Rapid7 detection and response customers have access to, and insights from, our experts and research driving the industry forward. This includes a robust library of out-of-the box detections curated from our global managed SOC team, plus insights from Rapid7’s global threat intelligence network.
InsightIDR has always prioritized detections first to accelerate time to value and threat identification for our customers. We are excited to announce that to build on this, we are now giving customers the option to also access the additional telemetry behind these detections with Enhanced Endpoint Telemetry (EET).
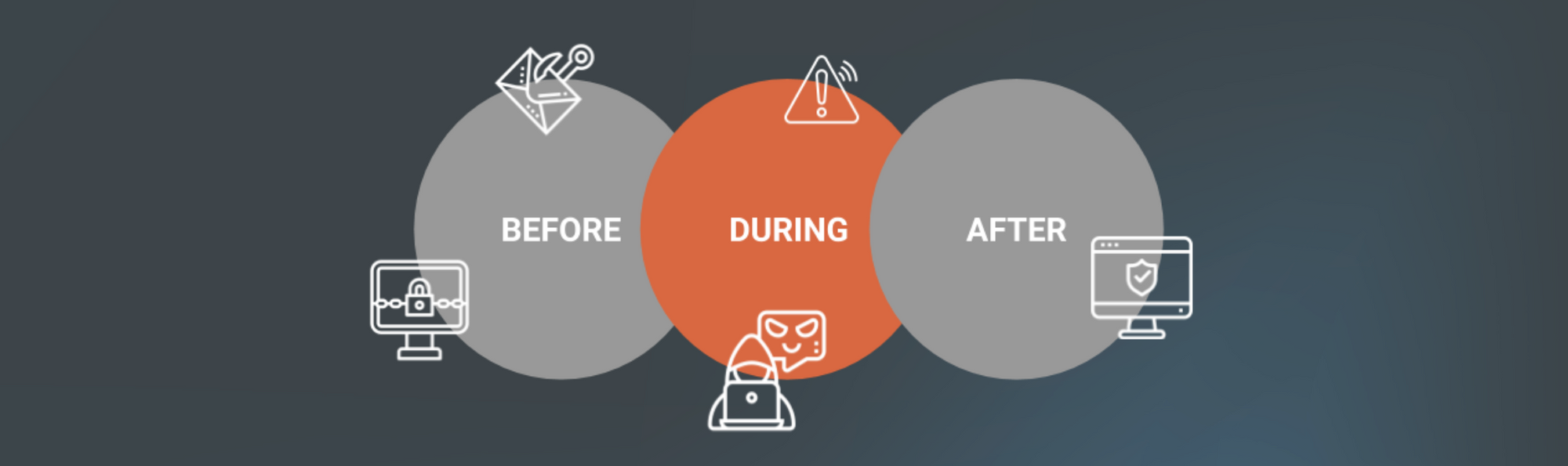
EET is the collection of detailed activity logs that are sent to InsightIDR each time a process starts on a monitored endpoint. In short, these logs give visibility into all endpoint activity—whether events occurred before, during, or after a detection. With this holistic view into endpoint activity, customers can unlock custom use cases and enrich investigations in InsightIDR.
Enhanced Endpoint Telemetry brings powerful MDR capabilities into InsightIDR
Rapid7’s Managed Detection and Response (MDR) team already uses this enhanced endpoint data in almost all of their investigations, and it’s a critical contributor to informing new detections. InsightIDR provides customers with these highly reliable, early out-of-the-box detections from our MDR team, but as security teams mature, they may be looking to expand their program to look beyond detections to root cause, broader remediation, hunting, and custom threats.
InsightIDR makes it possible for teams to continuously up-level their security programs by focusing on detections first, while also having advanced datasets—like EET or enhanced Network Traffic Analysis—available when they want a more granular look at their security data or network activity. By leveraging these add-on modules, InsightIDR customers can manage their environment with the same powerful data as our expert SOC team.
What can Enhanced Endpoint Telemetry do for you?
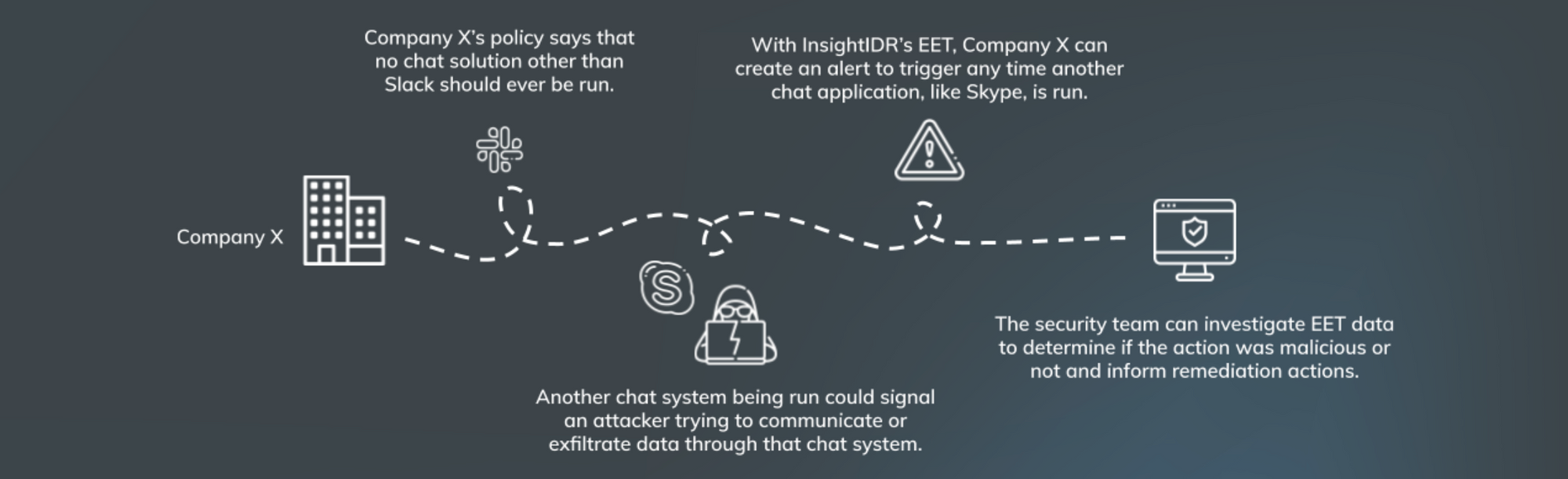
Detect and hunt custom threats. We recognize certain actions in your environment that indicate compromise may be totally normal for other organizations. For example, Skype being run on an endpoint may be routine for some organizations, but if your company policy only allows use of Slack, then it’s a red flag. We’ve got you covered. EET allows you to create alerts based on threats that are unique to your specific company policies, environment, or industry. You can also proactively hunt for threats by searching through this archive of endpoint activity data, such as patterns that may look benign in isolation, but together, indicate an attack.
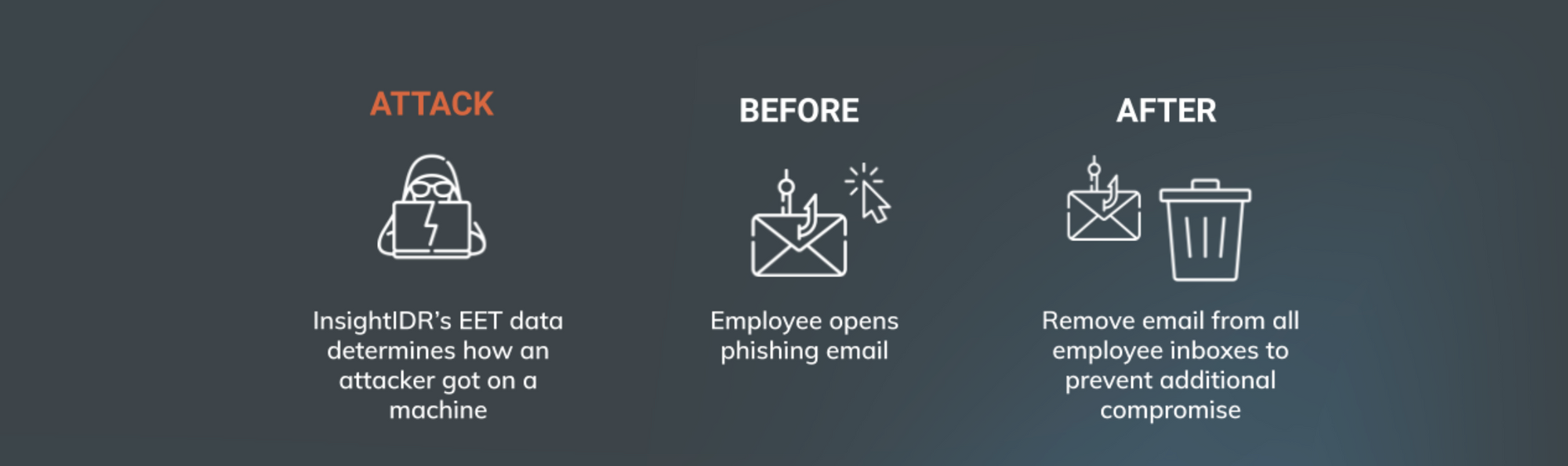
Accelerate investigations. Get the complete picture of what happened before, during, and after an attack. EET sends all endpoint start process data to log search in InsightIDR, giving you the data to understand the full scope of an attack on an endpoint, investigate incidents faster, and respond more thoroughly.
Ready to get started? Visit our help docs to learn more about EET and how it can up-level your endpoint detection capabilities in InsightIDR.

