In this blog post, we are going to talk about a couple of older, lesser-known features that can still provide amazing value in your vulnerability management program using InsightVM. The first thing we will be covering are vulnerability categories, where to find the categories, and how we can leverage them as asset filters with Dynamic Asset Groups (DAGs). These categories will allow us to create one of my favorite workflows to set up and run on new installations to both track and remediateion Default Account vulnerabilities. We will also see how we can use this workflow as a template for additional similar workflows with different vulnerability categories.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
SubscribeVulnerability Categories and Where to Find Them in InsightVM
The first thing I like to show every customer during a deployment while we are exploring the options in the scan template is the Vulnerability Categories. You can see a list of all vulnerability categories in the Vulnerabilities tab of any scan template. It will show a list of all of the different categories, and you can also dig into each category if you want to and see all of the actual vulnerability checks that reside in each category.
Navigate to the Vulnerability Check Tab on the Scan Template and click on ‘Add Categories’
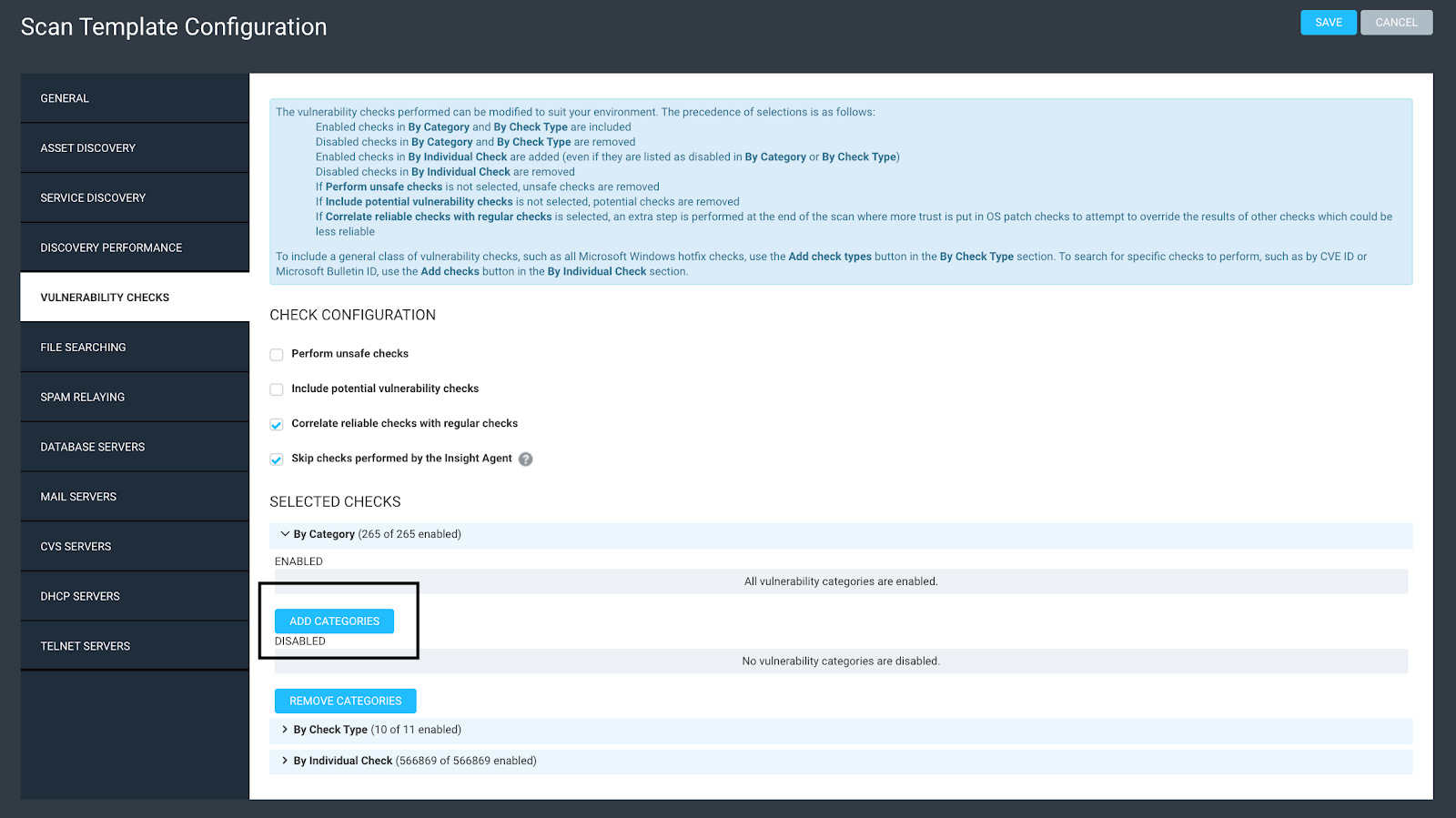
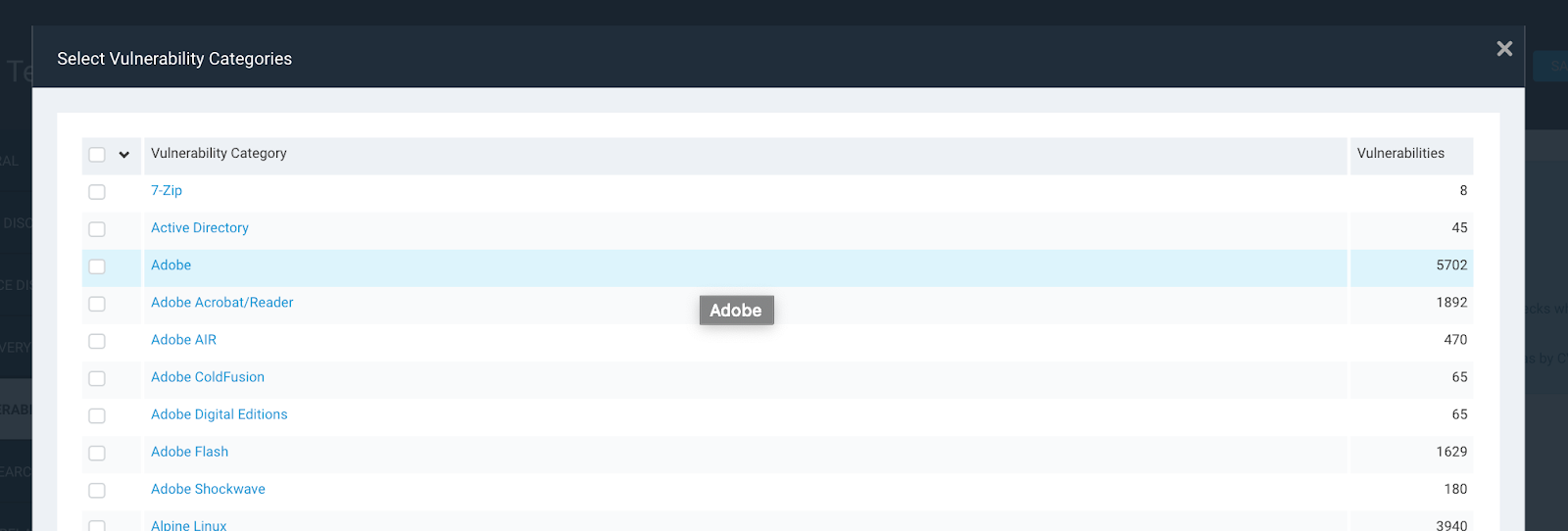
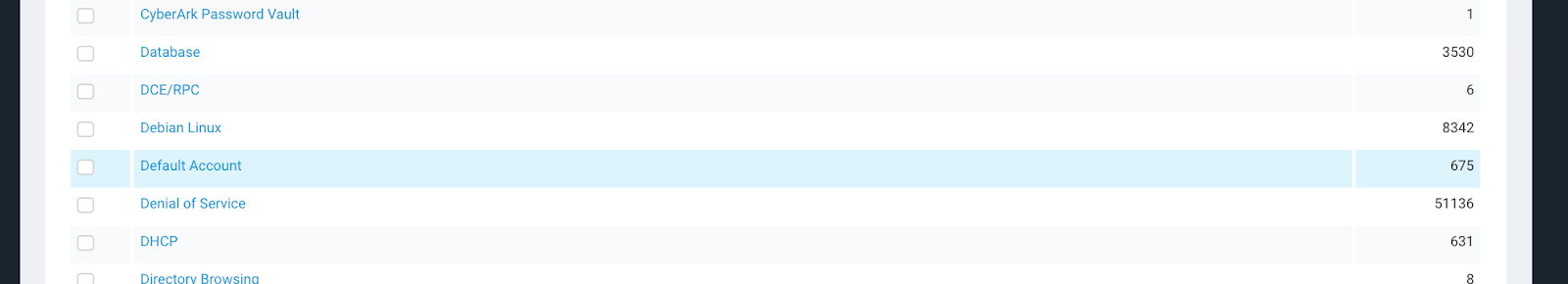
Now that we know about this list of vulnerability categories, let’s focus on my favorite vulnerability category, ‘Default Account’. This category will show all of the vulnerability checks associated with assets that are vulnerable to default account creds. An example of this might be a system running Telnet on port 23 using the username ‘admin’ and the password ‘admin’. This type of vulnerability should be the first thing that is cleaned up in your vulnerability management program, as they can be exploited with near zero hacking experience.
Creating a Dynamic Asset Group (DAG) in InsightVM
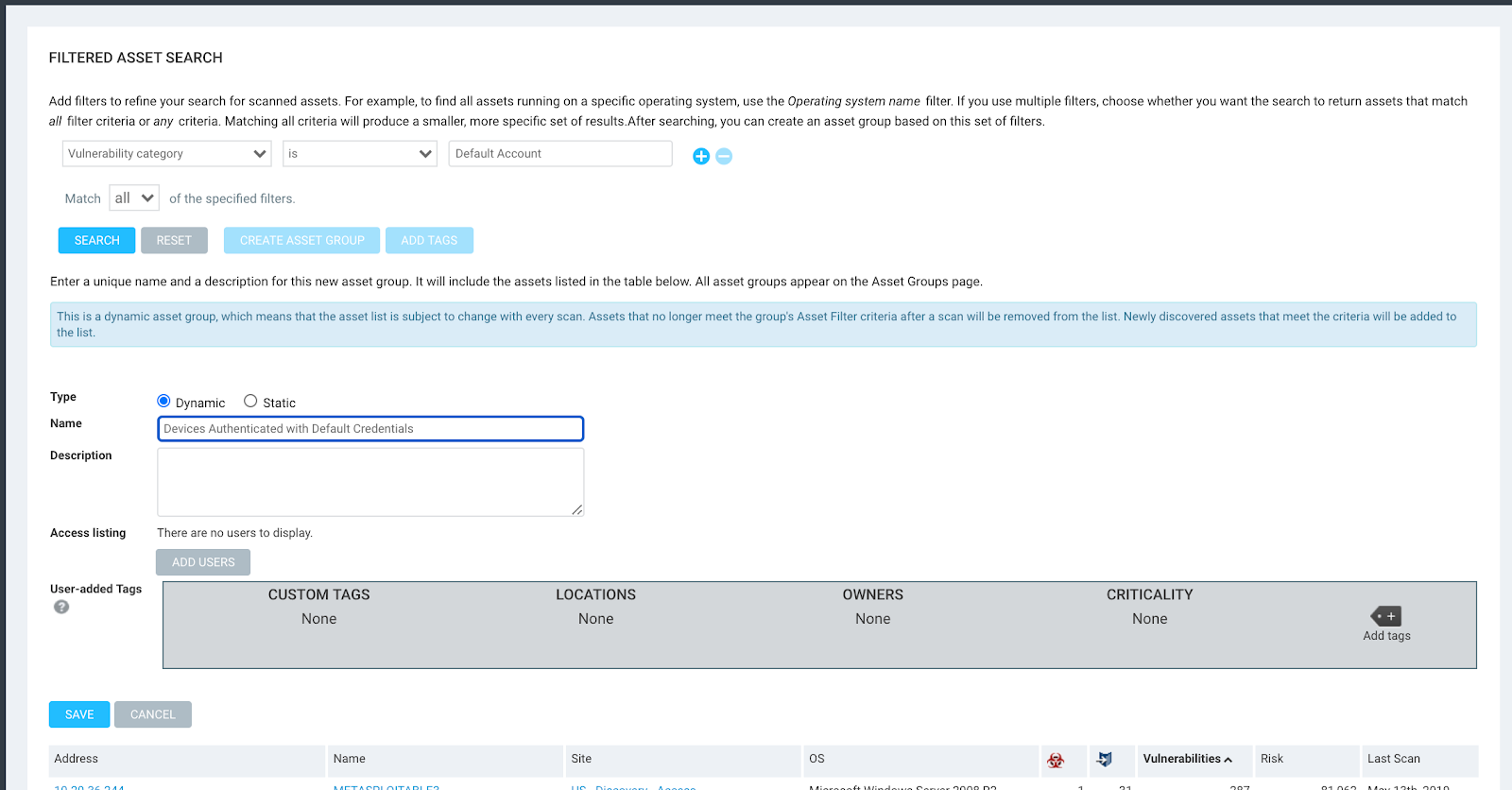
To take advantage of the ‘default account’ vulnerability category, the first thing I recommend doing is creating a Dynamic Asset Group or DAG. When you create a DAG, you can select ‘Vulnerability Category’ IS ‘default account’, hit search, and save the DAG with the name ‘Devices Authenticated with Default Creds’. This will show all of your assets that have default account vulnerabilities. The challenge is, if an asset has 1,000 vulnerabilities, good luck trying to figure out which vulnerability on that asset is the default account vulnerability. Let’s address how to overcome this challenge.
Create a Dynamic Asset Group (DAG)
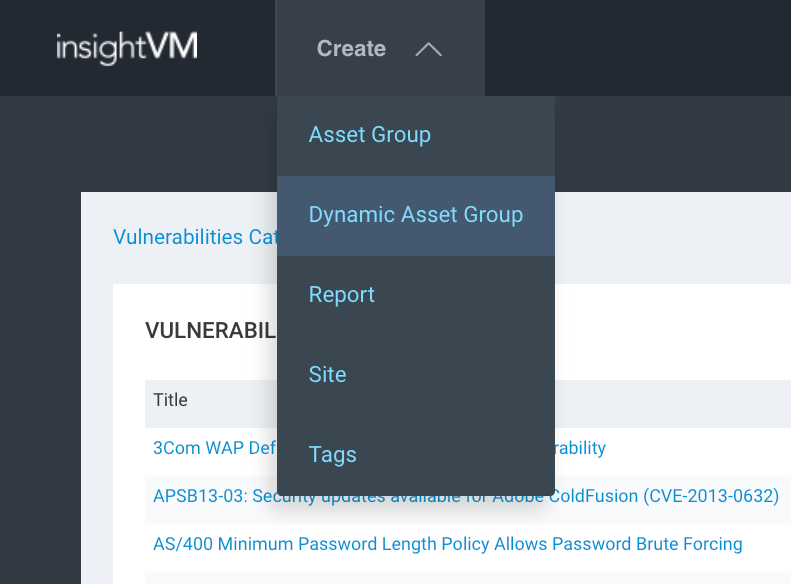
Create Dynamic Asset Group with ‘Vulnerability Category IS Default Account’:
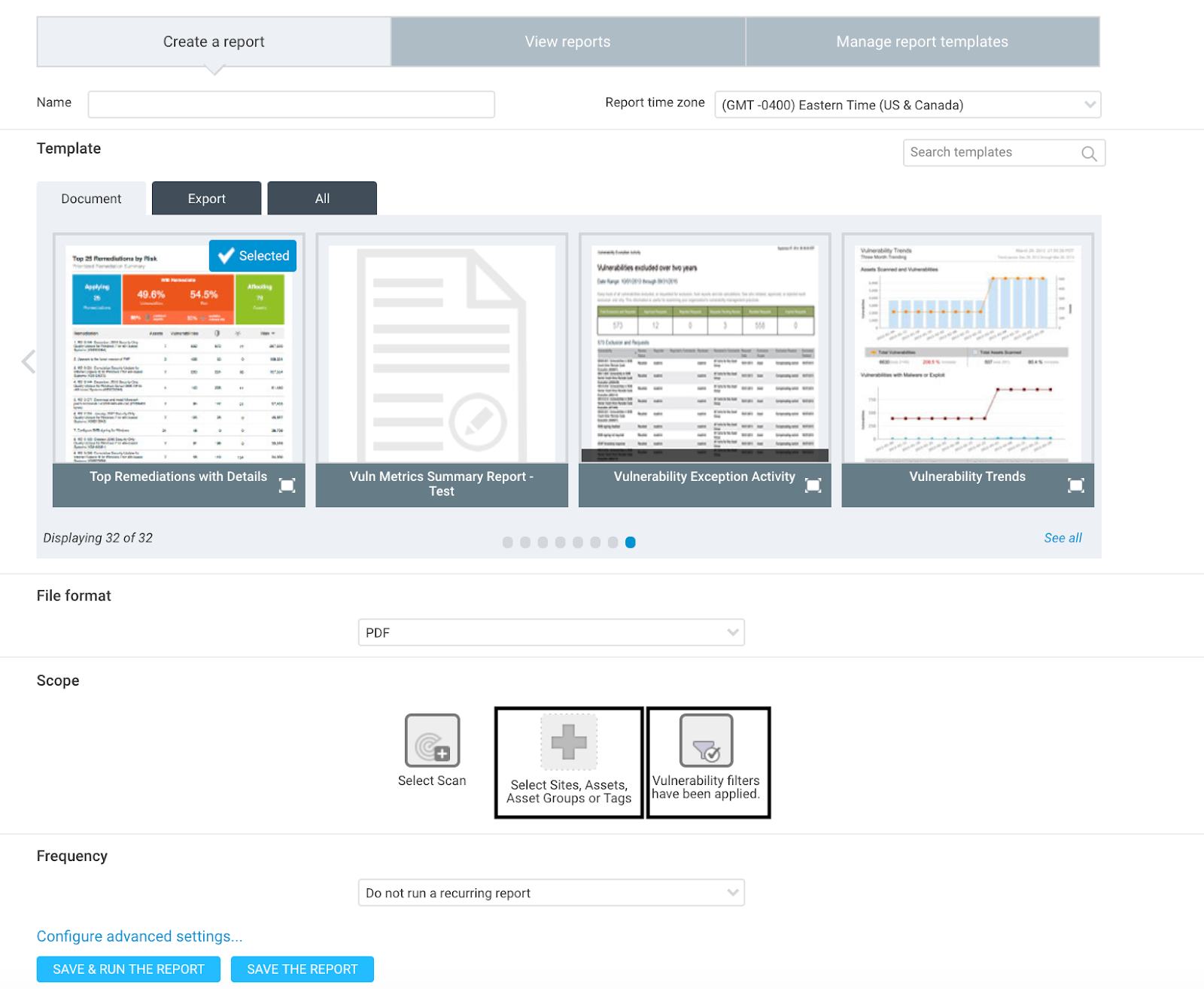
To solve this challenge, we can use a lesser-known feature when creating a report called a ‘Vulnerability Filters have been applied’. Then, scope a report with the ‘Devices Authenticated with Default Creds’ DAG we just created in the previous step.
Reporting on Default Account Vulnerabilities in InsightVM
Create Top Remediation report:
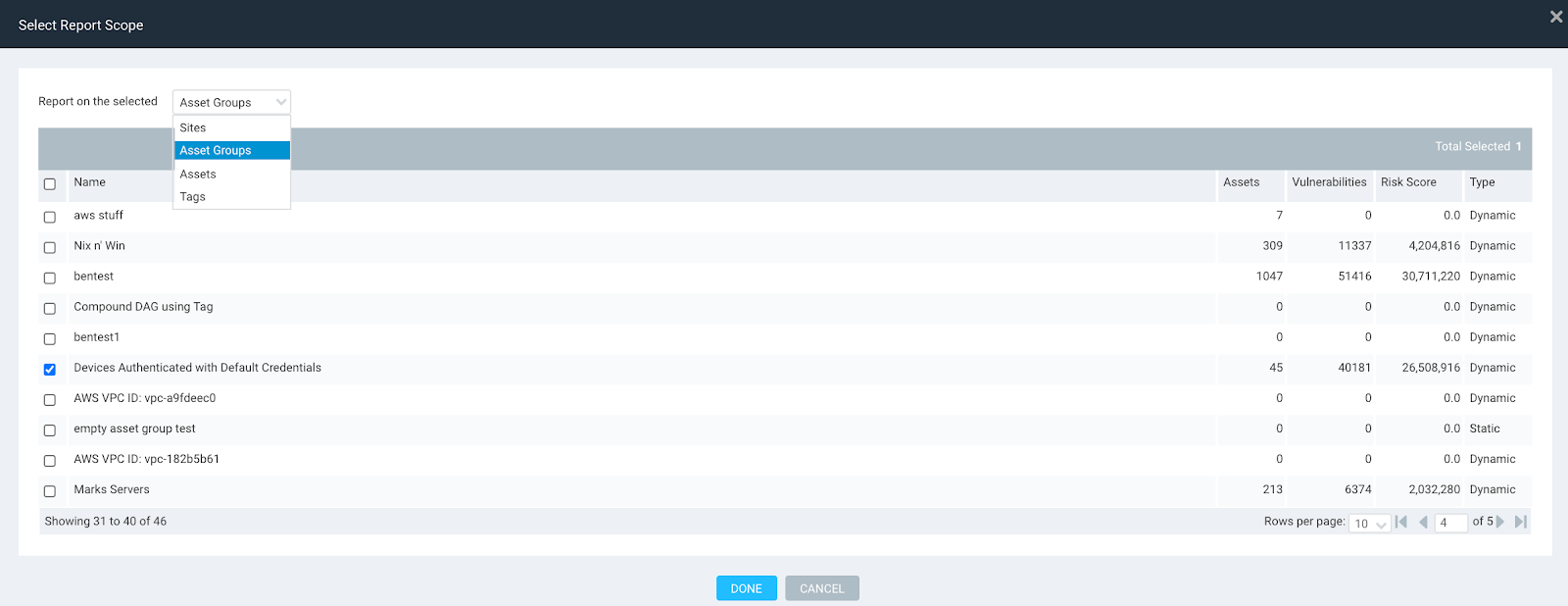
Scope with ‘Devices Authenticated with Default Credentials ‘Asset Group’ created in previous step:
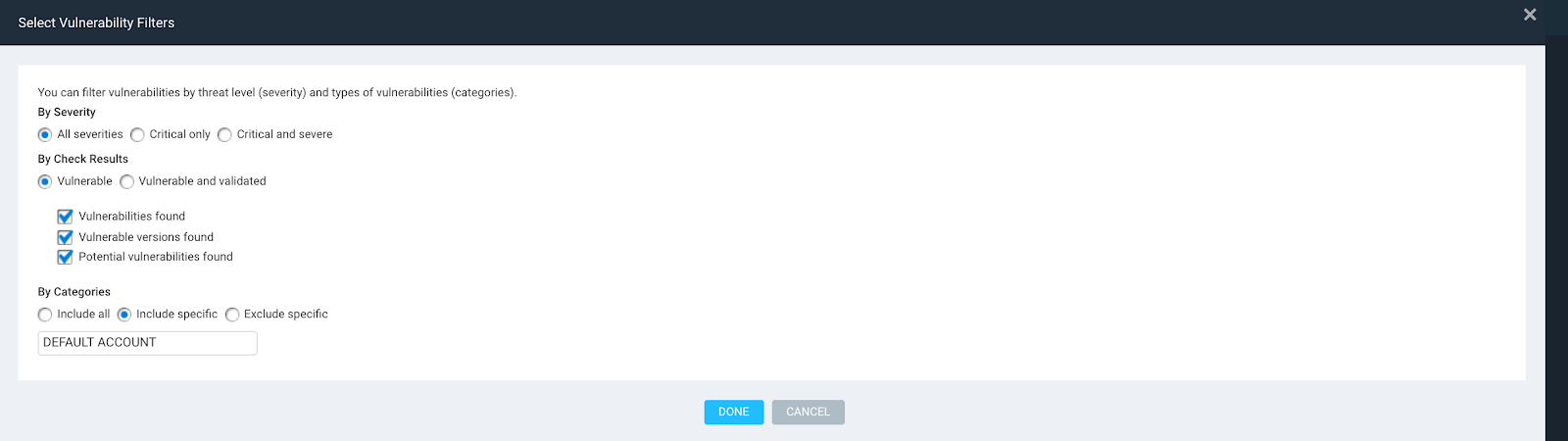
Set Vulnerability Filter to Include Specific Category ‘Default Account’:
Save and Run the report:
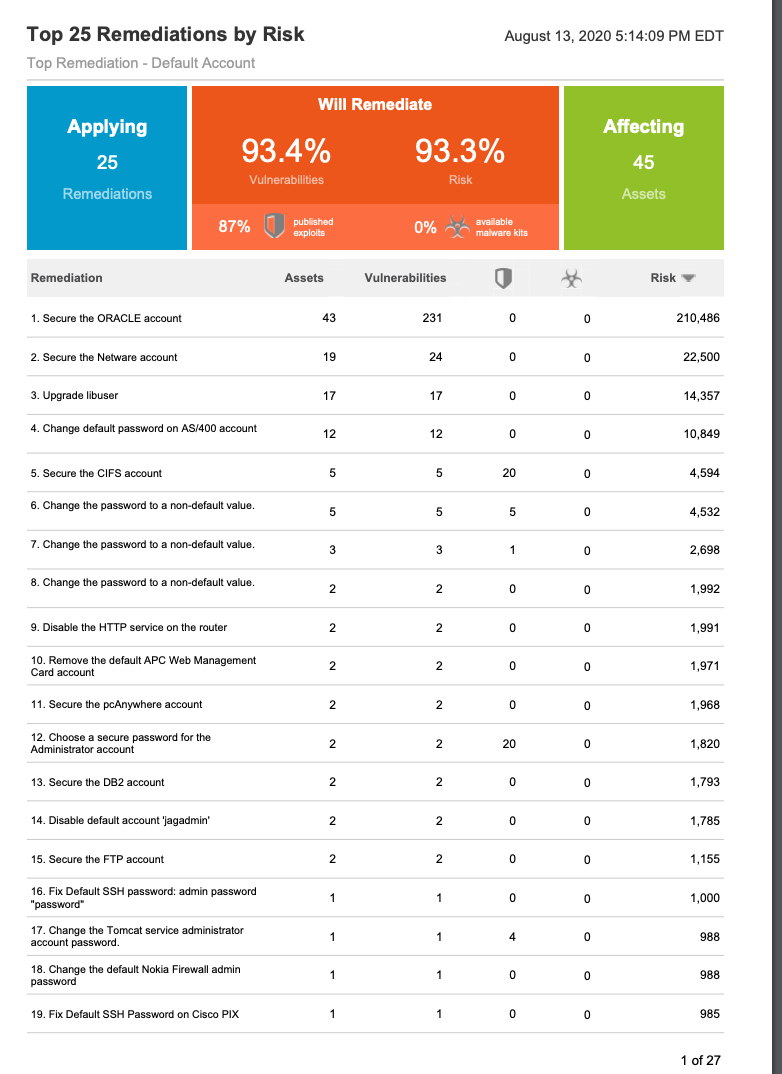
By combining the ‘Devices Authenticated with Default Creds’ DAG with the filter in a report (I recommend the ‘Top 25 Remediation with Details’ report), we can now get a report that shows only assets with default account vulnerabilities and only shows default account vulnerability solutions. This report will allow you to see exactly which ‘default account’ vulnerability there is on each asset and the solution on fixing the vulnerability.
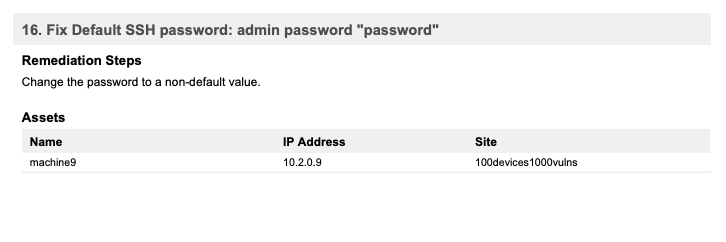
Example Default Account Vulnerability and Solution:
This workflow is something I like to show folks as a way to start things off in a positive direction. Not only can these types of checks be a great thing to fix first when starting your vulnerability management program, but it can also start establishing some amazing credibility and respect as you start calling out teams or individuals for allowing this to happen in the first place.
Now that you have seen this cool workflow and know how to see all of the possible vulnerability categories, we can use the same workflow with any vulnerability category. Some other vulnerability categories I would recommend using are ‘Obsolete OS’, ‘Insecure Remote Access’, ‘Obsolete Software’, or something bigger like ‘Adobe’.
