Zoom adoption has skyrocketed with spikes in remote working, but web application security needs to be a top priority to avoid disruptions in collaboration
Our SIEM, InsightIDR strives to make it easy to keep up with rapidly evolving environments. Most recently, for many organizations that likely includes an increase in remote endpoints, infrastructure as a service, and web applications. Even prior to COVID-19, the use of web applications has been growing steadily for the past several years, and an increasing remote workforce has accelerated the trajectory of this adoption. But this greater adoption has meant web applications are a growing target for attackers. The recently published Verizon Data Breach Investigations report highlights this trend, showing a staggering increase in web application breaches and attacks. Web applications were involved in 43% of breaches and nearly 90% of hacking targets were web applications. Yikes.
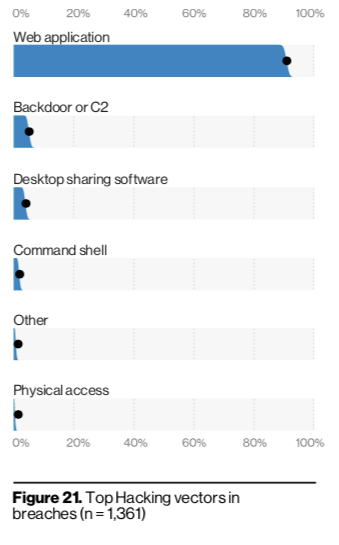
Our unoriginal passwords and good old-fashioned phishing have followed us into the cloud, and stolen credentials are the top gateway to compromised web applications. It’s no surprise that credential theft remains the No. 1 tactic used for hacking, according to the VDBIR. It’s the easiest way for attackers to get in, and many Zoom users learned this the hard way over the past few months, with more than 500,000 hacked Zoom accounts being given away for free on the dark web, according to Forbes. This—combined with a spike in “Zoom bombings” where strangers were getting access to enter and troll Zoom meetings—created a lot of headaches for Zoom and its users.
While Zoom has been quick to address privacy and security issues, it still brings up a good lesson for security teams: We can’t let the ease of adoption of these applications trump fundamental security best practices to ensure safety and privacy of users.
Zoom has made several product changes and shared a detailed blog of how to prevent hackers from bombing into meetings. These tips include:
- Make meetings private as a default
- Don’t use your personal meeting ID to host widely shared or public events.
- Use meeting passwords to help control attendanceYou can find an overview of Zoom’s security policies, resources, and configuration tips here.
Zoom Event Source in InsightIDR
Even with the most secure configurations in place, it’s still important to understand who is logging in and out of Zoom at your organization, which is why we’ve added it as a supported event source in our SIEM, InsightIDR.
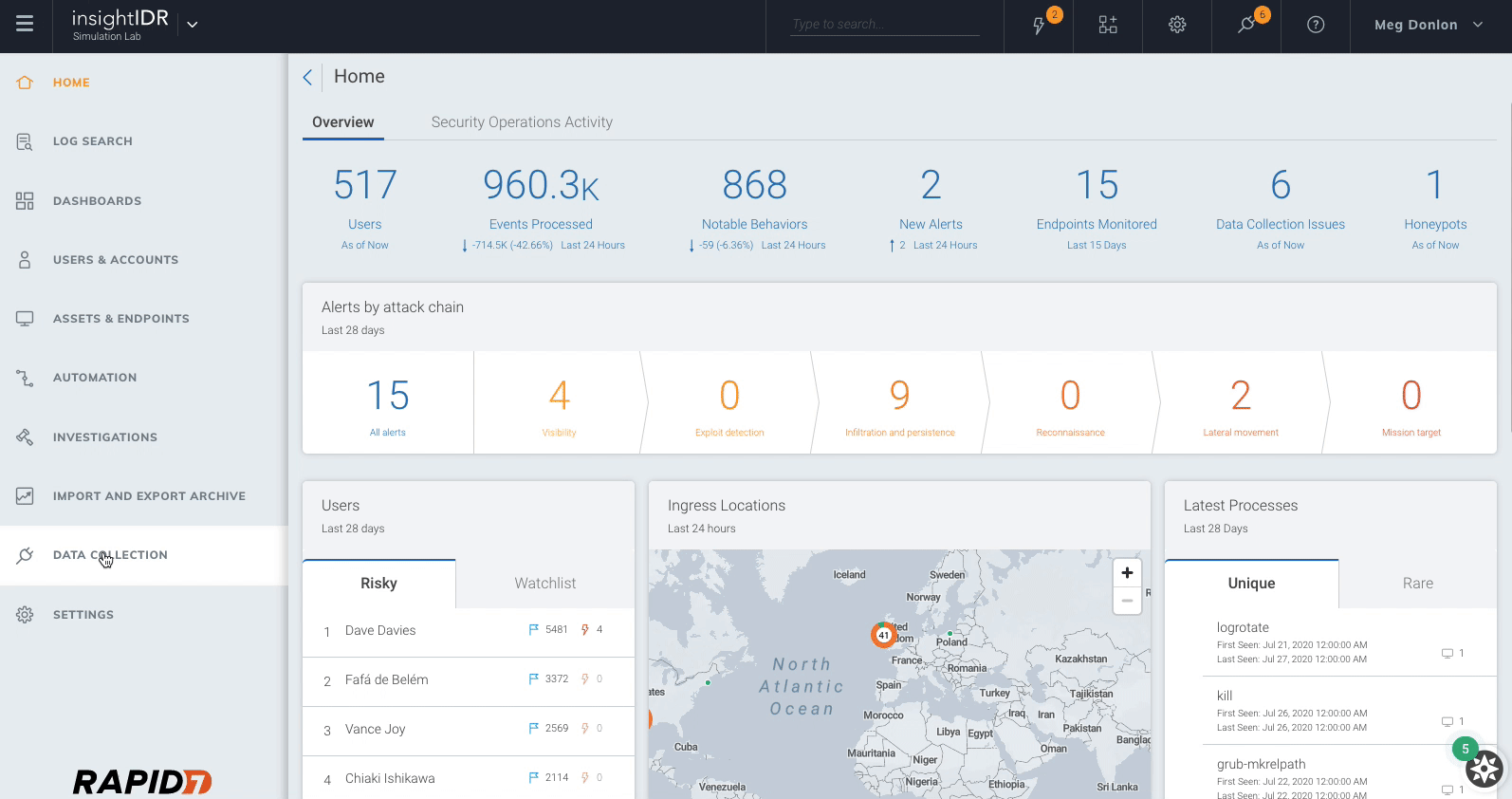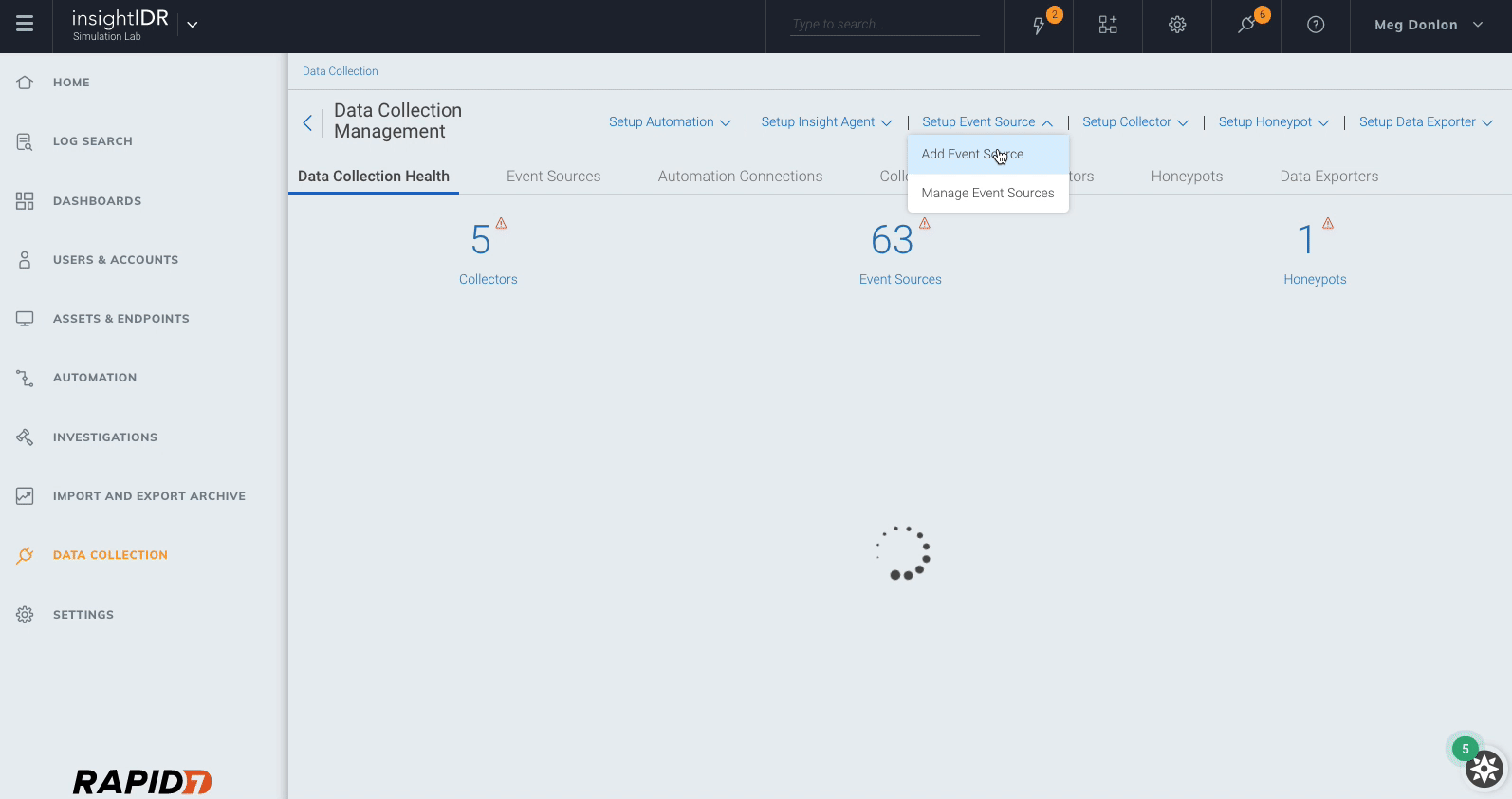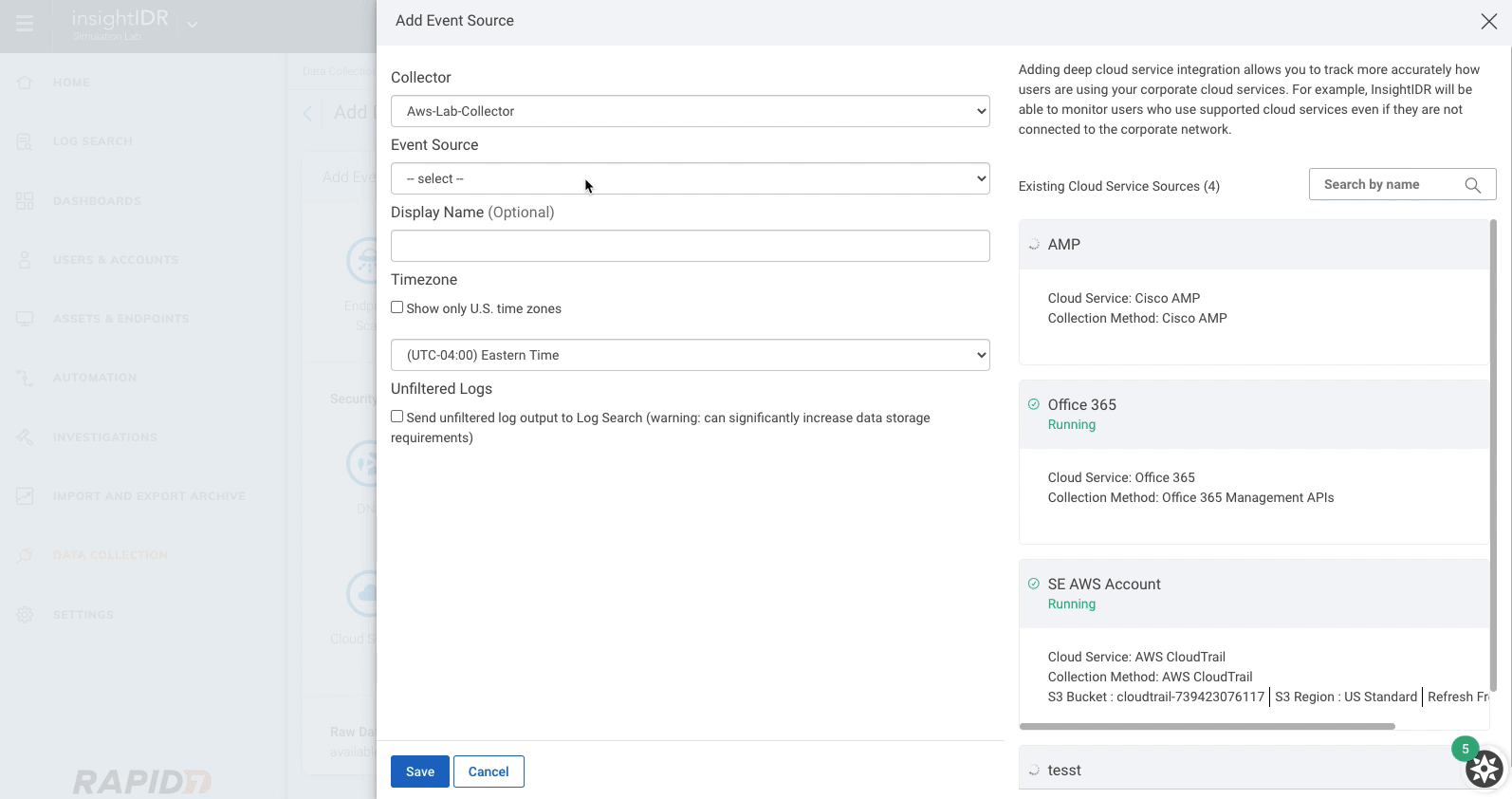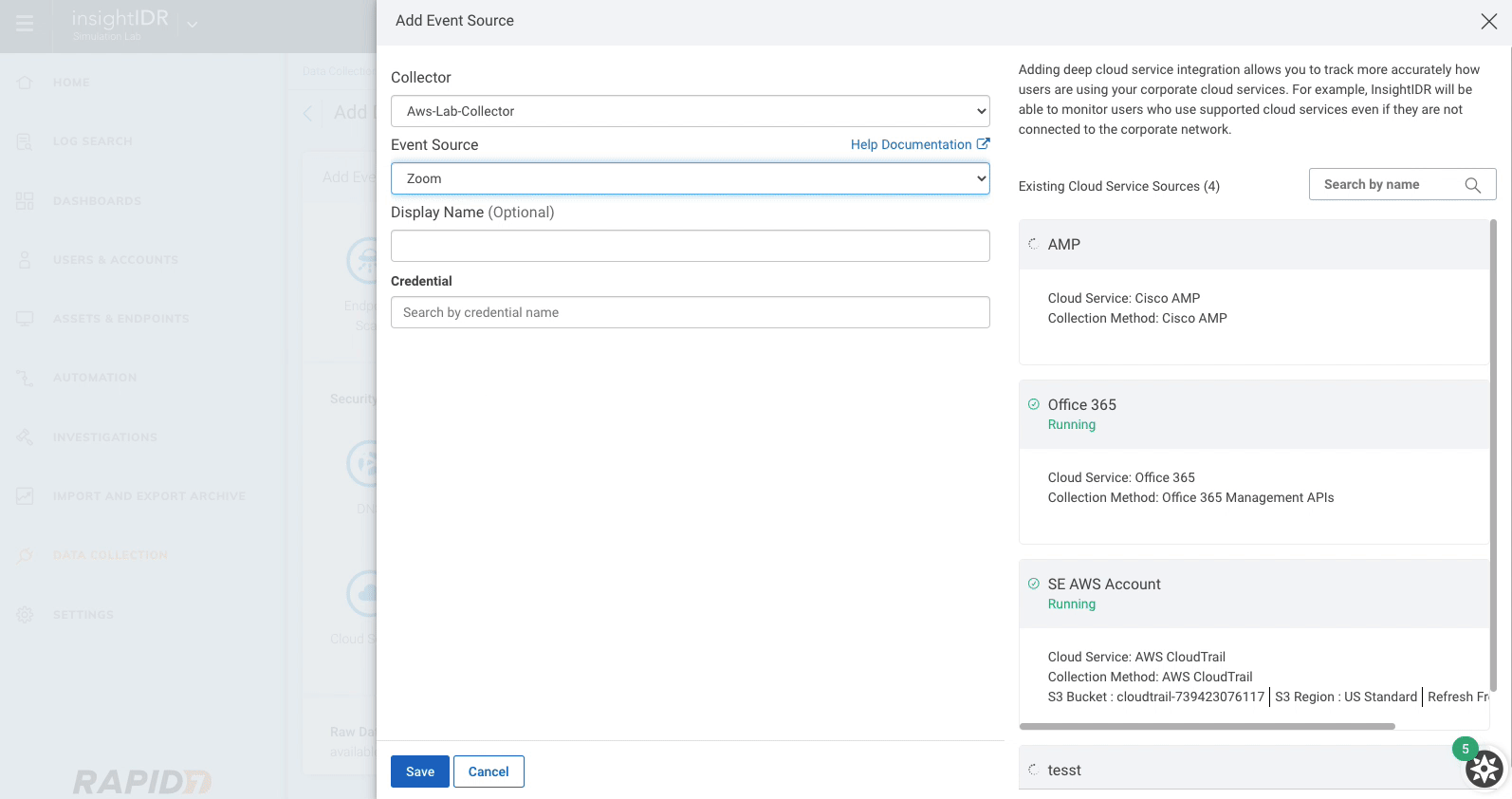
This integration leverages Zoom’s Sign In / Sign Out Activity report API to capture user Zoom activity. To take advantage of this integration, you should:
- Verify that you have a license for Zoom Pro, then create a JWT App (if you haven’t already) and obtain the API Key and API Secret. See instructions here.
- In InsightIDR, go to Data Collection on the left menu, click the Setup Event Source dropdown, and choose Add Event Source
- From the Cloud Service section, click the Zoom icon.
Once the connection is made, you’ll have this authentication information alongside all of your other security data in InsightIDR, meaning you can quickly monitor who is logging in and out of Zoom within your organization and spot potential malicious actors.
With better web application monitoring in place, you’re freed up to worry about the important things—like finding the perfect Zoom background.
Happy Zooming!

