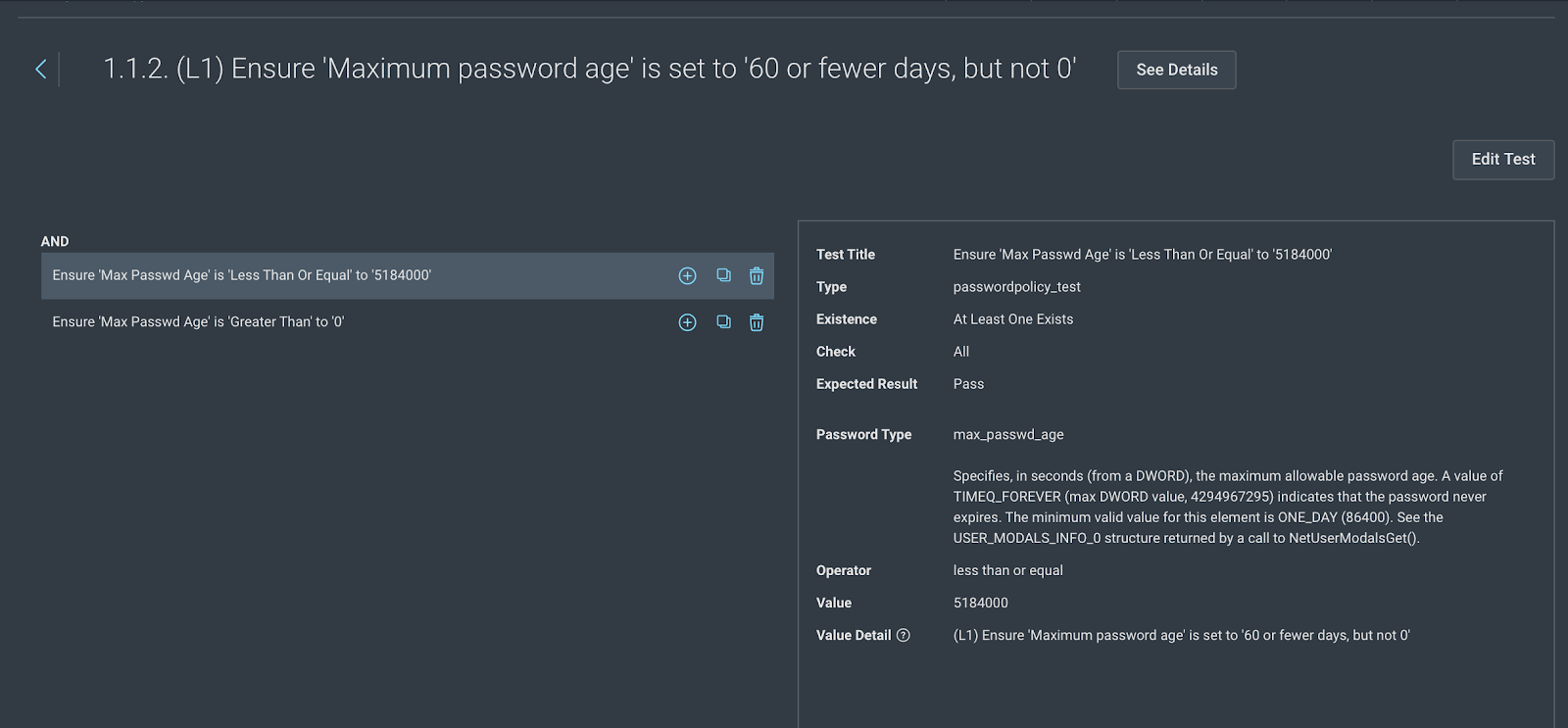
- Finally, save the changes to the test.
These two use cases are just some among the many that Custom Policy Builder supports. Need additional help? Check out our help documentation on Custom Policy Builder.
Interested in this policy editing and customization, but not yet an InsightVM customer? Start a free 30-day trial today to test it out for yourself!
