On July 22, Cisco released a patch for a high-severity read-only path traversal vulnerability in its Cisco Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) products. A successful compromise will allow unauthenticated, remote attackers to perform directory traversal attacks and read sensitive files on their chosen targets.
As noted in the AttackerKB information, the vulnerability is due to a lack of proper input validation of URLs in HTTP requests processed by an affected device. An attacker could exploit this vulnerability by sending a crafted HTTP request containing directory traversal character sequences to an affected device. A successful exploit could allow the attacker to view arbitrary files within the web services file system on the targeted device.
The web services file system is enabled when the affected device is configured with either WebVPN or AnyConnect features. This vulnerability cannot be used to obtain access to ASA or FTD system files or underlying operating system (OS) files.
As of July 22, 14:56 ET, a public proof-of-concept (PoC) was published by Ahmed Aboul-Ela demonstrating a successful exploitation via one path endpoint:
hxxps://<domain>/+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../
This was followed up at 23:31 ET (by the same individual) with another path endpoint susceptible to this flaw:
hxxps://<domain>/+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=%2bCSCOE%2b/portal_inc.lua
Mitigating the Cisco ASA / Firepower vulnerability (CVE-2020-3452)
Rapid7 encourages immediate patching of vulnerable ASA/FTD installations to prevent attackers from obtaining sensitive information from these devices which may be used in targeted attacks. There are no workarounds that address this vulnerability.
Cisco has provided fixes for all supported versions of ASA and FTD components. Cisco ASA Software releases 9.5 and earlier, as well as Release 9.7, along with Cisco FTD Release 6.2.2 have reached the end of software maintenance and organizations will have to upgrade to a later, supported version to fix this vulnerability.
Exposure information of CVE-2020-3452
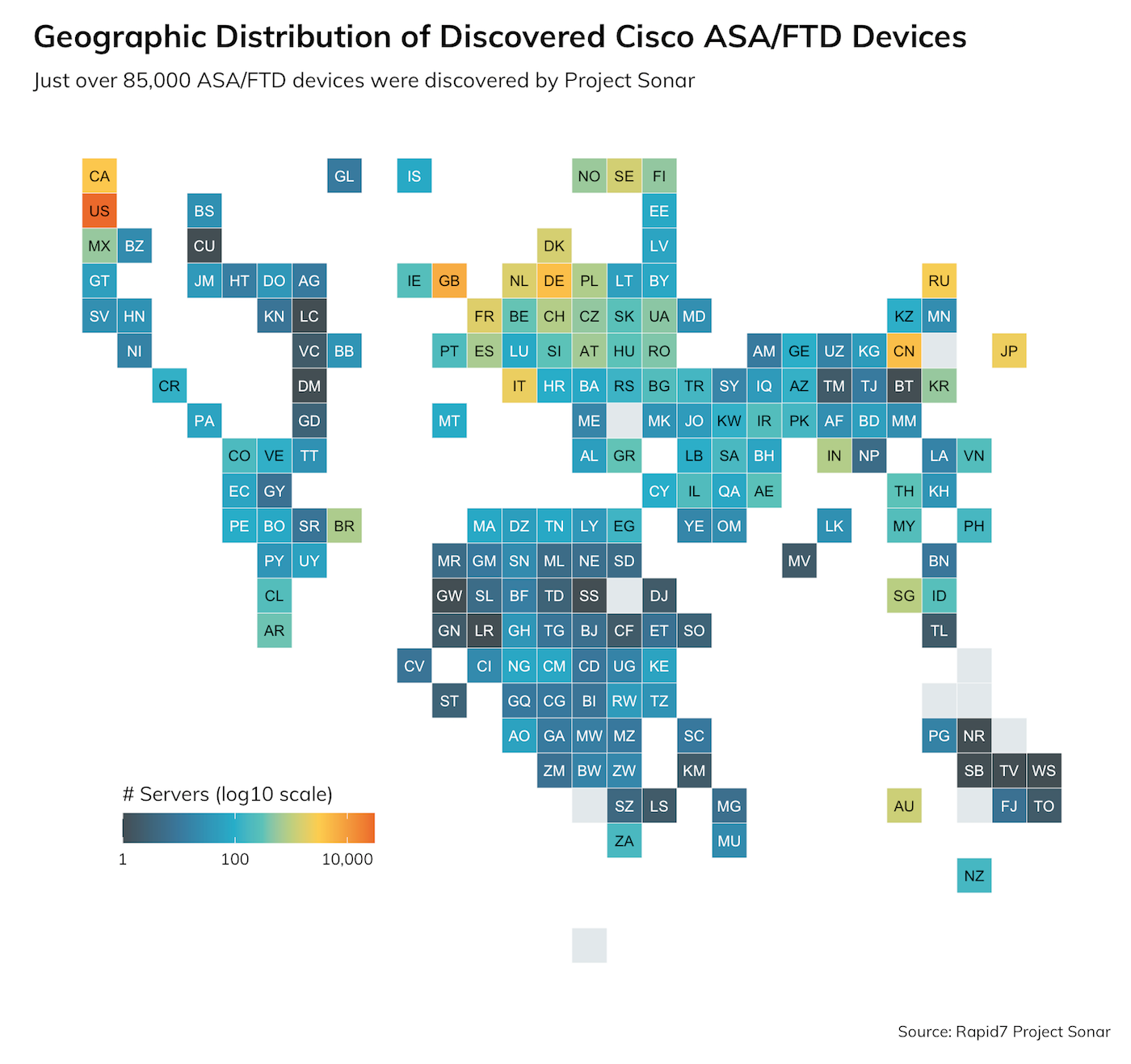
Rapid7’s Project Sonar discovered just over 85,000 ASA/FTD devices, 398 of which are spread across 17% of the Fortune 500:
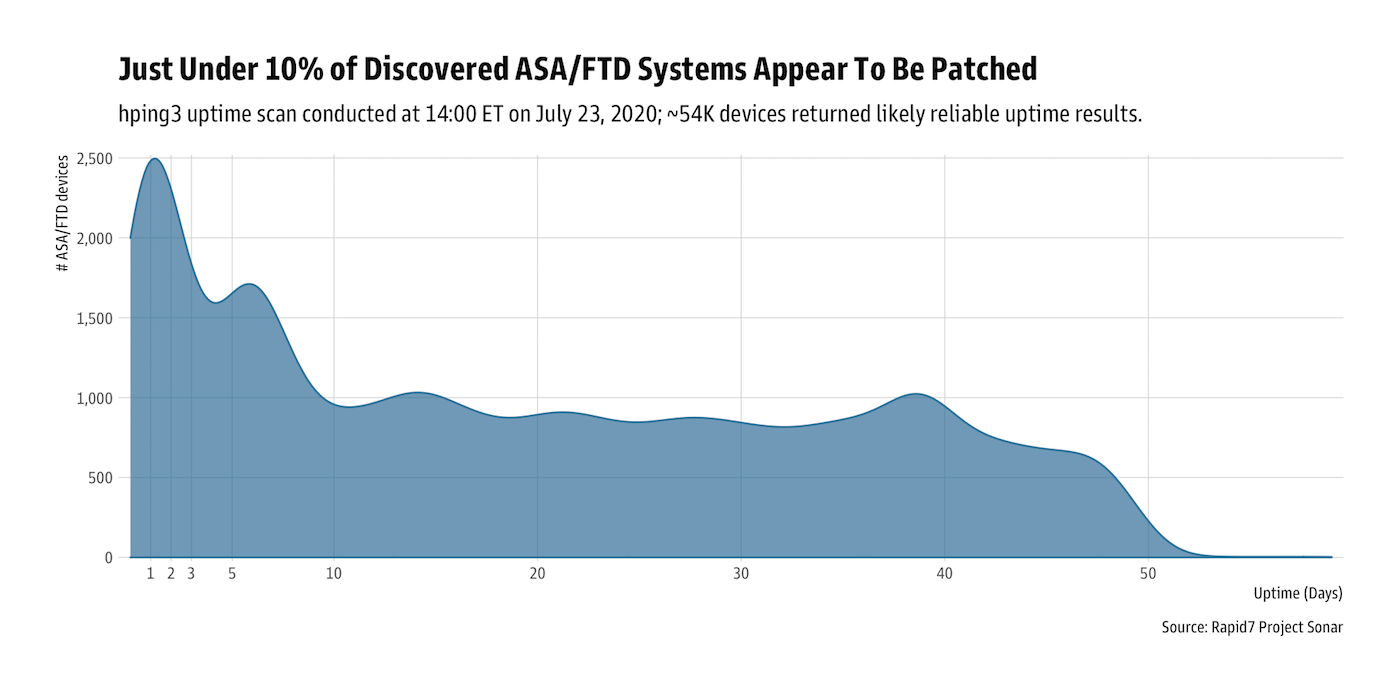
Since it is difficult (if not impossible) to legally fingerprint Cisco ASA/FTD versions remotely, Rapid7 Labs revisited the “uptime” technique described in a 2016 blog post for another Cisco ASA vulnerability, which shows that only about 10% of Cisco ASA/FTD devices have been rebooted since the release of the patch. This is a likely indicator they’ve been patched (only 27 of the 398 detected in Fortune 500 companies appear to have been patched/rebooted):
Rapid7 Labs will monitor Project Heisenberg for exploit attempts and update this blog post with any relevant findings.
Rapid7 InsightVM and Nexpose customers have full coverage for detecting vulnerable configurations.
Updates
- July 24, 2020: Project Heisenberg observed IPv4 46.30.189.6 looking for Cisco ASAs internet-wide across 560 ports on 2020-07-18 (i.e. before the vulnerability disclosure). This IP is not on GreyNoise benign list. We're also seeing intermittent use of the public exploits in Heisenberg despite not emulating Cisco ASAs.
